Cyber Security News
The Register
74

Image Credit: The Register
How to bridge the MFA gap
- Multi-Factor Authentication (MFA) plays a crucial role in protecting organizations despite low global adoption rates.
- Challenges to MFA deployment include cost constraints and complexities in selecting the right tools.
- An excessive number of MFA solutions can confuse users and lead to decreased security.
- Improperly implemented MFA systems can hinder productivity and increase a company's attack surface.
- Various attacks on MFA systems such as social engineering, SIM swapping, and session hijacking highlight vulnerabilities.
- Strategies to enhance MFA include comprehensive coverage, self-service password reset, and dynamic verification methods.
- Specops Software offers solutions like Specops Secure Access to streamline MFA deployment and improve security measures.
- The platform integrates with Active Directory, provides reporting capabilities, and enhances user authentication through contextual information.
- Specops uReset proved effective in large-scale password resets, aiding organizations like the Kalix municipality in recovering from ransomware attacks.
- Features of Specops Secure Access include fatigue attack protection, Active Directory integration, and scalability for MFA implementations.
Read Full Article
4 Likes
Medium
400

Fighting Deepfakes: Why a Proactive Defense is Key
- The current approach to deepfakes is reactive, waiting for them to go viral before debunking them.
- A proactive framework called 'Adaptive Spider Web' has been designed to embed a digital shield into images and videos at creation to prevent deepfakes.
- The defense system of 'Adaptive Spider Web' works in two integrated layers.
- By adopting a proactive strategy, creators can make content 'fireproof' from the source, putting control back in their hands.
- The proactive approach aims to shift from being 'firefighters' to preventing deepfakes from being created.
- Further innovation includes designing a collaboration platform integrating AI and a wearable device to optimize sleep cycles for productivity.
- Addressing the challenge of generative AI through innovation is crucial for building a safer digital future.
- The 'Adaptive Spider Web' proposal encourages collaboration and discussion on enhancing digital security.
- For a detailed technical exploration, the project repository can be accessed on GitHub at: 'https://github.com/rijal028/Adaptive-Web-Concept-Hub'
Read Full Article
24 Likes
Siliconangle
1.6k

Image Credit: Siliconangle
AWS focuses on simplifying cloud security at re:Inforce 2025 conference
- AWS announced enhancements at its re:Inforce 2025 conference to simplify cloud security at enterprise scale.
- The focus is on simplifying security while helping organizations manage risk and respond to threats effectively.
- Key updates include a new version of AWS Security Hub that prioritizes critical security issues and aids in reducing security risks.
- The updated Security Hub correlates findings across various tools into one actionable feed, boosting incident response efficiency.
- AWS Shield now includes network posture management with automated discovery of resources and remediation steps integrated in the console.
- Amazon GuardDuty Extended Threat Detection extends coverage to containerized environments like EKS for improved threat detection.
- Additional updates include improvements to AWS WAF, Amazon CloudFront, IAM Access Analyzer, and mandatory multifactor authentication for root users.
- AWS Network Firewall now blocks indicators of compromise, and multiparty approvals for air-gapped vaults enhance backup resilience.
- Development security offerings were enhanced with Amazon Inspector becoming generally available for code scanning.
- AWS introduced Amazon Verified Permissions for Express.js developers to implement authorization in web application APIs more easily.
- The release of @verifiedpermissions/authorization-clients-js simplifies authorization implementation for Express.js developers.
Read Full Article
15 Likes
Dev
193

Image Credit: Dev
CVE-2023-0386: Linux Kernel Improper Ownership Management Vulnerability
- CVE ID: CVE-2023-0386
- Vulnerability Name: Linux Kernel Improper Ownership Management Vulnerability
- Date Added: 2025-06-17, Due Date: 2025-07-08
- Description: Linux Kernel has an improper ownership management vulnerability in the OverlayFS subsystem, allowing local users to escalate privileges by copying a capable file from a nosuid mount.
- Known To Be Used in Ransomware Campaigns: Unknown
- Action: Apply mitigations as per vendor instructions or discontinue product use if mitigations are not available.
- Additional Notes: The vulnerability affects a common open-source component. Links for more information: https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=4f11ada10d0a, https://access.redhat.com/security/cve/cve-2023-0386, https://security.netapp.com/advisory/ntap-20230420-0004/, https://nvd.nist.gov/vuln/detail/CVE-2023-0386
- More CVEs: Common Vulnerabilities & Exposures (CVE) List
Read Full Article
11 Likes
Siliconangle
225

