Info. Security News News
Hackingblogs
261
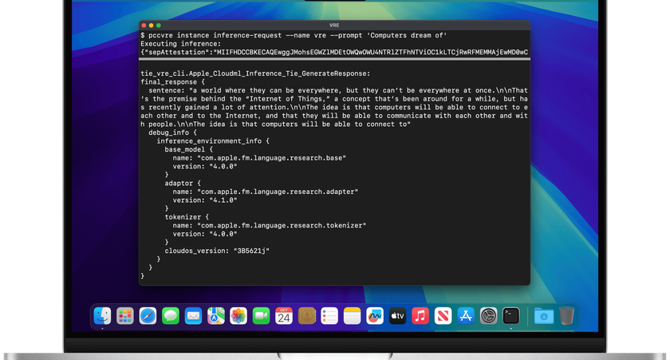
Image Credit: Hackingblogs
Apple Will Pay Up To $ 1 Million To Anyone Who Hacks there Private AI Cloud
- Apple will pay up to $1 million to security experts for identifying flaws in its private AI cloud.
- Researchers can receive up to $250,000 for privately reporting flaws that compromise user data.
- Apple announced the Virtual Research Environment to allow analysis of its private cloud compute.
- Source code for certain components of Private Cloud Compute will be made public.
Read Full Article
15 Likes
Sentinelone
318

Image Credit: Sentinelone
Safely Expanding the Frontiers of AI & LLMs | S Ventures’ Investment in Galileo
- S Ventures, the venture arm of SentinelOne, has announced a strategic investment in Galileo, an evaluation intelligence platform for AI teams.
- Galileo provides a comprehensive solution for developing, testing, monitoring, and securing AI applications, including large language models (LLMs).
- The platform addresses challenges such as ensuring reliability, accuracy, and safety of AI models, and mitigating risks like hallucinations and agent errors.
- Galileo has experienced significant growth, with 834% revenue growth since 2024 and a quadrupling of enterprise customers.
Read Full Article
19 Likes
Global Fintech Series
165

Image Credit: Global Fintech Series
FundingShield Announces Integration with OptiFunder to Deliver Integrated Fraud Prevention Services
- FundingShield has entered into an integration agreement with OptiFunder to deliver integrated fraud prevention services.
- The integration aims to optimize funding processes, prevent fraud, and bring cost savings to mortgage bank and warehouse lending clients.
- FundingShield offers real-time data verification solutions, while OptiFunder provides automation for loan funding and warehouse management.
- The partnership will enhance wire fraud prevention and provide automated risk management solutions to address evolving threats.
Read Full Article
9 Likes
Sentinelone
266

Image Credit: Sentinelone
The Good, the Bad and the Ugly in Cybersecurity – Week 43
- CISA has proposed new security measures to prevent adversary nations from accessing sensitive personal and government-related data across the U.S.
- The Mallox ransomware solution has been released as a free file recovery tool for early victims.
- Trend Micro reported threat actors disguising macOS.NotLockBit ransomware attacks under the LockBit brand.
- So far, ransomware for macOS remains a relatively small threat, but threat actors are ramping up the use of double extortion tactics.
- Security Researchers confirmed the exploitation of a critical-level “FortiJump” vulnerability since June.
- Researchers have attributed the attacks to a threat group tracked as UNC5820.
- Fortinet has notified affected customers and released a patch for CVE-2024-47575.
- For those who cannot patch immediately, the company urges users to use the set fgfm-deny-unknown enable command.
- The investigation to identify the actors’ motivations and location are ongoing as of this writing.
- Fortinet’s advisory lists all additional indicators of compromise (IOCs) as well as recovery methods to assist organizations in mitigating risk.
Read Full Article
16 Likes
Securityintelligence
384

Image Credit: Securityintelligence
Addressing growing concerns about cybersecurity in manufacturing
- Manufacturing is increasingly reliant on modern technology, ICS, IoT devices and OT, expanding the cyberattack surface making them vulnerable to cyberattacks.
- According to a report, the average total cost of a data breach in the industrial sector reached $5.56 million, showing an 18% increase for the sector.
- Ransomware is one of the most prevalent forms of cyberattacks in the manufacturing industry, causing severe financial and reputational damage, supply chain chaos, production delays, and lost revenue.
- Intellectual property theft is another major concern for manufacturers. Cyber criminals often target proprietary designs and trade secrets to gain economic or strategic advantages.
- Third-party suppliers or partners can lead to supply chain attacks, which can have a cascading effect across the entire production line. This interconnectedness makes the industry particularly susceptible to large-scale attacks.
- To mitigate risks, manufacturers should establish strong cybersecurity frameworks that govern all aspects of their operations, conduct regular security audits, implement robust incident response plans, and have a continuous employee training program.
- Regularly updating IoT devices and firmware, segmenting and air-gapping networks, investing in advanced threat detection, and having backup and disaster recovery planning are other measures that manufacturers can implement.
- Security Information and Event Management (SIEM) systems, such as IBM Security QRadar on Cloud technology, deployed as SaaS, can provide real-time visibility into network activity.
- ANDRITZ, a leading industrial plant provider, adopted a comprehensive approach to cybersecurity. In less than six months of deploying Managed Security Services (MSS), they had a new and comprehensive security services solution.
- Manufacturers must adopt proactive cybersecurity measures to protect their systems and data, leveraging new technologies securely, while ensuring they mitigate new risks.
Read Full Article
23 Likes
Socprime
344

