Info. Security News News
Hackingblogs
207

Image Credit: Hackingblogs
Uncovering The Mystery Behind Verified Issac Newton Google Scholar Profile : Pay For Blue Tick Models
- Sir Isaac Newton is now a verified Google Scholar despite being dead.
- Researchers have discovered Isaac Newton's Google Scholar profile with a verified email address.
- The process of creating a verified Google Scholar profile is relatively easy and only requires email address verification.
- The presence of a 'verified' label on open profiles does not guarantee the validation of the owner's identity.
Read Full Article
12 Likes
Securityaffairs
229

Image Credit: Securityaffairs
F5 fixed a high-severity elevation of privilege vulnerability in BIG-IP
- F5 has fixed a high-severity elevation of privilege vulnerability in BIG-IP.
- The vulnerability (CVE-2024-45844) could allow an authenticated attacker with Manager role privileges or higher to elevate privileges and compromise the BIG-IP system.
- The company released versions 17.1.1.4, 16.1.5, and 15.1.10.5 to address the issue.
- F5 also addressed a medium-severity stored cross-site scripting (XSS) bug (CVE-2024-47139) in BIG-IQ.
Read Full Article
13 Likes
Analyticsindiamag
233

Image Credit: Analyticsindiamag
The Disturbing Case of Jennifer Ann’s Chatbot Where AI Crossed the Line
- A chatbot created using Jennifer Ann’s name and image was in operation 18 years after her tragic death.
- Her father discovered the bot via a Google alert and found it had been already used in at least 69 chats.
- This incident raises questions on the direction we are headed with respect to the ethics and application of AI, privacy and human rights.
- AI developments are used as a means of societal control, mass surveillance and discrimination.
- Web scraping and biometric technologies raise significant privacy concerns.
- AI-powered IoT devices unlock insights into our daily lives and collective human mind.
- There are potential ethical concerns about animating someone who cannot give consent, and recreating a deceased individual’s voice without clear consent.
- The use of AI and algorithms in the Gaza conflict raises ethical concerns about the principles of proportionality and distinction that protect civilians.
- The increasing use of automation and algorithmic decision-making in all spheres of public and private life is threatening to disrupt the very concept of human rights as protective shields against state interference.
Read Full Article
14 Likes
Securityaffairs
331

Image Credit: Securityaffairs
U.S. CISA adds Veeam Backup and Replication flaw to its Known Exploited Vulnerabilities catalog
- The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added the Veeam Backup and Replication flaw CVE-2024-40711 (CVSS score of 9.8) to its Known Exploited Vulnerabilities (KEV) catalog.
- Ransomware operators are exploiting the critical vulnerability CVE-2024-40711 in Veeam Backup & Replication to create rogue accounts and deploy malware.
- Veeam released security updates in September 2024 to address multiple vulnerabilities impacting its products, including the critical remote code execution vulnerability CVE-2024-40711.
- CISA orders federal agencies to fix this vulnerability by November 7, 2024.
Read Full Article
19 Likes
Hackersking
371

Image Credit: Hackersking
Are Cybersecurity Jobs in High Demand?
- The global rise of cyber threats has made cybersecurity an essential field in technology as data, networks, and systems need to be protected from unauthorized access and malicious attacks.
- The demand for cybersecurity jobs is primarily driven by the growing number of cyberattacks, the evolving nature of technology, and the shortage of qualified professionals.
- The U.S. Bureau of Labor Statistics has projected a 35% increase in cybersecurity jobs between 2021 and 2031, much faster than the average of all other occupations.
- The shortage of qualified cybersecurity professionals has led to increased salaries, benefits, and job stability for those who enter the field, making it an attractive career choice for tech enthusiasts.
- The finance and banking, healthcare, and government and defense sectors have a particularly high demand for cybersecurity jobs due to their sensitivity and the need to protect customer information and critical infrastructures.
- Some of the most sought-after cybersecurity jobs include security analyst, penetration tester or ethical hacker, security architect, incident responder, and cybersecurity consultant.
- With cyberattacks becoming more frequent and sophisticated, the need for skilled cybersecurity professionals will remain critical for businesses, governments, and individuals alike.
- The combination of job security, high salaries, and the opportunity to work in a dynamic, evolving field makes cybersecurity an attractive career choice for anyone interested in technology and security.
- This trend is only expected to grow as the digital world expands, making cybersecurity jobs an excellent choice for career seekers who want to work on challenging, meaningful problems.
Read Full Article
22 Likes
Securityaffairs
411