Image Credit: Siliconangle
Engineering at speed: Fortinet’s playbook for cybersecurity success
- Fortinet Inc. continues its successful momentum in cybersecurity innovation despite macroeconomic uncertainties.
- John Whittle, COO of Fortinet, emphasizes the need to focus on engineering at speed to outpace evolving threats and competition.
- Fortinet's playbook includes elements like engineering fast, building natively, and serving relentlessly in the cybersecurity landscape.
- The company's strategy revolves around conscientious speed in innovation and execution, emphasizing organic product development for deep integration.
- Fortinet's shared operating system across various security offerings simplifies deployment and enhances the customer experience.
- The company aims to address the cybersecurity skills shortage by being a trusted partner in protecting customers against evolving threats.
- With over 500 AI-related patents, Fortinet excels in practical AI deployments for threat detection and automated incident response.
- Fortinet's AI-powered SecOps tools focus on solving customer problems effectively.
- Fortinet Inc. sponsored a CUBE Conversation highlighting its cybersecurity innovations.
Read Full Article
13 Likes
The Verge
294

Image Credit: The Verge
WhatsApp’s rollout of ads will change the app forever
- WhatsApp, known for its ad-free messaging approach, is now introducing ads within the app despite earlier commitments.
- Meta, WhatsApp's parent company, plans to place ads in the 'Update' tab, featuring sponsored status updates from businesses.
- The ads will be integrated into WhatsApp's status feature, where users can share disappearing photos, videos, and messages.
- Meta assures that personal messages, calls, and statuses will remain encrypted and not utilized for ad targeting.
- Meta generated over $160 billion in ad revenue from Facebook and Instagram in 2024, hinting at a possible increase in ads on WhatsApp.
Read Full Article
17 Likes
Dev
312

Image Credit: Dev
Mastering DevSecOps and GitOps for Secure Cloud-Native Applications
- The article highlights the importance of integrating DevSecOps practices with GitOps in the cloud-native landscape for enhanced security.
- GitOps, with its focus on a declarative model within Git repositories, aligns naturally with DevSecOps goals of embedding security early in the SDLC.
- Key strengths of GitOps such as establishing a single source of truth, immutability, and continuous reconciliation are beneficial for security and compliance.
- Integration of DevSecOps practices like shift-left security, policy as code, secret management, and runtime security enhances the security posture of GitOps pipelines.
- Challenges in adoption include cultural shifts, managing complexity, tooling integration, and the need for continuous training and awareness programs.
- Addressing these challenges can lead to a more resilient and secure GitOps pipeline, improving the efficiency of software delivery.
Read Full Article
18 Likes
Lastwatchdog
112

MY TAKE: Microsoft takes ownership of AI risk — Google, Meta, Amazon, OpenAI look the other way
- At Microsoft Build, Azure CTO warned about AI vulnerabilities, including jailbreak-style attacks and structural limitations.
- Microsoft admitted Crescendo Attacks, where AI can unknowingly step over the line due to training to be helpful.
- They introduced the concept of Crescendomation, AI learning to jailbreak itself, revealing vulnerabilities.
- Microsoft acknowledged that smarter AI systems may become more vulnerable, a structural flaw in AI.
- Microsoft's Discovery platform deploys agentic AIs in R&D, addressing complex problems like designing PFAS-free cooling fluids.
- Comparison with other tech giants reveals Microsoft's transparency in addressing AI vulnerabilities, unlike Google, Meta, Amazon, and OpenAI.
- Google remains opaque about vulnerabilities in its Gemini model and focuses on performance improvements.
- Meta acknowledges safety limitations but lacks transparent articulation for hardening strategies.
- Amazon is methodical in mitigating jailbreaks but lacks public narrative, missing an opportunity to lead on trust.
- Anthropic prioritizes safety in AI models with Constitutional AI framework, emphasizing trustworthiness from the start.
Read Full Article
6 Likes
Arstechnica
66