Image Credit: Socprime
UAC-0218 Attack Detection: Adversaries Steal Files Using HOMESTEEL Malware
- UAC-0218 group is behind phishing attacks using HOMESTEEL malware for file theft.
- SOC Prime Platform has published Sigma rules for UAC-0218 activity detection.
- The phishing emails contain invoice-related subject lures leading to malicious RAR archives.
- The malware facilitates exfiltration of files to an adversary server via HTTP requests.
Read Full Article
20 Likes
Silicon
78
Image Credit: Silicon
Worldwide IT Spending To Grow 9.3 Percent In 2025, Gartner Predicts
- Gartner has predicted an increase of 9.3% in the worldwide IT spending in 2025 as CIOs begin investing in generative AI (GenAI).
- However, Gartner also warns that the reality of what can be achieved with current GenAI models is not meeting today’s high expectations, as the state of CIOs data Corinne the progress.
- According to the forecast, server sales will increase substantially led by spending on GenAI with data centre spending growing by nearly 35% in 2024, set to reach up to $367bn by 2025.
- GenAI is one of the big drivers of growth, and IT spending should cross the $7tn threshold in 2028.
- GenAI’s impact on IT spending is expected to eclipse those of cloud and outsourcing vendors, with GenAI demand expected to almost triple server sales from 2023 to 2028.
- Gartner predicts that the overall spending on device spending will rise by 9.5% to $805bn, while communication services will increase by 4.4% to $1.6tn in 2025.
- Software spending is also set to increase 14% in 2025, up from 11.7% growth in 2024, while IT services are expected to grow 9.4% in 2025, up from 5.6% in 2024.
- CIOs are becoming more realistic in what GenAI can accomplish, shifting from ‘text to text’ to ‘text to action’ in business use of GenAI, says a VP Strategy at WalkMe.
- Companies providing the tools to assist with AI or bring AI projects to fruition will benefit from the growth in GenAI investment as the demand for GenAI is expected to triple server sales by 2028.
- Gartner highlights that despite the age and consolidation of email providers, IT spending will continue to add $6.6bn to global spending in 2024 and $7.4bn by 2025 due in part to GenAI products and services.
Read Full Article
4 Likes
Securityaffairs
261
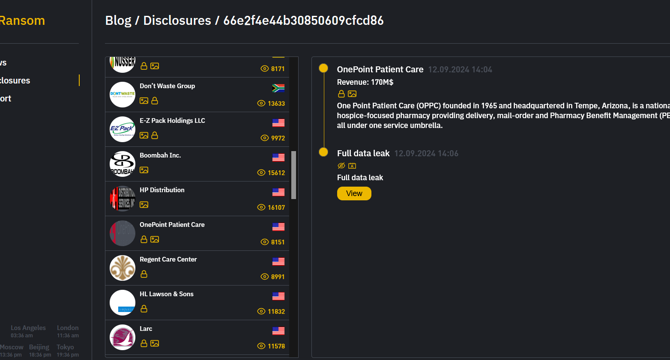
Image Credit: Securityaffairs
OnePoint Patient Care data breach impacted 795916 individuals
- US hospice pharmacy OnePoint Patient Care experienced a data breach that impacted approximately 800,000 individuals.
- The breach resulted in the exposure of personal information, including names, residence info, medical records, and Social Security numbers.
- OnePoint Patient Care detected suspicious network activity on August 8, 2024, prompting an internal investigation and engagement of a forensic security firm.
- The breach was attributed to the INC RANSOM ransomware group, which leaked stolen data after the company refused to pay the ransom.
Read Full Article
15 Likes
Securityaffairs
318

