Cyber Security News
TechBullion
223

Image Credit: TechBullion
The Rise Of Automated Security Systems In Smart Homes: 2025 Trends To Watch
- Smart home technology has revolutionized the way we live in recent years, with automated security systems becoming essential features in modern homes.
- The global smart home security market is projected to surpass $90 billion by 2028 with AI, machine learning, and IoT driving growth in automated security.
- Key automated security trends for 2025 include AI-powered surveillance systems, integrated access control systems, remote monitoring features, and sensors for various threats.
- AI-powered surveillance systems reduce false alarms and enable homeowners to respond quickly to threats, enhancing security.
- Integrated access control systems like smart locks and automated gates improve entry and exit management without compromising security.
- Modern automated surveillance systems offer features like remote monitoring, alerts, and shut-off protocols to prevent damages and enhance household safety.
- The market for affordable, scalable, and user-friendly security systems is growing, making advanced smart home security more accessible.
- Factors fueling the rise of automated security systems in 2025 include advancements in technology, increasing safety concerns, and integration with smart home ecosystems.
- Automated security systems are becoming core components in smart homes, offering proactive, personalized, and integrated solutions for enhanced home protection.
- Homeowners are encouraged to invest in automated security systems to stay ahead of trends and ensure a safer living environment.
Read Full Article
13 Likes
Analyticsindiamag
2.2k