Image Credit: Securityaffairs
Omni Family Health data breach impacts 468,344 individuals
- Omni Family Health disclosed a data breach affecting nearly 470,000 current and former patients and employees.
- The breach was a result of a cyberattack that occurred earlier this year and was discovered on August 7, 2024.
- Personal information such as names, addresses, Social Security numbers, and medical information may have been exposed.
- The organization is offering impacted individuals 12 months of free credit monitoring and identity protection services.
Read Full Article
24 Likes
Securityaffairs
48

Image Credit: Securityaffairs
Iran-linked actors target critical infrastructure organizations
- U.S. and allies warn of attacks from Iran-linked actors targeting critical infrastructure through brute-force attacks in a year-long campaign.
- Intelligence and cybersecurity agencies from the U.S., Australia, and Canada warn about a year-long campaign carried out by Iran-linked threat actors.
- The attackers targeted organizations in healthcare, government, IT, engineering, and energy sectors.
- The attackers used brute-force attacks, password spraying, and multi-factor authentication (MFA) prompt bombing techniques.
Read Full Article
2 Likes
Hackersking
278

Image Credit: Hackersking
Cybersecurity vs Software Engineering in 2024
- Cybersecurity and software engineering stand as two of the most critical fields shaping the tech industry, with cybersecurity having a massive surge in importance due to the increasing number of cyber threats.
- Current trends in cybersecurity include AI-driven attacks, zero-trust security models, quantum threats, and ransomware evolution.
- The demand for cybersecurity professionals continues to skyrocket in 2024, with a global shortage of 3.5 million cybersecurity professionals, making it one of the most lucrative fields in tech.
- While cybersecurity is receiving much attention, software engineering remains an integral part of the technology ecosystem, with innovations and products that make the modern world function.
- Current trends in software engineering include AI integration, low-code/no-code development, cloud computing, and DevSecOps.
- Cybersecurity and software engineering are interdependent fields where cybersecurity professionals protect digital tools and systems while software engineers build them.
- The convergence of these two fields is crucial to drive innovation while maintaining safety in a world where AI and other disruptive technologies continue to reshape industries.
- While cybersecurity is becoming increasingly critical, software engineering remains a solid and essential career choice, especially with the rise of AI and cloud computing.
- For those looking to make a significant impact on the future of digital security, cybersecurity is the field to watch in 2024.
- The demand for cybersecurity experts has never been greater, so professionals should take the leap and explore courses and certifications to position themselves for successful careers in protecting the digital world.
Read Full Article
16 Likes
Sentinelone
310

Image Credit: Sentinelone
The Good, the Bad and the Ugly in Cybersecurity – Week 42
- An unsealed indictment charged two brothers with operating the hacktivist group ‘Anonymous Sudan’, responsible for over 35,000 Distributed Denial of Service (DDoS) attacks globally.
- Latest research notes OilRig deploying a novel backdoor to exploit Microsoft Exchange servers for credential theft. So far, the APT has also been seen leveraging known vulnerabilities to escalate privileges on compromised systems.
- RomCom (aka Storm-0978, UAC-0180, and Void Rabisu) has been active since 2022 and is known for multi-faceted operations that include elements of ransomware, extortion, and credential theft.
- Security researchers highlight the similarities between StealHook and previous OilRig malware, suggesting a gradual evolution of past tools.
- U.S. officials described Anonymous Sudan as one of the most dangerous cyber groups within the DDoS threat ecosystem.
- Rather than rely on compromised devices, Anonymous Sudan leveraged tools like Skynet Botnet and DCAT that used open proxies to overload servers.
- Current concern is that RomCom may potentially add ransomware to their arsenal for future campaigns, affecting the high-value entities that the group so often targets within the energy sector.
- OilRig then installs a password filter DLL to capture plaintext credentials during password changes and uses the remote monitoring tool ‘ngrok’ for stealthy communications.
- This suggests a clear espionage-based motive, as opposed to short-term attacks focused solely on disruption or financial gain.
- RomCom attacks begin with spear phishing emails that deliver downloaders such as MeltingClaw or RustyClaw to deploy the ShadyHammock and DustyHammock backdoors.
Read Full Article
18 Likes
Securityintelligence
35

