Cyber Security News
Securityaffairs
355
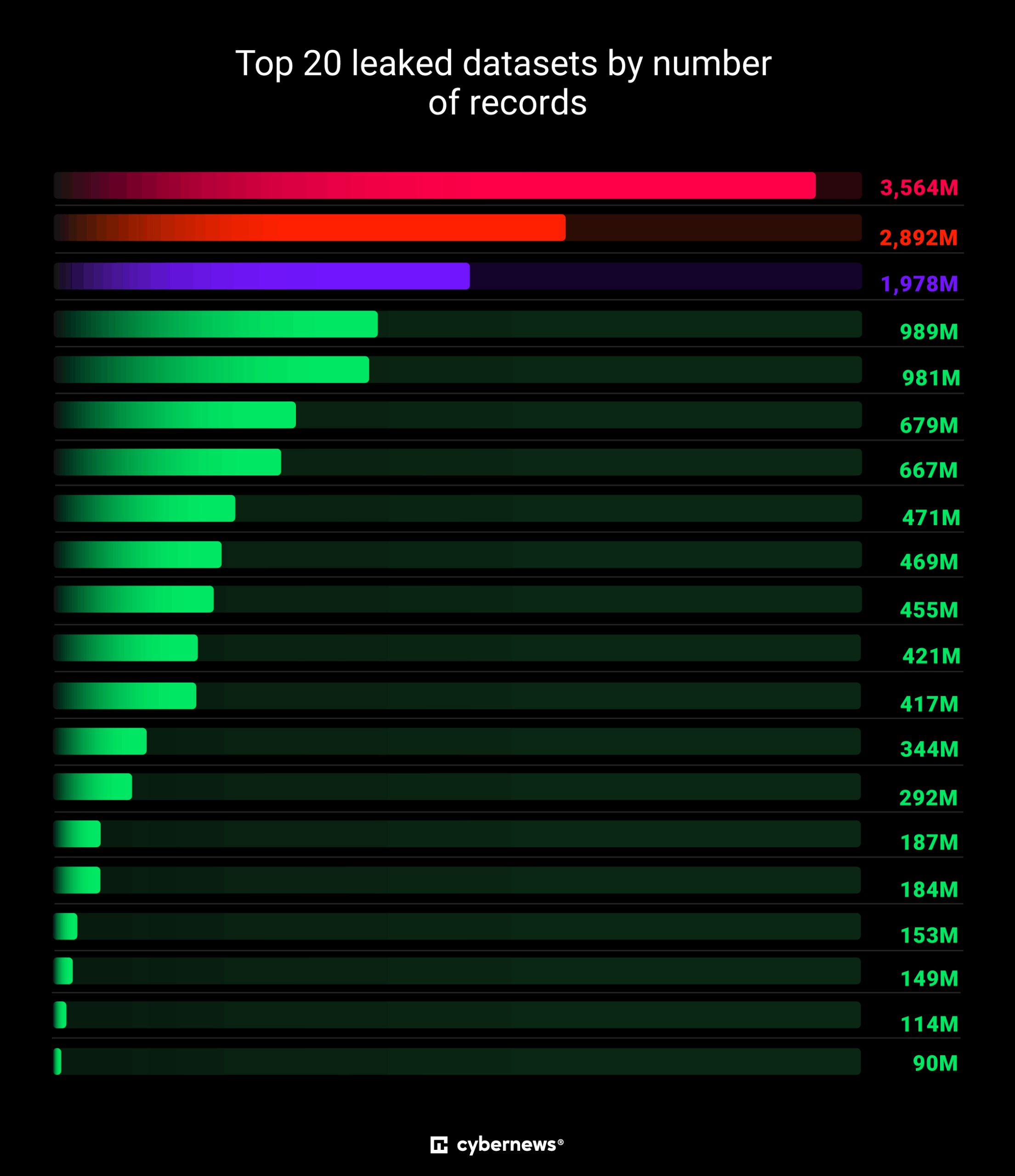
Image Credit: Securityaffairs
Researchers discovered the largest data breach ever, exposing 16 billion login credentials
- Researchers discovered the largest data breach ever, exposing 16 billion login credentials likely due to multiple infostealers.
- The discovery of the data breach, consisting of 30 massive leaked datasets totaling 16 billion exposed login records, was announced by Cybernews researchers.
- Most of the leaked datasets were newly discovered, with infostealer malware being widespread as alarming new leaks continue to surface.
- The exposed data was briefly accessible, mainly on unsecured Elasticsearch or storage instances, making it a blueprint for mass exploitation.
- The leaked data includes 16 million to 3.5 billion records targeting services like Apple, Google, Facebook, Telegram, GitHub, and government portals.
- The data likely gathered by infostealers includes tokens, cookies, and sensitive metadata, posing significant risks for phishing, ransomware, and account takeovers.
- In 2024, CyberNews also uncovered the largest password compilation called RockYou2024 containing almost 10 billion unique plaintext passwords.
- RockYou2024 is an expansion of the RockYou2021 collection discovered in 2021, hinting at a massive collection of passwords from old and new data breaches.
Read Full Article
21 Likes
TechJuice
276

