Cyber Security News
TechBullion
413

Image Credit: TechBullion
Why Corporate Executives Are Choosing Armored Sedans Over Traditional Security Details
- Corporate executives are choosing armored sedans over traditional security details as personal security becomes a strategic necessity.
- Armored sedans combine enhanced protection with secrecy, moving away from noticeable security teams for a low-profile solution.
- They offer ballistic and explosive protection meeting high standards like CEN 1063 BR6 or BR7, essential for volatile environments.
- Armored sedans maintain a discrete profile, resembling luxury non-armored vehicles like Mercedes-Benz S-Class or BMW 7 Series.
- Enhancements include custom suspension, high-performance braking systems, and re-engineered drivetrains for threat scenarios.
- Armored sedans feature autonomous threat response, high mobility for fast exits, and evasive maneuvers, providing strategic advantages.
- Customizable protection features such as escape hatches and route-based analysis cater to varying security needs.
- Integration of intuitive controls, surveillance features, and low cognitive load systems for executive ease of use.
- While the initial cost is high, armored sedans offer cost-efficiency over time compared to traditional security convoy expenses.
- Armored sedans serve as a self-contained security solution, saving time, money, and reducing operational vulnerabilities for corporate leaders.
Read Full Article
24 Likes
Pymnts
364

Image Credit: Pymnts
Abacus Group Acquires Entara to Bolster Cybersecurity Offering
- Abacus Group has acquired Entara, a Chicago-based managed services provider specializing in financial services sector.
- The acquisition aims to enhance Abacus Group's cybersecurity, professional services, and digital infrastructure offerings.
- Abacus Group plans to extend Entara's incident response capabilities to its clients and bring AI-driven ServiceNow platform for improved service experience.
- The merger enables global expansion of managed IT and cybersecurity services through the abacusFlex platform.
- This combination benefits clients of all sizes, offering premium and compliant services to financial managers and multinational organizations.
- Entara's founder mentioned the merger creates a unique provider in the cybersecurity landscape by scaling service levels without losing personal attention.
- Cybersecurity company Cerby emphasized the importance of secure digital identities in the era of AI.
- Cerby focuses on securing nonstandard applications that are often neglected by traditional identity platforms.
- These applications, not easily integrated with modern identity standards, can be vulnerable to exploitation by bad actors.
- Cerby engages with security teams and line-of-business owners to address unique security dynamics.
- The news was originally reported by PYMNTS.com.
- The acquisition of Entara by Abacus Group is set to bolster Abacus Group's cybersecurity offerings.
- The merger will provide enhanced incident response capabilities and AI-driven services to clients.
- The collaboration aims to deliver premium and regulatory-compliant services to financial managers and multinational organizations.
- The merger aims to scale services from high-touch boutique levels to enterprise-grade global operations.
- Entara's specialized incident response capabilities will strengthen Abacus Group's cybersecurity defenses.
- The news highlights the growing importance of cybersecurity in the financial services sector.
Read Full Article
21 Likes
Hackernoon
294

Image Credit: Hackernoon
Halo Security Honored With 2025 MSP Today Product Of The Year Award
- Halo Security has won the 2025 MSP Today Product of the Year Award for its attack surface management solution.
- The award recognizes products reshaping the managed services landscape, meeting evolving end-user needs.
- Halo Security's platform enables organizations and MSPs to discover, monitor, and secure internet-facing assets.
- It combines attacker-like discovery, security monitoring, vulnerability scanning, and penetration testing services.
- The platform offers easy client management, integrations with tools like Slack, Jira, and cloud providers.
- MSPs can deliver scalable security services with features like PCI compliance reporting, dark web monitoring, and DAST.
- Lisa Dowling, CEO of Halo Security, highlighted their mission to provide visibility into digital presence.
- Rich Tehrani, CEO of TMC, praised Halo Security's commitment to the Channel and product innovation.
- Winners will be featured on MSP Today and TMCnet's media platforms.
- Halo Security offers external attack surface management with asset discovery, risk assessment, and penetration testing.
- MSP Today is a key resource for managed service providers globally, delivering news and product insights.
- TMC has been honoring technology companies for over 20 years, providing valuable insights for global buyers.
Read Full Article
17 Likes
Wired
79

