Info. Security News News
Dataprivacyandsecurityinsider
349

AI Service Provider Faces Class Actions Over Catholic Health Data Breach
- AI service provider Serviceaide Inc. is facing two proposed class action lawsuits over a data breach linked to Catholic Health System Inc. in Buffalo, New York.
- The breach exposed the personal information of over 480,000 individuals, including patients and employees.
- The lawsuits allege that Serviceaide negligently failed to protect sensitive data in its Elasticsearch database, which was publicly accessible for months before disclosure.
- Plaintiffs claim that Serviceaide delayed notifying affected individuals for seven months after the incident, seeking nationwide representation for those impacted and pursuing damages, injunctive relief, and attorneys' fees.
Read Full Article
20 Likes
Dataprivacyandsecurityinsider
60

Privacy Tip #444 – Best Phishing Campaigns are from HR or IT
- Phishing campaigns, including emails, SMS texts, and QR codes, continue to deceive people despite their belief in spotting them.
- A summary by KnowB4 reveals that HR or IT impersonation schemes are the most successful in phishing tests conducted between January and March 2025.
- Employees are highly susceptible to interacting with links related to internal team topics and various file types like PDFs, HTML, and .doc, along with falling for trusted brand impersonations.
- The summary also highlights the risk posed by QR code scams, such as those related to company policies, DocuSign requests, and seemingly innocent messages, urging caution while interacting with them.
Read Full Article
3 Likes
Qualys
306

Image Credit: Qualys
Building Confidence in Cyber Essentials Compliance with Qualys Policy Audit
- Cyberattacks are increasing in frequency, sophistication, and damage, prompting organizations globally to prioritize cybersecurity measures.
- Cyber Essentials is a UK government-backed framework enhancing cybersecurity posture against evolving threats with clear guidance.
- The framework focuses on five technical controls to mitigate common cyber threats and establish a baseline security posture.
- Key domains of Cyber Essentials include firewalls, secure configuration, user access control, malware protection, and security update management.
- The framework addresses fundamental security hygiene issues and emphasizes accountability, measurability, and adaptability in modern IT environments.
- Qualys Policy Audit aids in Cyber Essentials compliance by automating control assessments, highlighting gaps, and providing audit-ready reports.
- The platform offers real-time visibility into compliance posture, aligning systems with Cyber Essentials requirements and regulatory standards.
- Qualys SAQ application supports non-technical aspects by evaluating areas like user awareness, third-party risk, and data handling practices.
- Audit Readiness Report summarizes security posture, compliance alignment, control insights, and recommendations for compliance improvements.
- Qualys Policy Audit and SAQ combined deliver continuous validation of technical and procedural controls, easing compliance efforts.
- By integrating Qualys tools with Cyber Essentials, organizations can maintain scalable compliance, align controls, and mitigate risks effectively.
Read Full Article
18 Likes
Kaspersky
4

Image Credit: Kaspersky
A Kaspersky checklist for a safe vacation | Kaspersky official blog
- The average user spends around 2.5 months of a year on their smartphone, highlighting the significant role of mobile devices in our lives.
- Digital detoxes can improve sleep quality, reduce anxiety, stress, and phone addiction, and enhance the brain's ability to focus and process information deeply.
- While taking a break from screens is beneficial for mental health, it can pose cybersecurity risks such as account theft, unauthorized subscriptions, and personal data leaks.
- To ensure security during a digital detox, strengthen passwords, enable two-factor authentication, make backups, and notify your bank of travel plans.
- Install security updates, protect devices with reliable security software, and safeguard SIM cards from being swapped to minimize cybersecurity risks while on vacation.
- Designate trusted contacts for digital legacy access, secure IoT devices, and establish backup communication channels for personal safety during a digital detox.
- Minimize gadget use on vacation by limiting access to distracting apps, avoiding risky connections, and storing devices securely.
- After returning from a digital detox, check for updates, review notifications and logs for any suspicious activity, and assess the resilience of your digital ecosystem.
- Reflect on the experience and make necessary amendments to improve security measures for future digital detox vacations.
- Following these tips can help ensure a smooth and secure digital-detox vacation, allowing you to enjoy your time offline without compromising your cybersecurity.
Read Full Article
Like
Socprime
103