Image Credit: TechJuice
Google, Apple, Meta’s18bn Passwords leaked! Do this now to Secure your account
- Cybersecurity researchers discover 30 exposed datasets with 18 billion login credentials, involving major tech giants like Google, Apple, Meta, and YouTube.
- The exposed data includes information from infostealer malware, credential stuffing sets, and repackaged leaks, posing a significant threat to online security.
- Exposed records include service URLs, login details, and passwords, making them directly usable for unauthorized access.
- Researchers highlight the continuous and evolving threat posed by these datasets.
- The presence of tokens, cookies, and metadata in the data allows attackers to bypass security measures and gather deeper insights into user accounts.
- The risk of account takeover is increased significantly due to widespread credential exposure.
- Proactive steps to secure online accounts include changing passwords, using strong and unique passwords, enabling MFA, monitoring accounts, being wary of phishing, and checking for compromise.
- Services like 'Have I Been Pwned?' can help users check if their email addresses or phone numbers have been involved in data breaches.
- Constant vigilance and strong cybersecurity practices are crucial in combating threats like infostealer malware.
Read Full Article
16 Likes
Bitcoinsensus
342

Image Credit: Bitcoinsensus
KuCoin Adds BitGo Support — Boosts Security for Institutional Trades
- KuCoin integrates BitGo's Go Network for off-exchange settlement, enhancing security for institutional trades.
- Institutional clients can trade without giving up custody of their assets.
- Assets are protected in insured, segregated wallets, reducing counterparty risk.
- The integration eliminates the need for pre-funding exchange wallets.
- Part of KuCoin's $2 billion Trust Project and regulatory expansion to enhance transparency and trust.
- Assets stay in segregated custody accounts with BitGo's $250M insurance backing.
- Institutional clients have full control with automated post-trade settlement.
- Clients can access KuCoin's spot, margin, futures, and options markets securely.
- KuCoin's move signals commitment to infrastructure, custody, and compliance for institutional players.
- The integration aligns with KuCoin's goal for a regulated, secure ecosystem across jurisdictions.
Read Full Article
20 Likes
Dev
421

Image Credit: Dev
Optimal VPC Subnetting: High Availability, Security, & Seamless On-Prem Connectivity
- Most cloud networks in enterprises require efficient IP allocation and management for high availability, security, and on-premise connectivity.
- Subnet segmentation within a VPC is essential for balancing security, scalability, and operational efficiency.
- Considerations for VPC subnet segmentation include security requirements, high availability design, IP address management, scalability, and management complexity.
- Advantages of subnet segmentation include granular security controls, resource isolation, robust defense, least privilege access, and simplified auditing.
- Efficient routable CIDR usage is promoted through segmentation to reduce reliance on limited IPAM routable addresses.
- Primary and secondary CIDR ranges play roles in optimal VPC design by accommodating workloads and providing additional IP space respectively.
- Challenges of VPC subnet segmentation include careful planning, reconfiguration difficulties, IP address limitations, and route table management overhead.
- Mitigation strategies involve planning for growth, using IP address management solutions, documenting CIDR allocations, and evaluating operational overhead.
- Clear subnet segmentation enhances security and operational benefits, offering a maintainable and scalable foundation for different resource types.
Read Full Article
25 Likes
Tech Radar
258