Image Credit: Analyticsindiamag
Google Opens Cybersecurity Hub in Hyderabad to Strengthen India’s Digital Safety Infra
- Google has inaugurated its first Google Safety Engineering Centre (GSEC) in Hyderabad to enhance India’s digital safety infrastructure, marking it as the fourth such centre globally.
- The Centre was launched by Telangana CM Revanth Reddy, along with state IT minister D Sridhar Babu and other government officials.
- This launch aligns with Google’s ‘Safety Charter’ for India’s AI-led transformation, focusing on online fraud protection, cybersecurity for enterprises and government, and responsible AI solutions.
- The GSEC will work on initiatives such as real-time scam alerts, fraud detection improvements across services like Pay and Search, and enhancing defenses like Google Play Protect.
- The center will also address AI misuse through initiatives like adversarial testing and red teaming.
- Telangana CM Reddy described the centre as beneficial for job creation, skill development, and enhancing India’s cyber defense.
- India's expanding digital presence has increased vulnerability, highlighting the importance of cybersecurity measures.
- Google Pay alone prevented ₹13,000 crore worth of financial fraud in 2023.
- However, cybercrime losses in India are projected to reach ₹20,000 crore by 2025.
- The Digital Threat Report 2024 highlighted a significant rise in phishing attacks, with the majority of business email compromise cases involving AI-generated deepfakes.
- The CERT-In cybersecurity agency has responded to over 14 lakh incidents in 2022, emphasizing the need for robust cybersecurity measures.
- Google’s VP for public policy, Wilson White, noted that Asia-Pacific is a significant hub for digital scams, accounting for two-thirds of global fraud losses.
- AI technologies can play a vital role in detecting and eliminating fraudulent activities.
- The GSEC in Hyderabad aims to strengthen India’s digital safety infrastructure and contribute to combating digital threats effectively.
- The facility will serve as a regional hub for Asia-Pacific to address cybersecurity challenges.
- The Google Safety Engineering Centre in Hyderabad is a significant step towards bolstering India’s cybersecurity framework.
- The article qualifies for web story generation as it covers recent news related to technology, cybersecurity, and Google's initiatives in India.
Read Full Article
30 Likes
Securityaffairs
434
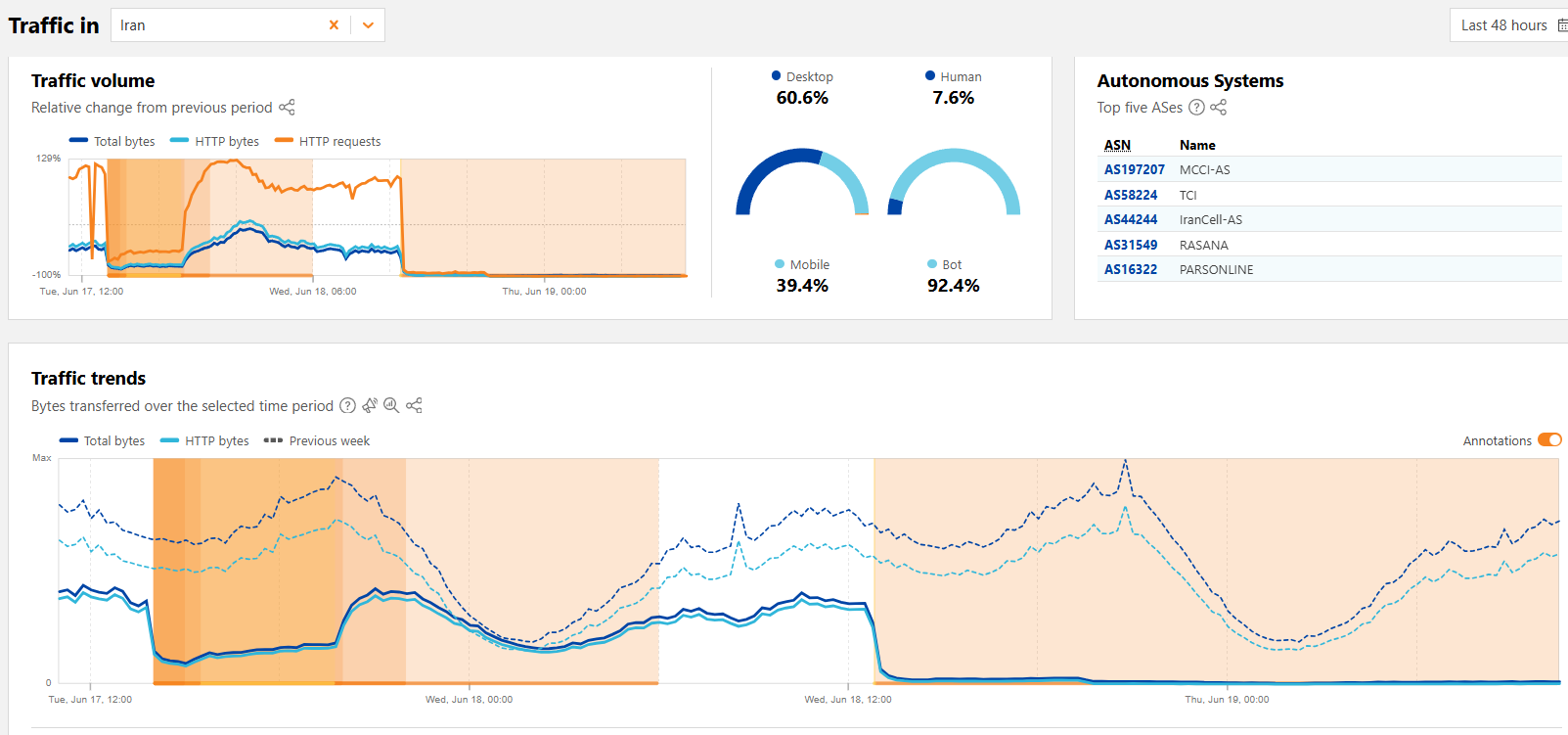
Image Credit: Securityaffairs
Iran experienced a near-total national internet blackout
- Iran experienced a near-total internet blackout amid escalating tensions with Israel.
- Global internet monitor NetBlocks reported near total internet disruptions in Iran, but the exact cause remains unclear.
- The blackout coincides with escalating military conflict and cyberattacks, with no definitive evidence linking it to a specific cause.
- Cloudflare also reported internet traffic disruptions in Iran.
- Cyberattacks targeted Iranian institutions, including the major bank Iran’s Bank Sepah, leading to the blackout.
- The pro-Israel hacking group 'Predatory Sparrow' claimed responsibility for cyberattacks on Iran, including breaching crypto exchange Nobitex.
- Nobitex confirmed the breach and suspended access following the attack by 'Predatory Sparrow.'
- The group also claimed to have destroyed data at Iran’s state-owned Bank Sepah.
- Crypto-tracking firms confirmed that stolen crypto was sent to unusable wallets referencing Iran’s Islamic Revolutionary Guard Corps.
- Iran’s Fars news agency warned of potential banking disruptions following the cyberattacks.
- The situation underscores the ongoing cyber tensions amidst the broader military conflict between Iran and Israel.
Read Full Article
26 Likes
Medium
3.5k