Image Credit: Securityintelligence
What’s behind the 51% drop in ransomware attacks?
- Ransomware attacks on state and local governments have dropped by 51% in 2024, due to fewer governments paying ransoms, making them less attractive targets to cyber criminals.
- Law enforcement has played a significant role in disrupting major ransomware operators, contributing to the decline in ransomware attacks. These operations did not eliminate the groups entirely but dealt severe blows to their operations by disrupting their infrastructure and identifying key members.
- The decline in ransomware attacks is largely tied to a fundamental change in how governments are responding to these attacks, with a growing awareness about the risks of paying ransoms, coupled with increased support from the Cybersecurity and Infrastructure Security Agency (CISA), leading to a more cautious approach.
- While the number of ransomware attacks has decreased, the cost of recovering from these attacks has skyrocketed, with the average recovery cost for state and local governments in 2024 reaching $2.83 million, more than double the $1.21 million reported in 2023.
- One of the more interesting trends in 2024 has been the rise of unaffiliated ransomware actors, often referred to as “lone wolves.” These attackers operate independently of established ransomware brands like LockBit or BlackCat, making it more challenging to attribute attacks to a specific group.
- Enterprises, critical infrastructure organizations and government agencies must focus on defending against the tactics, techniques and procedures (TTPs) of ransomware attacks, rather than simply tracking the movements of known groups. They should remain vigilant about the possibility of unaffiliated actors targeting their systems.
- The increased involvement of law enforcement and the reluctance of governments to pay ransoms are positive developments, but they do not signal the end of the ransomware threat. Now is the time for organizations to ramp up their cybersecurity efforts.
Read Full Article
2 Likes
Amazon
265

Image Credit: Amazon
Options for AWS customers who use Entrust-issued certificates
- Multiple popular browsers will no longer trust public certificates issued by Entrust later this year. Certificates issued by Entrust after October 31, 2024 will not be trusted.
- If you imported Entrust certificates into AWS Certificate Manager (ACM), you should consider reissuing them before October 31, 2024 and exploring potential alternatives.
- To determine if you’ve imported certificates to ACM, you can use the ACM console and the AWS CLI or APIs.
- If you’ve imported Entrust certificates to ACM, use the Issuer field of the DescribeCertificate response to check if they will be affected by the changes.
- Consider replacing Entrust certificates with public certificates issued through ACM. You can get DV certificates at no additional cost, and ACM automatically renews and redeploys the certificate when it is 60 days from expiration.
- For internal-facing workloads, private certificates are typically better suited, allowing you to control the certificate parameters.
- Re-evaluate your usage of EV and OV certificates, and consider whether they could be replaced with DV certificates.
- If you need more time to evaluate your options before making a decision, consider re-issuing and re-importing your certificates from Entrust before October 31, 2024.
- You can learn more about ACM by reviewing the AWS documentation and get started issuing certificates from ACM in the AWS Management Console.
Read Full Article
15 Likes
Socprime
234