Image Credit: Wired
Iran’s Internet Blackout Adds New Dangers for Civilians Amid Israeli Bombings
- Iran has a history of controlling and shutting down internet access for its citizens, impacting information flow and the economy.
- During the conflict with Israel and recent bombings, Iran has imposed internet restrictions, limiting communication and access to information.
- The internet connectivity in Iran dropped significantly following the conflict escalation, affecting various service providers.
- Iranian authorities have restricted international internet access to prevent potential cyberattacks and maintain control over information.
- Reports indicate severe disruptions in mobile data services and VPNs, making communication and information dissemination challenging.
- Internet shutdowns are a common tactic in repressive regimes to curb protests, restrict communication, and control information flow.
- Countries like Iran develop intranet systems to censor content, promote domestic apps, and exert control over the internet.
- Despite claims of cybersecurity protection, internet shutdowns primarily aim to control and limit information to maintain power.
- Experts suggest that internet shutdowns are ineffective against state-level cyberattacks and mainly restrict access to information for society.
- The ultimate goal of internet restrictions in Iran is speculated to be about controlling the population and narrative, rather than cybersecurity.
Read Full Article
4 Likes
Mcafee
74
Image Credit: Mcafee
Navigating cybersecurity challenges in the early days of Agentic AI
- Agentic AI involves AI systems working together unsupervised, like finding events to attend.
- Requires building blocks like Large Language Models and invoking tools for tasks.
- Potential to augment human productivity but poses cybersecurity challenges.
- Security implications around Agentic AI include threats of scams and exploitation.
- Cybercriminals can leverage Agentic AI for phishing, social media manipulation, and scams.
- Possible vulnerabilities include injection points and errors in AI behavior.
- Need for caution in adopting and using Agentic AI to prevent exploitation and cyber attacks.
- Urges vigilance, caution, and robust cybersecurity measures in the era of Agentic AI.
- Agentic AI offers opportunities for improvement but requires safeguards against misuse.
- Important to be aware of potential threats and take proactive cybersecurity measures.
Read Full Article
4 Likes
Socprime
211

Image Credit: Socprime
AI Threat Intelligence
- Generative AI (GenAI) is reshaping the threat intelligence domain, enabling real-time analysis and more scalable defenses.
- AI in Threat Intelligence is crucial for transforming data interpretation and acting on threats strategically, operationally, and tactically.
- AI automates long-term planning, situational awareness, and response to immediate threats in organizations.
- It plays a key role in every phase of the Threat Intelligence Lifecycle, from collection to planning and feedback.
- AI-based threat protection utilizes ML, NLP, and behavioral analytics for real-time threat detection and response.
- Use cases for AI in Threat Intelligence include aggregating data, NLP, pattern recognition, IOC discovery, and more.
- Advantages of AI in Threat Intelligence include accelerated processing, continuous monitoring, predictive insights, and scalability.
- Challenges include adversarial manipulation, human-AI synergy, bias, and compliance complexity.
- The future of AI in threat intelligence involves predictive modeling, autonomous hunting, and self-optimizing defenses.
- AI-native threat intelligence shifts to autonomous AI-driven threat detection and response for more adaptive and proactive defense.
- SOC Prime's AI SOC Ecosystem combines AI speed with human expertise to enhance threat intelligence programs.
Read Full Article
12 Likes
TechJuice
422
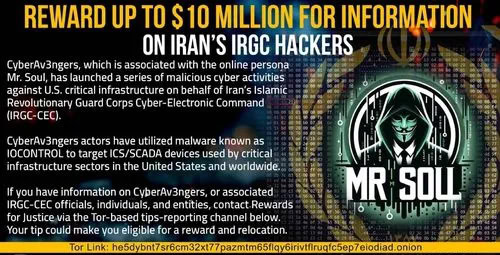
Image Credit: TechJuice
US Fights Iranian Cyberattacks: $10M for IOControl Hacker Info
- The U.S. State Department offers a $10 million reward for identifying Iranian hackers behind IOControl malware targeting critical infrastructure like industrial control systems globally.
- The reward is part of the Rewards for Justice (RFJ) program and focuses on CyberAv3ngers, a hacking group tied to Iran’s Islamic Revolutionary Guard Corps Cyber-Electronic Command.
- The reward notice targets an online persona known as "Mr. Soul" associated with CyberAv3ngers.
- IOControl (OrpaCrab) malware is designed to target Industrial Control Systems (ICS) and SCADA devices crucial for managing sectors like water, energy, and manufacturing.
- IOControl enables remote control of infected devices and movement within victim systems, compromising industrial technologies from various vendors.
- IOControl has been linked to attacks on water treatment facilities in the U.S. and Israel, as well as fuel management systems, causing disruptions.
- The malware leverages the MQTT protocol for secure command-and-control communications and supports commands for executing code and port scans.
- The reward aligns with escalating military and cyber tensions between Israel and Iran, with U.S. officials anticipating intensified Iranian cyberattacks on critical infrastructure.
- Amidst concerns about potential disruptions and the sanctioning of individuals linked to the IRGC-CEC, the U.S. pursues identifying hackers behind IOControl.
- Attacks using IOControl, while not highly sophisticated, have been disruptive, with instances of cutting off water supplies to project power and induce fear.
- The initiative indicates a focus on combating cyber threats and ensuring the security of critical infrastructure amid increasing tensions in the cyber realm.
- The U.S. State Department's move aims to enhance cybersecurity efforts and deter malicious cyber activities targeting vital systems.
- The Malware IOControl's use in targeting industrial systems underscores the need for heightened vigilance and proactive measures to safeguard critical infrastructure.
- Given the significance of the issue, the U.S. government takes proactive steps to identify and counteract cyber threats, contributing to global cybersecurity efforts.
- The $10 million reward reflects the seriousness with which the U.S. views cyber threats and the importance of deterring malicious actors from targeting critical infrastructure.
- The announcement of the reward demonstrates the U.S. government's commitment to cybersecurity and the protection of essential services from cyberattacks.
Read Full Article
25 Likes
The Verge
217