Image Credit: Securityaffairs
From Risk Assessment to Action: Improving Your DLP Response
- Data loss prevention (DLP) is an essential part of a cybersecurity strategy that helps in identifying, evaluating, and mitigating risks related to data loss or unauthorized access. DLP risk assessments work towards detecting and protecting sensitive information including personally identifiable information (PII), intellectual property, and financial data. It helps in identifying potential vulnerabilities, mapping data flows, reviewing security policies, and enhancing DLP strategies, such as updating DLP tools, refining data classification rules. These assessments ensure compliance with several data protection regulatory standards like GDPR, HIPAA, and PCI DSS. The key takeaway is that DLP risk assessments are crucial, but they mean nothing unless implemented properly and conducted regularly.
- Risk assessments for each organization will slightly differ based on organizational needs and differences in IT infrastructures. IT teams and data protection officers should conduct a planned, methodical approach based on eight steps. The first essential step is the identification and classification of data based on its sensitivity and regulatory requirements, followed by the evaluation of existing DLP tools and assessing data flows. Another crucial stage is ensuring your security policies align with regulatory requirements and establish best practices for data protection.
- By simulating attacks like phishing attempts, malware infections, and unauthorized data transfers, organizations can evaluate the effectiveness of their DLP solutions and incident response plans. Regularly conducting assessments, monitoring data flows and security measures are equally crucial. The gist is a DLP risk assessment is only useful when implemented correctly and conducted routinely to ensure continuous protection.
- According to Josh Breaker-Rolfe, DLP is key in cybersecurity due to the continuous refinement required for effective cybersecurity because of cyber criminals' adaptation to evolving and sophisticated tactics. Organizations must conduct DLP risk assessments and identify the types of data that need protection, the threats they face, and the necessary measures to safeguard them.
- These assessments can help safeguard against cyberattacks and inadvertent data exposure, comply with data protection regulations and enhance data protection strategies such as updating DLP tools, refining data classification rules, streamlining communication channels, or implementing employee awareness training programs.
- It is crucial to set up a regular DLP risk assessment timeline, including all stages to ensure comprehensive protection from a variety of cyber threats. Failure to do so could result in legal and financial consequences. In summary, DLP risk assessments are a continuous process that helps you keep pace with changing IT environments and ever-evolving cybercriminal tactics.
- Josh Breaker-Rolfe holds a degree in Journalism and has a background in cybersecurity PR. He is a Content writer at Bora and has written on a wide range of topics, from AI to zero trust and particularly interested in the impact of cybersecurity on the wider economy.
Read Full Article
19 Likes
Securityaffairs
82

Image Credit: Securityaffairs
U.S. CISA adds Cisco ASA and FTD, and RoundCube Webmail bugs to its Known Exploited Vulnerabilities catalog
- U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Cisco ASA and FTD, and RoundCube Webmail bugs to its Known Exploited Vulnerabilities catalog.
- CISA added CVE-2024-20481 Cisco ASA and FTD Denial-of-Service Vulnerability and CVE-2024-37383 RoundCube Webmail Cross-Site Scripting (XSS) Vulnerability to the KEV catalog.
- Cisco addressed multiple vulnerabilities in ASA, FMC, and FTD products, including the actively exploited CVE-2024-20481, which causes a denial of service.
- RoundCube Webmail vulnerability CVE-2024-37383 was actively exploited in phishing campaigns aimed at stealing user credentials.
Read Full Article
4 Likes
Cybersecurity-Insiders
771

Image Credit: Cybersecurity-Insiders
WhatsApp offers new contact management for data security
- WhatsApp introduces an update to enhance contact management and data security.
- Users can now share and manage contacts across multiple devices on WhatsApp's web service.
- A new feature allows users to save contacts exclusively within the WhatsApp platform for increased privacy and security.
- WhatsApp plans to implement Identity Proof Linked Storage (IPLS) in November, enabling secure contact restoration.
Read Full Article
14 Likes
Securityaffairs
393

Image Credit: Securityaffairs
Pwn2Own Ireland 2024 Day 2: participants demonstrated an exploit against Samsung Galaxy S24
- On the second day of Pwn2Own Ireland 2024, researchers demonstrated an exploit for the Samsung Galaxy S24.
- Hackers demonstrated attacks against 51 zero-day vulnerabilities, earning a total of $358,625.
- The total payout at the event organized by Trend Micro’s Zero Day Initiative is nearly $850,000.
- Ken Gannon of NCC Group earned $50,000 and 5 Master of Pwn points by chaining five vulnerabilities to hack a Samsung Galaxy S24 device.
Read Full Article
23 Likes
Dataprivacyandsecurityinsider
30

Image Credit: Dataprivacyandsecurityinsider
Microsoft Report Highlights Attacks Against Healthcare Organizations
- Ransomware attacks against healthcare organizations are a significant cybersecurity threat.
- The healthcare sector was among the top 10 most impacted industries in Q2 2024.
- Ransomware attacks against healthcare organizations have surged by 300% since 2015.
- Four case studies highlight the far-reaching effects of ransomware attacks on healthcare organizations.
Read Full Article
1 Like
Dataprivacyandsecurityinsider
432

Image Credit: Dataprivacyandsecurityinsider
Ally Financial Faces Class Actions Over Data Breach
- Ally Financial Inc. faces two class action lawsuits over a data breach in April 2024.
- The suits allege that Ally failed to secure customers' personal information.
- Lead plaintiffs claim fraudulent activity and exposure of personal information on the dark web.
- Ally is accused of negligence in preventing the breach and delaying customer notifications.
Read Full Article
26 Likes
Dataprivacyandsecurityinsider
0

Image Credit: Dataprivacyandsecurityinsider
CT AG Settles Data Breach Case with Guardian Analytics
- Connecticut Attorney General settles data breach case with Guardian Analytics for $500,000.
- Data breach exposed personal information of 157,629 Connecticut residents.
- Guardian Analytics accused of failing to implement reasonable data security measures.
- Settlement requires Guardian Analytics to maintain information security program and implement various security measures.
Read Full Article
Like
For uninterrupted reading, download the app