Image Credit: Socprime
MEDUZASTEALER Detection: Hackers Distribute Malware Masquerading the Sender as Reserve+ Technical Support via Telegram Messaging Service
- Hackers are distributing the MEDUZASTEALER malware via Telegram, posing as Reserve+ technical support from the Ministry of Defense of Ukraine.
- The Cyber Emergency Response Team of Ukraine (CERT-UA) has issued an alert regarding spoofed phishing attacks that distribute MEDUZASTEALER.
- The malware is being spread through suspicious messages prompting users to install 'special software' and containing an archive named 'RESERVPLUS.zip'.
- Once executed, the malware exfiltrates files with specific extensions and deletes itself to bypass security software.
Read Full Article
14 Likes
Securityaffairs
420
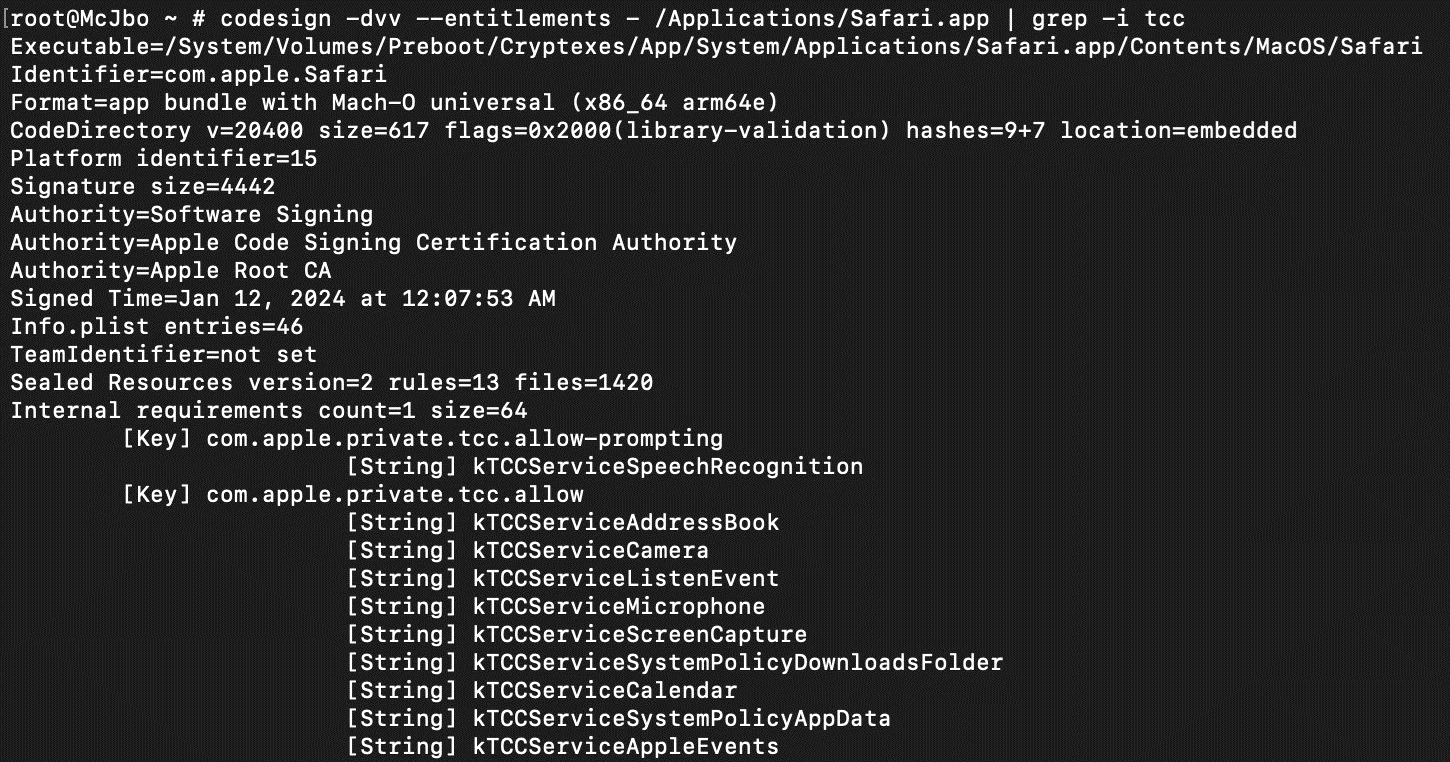
Image Credit: Securityaffairs
macOS HM Surf flaw in TCC allows bypass Safari privacy settings
- Microsoft disclosed a flaw in the macOS Apple’s Transparency, Consent, and Control (TCC) framework that could allow it to bypass privacy settings and access user data.
- The vulnerability, known as 'HM Surf,' removes TCC protection from Safari, allowing access to user data including browsing history, camera, microphone, and location without consent.
- Apple addressed the vulnerability with the release of macOS Sequoia 15.
- Third-party browsers are not affected by this vulnerability.
Read Full Article
25 Likes
Securityaffairs
252
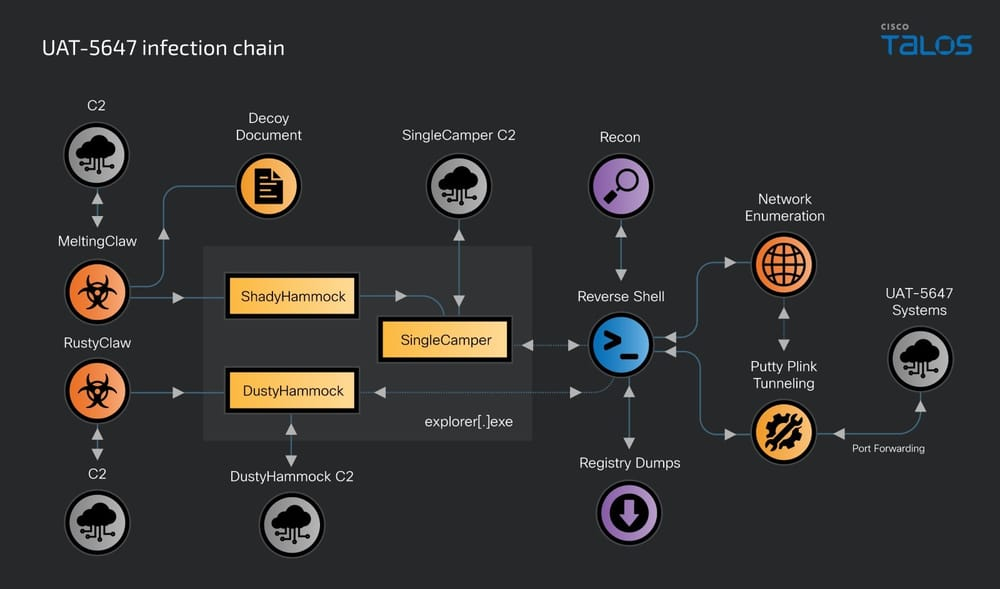
Image Credit: Securityaffairs
Russia-linked RomCom group targeted Ukrainian government agencies since late 2023
- Russia-linked threat actor RomCom targeted Ukrainian government agencies and Polish entities in cyber attacks since late 2023.
