Devops News
Dev
17

Image Credit: Dev
🧠 Monitor Your Full LAMP Stack with ELK + Metricbeat (No Guesswork, Just Data)
- The article discusses the importance of monitoring a traditional LAMP stack efficiently.
- It emphasizes the need for accurate monitoring using ELK Stack combined with Metricbeat for real-time metrics.
- The tutorial covers monitoring Apache, MySQL, system-level metrics, deploying Metricbeat agents, visualization in Kibana dashboards, and load simulation.
- The setup aims to provide a clear and powerful monitoring solution without the need for expensive tools or complex suites.
Read Full Article
1 Like
Dev
13

Image Credit: Dev
PODS CHEAT SHEET
- Creating pods in Kubernetes can be done imperatively using commands like kubectl run or declaratively using YAML files.
- Using 'kubectl apply -f
' command helps apply changes in YAML files for pods. - Utilizing 'kubectl explain pod' assists in understanding the structure and fields of the YAML file.
- The 'dry-run' option with 'kubectl create' allows generating YAML templates for resources without executing the command.
- Outputting JSON or YAML formats can be achieved using the '-o' flag in commands like 'kubectl run'.
- Editing pod configurations can be done either imperatively using 'kubectl edit pod
' or declaratively by updating the YAML file and then applying it. - Duplicating pod configurations can be useful for making changes without affecting the original pod setup.
- Inspecting pods can be performed by checking logs using 'kubectl logs' or gathering detailed information using 'kubectl describe'.
- Interacting with pods in interactive mode is helpful for debugging or monitoring by using 'kubectl exec -it
-- '. - Deleting pods is possible with the 'kubectl delete pod
' command.
Read Full Article
Like
Dev
187

Image Credit: Dev
Step-by-Step Guide to Installing RabbitMQ on a Virtual Server
- RabbitMQ is an open-source message broker facilitating asynchronous communication in applications, enhancing resilience and scalability.
- Decouples sender and receiver functionalities, suitable for various systems like microservices and event-driven apps.
- Offers robust functionality supporting multiple messaging protocols and flexible deployment options like clustering and high availability.
- Compatible with multiple programming languages, backed by a large open-source community and minimal resource consumption.
- Tutorial guides the installation on a Debian-based virtual server with prerequisites, repository setup, server installation, and management plugin activation.
- Emphasizes creating secure users, configuring permissions, and advanced settings like SSL, clustering, and tailored configurations.
- Access the RabbitMQ Management Dashboard, troubleshoot common issues, and secure RabbitMQ using TLS, firewalls, and monitoring tools.
- RabbitMQ's versatility caters to use cases like job scheduling, microservice communication, IoT, real-time apps, and processing pipelines.
- Guidance provided for securing RabbitMQ within Docker or Kubernetes environments with SSL, access control, and monitoring.
- A comprehensive guide to setting up RabbitMQ confidently, emphasizing security measures, and scalability for various applications.
Read Full Article
11 Likes
Medium
49

Image Credit: Medium
A Self-Guided Performance Assessment for Agile Delivery Teams
- Teams often neglect to address failing builds and tests, lacking curiosity and follow-through into production.
- This article proposes a self-guided performance assessment for agile delivery teams to evaluate how they work together.
- Focusing on team dynamics and collaboration, the assessment aims to complement existing delivery performance metrics like DORA and Flow Metrics.
- The framework encourages teams to assess themselves across key dimensions such as collaboration, planning, code quality, and operational readiness.
- It provides reflection prompts and signs of struggle in various categories to help teams identify areas for improvement.
- Teams are advised to use the tool during retrospectives, make it their own by customizing dimensions, and leverage metrics to enrich discussions.
- The assessment promotes self-awareness, open conversations, and a focus on continuous improvement for high-performing teams.
- Teams can decide their performance level and explore actionable insights to enhance their working dynamics.
- This reflective framework serves as a resource for enhancing team cohesion, fostering trust, and strengthening overall capability.
- By initiating intentional reflection, teams can adapt, improve, and succeed not just in meeting deadlines but in evolving together.
- The focus is on enhancing team performance by considering not just the 'what' but also the 'how' of delivery.
Read Full Article
2 Likes
Discover more
- Programming News
- Software News
- Web Design
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Dev
223