Image Credit: Socprime
Detect APT28 Attacks: russian GRU Unit 26156 Targets Western Logistics and Technology Companies Coordinating Aid to Ukraine in a Two-Year Hacking Campaign
- A joint Cybersecurity Advisory reveals a two-year cyberespionage campaign by russian GRU Unit 26165 targeting logistics and tech companies coordinating aid to Ukraine.
- The campaign by APT28 (Forest Blizzard, Fancy Bear) aims at intelligence gathering and includes spearphishing and malware deployment strategies.
- Known for targeting Ukraine, APT28 expanded cyber operations to Europe and North America, using persistent tactics to infiltrate critical infrastructure.
- The group deployed various TTPs such as credential guessing, spearphishing emails, and exploiting vulnerabilities like CVE-2023-23397.
- APT28 leverages malware like HEADLACE, MASEPIE, OCEANMAP, and STEELHOOK for data exfiltration and establishing persistence in targeted systems.
- To evade detection, adversaries use encrypted connections, abuse public infrastructure, and exploit vulnerabilities in SOHO devices.
- The attackers conduct reconnaissance, lateral movement, and data exfiltration post initial access, utilizing tools like Impacket, PsExec, and RDP.
- To enhance defense, organizations are advised to implement network segmentation, zero-trust principles, restrict lateral movement, and monitor logs for anomalies.
- Proactive cybersecurity measures, including AI-backed solutions and real-time threat intelligence, are crucial for defending against evolving APT28 attacks.
- The insights from the joint advisory aim to equip security teams with the necessary tools and strategies to combat sophisticated cyber threats effectively.
Read Full Article
6 Likes
Securityaffairs
327
Image Credit: Securityaffairs
New Signal update stops Windows from capturing user chats
- Signal update for Windows app blocks screenshots by default to protect user privacy from Microsoft's Recall feature.
- The new 'Screen security' setting in Signal Desktop prevents Windows from capturing screenshots of Signal chats.
- Microsoft's Recall feature captures screenshots of users' laptops every few seconds, raising privacy concerns.
- Signal's screen security can be disabled but may impact accessibility tools; the setting only applies locally on Windows 11.
Read Full Article
19 Likes
Sentinelone
8

Image Credit: Sentinelone
Caught in the CAPTCHA: How ClickFix is Weaponizing Verification Fatigue to Deliver RATs & Infostealers
- ClickFix attack methodology involves compromising websites and embedding fraudulent CAPTCHA images to deliver malware and malicious code like infostealers and RATs.
- This tactic of using deceptive verification challenges relies on user fatigue with anti-spam verifications, leading victims to inadvertently execute PowerShell code and additional payloads.
- Attackers require victims to solve a CAPTCHA challenge, walk them through running PowerShell code by pasting hidden content, and ultimately infecting themselves.
- Delivery methods of ClickFix attacks include injecting code into legitimate websites, setting up phishing sites, email attachments, social-media lures, and more.
- After clicking the malicious CAPTCHA challenge, victims are instructed to paste commands into the Windows 'Run' dialog, triggering the execution of malware.
- Malicious activities observed in ClickFix campaigns often involve delivering infostealers like Lumma Stealer, NetSupport RAT, and SectopRAT.
- Preventive measures against ClickFix attacks include raising awareness, user training, user restrictions on PowerShell commands, and deploying effective EDR solutions.
- Indicators of Compromise include network communications, fake CAPTCHA domains, PowerShell download domains, and various IP addresses associated with malicious activities.
- Common commands and file names related to ClickFix attacks include PowerShell executions, DLL implants, droppers, RAT components, and scheduled tasks.
- Mitigation strategies for ClickFix attacks involve understanding the tactics employed, monitoring for associated indicators of compromise, and implementing relevant security controls.
Read Full Article
Like
Precisely
69