- RomCom deployed an updated variant of the RomCom RAT called 'SingleCamper' and used two new downloaders, RustClaw and MeltingClaw, along with two backdoors, DustyHammock and ShadyHammock.
- RomCom is focusing on data exfiltration from Ukrainian targets, using various tools and malware languages for long-term espionage access.
- The group employed spear-phishing messages and established remote tunnels using PuTTY's Plink tool to connect with attacker-controlled servers.
Read Full Article
15 Likes
Kaspersky
159

Image Credit: Kaspersky
Which cybersecurity processes can be automated with AI? | Kaspersky official blog
- Artificial intelligence can automate and accelerate all phases of incident handling such as from detection to response. However, many applications are underperforming when it comes to cybersecurity.
- The two long-tested techniques for AI cybersecurity are: attack detection and anomaly detection. Although they may assist in reducing human workload, neither approach is considered entirely reliable.
- AI can be helpful in filtering FPs, alert prioritization, anomaly detection, and detecting suspicious behavior, but it is not a silver bullet to solve all detection problems, and it cannot work autonomously.
- Large Language Models in cybersecurity LLMs for routine tasks, such as generating detailed cyberthreat descriptions and initial analysis of source code can be helpful.
- Available research on the performance of skilled employees aided by LLMs shows mixed results. Therefore, these solutions should be implemented gradually upon an evaluation of the time investment and the quality of the result.
Read Full Article
9 Likes
For uninterrupted reading, download the app