Image Credit: Dev
List of important Docker commands: Docker Series 03
- This blog series covers everything about Docker commands for beginners.
- Key Docker commands include listing active containers with 'docker ps' and all containers with 'docker ps -all'.
- Commands for creating, starting, getting logs, executing additional commands, stopping, and removing containers are explained.
- Other commands covered include listing images, removing images, binding ports, tagging images, and more.
Read Full Article
13 Likes
Dev
13

Image Credit: Dev
Containers vs Virtual Machines: What's the Difference?
- A container is a software unit that packages code and its dependencies to run reliably across different environments.
- Containers are lightweight, share the host OS kernel, and include everything needed to run an application.
- Containers and virtual machines isolate applications, but containers are lighter, more portable, less secure, and easier to manage.
- Containers are smaller and efficient due to not bundling a full OS, unlike VMs, and Docker is a containerization platform.
Read Full Article
Like
Dev
330

Image Credit: Dev
Navigate Linux Like a Pro: Understanding Absolute vs Relative Paths
- Understanding the difference between absolute and relative paths is crucial for effective navigation within a Linux environment.
- Absolute paths start from the root (/) and show the full directory route to a file or folder; relative paths start from the current directory.
- Using absolute paths in scripts ensures reliability, especially in scenarios like automation (e.g., cron jobs).
- Practicing navigation with both absolute and relative paths, combining knowledge with common commands like cd, pwd, ls, and find, can enhance efficiency in working with Linux.
Read Full Article
19 Likes
Dev
317

Image Credit: Dev
Killing Bots at the Gate: Detecting Malicious Crawlers with Nginx
- Bots are a common presence on the internet, some helpful like search engine crawlers and others malicious scraping data, spamming forms, or brute-forcing login pages.
- Nginx can be used to detect and stop malicious bots without needing an expensive SaaS WAF, by analyzing logs for patterns, identifying suspicious behavior, blocking with Nginx configurations, and utilizing tools like Fail2Ban for automatic IP bans.
- Key steps include starting with logs to understand the activity, creating filters to block obvious bot behavior, implementing rate limits for abusive IPs, using tools like Fail2Ban for automated bans, and exploring advanced solutions like CrowdSec, ModSecurity, and OpenResty for smarter bots.
- An unconventional approach involves serving zip bombs to deter bots, where a compressed file expands to a large size when decompressed, causing issues for bots attempting to access it.
Read Full Article
19 Likes
Dev
246

Image Credit: Dev
Understanding Virtual Machines vs. Containers: A Complete Guide
- In the IT world, choosing between virtual machines (VMs) and containers is crucial for application environments.
- VMs emulate full physical computers with hypervisors, enabling multiple OS on a single host.
- VMs provide true isolation, multiple OS support, security, and legacy app compatibility.
- Containers are lightweight, portable software units without full OS, sharing the host kernel.
- Containers start quickly, are highly scalable, and promote consistent microservices applications.
- Containers differ from VMs in OS kernel sharing, fast startup, and infrastructure as code advantages.
- Use VMs for OS-specific software, full isolation, and varied OS testing; use containers for CI/CD, microservices, and cross-platform software sharing.
- Security in VMs is strong with full isolation, while containers require best practices like image signing and network policies.
- Pro tips include using VMs and containers together, immutable infrastructure, limited privileges, and a security-first mindset.
- Common pitfalls include running containers as root, storing data in container filesystems, and ignoring base image updates.
- VMs excel in OS isolation and compatibility, whereas containers prioritize speed and integration with modern DevOps tools.
Read Full Article
14 Likes
Dev
165

Image Credit: Dev
Day 11/ 30 Days of Linux Mastery: Setting Up a Local Repository Using RHEL 9 ISO
- Day 11 of the Linux Mastery series focuses on setting up a local repository using RHEL 9 ISO for systems without internet access.
- Repositories are essential for installing software packages where dnf install command could fail without knowing where to find the package.
- Local repositories can be set up offline using RHEL ISO files, which are packed with default software.
- Core dnf commands include mounting an ISO, creating a mount point, editing .repo files, cleaning cache, and installing packages.
- A real-world scenario involves mounting the RHEL 9 ISO, creating a .repo file, cleaning and verifying repos, and installing Apache locally.
- Steps include mounting the ISO, creating .repo files, clearing cache, verifying the new repo, and installing software packages.
- Setting up a local repository is crucial for Linux system administration in secured environments with no internet access.
- This skill involves managing ISO files, writing .repo files, and working offline, making it a common task in Red Hat systems.
- The article guides on mounting, creating .repo files, and installing packages offline, showcasing a repeatable task for Red Hat systems.
- The process outlined using RHEL ISO enhances the understanding of managing local repositories for software installations.
Read Full Article
9 Likes
Dev
8

