Cyber Security News
Tech Radar
412

Image Credit: Tech Radar
Scania hit by cyberattack - thousands of customers potentially affected, here's what we know
- Scania, a Swedish automotive manufacturer, was hit by a cyberattack where hackers accessed sensitive customer data.
- The attack involved an external IT partner losing login credentials through an infostealer, which hackers used to access Scania and steal files.
- Hackers demanded money from Scania and later offered the stolen archive for sale on the dark web.
- A dark web forum ad claimed to be selling a database allegedly taken from 'insurance.scania.com' containing 34,000 files.
- Scania confirmed the breach originating from the external IT partner in late May 2025 as a supply chain attack.
- A perpetrator used leaked credentials to access an insurance system and downloaded documents related to insurance claims.
- The stolen files may contain sensitive information, and the number of affected individuals is currently unknown.
- The threat actor attempted to extort money from Scania but eventually offered the database for sale on the dark web.
Read Full Article
23 Likes
TechBullion
61

Image Credit: TechBullion
Cybersecurity in 2025: What You Need to Know
- Cybersecurity in 2025 is evolving rapidly with increasing threats like ransomware, phishing scams, and AI-powered attacks.
- Businesses need to be informed and protected as cyber threats are now considered business risks rather than just technical issues.
- The average cost of a data breach has exceeded $5 million with small and medium-sized businesses facing the brunt of such incidents.
- Companies face threats due to the rise in devices, access points, and more advanced attackers, making every business a potential target.
- In 2025, businesses require a proactive, layered cybersecurity strategy, going beyond traditional antivirus software.
- Key components of an effective cybersecurity strategy include advanced threat detection tools, limited access, regular system updates, employee training on cybersecurity, and 24/7 threat response.
- Human error remains a significant cybersecurity vulnerability, emphasizing the need for employee training to identify suspicious emails and prevent common attacks.
- Hudson Strategic Technologies offers tailored information technology solutions, technical support, and IT consulting to protect businesses against cyber threats.
- Services provided by Hudson Strategic Technologies include installing and configuring security tools, offering managed cybersecurity solutions, and responding quickly to threats round the clock.
- Businesses in Plano, Richardson, Frisco, Allen, and beyond can benefit from personalized services, responsive action, and reliable protection from cyber threats through Hudson Strategic Technologies.
Read Full Article
3 Likes
Secureerpinc
184

TikTok Users Targeted by AI Malware Videos
- Trend Micro discovered AI malware targeting TikTok users by offering fake premium versions of software for free.
- Cybercriminals create TikTok accounts to spread malicious content quickly using AI-generated spoken instructions.
- The malware tricks users into downloading harmful software that can steal login and payment details.
- Organizations need to educate employees on recognizing modern threats like deepfake phishing emails.
- Implementing strong spam filters and configuring firewalls can help stop threats before interaction.
- Regularly updating software and investing in antimalware programs are vital for cybersecurity measures.
Read Full Article
11 Likes
Wired
351

Image Credit: Wired
Israel-Tied Predatory Sparrow Hackers Are Waging Cyberwar on Iran's Financial System
- The Israel-linked hacker group Predatory Sparrow, known for disruptive attacks, targets Iran's financial system, destroying $90 million in crypto assets from Nobitex.
- In another attack, they claim to have destroyed all data of Iran's Sepah bank, impacting civilians' fund access and showing links to IRGC.
- The group's sabotage includes using crypto addresses with political messages, indicating a focus on political rather than financial motives.
- Elliptic confirms Nobitex's links with sanctioned groups, making the attack not only disruptive but also an act of sabotage against Iran's sanctions evasion.
- Predatory Sparrow, with possible ties to Israel's military, has a history of cyberwarfare against Iran, targeting critical infrastructure like railways and gas stations.
- The group's recent focus on Iran's financial sector could signal vulnerability or strategic targeting, potentially leading to more consequential attacks.
- Cybersecurity experts warn of serious consequences as Predatory Sparrow's capabilities indicate they can follow through on threats, hinting at more attacks to come.
- The ongoing cyber conflict highlights the increasing role of hacktivists and state-sponsored hackers in modern conflicts, with expected cyberattacks from various actors.
- The situation remains unclear, but given Predatory Sparrow's history and capabilities, the financial sector attacks could be a prelude to more significant disruptions.
- Cybersecurity researcher Hamid Kashfi notes the collateral damage from the attacks on Sepah bank, affecting online banking and ATMs, causing chaos for civilians.
Read Full Article
21 Likes
Pymnts
10.5k