Image Credit: Tech Radar
Your Facebook account just got even more secure – and it could make phishing a thing of the past
- Meta has introduced passkey support for Facebook on mobile devices to enhance security and ease of login.
- Passkeys, such as fingerprints, face recognition, or PIN, offer enhanced security and quicker login compared to traditional passwords.
- Passkeys will soon be available for Facebook and Messenger on iOS and Android devices.
- Passkeys are more secure than passwords and one-time codes, making them less susceptible to theft.
- Passkeys are stored locally on the user's device, ensuring Meta does not have access to them.
- However, losing a device with the stored passkey can complicate account access and setting up a new passkey.
- Meta plans to extend passkeys to verify payments through Meta Pay and protect encrypted message backups on Messenger.
- To set up a passkey, users can navigate to Settings, then Accounts Center, and finally Passkey within the Facebook app.
Read Full Article
15 Likes
Tech Radar
48
Image Credit: Tech Radar
Minecraft players watch out - these fake mods are hiding password-stealing malware
- Cybercriminals are targeting Minecraft players to steal login credentials and crypto wallet information.
- Check Point Research discovered a large-scale operation by the Stargazers Ghost Network distributing malware and infostealers under the guise of Minecraft mods.
- The group created hundreds of malicious GitHub repositories impersonating popular Minecraft mods like Skyblock Extras and Polar Client.
- These repositories have garnered thousands of views, indicating significant success for the cybercriminals.
- The malware used in the attack is written in Java, making it undetectable by antivirus software.
- Approximately 500 GitHub repositories were part of this operation aimed at Minecraft players.
- The attackers used stars on GitHub to boost the repositories' legitimacy and increase infection chances.
- The attack involves two phases: targeting Minecraft account tokens and user data in the first phase, followed by deploying an infostealer called '44 Caliber' to steal browser data, VPN information, and crypto wallet data in the second phase.
Read Full Article
2 Likes
Securityaffairs
434

Image Credit: Securityaffairs
China-linked group Salt Typhoon breached satellite firm Viasat
- China-linked APT group Salt Typhoon hacked satellite firm Viasat and had breached multiple telecom providers previously.
- Viasat, a global communications company based in Carlsbad, California, discovered the intrusion earlier this year.
- No evidence found that Viasat customers were affected by the breach.
- The Salt Typhoon group targeted more US telecoms, including Charter Communications and Windstream, exploiting vulnerabilities in network devices.
- In response to the cyber espionage, the US, Australia, Canada, and New Zealand issued a joint advisory warning about PRC-linked threats.
- Recorded Future's Insikt Group reported ongoing attacks by Salt Typhoon on telecom providers globally by exploiting Cisco vulnerabilities.
- Cisco's zero-day vulnerabilities, CVE-2023-20198 and CVE-2023-20273, were actively exploited by Salt Typhoon for network breaches.
- Insikt Group recommended promptly patching Cisco IOS XE devices to prevent further exploitation by Salt Typhoon.
- Salt Typhoon, previously known as FamousSparrow and GhostEmperor, has been active targeting government entities and telecom companies since at least 2019.
- The article is eligible for web story generation.
Read Full Article
26 Likes
Siliconangle
210

Image Credit: Siliconangle
Tadaweb raises $20M to scale open-source intelligence platform enhanced with AI
- Tadaweb S.A. raised $20 million in funding to scale its small data operating system enhanced with artificial intelligence for generating security insights.
- The platform uses publicly available information (PAI) and open-source intelligence (OSINT) to extract actionable intelligence for enterprise businesses, law enforcement, and government agencies.
- OSINT involves collecting, analyzing, and understanding signals from various public sources like print media, online platforms, social media, and public records to address security concerns.
- Tadaweb was founded in 2011 and focuses on 'small data,' combining precise data points to offer actionable insights that can be processed by humans.
- The company utilizes AI to assist human analysts in processing data sourced from PAI, commercially available information, and emerging sources to reduce investigation time significantly.
- Tadaweb distinguishes itself by using AI to distill insights from data noise, ensuring transparency and human control over solutions while embracing AI technology.
- The company's clientele includes government agencies, national security, public safety organizations in Europe and the U.S., as well as private sector cyber threat intelligence and corporate security entities.
- Arsenal Growth and Forgepoint Capital International led the recent investment, with Wendel also participating. The total investment in Tadaweb now amounts to $40 million.
Read Full Article
12 Likes
Tech Radar
30