Image Credit: Arstechnica
Cybersecurity takes a big hit in new Trump executive order
- Cybersecurity practitioners are concerned about a new executive order from the White House.
- The order weakens cybersecurity requirements for government software and network security.
- The executive order, issued on June 6, reverses key cybersecurity orders put in place by President Joe Biden.
- Donald Trump's executive order criticized Biden's directives on cybersecurity as introducing distracting issues.
- Trump's order is described as pro-business and anti-regulation.
- Trump's order relaxed or eliminated requirements for quantum-safe encryption, Secure Software Development Framework, phishing-resistant regimens, securing Internet routing, and digital identity forms.
- Some of the dropped requirements included mandating federal agencies and contractors to adopt quantum-safe encryption products as they become available.
- A stringent Secure Software Development Framework (SSDF) for federal software and services was one of the relaxed orders.
- The order also eased the adoption of phishing-resistant regimens like the WebAuthn standard.
- Implementation of new tools for securing Internet routing through the Border Gateway Protocol was another requirement relaxation.
- The order encouraged the use of digital forms of identity.
- Cybersecurity experts are worried about the implications of the executive order on national security.
- The order undermines efforts to strengthen cybersecurity controls amidst evolving threats.
- The decision to reverse these cybersecurity mandates has raised questions about the government's commitment to cybersecurity.
- Overall, the new executive order is causing significant debate within the cybersecurity community.
- It remains to be seen how this shift in cybersecurity policy will impact government agencies and national cybersecurity measures.
Read Full Article
3 Likes
Siliconangle
396