Image Credit: Pymnts
IBM Creates Integrated Solution for AI Security and Governance
- IBM has integrated its AI governance tool, watsonx.governance, and AI security tool Guardium AI Security to enhance security and governance for AI systems.
- The integration aims to bring AI security and governance teams together, provide a unified view of enterprise risk posture, and support compliance standards.
- The enhanced tools can now detect new AI use cases, automate red teaming for vulnerability detection, and facilitate monitoring of AI agents.
- Embedding security from the start is crucial for protecting data, ensuring compliance, and building trust, according to IBM.
- Chief financial officers are adopting generative AI, but some express concerns about its reliability and potential security risks.
- A PYMNTS Intelligence report highlighted worries about generative AI producing less insightful results, unauthorized data access, and output integrity issues.
- Another report noted a significant increase in COOs leveraging AI-powered cybersecurity management systems to mitigate security breaches and fraud.
- AI is becoming an essential tool for organizations to enhance cybersecurity and combat fraudulent activities.
Read Full Article
52 Likes
Dev
48

Image Credit: Dev
Exploring Cybersecurity Roles: A Walkthrough of TryHackMe's "Careers in Cyber" Room
- The article discusses the author's experience exploring cybersecurity roles through TryHackMe's 'Careers in Cyber' room.
- The room is designed as a career exploration module rather than a traditional hacking challenge, focusing on various cybersecurity roles.
- Key roles covered include Security Analyst, Security Engineer, Incident Responder, Penetration Tester, and Governance, Risk, and Compliance (GRC) professional.
- Each role's responsibilities, required skills, and recommended learning paths are outlined in the article.
- The author provides personal insights on each role, highlighting their unique aspects and ideal personality fits.
- Lessons learned emphasize the diversity of roles in cybersecurity, the importance of soft skills, and the value of starting with curiosity.
- The author's next steps involve focusing on the Security Analyst path and further developing skills through TryHackMe's learning paths.
- The Careers in Cyber room is praised for its informative and structured approach, offering clear guidance for individuals navigating cybersecurity career choices.
- The article encourages beginners or those considering a career switch to explore the room to gain insights into the cybersecurity landscape.
Read Full Article
2 Likes
TechCrunch
140

Image Credit: TechCrunch
Hackers steal and destroy millions from Iran’s largest crypto exchange
- Iran's largest crypto exchange, Nobitex, was hacked, leading to funds being drained from its hot wallet.
- The company detected unauthorized access to its infrastructure and hot wallet, storing customers' cryptocurrency.
- Hackers stole at least $90 million of Nobitex's assets by sending the crypto to inaccessible wallets.
- Blockchain analysis firm Elliptic confirmed the funds were effectively taken out of circulation.
- The cyberattack was claimed by the hacking group Predatory Sparrow, known for targeting Iranian organizations.
- The group alleged Nobitex financed terrorism for the Iranian regime and evaded international sanctions.
- Nobitex has over 10 million customers, according to archived data.
- Predatory Sparrow also claimed responsibility for a hack on Iran's Bank Sepah, causing ATM outages.
- Israel and Iran are engaging in cyberattacks amid military conflict.
- Predatory Sparrow, tied to Israeli interests, has a history of targeting Iranian entities.
- Iranian media reported Israel conducting a cyber war against Iran's digital infrastructure.
- Nobitex stated its website and app will be unavailable during the investigation.
- The incident highlights security challenges in the cryptocurrency sector.
- The hack underscores the ongoing geopolitical tensions between Israel and Iran.
- The situation raises concerns about the vulnerability of digital assets to cyber threats.
Read Full Article
8 Likes
Tech Radar
371

Image Credit: Tech Radar
Asana admits one of its AI features might have exposed your data to other users
- Asana introduces Model Context Protocol (MCP) server tool for AI interaction in May 2025, allowing natural language queries and real-time updates.
- A bug in the tool exposed Asana user data to other MCP users, potentially leaking sensitive information like project metadata and team details.
- The bug was discovered on June 4 after leaking data for a month, affecting around 1,000 customers out of Asana's 130,000 paying customers worldwide.
- Asana is sending notices to impacted organizations and advising users to review logs for MCP access and set restrictions on integrations for safety.
Read Full Article
16 Likes
Siliconangle
417