Image Credit: Medium
The Daily Tech Digest: 19 June 2025
- The field of Artificial Intelligence and Machine Learning shows significant advancements in model evaluation, diverse sector applications, and strategic investments.
- OpenAI introduces ChatGPT's image generation on WhatsApp for wider access to generative AI tools within messaging platforms.
- Microsoft's Azure AI Foundry aids retail decisions for personalized recommendations, exemplified by Albert Heijn leveraging AI for consumer assistance.
- OpenAI stops using Scale AI as a data provider, indicating a shift in data sourcing strategies possibly influenced by competitive factors or focus realignment.
- Google experiments with real-time AI voice chats in Search to enhance interactive search experiences through conversational answers.
- MIT devises continual learning for large language models (LLMs), progressing towards AI that continuously enhances itself without frequent retraining.
- BMW Group utilizes NVIDIA Omniverse for Digital Twins in automotive manufacturing, enabling virtual factory optimization and simulation with AI for enhanced processes.
- Neo4j discusses building scalable, privacy-respecting AI memory for compounding insights over time, emphasizing critical innovation areas in AI memory solutions.
- The article discusses cybersecurity vulnerabilities, ethical considerations in AI innovation, and global cybersecurity threats and incidents.
- The corporate landscape adjusts with startups making strategic moves, tech sector changes, and cybersecurity measures implementing to combat emerging threats.
Read Full Article
3 Likes
Socprime
285

Image Credit: Socprime
Mocha Manakin Attack Detection: Hackers Spread a Custom NodeJS Backdoor Dubbed NodeInitRAT Using the Paste-and-Run Technique
- Mocha Manakin uses the paste-and-run technique with a custom NodeJS backdoor named NodeInitRAT, linked to Interlock ransomware activities.
- Security experts monitor malicious PowerShell usage by attackers for backdoors and offensive actions within organization infrastructures.
- The paste-and-run method by Mocha Manakin deceives users to run scripts, potentially leading to ransomware attacks.
- Register for SOC Prime Platform for Sigma rules tailored for Mocha Manakin detection and proactive cyber defense strategies.
- Mocha Manakin's deployment of NodeInitRAT via paste-and-run lures exploits user interactions for malicious script execution.
- Mocha Manakin's paste-and-run techniques distribute harmful payloads like LummaC2 and Vidar, a tactic increased since August 2024.
- NodeInitRAT allows persistent access for threat actors, conducting reconnaissance and communicating with attacker servers through Cloudflare tunnels.
- Paste-and-run lures by Mocha Manakin trick users with access repair and fake CAPTCHA prompts, facilitating the execution of malicious commands.
- Mitigations against paste-and-run attacks include disabling Windows hotkeys and terminating suspicious processes like node.exe associated with NodeInitRAT.
- Early detection of Mocha Manakin and NodeInitRAT activities is crucial to prevent ransomware incidents and safeguard infrastructure effectively.
Read Full Article
17 Likes
Tech Radar
272

Image Credit: Tech Radar
Over 16 billion records leaked in "unimaginable" major data breach - here's what we know, and how you can see if you're safe
- Security researchers have found 30 databases with 16 billion records online, likely generated by infostealers.
- The databases range in size from millions to billions of records, including data from Apple, Google, VPN services, GitHub, and more.
- Most of the discovered databases were not reported before, with only one having 184 million records previously noted.
- New massive datasets emerge every few weeks, indicating the prevalence of infostealer malware.
- The briefly exposed databases were quickly secured, but the owners remain unknown.
- Determining the exact number of affected individuals is challenging due to potential data overlap and widespread internet access.
- Unprotected databases are a common cause of data breaches, highlighting the lack of understanding in securing cloud service data.
- Cybercriminals exploit leaked data for phishing, identity theft, wire fraud, and ransomware attacks, capitalizing on sensitive information.
Read Full Article
16 Likes
Neuways
395