Image Credit: The Verge
Facebook rolls out passkey support to fight phishing attacks
- Facebook is introducing passkey support on its mobile app for enhanced security against phishing attacks.
- Passkeys allow users to log in using fingerprint, face scan, or PIN, making it harder for unauthorized access.
- Passkeys are more secure than traditional passwords as they can't be stolen or leaked, providing protection against phishing scams.
- Browser integration with passkeys ensures they only work on genuine domains and not on fake login pages.
- Meta, Facebook's parent company, plans to launch passkey support on Android and iOS soon, extending to the Messenger app as well.
- Various big tech companies like Google, Microsoft, Apple, and WhatsApp already use passkeys for secure sign-ins.
- Users can still utilize passwords, physical security keys, or two-factor authentication in addition to passkeys for logging in.
- In addition to account logins, passkeys can be used for autofilling payment information on Meta Pay.
Read Full Article
12 Likes
Tech Radar
21

Image Credit: Tech Radar
Top email hosting provider Cock.li hacked - over a million user records stolen
- Email hosting provider Cock.li, known for its popularity among hackers, has been hacked, compromising sensitive data of over a million users.
- A threat actor is selling two Cock.li databases on the dark web, containing email addresses, login details, contact information, and user preferences.
- Cock.li confirmed the authenticity of the leaked data and urged users to change their passwords.
- The hacker exploited a vulnerability in Cock.li's Roundcube webmail platform, affecting users who logged in since 2016.
- Sensitive information of approximately 1,023,800 users and 10,400 contact entries were compromised in the breach.
- The stolen data includes email addresses, login timestamps, preferences, names, emails, vcards, and comments.
- Passwords, emails, IP addresses, and data of non-webmail users were reportedly not compromised in the breach.
- Cock.li, a German email provider focusing on privacy, decided to abandon Roundcube due to an exploited remote code execution flaw.
- After the breach, Cock.li experienced disruptions and the databases were put up for sale on the dark web for one bitcoin.
- Cock.li admin team advised users to update their passwords as a precautionary measure.
Read Full Article
1 Like
TechCrunch
365

Image Credit: TechCrunch
Internet collapses across Iran, say web monitoring firms
- Internet connectivity in Iran almost completely disappeared on Wednesday, with web monitoring firms reporting a near-total national internet blackout amidst the ongoing war with Israel.
- NetBlocks confirmed the blackout in Iran, with IODA also detecting a sudden collapse of internet connectivity in the country.
- Data from Cloudflare indicated a drastic drop in internet traffic levels in Iran, which were significantly lower compared to the previous week.
- The internet blackout coincides with heightened military conflict between Iran and Israel, with Iran facing cyberattacks on major institutions.
- Iranian news outlet IRIB mentioned Israel's involvement in a 'massive cyber war,' prompting Iranian officials to restrict internet access.
- The reason behind Iran's internet collapse remains unclear, with experts noting the lack of visible network activity despite the significant traffic decrease.
- David Belson from Cloudflare highlighted the absence of announced IP address space as an unusual aspect of this outage.
- Doug Madory from Kentik also observed the severity of the blackout, with many Iranian service providers offline for the second day in a row.
Read Full Article
21 Likes
Amazon
30