Image Credit: Siliconangle
INKY warns of new QR code phishing tactic using embedded JavaScript
- Cybersecurity company INKY Technology Corp. warns of a new phishing threat using QR codes with embedded JavaScript.
- Attackers are now using QR codes with raw HTML and JavaScript to execute payloads instantly upon scanning.
- This method bypasses the need for link clicks and can hijack login pages, capture keystrokes, and launch exploits within the browser.
- Malicious JavaScript in the QR codes can create fake login portals, exfiltrate data, and fingerprint devices for exploitation.
- The technique involves embedding base64-encoded HTML in QR codes, which, when scanned, automatically opens and executes in the system browser.
- These QR codes evade traditional security measures as the payload is self-contained and does not rely on external URLs.
- Using advanced compression and encoding, attackers can hide malware in QR codes to avoid detection.
- INKY recommends organizations to educate users against scanning unsolicited QR codes, disable automatic browser opening, and report suspicious emails to security teams.
Read Full Article
25 Likes
The Verge
395

Image Credit: The Verge
Eufy’s new smart display keeps an eye on your security cams
- Eufy is launching a portable smart display, the Smart Display E10, for monitoring security devices from a single hub.
- The E10 can display up to four live camera feeds, pair with AI-supported video doorbells and smart locks, and provide live notifications and facial recognition.
- It features an 8-inch HD touchscreen, 4,050mAh battery lasting over 24 hours, and supports LAN and dual-band Wi-Fi 6 connections.
- When paired with the Homebase S380 data hub, the E10 generates a morning 'Sunrise Summary' and an evening 'Twilight Recap' of captured events.
- These summaries include AI facial and package recognition features combined with stitched video clips.
- The E10 automatically shows live feed from Eufy doorbells or locks when motion is detected or the doorbell is pressed.
- It will be available for $199.99 on Amazon and Eufy's webstore starting June 30th, with presales available now.
- There's no confirmation yet on the E10's compatibility with third-party smart home security devices.
- The E10 comes with a charging station and wall stand for flexible positioning around the home.
- Leaks prior to the official announcement revealed technical specifications similar to those of the E10.
- The E10 can be mounted on a wall or carried between rooms due to its portable design.
- It provides notifications and facial recognition features for enhanced security monitoring.
- The E10 combines multiple security devices into a single hub for convenient control.
- Users can view multiple camera feeds simultaneously on the E10's 8-inch touchscreen.
- Eufy plans to offer a 'Sunrise Summary' in the morning and a 'Twilight Recap' in the evening for captured events.
- Live feeds from smart doorbells or locks appear on the E10 when triggered, displaying visitor information if recognized.
Read Full Article
23 Likes
The Verge
70
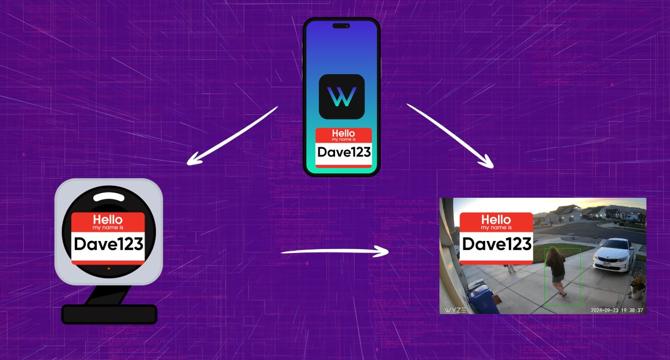
Image Credit: The Verge
Wyze tell us why its security cameras deserve your trust again
- Wyze introduces VerifiedView feature to enhance security by embedding user ID into camera footage metadata, preventing unauthorized access.
- The company admits to past security flaws and emphasizes the importance of rebuilding trust through rigorous security measures.
- Wyze has invested in expanding its security team, re-architecting its security stack, implementing two-factor authentication, bug bounty program, and monitoring tools.
- VerifiedView, available via firmware update, aims to prevent unauthorized access by linking user ID to camera footage, ensuring data security.
- Wyze's approach with VerifiedView resembles DRM, ensuring user identity is bound to digital content for additional security.
- While offering strong protections, VerifiedView cannot prevent account holders from accessing footage; Wyze strengthens login security with two-factor authentication.
- Wyze assures users that VerifiedView will remain a free feature, committed to maintaining this security measure for all Wyze Cams.
- Wyze explains the trade-off between end-to-end encryption (E2EE) and VerifiedView, focusing on preserving user experience and functionality like AI features.
- The company plans to enhance local processing for security cameras, moving towards edge computing, alongside cloud collaboration for enhanced functionality.
- Despite the reliance on cloud services, Wyze aims to continually improve security measures, offering users confidence in the protection of their footage.
Read Full Article
4 Likes
Tech Radar
189