Image Credit: Siliconangle
How DevSecOps is creating ‘a continuous thread of trust’ in software development
- DevSecOps, which integrates security into the software development process, is gaining popularity in the enterprise world.
- At the recent AppDev Done Right Summit, experts highlighted the importance of incorporating security in continuous integration/continuous delivery pipelines for enhanced value and faster software delivery.
- The emphasis is on shifting security left and enabling it in every stage of the CI/CD pipeline, from code to cloud, to secure software supply chains, policy as code, threat detection, and cloud-native environments.
- Security is seen as a continuous thread of trust rather than just a gate in the DevSecOps approach.
- The three stages of DevSecOps are Day Zero (planning), Day One (building and release), and Day Two (operations, observability, and incidence response).
- Incorporating security into each stage has presented challenges, with a survey showing only 8% of respondents able to ship code hourly despite 24% desiring to do so.
- There is a growing need for systems that evolve, learn, and recover in real-time, with a call for full-stack observability solutions to address the tool sprawl in the ecosystem.
- DevSecOps is deemed a shared responsibility to create reliable and trusted software, requiring collaboration across teams.
- The industry is shifting towards a unified approach that goes beyond monitoring to include logging, tracing, and actionable insights for faster application delivery.
Read Full Article
23 Likes
Hackernoon
70
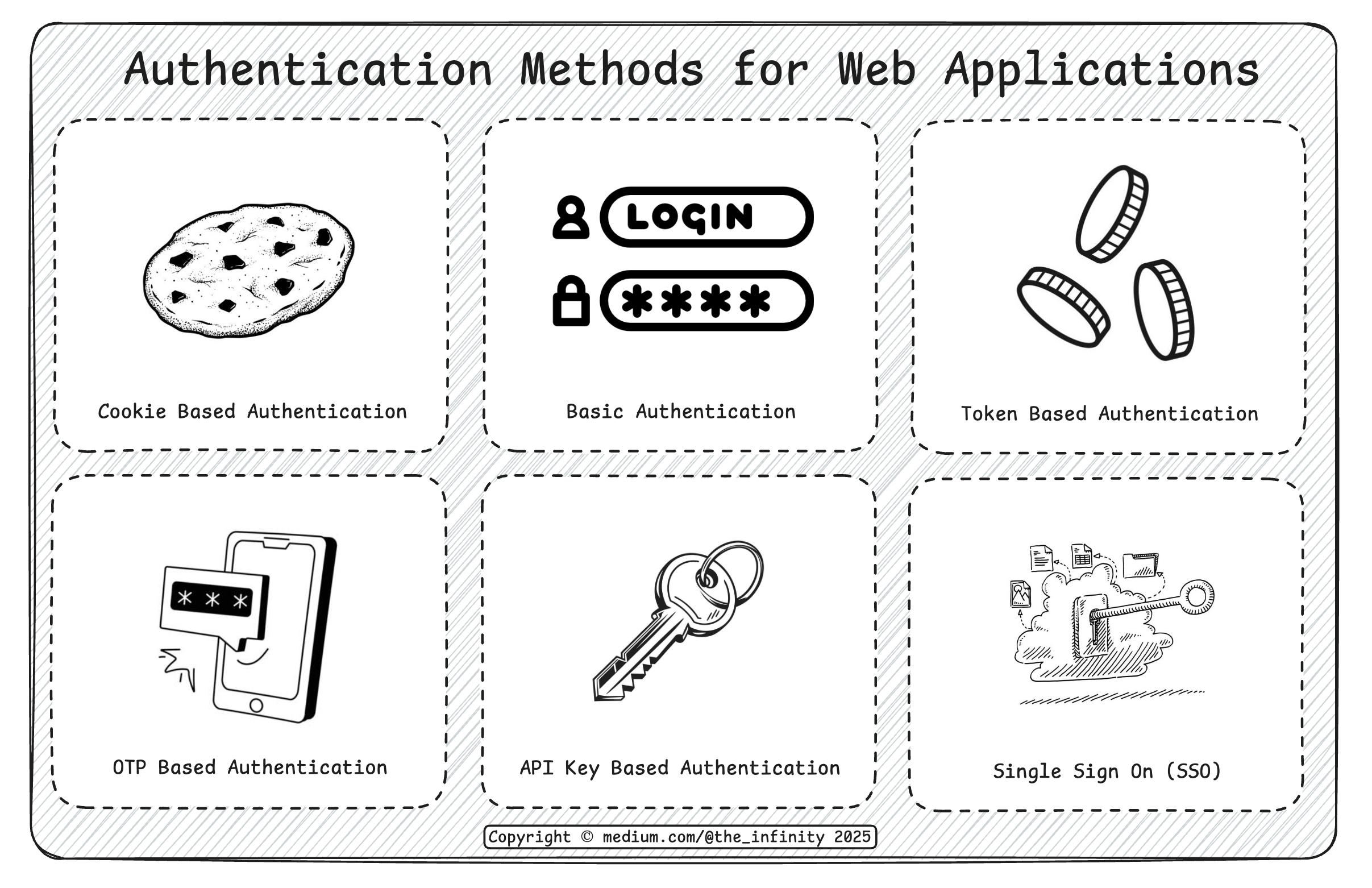
Image Credit: Hackernoon
6 Login Methods Every Developer Should Know
- Authentication methods like Basic Auth, Cookies, Tokens, API Keys, OTP, and SSO serve specific purposes with varying levels of security and usability.
- Basic Authentication, the oldest method, is simple but insecure due to vulnerabilities like man-in-the-middle attacks and lack of server-side logout.
- Cookie-Based Authentication enhances security with features like server-side logout but requires server-side session management and may not scale well.
- Token-Based Authentication provides a stateless, scalable solution with JWT being a popular choice, although securely storing tokens is crucial.
- API Key-Based Authentication is used for accessing APIs, offering simple access control and monitoring for billing, analytics, and security.
- OTP-Based Authentication adds security through unique, time-sensitive codes transmitted via trusted channels, reducing risks like phishing.
- SSO enables users to log in once and access multiple services without repeated logins, streamlining authentication across various systems.
- Each method has its pros and cons in terms of security, scalability, and usability, catering to different use cases and security requirements.
- These authentication methods play crucial roles in web app development, offering a range of options to verify and secure user identities efficiently.
- Understanding these authentication methods is essential for developers to implement robust and secure login systems in their web applications.
- The blog covers Basic Auth, Cookies, Tokens, API Keys, OTP, and SSO authentication methods, detailing their mechanisms and applications.
Read Full Article
4 Likes
TechBullion
4
Image Credit: TechBullion
Latent AI Launches Groundbreaking “Latent Agent” Platform to Eliminate “Model-to-Hardware” Guessing Game for Devices
- Major enterprises face challenges deploying AI models on edge devices due to compatibility and performance issues related to memory, computing capability, latency, and power usage.
- The launch of Latent Agent by Latent AI aims to eliminate the 'model-to-hardware' guessing game and accelerate AI deployment on edge devices.
- Latent Agent empowers developers to describe deployment needs in plain English, providing optimized AI model recommendations based on real-world performance data.
- Developers can streamline the process using Latent Agent's natural language interface in Visual Studio (VS) Code, simplifying AI model optimization.
- The platform utilizes over 200,000 hours of real-world data to make precise model recommendations for edge devices, reducing deployment times significantly.
- Latent Agent's self-healing models automatically detect and resolve performance issues, ensuring uninterrupted productivity in enterprise environments.
- LEIP, Latent AI's primary edge AI modeling solution, has already shown success in industries like the United States Navy Task Force and the Future of Sports (FSP).
- Several enterprises, including Gartner Peer Insights, have benefited from Latent AI's solutions by reducing model deployment times, enhancing operations, and transforming sports venues.
- Latent Agent revolutionizes AI deployment by offering a future where scaling AI across edge devices is faster, efficient, and more reliable.
- With Latent Agent, the process of deploying AI models on edge devices becomes more straightforward and efficient, marking a significant advancement in AI technology.
Read Full Article
Like
TechBullion
154
Image Credit: TechBullion
Mattermost Launches Enterprise Advanced: Multi-Domain Operations for Defense, Intelligence, and Critical Infrastructure
- Mattermost has launched Enterprise Advanced, a new product tier designed for high security and complex mission environments.
- Enterprise Advanced is aimed at defense, intelligence, cybersecurity, and critical infrastructure sectors, offering secure collaboration and AI-ready capabilities.
- The platform provides sovereign control, accelerates operations, enforces Zero Trust security, and ensures compliance with cybersecurity standards.
- It goes beyond communication to secure, automate, and align operations with national security mandates.
- Enterprise Advanced unifies teams with access controls, workflow automation, and incident response for mission success.
- The platform is suitable for government, defense agencies, intelligence, and critical infrastructure organizations.
- It offers Zero Trust-aligned security controls, sensitive information controls, and advanced workflows.
- Enterprise Advanced is engineered for secure collaboration, sovereign control, and automation in high-stakes environments.
- The new tier will be available in July 2025 and will undergo continuous enhancements throughout the year.
- Mattermost's platform supports MissionOps, DevSecOps, Cyber and Defense with messaging, file sharing, audio, screen sharing, workflow automation, and AI assistance.
- It is trusted by the U.S. Department of Defense and Fortune 500 companies.
- Mattermost is co-developed with security experts to meet demanding operational needs.
- Enterprise Advanced empowers operations with enhanced security, agility, and confidence in hostile environments.
- The platform is designed for operators managing complexity under pressure.
- For more information about Mattermost Enterprise Advanced, visit their website or contact the sales team.
Read Full Article
9 Likes
Siliconangle
424