Image Credit: Neuways
Penetration Testing: Why Its True Value Begins After the Test
- Penetration testing goes beyond uncovering vulnerabilities; its true value lies in post-test actions.
- Businesses benefit by treating pen testing strategically for long-term resilience and risk reduction.
- It fosters a culture of continuous security, helps in incident response readiness, and reduces the total cost of cyber risk.
- Pen testing strengthens cloud security, evaluates third-party risks, and drives compliance improvements.
- Regular testing aids in improving incident response, reducing operational downtime, and minimizing reputational damage.
- It also identifies trends in security weaknesses, fosters a security-first mentality, and strengthens coordination between teams.
- By detecting vulnerabilities unique to modern infrastructure, pen testing supports secure scaling and reinforces Zero Trust strategies.
- It helps in driving compliance that enhances security posture, builds resilience, and adapts security controls to emerging threats.
- Neuways provides tailored penetration testing services to translate insights into actionable cyber resilience strategies.
- With a proactive approach, businesses can leverage pen testing for ongoing security enhancement and threat adaptation.
Read Full Article
23 Likes
TronWeekly
17

Image Credit: TronWeekly
Nobitex Breach: Iran Limits Crypto Exchange Hours After $100 Million Hack
- Iran's central bank imposed strict operating hours on crypto exchanges following a $90 million hack on Nobitex.
- The attack, linked to a pro-Israel group, indicated political motivations over financial gain.
- Concerns over Nobitex's ties to sanctioned and illicit networks deepen worry about Iran's crypto infrastructure.
- Nobitex, Iran's largest digital asset platform, lost over $90 million in a recent exploit affecting various cryptocurrencies like Bitcoin, Ethereum, Ripple, and Solana.
- The exchange has connections with sanctioned entities and has facilitated transactions involving groups like Hamas and the IRGC.
- Chainalysis revealed that Nobitex interacted with sanctioned platforms like Garantex and Bitpapa, aiding illicit finance.
- The exchange serves as a critical gateway for Iranians evading international sanctions, making it a target for politically motivated cyberattacks.
- In response to the breach, Iran's Central Bank mandated limited trading hours (10 AM to 8 PM) for internal exchanges, aiming to bolster monitoring.
- Nobitex has improved security by moving significant holdings to new wallets and has promised users enhanced protection.
- Increased scrutiny post-hack is isolating the Iranian exchange and crypto market, causing global observers to closely monitor the situation.
- Global partners are restricting services to Iranian wallet vendors, while blockchain startups face investor disinterest and operational challenges.
- Startups in Iran are contemplating relocation or stealth mode operations due to diminished venture capital interest post-hack.
- Geopolitical tensions are limiting access to essential tools like GitHub, API nodes, and stablecoin liquidity for crypto projects in Iran.
- The backlash from the Nobitex exploit could impede innovation and slow down crypto adoption in the country.
- Crypto projects in Iran are facing challenges in product launches and funding opportunities post-Nobitex hack.
- The sector is experiencing increased isolation and monitoring amidst geopolitical sensitivities.
Read Full Article
1 Like
Neuways
81

Image Credit: Neuways
Cyber Attacks Surge: Adidas Joins Growing List of High-Profile Breaches
- Adidas confirms a data breach affecting customers who contacted its help desk, with mainly contact information stolen.
- The breach is part of a concerning trend in the UK and highlights supply chain risks for businesses.
- The breach originated from a third-party customer service provider.
- Marks & Spencer, Co-op, and Harrods have also experienced major cyber attacks with significant financial impacts.
- Recent breaches focus on compromising core business systems and causing operational disruption.
- Adidas breach via a third-party vendor indicates that a business's security is only as strong as its weakest partner.
- Businesses must acknowledge that cyber risks have business-level implications.
- It is crucial to vet and monitor third-party vendors, especially those handling sensitive data.
- Data breaches can be dangerous even without compromising payment data.
- Companies must comply with data protection regulations like GDPR to avoid fines and reputational damage.
- Businesses need to shift to proactive cyber security approaches like penetration testing and incident response planning.
- Cyber resilience should be a boardroom issue, involving all layers of the organization.
- Lessons from Adidas, M&S, and Co-op emphasize the need for comprehensive cyber resilience strategies.
- Enquiring about IT support is recommended for businesses looking to enhance their cyber security measures.
Read Full Article
3 Likes
Securityaffairs
101