Image Credit: Tech Radar
Major spam email warning - AI now generates almost all of your junk mail
- Most spam emails today are AI-generated, with 51% of spam emails being produced by AI by April 2025, compared to pre-GPT era spam.
- Cybercriminals are using Generative Artificial Intelligence (GenAI) to write emails, making them more sophisticated and harder to detect.
- Business Email Compromise (BEC) attacks still rely more on human input rather than AI, with only 14% of BEC attacks being AI-generated by April 2025.
- AI-generated emails exhibit higher formality, fewer grammar errors, and increased linguistic sophistication, making them more credible to recipients.
- Attackers, especially non-native English speakers, can target English-speaking countries more easily with AI-generated spam.
- Criminals are leveraging AI to A/B test different spam variants to optimize their effectiveness in real-world environments.
- Effective defense against AI-generated spam involves AI-powered email security solutions with advanced detection capabilities.
Read Full Article
1 Like
Cultofmac
105
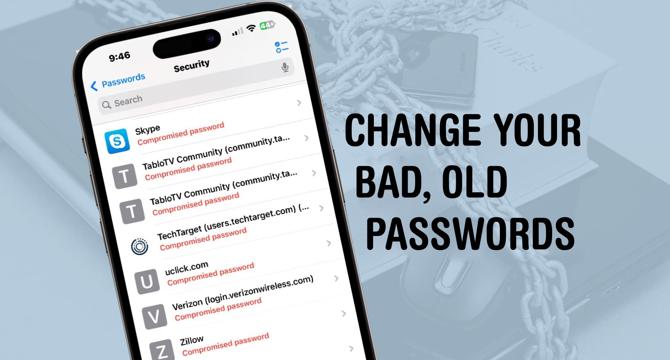
Image Credit: Cultofmac
Protect yourself online by changing bad old passwords
- A recent data leak of over 16 billion records highlights the importance of changing old passwords to protect against hackers accessing sensitive information.
- Apple's Passwords app simplifies finding leaked passwords and enables users to change them directly on their iPhone for enhanced security.
- Storing and using passwords with Passwords app makes managing multiple login details easier and encourages the use of strong, secure passwords.
- Reusing passwords across multiple sites can lead to vulnerabilities, as demonstrated by the 16 billion credentials leaked online.
- Apple devices protect stored login details effectively, reducing the risk of compromising sensitive information in case of a data breach.
- The Passwords app alerts users to compromised login details and provides a straightforward process to update passwords for improved security.
- Users can easily identify and address security issues in their passwords by utilizing the Security section in the Passwords app on iPhone, iPad, or Mac.
- Changing compromised passwords on the iPhone involves navigating to the Passwords app, selecting the Security section, and choosing accounts to update.
- The Passwords app guides users through the password change process, offering suggestions for strong passwords and securely storing new credentials.
- Regularly changing passwords is essential to prevent unauthorized access and potential financial loss, emphasizing the importance of proactive security measures.
Read Full Article
6 Likes
Medium
215

Image Credit: Medium
From Thinking to Doing
- Breakthroughs in understanding reshape the world by turning ideas into action, from tools to modern technology.
- Artificial General Intelligence explores reasoning like humans through varied approaches.
- Agentic AI systems observe, decide, and act autonomously, shifting from reactive to proactive intelligence.
- Agentic systems are reshaping machine intelligence, making AI more accessible and impactful.
- In cybersecurity, agentic AI autonomously detects and responds to threats, enhancing security measures.
- Autonomous system behaviors present ethical challenges, requiring considerations on optimal objectives.
- Agentic AI asks profound ethical questions on decision-making authority between humans and machines.
- Human judgment complements agentic systems by recognizing contextual patterns and making informed decisions.
- Successful agentic systems blend algorithmic processing with human understanding to navigate complexity.
- The future belongs to thoughtfully designed AI systems balancing autonomy with ethical frameworks for human flourishing.
Read Full Article
12 Likes
TechDigest
114