Image Credit: Siliconangle
Key takeaways from Cisco Live 2025
- Cisco Live 2025 was highlighted by Jeetu Patel as a significant event focusing on AI strategy and product unveiling.
- Cisco's emphasis on AI networking showcased the importance of networks in the AI era, leading to growth opportunities.
- The company's growth prospects are no longer constrained, with a focus on security and AI networking expansion.
- Cisco's unique advantage lies in Silicon One, enabling tailored networking solutions for the AI era.
- CX transformation aligned with product offerings ensures customer success and product absorption.
- Cisco's shift towards embracing multivendor environments signifies a move towards openness and collaboration.
- The company's positive outlook, new product offerings, and focus on AI position it for significant growth.
- Cisco's stock at a 25-year high indicates confidence in its future prospects and strategic direction.
- Executive appointments and strategic moves like embracing openness aim to propel Cisco's growth in the coming years.
- Zeus Kerravala from ZK Research shared insights and reflections on Cisco Live 2025 in this article for SiliconANGLE.
Read Full Article
25 Likes
Tech Radar
0

Image Credit: Tech Radar
Cybercrime gang hacks major health data provider - millions of highly personal files could be at risk of breach
- A cybercrime gang, World Leaks, claims to have hacked Freedman HealthCare, a U.S.-based consulting firm.
- The group has allegedly exfiltrated tens of thousands of sensitive files from the consulting firm.
- World Leaks, a new player in cybercrime, is possibly linked to other infamous organizations but the exact connection is uncertain.
- The attackers have not yet disclosed the nature of the stolen 42,204 files, amounting to over 50GB.
- Freedman HealthCare deals with personal health information of millions of Americans.
- The company's involvement in handling various sensitive data for healthcare and state agencies raises concerns.
- Freedman HealthCare has not officially responded to the cyberattack claims.
- World Leaks operates on an 'extortion-as-a-service' model and was initiated in early 2025.
- The threat actors behind World Leaks are believed to be Russian and have targeted over 150 victims in the past year.
- The cybercriminal group is active and may resort to ransom demands to pressure organizations into paying.
- The precise link between World Leaks and other cybercrime entities like Hunters International remains unclear.
- Hunters International, associated with previous cyber incidents, may have inspired the creation of World Leaks.
- The ransomware tactics of Hunters International reportedly led them to adopt a new extortion method.
- The emergence of World Leaks signals a shift towards a service-based approach in cyber extortion.
- The cybercriminals are leveraging the threat of data leaks to potentially extort funds from affected organizations.
Read Full Article
Like
For uninterrupted reading, download the app