Image Credit: Tech Radar
AWS just hit a major cloud security milestone - and it could be a win-win for businesses everywhere
- AWS has achieved 100% MFA enforcement for root users across all account types.
- This milestone is part of AWS' voluntary commitments to the CISA Secure By Design initiative.
- Multi-factor authentication helps enhance security by providing a phishing-resistant verification method.
- AWS made the announcement at its re:Inforce conference, showcasing its ongoing dedication to security.
- New features announced include improvements in Identity and Access Management with Access Analyzer.
- AWS Security Hub now provides notifications ranked by significance to aid security teams.
- GuardDuty Extended Threat Detection now supports container-based applications on Amazon Elastic Kubernetes Service.
- AWS Shield introduces a network security director to identify network misconfigurations that may be exploited in attacks.
- These advances reinforce AWS's commitment to enhancing cloud security across organizations.
Read Full Article
11 Likes
TechJuice
123

Image Credit: TechJuice
New Winos 4.0 Malware Hits Windows via Fake Installers
- A sophisticated campaign using Winos 4.0 malware targets Windows users in Chinese-speaking environments through fake installers.
- The attack starts with phishing emails posing as official notifications, leading users to download malicious software installers.
- The malware employs a multi-stage loader called Catena to silently introduce Winos 4.0 into memory.
- Security experts note the campaign initiated in early 2025, with Winos 4.0 establishing persistence, exploiting privileges, and communicating with command-and-control servers.
- Winos 4.0's delivery mechanism involves disabling Windows Defender, using reflective DLL injection for stealthy execution, and maintaining persistence through various methods.
- The malware, also known as ValleyRAT, offers remote control features like shell access, keylogging, data exfiltration, and cryptocurrency theft.
- It connects to attacker-controlled servers for encrypted communication, indicating a strategic shift towards long-term espionage by the Void Arachne group.
- Security advice includes installing software from trusted sources, updating systems regularly, using advanced threat detection tools, and educating users about phishing emails.
Read Full Article
7 Likes
Medium
431

Image Credit: Medium
How Do HTTP Headers Make or Break Security
- HTTP headers play a crucial role in web security by controlling access and cache settings.
- Developers often overlook HTTP headers, leaving vulnerabilities that hackers can exploit.
- This article delves into how hackers use HTTP headers to steal data with real examples.
- It also highlights the importance of configuring the 5 most critical security headers.
- Misconfigurations in Fortune 500 companies are discussed, revealing potential security risks.
- A comprehensive checklist is provided to strengthen website security.
- HTTP headers govern communication between browsers and servers during HTTP requests and responses.
Read Full Article
25 Likes
Tech Radar
422

Image Credit: Tech Radar
One of the world's most popular CMS tools has an embarrassing security flaw, so patch immediately
- The Sitecore Experience Platform, a popular CMS, had vulnerabilities that allowed threat actors to take over vulnerable servers.
- One of the vulnerabilities was a hardcoded password for an internal user, making it easy to guess.
- Malicious users could authenticate via an alternate login path to gain access to internal endpoints.
- A 'Zip Slip' flaw in Sitecore Upload Wizard allowed authenticated attackers to upload malicious files.
- Attackers could write arbitrary files in the webroot due to insufficient path sanitation.
- With the Sitecore PowerShell Extensions module installed, attackers could achieve a 'reliable RCE'.
- Around 22,000 publicly exposed Sitecore instances are vulnerable, from versions 10.1 to 10.4.
- It is advised to patch immediately as attackers could potentially exploit these vulnerabilities.
- No reports of abuse have been seen in the wild, but users are recommended to update as soon as possible.
Read Full Article
25 Likes
For uninterrupted reading, download the app