Image Credit: Dev
Docker Bind Mounts: Supercharging Your Development Workflow
- Developers using Docker often face issues with live updates due to limitations in how Docker handles file updates within containers.
- Bind mounts in Docker solve the live update problem by mapping a file or directory on the host machine to a path inside the running container.
- Using bind mounts, developers can make real-time changes to the code on their local system and see the updates immediately reflected inside the container.
- Bind mounts offer more control compared to volumes, allowing developers to manage where and what to mount for efficient development workflows.
Read Full Article
Like
Dev
102

Image Credit: Dev
System Performance Monitoring
- System performance monitoring is crucial for ensuring the security and efficiency of systems, highlighting issues before they escalate.
- Key performance metrics to monitor include CPU usage, memory usage, disk I/O and storage, network usage, processes and services, and system logs.
- Tools like Glances, Zabbix, Netdata, Nagios, Prometheus, and Grafana can automate monitoring, but best practices involve setting alerts, establishing baselines, and monitoring trends.
- Monitoring is a proactive approach to prevent issues, enhance performance, and serve as an early warning system, emphasizing the importance of continuous surveillance.
Read Full Article
6 Likes
Dev
336

Image Credit: Dev
AI-Powered Deployment Automation for Agencies: Save Time and Scale Client Projects
- Deployment process consumes significant time for agencies, affecting project scalability and efficiency.
- AI-powered deployment automation is transforming the way agencies handle deployments by saving engineering hours and accelerating client project scaling.
- Challenges faced by agencies include manual cloud setups, complex deployments across multiple environments, client-specific infrastructure needs, and post-deployment bugs.
- AI-powered deployment tools automate server configurations, optimize infrastructure, offer rollback safety nets, and enhance overall deployment efficiency for agencies.
Read Full Article
19 Likes
Dev
138

Image Credit: Dev
Real-World Blue-Green Deployment: 10 Lessons I Wish I Knew Earlier
- Implementing blue-green deployment in real-world systems revealed 10 valuable lessons.
- Ensuring identical environments is challenging even with automation tools like Terraform and Ansible.
- Database schema changes pose a high risk during blue-green deployments, requiring versioned migrations and compatibility shims.
- Issues with DNS propagation, increased costs, monitoring tool adaptability, and the importance of automation and observability were key takeaways.
- Partial rollouts, strong observability, and thorough preparation were highlighted as essential practices for successful blue-green deployments.
Read Full Article
8 Likes
Medium
295
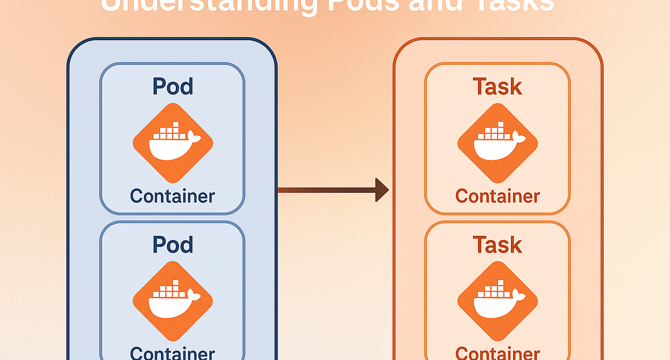
Image Credit: Medium
Understand What Pods and Tasks Are: A Clear Guide for Developers
- A container is a packaged environment including the application and dependencies, isolated from the host system, and created from a Docker image.
- In AWS ECS, a Task represents one or more containers running together; for example, a Task Definition can specify resources for a container like a Spring Boot API.
- In Kubernetes, the equivalent of a Task is a Pod, which is deployed using a Deployment that manages replicas, rolling updates, and health checks within the cluster.
- When deploying Docker images to ECS, they become Tasks that can run on Fargate (serverless) or EC2 instances, with each component performing specific functions under different runtimes.
Read Full Article
17 Likes
For uninterrupted reading, download the app