IBM’s New MFA Offering is a Step in the Right Direction – But Only Part of the Picture
- IBM's introduction of native support for multi-factor authentication (MFA) on IBM i signifies the growing importance of MFA in cybersecurity.
- Although IBM's MFA offering is a positive step, Precisely Assure MFA provides more comprehensive and flexible protection for IBM i environments.
- Modern cyber threats and the prevalence of credential theft emphasize the necessity of robust security measures like MFA.
- MFA enhances security by requiring verification through multiple factors such as passwords, devices, and biometrics, significantly reducing unauthorized access risks.
- Precisely Assure MFA excels in user-friendly authentication, centralized management, integration with IAM platforms, incremental MFA definitions, ransomware protection, flexible control, and support for older OS versions.
- Every organization should prioritize implementing MFA on IBM i systems for enhanced security.
- Consider crucial factors when choosing an MFA solution, including hardware and software compatibility, policy adaptability, and integration with IAM platforms.
- Evaluate your MFA strategy thoughtfully to ensure it aligns with your organization's evolving needs and requirements.
- Enhance your MFA deployment with Precisely Assure MFA to establish a scalable and comprehensive security solution tailored to your business.
- Security is an ongoing journey, and MFA plays a crucial role in strengthening access control defenses for IBM i customers.
Read Full Article
4 Likes
Schneier
405