Image Credit: Amazon
Accelerate threat modeling with generative AI
- Generative AI is transforming threat modeling by automating vulnerability identification, generating attack scenarios, and providing mitigation strategies.
- Traditional automation tools struggled with threat analysis creativity and context, but generative AI understands complex relationships and novel attack vectors.
- Threat modeling involves identifying, quantifying, and addressing security risks, analyzing architecture, and implementing mitigations.
- Effective threat modeling in the design phase reduces security debt, enabling innovation and resilient system development.
- Generative AI automates complex analytical tasks, leveraging security frameworks to identify vulnerabilities across systems.
- Threat Designer uses enterprise-grade foundation models like Amazon Bedrock and Anthropic's capabilities for comprehensive threat assessments.
- Key features of Threat Designer include architecture diagram analysis, an interactive threat catalog, iterative refinement, and standardized exports.
- The serverless architecture of Threat Designer incorporates AWS managed services for scalability, availability, and cost-efficiency.
- The agent service workflow in Threat Designer follows a directed graph structure for processing system diagrams and identifying vulnerabilities.
- Generative AI in threat modeling democratizes security analysis for development teams, making shift-left security practical and accessible.
Read Full Article
1 Like
Tech Radar
395

Image Credit: Tech Radar
These popular TP-Link routers could be facing some serious security threats - find out if you're affected
- CISA has flagged a security issue affecting multiple TP-Link routers, with a command injection vulnerability allowing threat actors to execute system-level commands.
- The affected routers have reached end-of-life status, dating back between 2010 and 2018, and are no longer receiving updates from TP-Link.
- The vulnerability, tracked as CVE-2023-33538, impacts models like TP-Link TL-WR940N, TL-WR841N, and TL-WR740N.
- There is no patch available to address the vulnerability, prompting users to replace outdated hardware with newer versions by the deadline of July 7, 2025.
- Popular older models with thousands of positive reviews on Amazon are advised to be discontinued for usage.
- Proof-of-concept exploits for these vulnerabilities are easily accessible online, posing a significant risk particularly for publicly exposed routers with remote access capabilities.
Read Full Article
23 Likes
Medium
259

Image Credit: Medium
Calling The Video Game Industry — Toxic Waste Clean-Up on Aisle Everywhere
- Ubisoft and Riot Games are partnering to use an AI moderation tool to tackle toxicity in online video games.
- The Zero Harm in Comms initiative will employ natural language processing to understand message context.
- Riot Games introduces cabined accounts to offer a more secure gaming experience for kids.
- Cabined accounts will disable certain features until parents explicitly enable them.
- League of Legends, Fortnite, Rocket League, and Fall Guys are implementing Cabined Accounts.
- It is important for parents to ensure their child provides accurate age information during game registration.
- Efforts to combat toxic behavior in online gaming are focusing on creating safer and more inclusive environments.
- Riot Games is known for League of Legends, a leading competitive game globally.
- AI technologies are seen as vital tools in addressing harassment and bullying in video games.
- The industry is urged to cooperate in developing systems for healthy interactions in gaming.
- Attempts to clean up toxic behavior are expanding beyond filtering out specific problematic words.
- Artificial intelligence is expected to enhance the detection of harmful messages in gaming platforms.
- The initiative aims to offer users a more pleasant and welcoming gaming atmosphere.
- Riot Games emphasizes the importance of keeping young gamers safe and engaged.
- Cabined accounts are part of efforts to provide a secure and tailored gaming environment for children.
- Various popular games are implementing features like Cabined Accounts to enhance safety for young players.
Read Full Article
15 Likes
Medium
149

Image Credit: Medium
How Kids FEEL About Their Online Worlds Is More Important Than What They Do Online
- It's essential to consider how kids feel about their online activities rather than just focusing on what they do online, as their personalities shape their technology interests.
- Online interactions, whether in gaming or social media platforms, can potentially have negative impacts on children, emphasizing the importance of understanding their responses to online activities.
- Parents are advised to quietly observe how their children engage with technology to determine if it affects their self-esteem and have meaningful conversations with them about their online experiences.
- Engaging in discussions with children and their peers about online activities can provide insights into potential issues and create a supportive environment for open communication.
- Encouraging children to be accountable for their online behavior and fostering an inner voice can guide them in making responsible decisions both now and in the future.
Read Full Article
8 Likes
Docker
277

Image Credit: Docker
Docker State of App Dev: Security
- Security in software development is now seen as a collaborative effort rather than a specialized function, according to Docker's 2025 State of Application Development Report.
- Roles in organizations are blending, and security is a concern across all functions, with just 1 in 5 organizations outsourcing security.
- In larger organizations, security is more likely to be handled exclusively by security engineers.
- Team leads and developers of various experience levels are now focusing on security, illustrating its integration into every aspect of development.
- During security incidents, all team members collaborate to address vulnerabilities, with fixing vulnerabilities being a time-consuming task.
- Security isn't the main bottleneck in development processes, with planning and execution taking precedence.
- The concept of 'shift security left' is becoming less prominent in comparison to trends like AI and infrastructure as code, but it still holds influence.
- Ultimately, security is no longer a barrier but an inherent part of development, emphasizing the importance of continuous improvement.
Read Full Article
16 Likes
For uninterrupted reading, download the app