Image Credit: Securityaffairs
Malicious Minecraft mods distributed by the Stargazers DaaS target Minecraft gamers
- Malicious Minecraft mods distributed by the Stargazers DaaS target Minecraft gamers.
- Java-based malware distributed through fake cheat tools on GitHub is targeting Minecraft users via the Stargazers Ghost Network.
- The malware, disguised as cheat tools like Oringo and Taunahi, uses a multi-stage infection chain with Java/.NET stealers to extract sensitive data.
- Check Point researchers detected this campaign aimed at Minecraft's vast modding community of over a million active users.
- The malware, identified since March 2025, poses as Java mods on GitHub, exploiting Minecraft players' trust.
- The attack involves a Java-based loader checking for virtual machines and analysis tools, followed by a second-stage Java stealer extracting game and Discord data.
- A third-stage .NET stealer collects browser credentials, crypto wallets, VPN data, and more, sending it to a Discord webhook.
- The Russian-speaking threat actors behind this campaign carefully evade sandbox analysis by camouflaging the malware as Forge plugins.
- The report advises caution when downloading third-party content related to Minecraft to avoid falling victim to such malicious activities.
- The Stargazers Ghost Network actively distributes this malware, exploiting the Minecraft player community to deploy stealers that compromise user data.
- The malware campaign underscores the growing trend of using gaming communities as targets for malware distribution, emphasizing the need for vigilance and cybersecurity awareness.
- Indicators of Compromise provided in the report can help identify potential malicious activities targeting Minecraft users.
- The threat actor involved in this campaign is suspected to be of Russian origin, highlighting the global reach of cyber threats in popular online platforms.
- The disguised malware poses a significant risk to Minecraft players seeking mods, showcasing the importance of verifying sources before downloading any third-party content for the game.
- The campaign's use of Java-based loaders and .NET stealers demonstrates the sophistication of cyber attacks targeting the gaming community.
- Vigilance and caution are paramount in the gaming community to prevent falling victim to malicious activities like the Stargazers DaaS campaign targeting Minecraft gamers.
- The Stargazers DaaS malware distribution campaign targeting Minecraft users serves as a reminder of the persistent threats faced by online gaming communities in the cybersecurity landscape.
Read Full Article
6 Likes
Medium
92

Image Credit: Medium
The Cybersecurity Crisis: How AI is Changing the Game in 2025
- Cybersecurity threats are intensifying rapidly as technology becomes more pervasive in daily life.
- In 2025, AI is significantly reshaping the battle against cyber threats, serving as both a powerful defense tool and weapon for cybercriminals.
- Traditional cybersecurity measures relying on human intervention are inadequate against dynamic threats.
- AI enhances cybersecurity by improving threat detection accuracy and speed through machine learning algorithms.
- AI-driven behavioral analytics monitor user and system behavior to detect potential security breaches.
- AI enables real-time, automated responses to cybersecurity incidents, minimizing damage.
- AI enhances threat intelligence by predicting attack vectors and reinforcing system defenses proactively.
- AI-powered cybersecurity platforms utilize self-learning algorithms to detect and respond to threats in real-time.
- AI helps in comprehensive endpoint protection by identifying and neutralizing threats automatically.
- Challenges with AI-driven cybersecurity include false alarms, upfront investments, maintenance, and privacy concerns.
- Businesses must prepare for the AI-driven cybersecurity landscape technologically and organizationally.
- Important ethical and regulatory considerations arise with AI in cybersecurity.
- AI will aid in developing quantum-resistant encryption and drive complete automation in cybersecurity.
- Emerging standards will emphasize privacy, minimizing bias, and transparent operation in AI-driven cybersecurity.
- AI is crucial for companies to balance technological advancement with ethical responsibility in cybersecurity.
- Organizations must remain vigilant, adaptable, and proactive in securely navigating the AI-powered cybersecurity evolution.
Read Full Article
5 Likes
Fintechnews
140