Image Credit: TechDigest
Unprecedented data breach exposes 16 billion records
- A massive data breach has exposed a staggering 16 billion login credentials, forming one of the largest data compromises in history.
- Discovered by the Cybernews research team, this breach includes supermassive datasets with structured information like URLs, login details, and passwords.
- The exposed data, likely from various sources such as infostealer malware, poses a significant risk to online security.
- The breach provides cybercriminals access to a wide array of online services, potentially leading to account takeovers, identity theft, and highly targeted phishing.
- Researchers warn that this breach is fresh and weaponizable intelligence at scale, incorporating recent infostealer logs, tokens, cookies, and metadata.
- While the datasets were briefly accessible online, the owners are unidentified, posing challenges in determining the exact number of affected individuals.
- Basic cybersecurity measures are critical, urging users to use strong passwords and enable multi-factor authentication across all accounts.
- Organizations with poor credential hygiene practices are at risk of various cyber attacks like phishing campaigns, ransomware intrusions, and account takeovers.
- Users need to be vigilant against infostealer malware and regularly review systems to prevent further data loss.
Read Full Article
6 Likes
Ars Technica
122

Image Credit: Ars Technica
Israel-tied Predatory Sparrow hackers are waging cyberwar on Iran’s financial system
- The Israel-linked hacker group Predatory Sparrow has been conducting destructive cyberattacks on Iran, targeting its financial system.
- They recently attacked the Iranian crypto exchange Nobitex, destroying over $90 million in holdings and accusing the exchange of supporting terrorism and violating sanctions.
- In a separate attack on Iran's Sepah bank, they claimed to have destroyed all the bank's data, citing associations with the Islamic Revolutionary Guard Corps.
- The cyberattacks have caused disruptions, with reports suggesting Sepah's online banking and ATMs being offline, affecting civilians' access to funds.
- Predatory Sparrow's sabotage involved moving stolen funds to crypto addresses with politically charged titles to effectively 'burn' the money.
- Blockchain analysis revealed links between Nobitex and sanctioned groups, showing the exchange's involvement in evading sanctions through cryptocurrency.
- The group, potentially linked to Israel's military or intelligence agencies, has a history of targeting Iran's critical infrastructure and conducting destructive attacks.
- The motives behind Predatory Sparrow's focus on Iran's financial sector remain unclear, indicating possible future cyber warfare actions with serious consequences.
- The group's capabilities and past actions make them a significant threat, with the potential to follow through on their cyber threats.
- The situation highlights the escalating cyber warfare dynamics between various state-sponsored and hacktivist groups.
Read Full Article
7 Likes
Pcgamer
8

Image Credit: Pcgamer
Fake Minecraft mods that steal all your personal data including crypto wallets are being distributed via GitHub accounts
- Fake Minecraft mods distributed via GitHub accounts are stealing personal data including crypto wallets.
- Security researchers discovered a malware campaign targeting Minecraft users conducted by the Stargazers Ghost Network.
- Malicious Java downloaders impersonating Minecraft cheat tools are being distributed on GitHub repositories.
- These downloaders are undetected by antivirus software and mainly target Minecraft users.
- The malware steals browser credentials, cryptocurrency wallets, VPN information, and other sensitive data.
- The threat actor behind these campaigns is believed to be of Russian origin.
- Popular gaming communities can be exploited as effective vectors for malware distribution.
- Users are advised to download mods only from known and trusted sources to avoid falling victim to such attacks.
Read Full Article
Like
Tech Radar
127

Image Credit: Tech Radar
Major US healthcare data provider hit by data breach - over 5 million patients affected, here's what we know
- Episource, a major US healthcare data provider, confirmed a cyberattack in late January 2025, affecting over 5 million patients, including policy and MedicAid information.
- The intrusion was discovered on February 6, 2025, and data copies were taken between January 27 and February 6, 2025.
- Data stolen includes health plans, insurance companies, member/group ID numbers, Medicaid-Medicare ID numbers, medical records, diagnoses, medications, test results, and personal data like dates of birth and Social Security numbers.
- Cybercriminals often target healthcare organizations for sensitive data that can be used in phishing and identity theft scams.
- Episource reported to have notified 5,418,866 affected individuals on April 23, 2025.
- The company advises impacted individuals to stay vigilant against potential impersonation and scam attempts.
Read Full Article
7 Likes
For uninterrupted reading, download the app