Image Credit: Fintechnews
Vyntra Launches Following NetGuardians and Intix Merger to Tackle Financial Crime
- Vyntra has officially launched as a new company focused on transaction intelligence, formed through the merger of NetGuardians and Intix.
- It aims to provide financial institutions with real-time transaction insights to enhance trust and transparency.
- Backed by Summa Equity, Vyntra combines AI fraud prevention tools with transaction data analytics.
- The company serves over 130 institutions in more than 60 countries, including banks and fintech firms.
- CEO Joël Winteregg highlights Vyntra's mission of aiding financial institutions in navigating complexity and protecting transactions' integrity.
- The launch responds to the demand for end-to-end transaction visibility to support compliance and reduce risks.
- Vyntra offers services like financial crime prevention, AML compliance, and transaction monitoring to enhance operational resilience.
- The company's Chief Strategy Officer emphasizes Vyntra's commitment to providing operational resilience and superior customer experiences.
- Vyntra's services include real-time tracking, fraud detection, AML monitoring, and community-based intelligence.
- It sets a new standard for addressing financial crime and transaction visibility on a large scale.
Read Full Article
8 Likes
Medium
408

Image Credit: Medium
TAILS Tutorial with a Cyberpunk Twist
- TAILS (The Amnesic Incognito Live System) is a Linux-based live operating system that allows users to operate anonymously from a USB stick with no trace on the host machine.
- The system is designed for privacy, running entirely from RAM and leaving no logs, caches, or footprints.
- Users can access the Tor network for added anonymity and security, making it difficult for entities like ISPs or surveillance systems to track their online activities.
- To use TAILS, download it from tails.net or access it via Tor, ensuring its authenticity through the built-in verification tool to prevent supply-chain attacks.
- Utilize Rufus to burn the TAILS ISO image to a USB stick for booting up the system.
- TAILS provides a secure, encrypted persistent storage option on the USB for saving essential data with a passphrase for access.
- After booting up, users can connect to the Tor network for browsing the internet anonymously using the Tor Browser with no browsing history or traces.
- The system is commonly used by journalists, whistleblowers, activists, and privacy-conscious individuals to maintain their anonymity online.
- Despite its security features, TAILS is not entirely immune and users are advised to remain cautious and informed while using it.
Read Full Article
24 Likes
Medium
342
Image Credit: Medium
Boost Strategy With Smarter GRC
- Q4 audit approaching, GRC dashboard messy, CEO questions growth slowdown.
- Team overwhelmed with unread reports, board sees GRC as cost center.
- Aligning GRC to business strategy crucial for success.
- GRC as a driver of performance, trust, and growth.
- Connect GRC to real business risks for attention and respect.
- Link GRC controls and initiatives to strategic risks.
- Define metrics showing GRC's contribution to strategic goals.
- Reframe GRC as a strategic enabler rather than compliance clean-up.
- Align risk and control review processes with project milestones for transparency.
- Track progress from reactive compliance to proactive strategy.
- Flip the script to turn GRC into a strategic asset.
- GRC drives performance and business value when aligned with strategy.
Read Full Article
20 Likes
Dev
122

Image Credit: Dev
From Trust Anchors to SPIFFE IDs: Understanding Linkerd’s Automated Identity Pipeline
- Linkerd enables mTLS for TCP traffic among meshed pods by utilizing Root Trust Anchor and Identity Intermediate Issuer certificates.
- The Root Trust Anchor acts as the ultimate trust point and signs intermediate CA certificates, ensuring mesh-wide trust without exposing the root key.
- Linkerd's Root Trust Anchor certificate is stored in a ConfigMap, providing the public key for all intermediates and end-entity certificates.
- New Linkerd proxies receive the Root Trust Anchor certificate during injection, helping bootstrap trust and secure communication.
- The proxy initializes by loading the trust-anchor certificate, generating a key pair, creating a CSR with the proxy's identity, and starting the Rust identity client.
- The identity client obtains the ServiceAccount JWT, Root Trust Anchor cert, private key, and CSR to issue a unique Leaf Certificate for the proxy's SPIFFE ID.
- The Identity Intermediate Issuer Certificate, located in the linkerd-identity-issuer secret, validates ServiceAccount tokens and issues certificates with SPIFFE URIs.
- The Identity service constructs x509.Certificate templates based on the CSR, signs certificates, and returns them to the proxy for mTLS.
- The proxy consumes the received certificate for mTLS, automatically renewing it when necessary by generating new CSRs for rotation.
- The flow involves trust anchor setup, certificate generation, proxy identity validation, and automated rotation to maintain secure communication within the Linkerd service mesh.
Read Full Article
7 Likes
For uninterrupted reading, download the app