The Voter Experience
- Campaigns are utilizing technology and innovation to enhance voter outreach and engagement, but overall trust in the electoral process has declined.
- Applying the concept of user experience (UX) to elections, specifically focusing on the voter experience (VX), can provide valuable insights.
- Considering the full impact of the electoral cycle from the voters' perspective is crucial in understanding the effectiveness of voter engagement strategies.
- Questions surrounding how voters perceive their interactions with political campaigns and the enjoyment or dissatisfaction with the electoral process are important to address.
- Measuring the cumulative impacts of political content interactions and longitudinal sentiment from citizens can offer valuable insights for improving democratic participation.
- Implementing UX principles in political tech tools, such as volunteer user flow improvement and data hygiene enhancements, can lead to more effective engagement.
- A focus on VX can help in identifying additional metrics beyond traditional turnout numbers to gauge the collective impact of campaigning efforts.
- By incorporating VX methodology, there is potential to increase civic participation, trust in institutions, and promote higher voter turnout.
- Prioritizing the citizen user experience in democratic processes can lead to the design of systems that strengthen participation, trust, and accountability at every level.
- The approach of focusing on VX aims to restore civic participation, build inclusive democracy, and address shortcomings in current electoral strategies.
Read Full Article
24 Likes
Securityaffairs
409
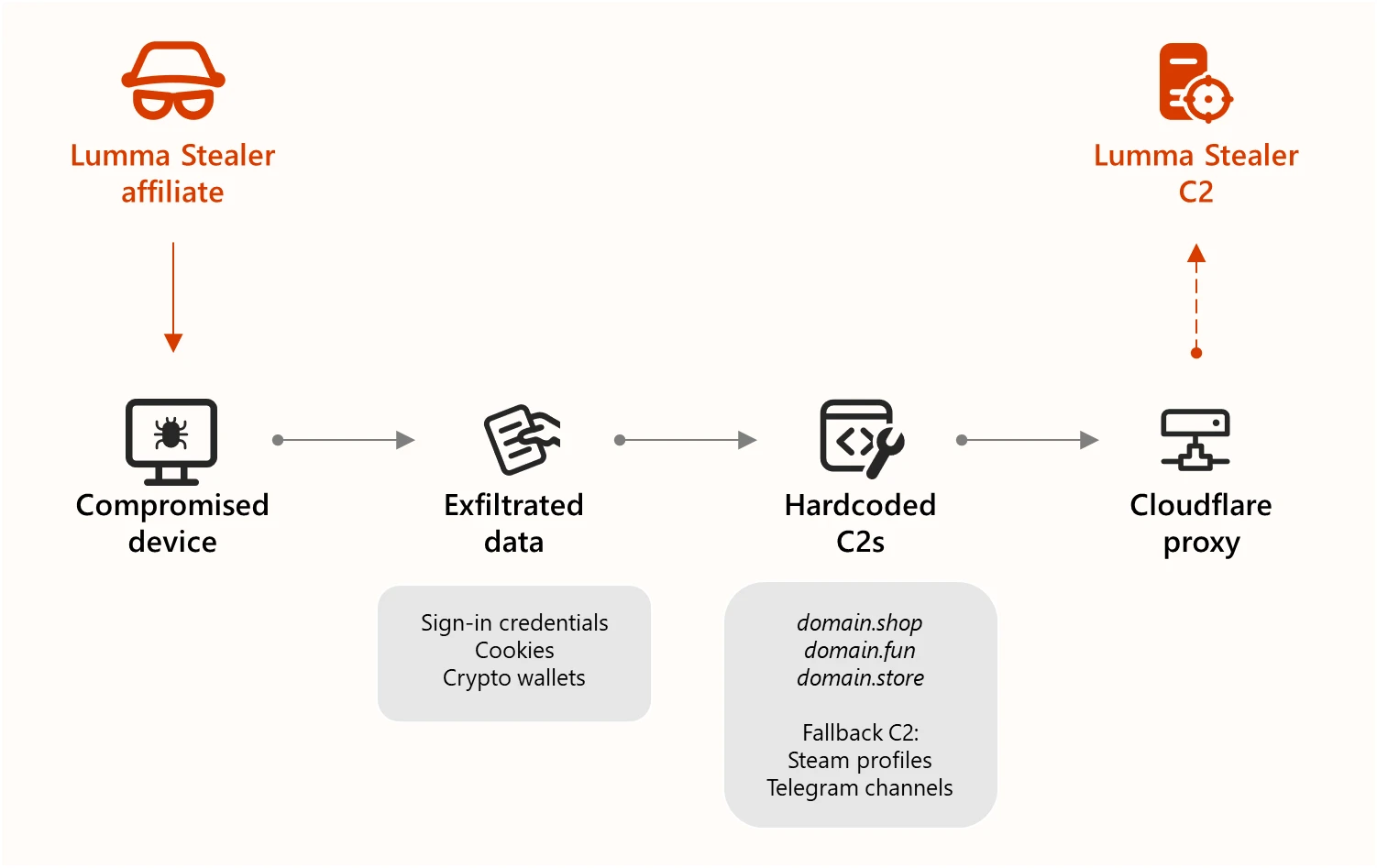
Image Credit: Securityaffairs
Law enforcement dismantled the infrastructure behind Lumma Stealer MaaS
- Law enforcement, with the help of Microsoft, Europol, and Japan’s JC3, dismantled the infrastructure behind Lumma Stealer Malware-as-a-Service (MaaS) operation, seizing 2,300 domains used for command-and-control.
- The malware, known as Lumma Stealer, targeted over 394,000 Windows systems, including those of global manufacturers, to steal sensitive data like passwords, credit card information, and crypto wallet keys.
- Microsoft's Digital Crimes Unit sinkholed over 1,300 domains used by Lumma Stealer to reroute victims to safe servers for analysis and cleanup, showcasing the collaboration between law enforcement and tech companies against cyber threats.
- The FBI and US CISA released a joint advisory containing tactics, techniques, and procedures associated with Lumma Stealer, along with indicators of compromise (IOCs), emphasizing the importance of public-private partnerships in combating cybercrime.
Read Full Article
24 Likes
Securityaffairs
125
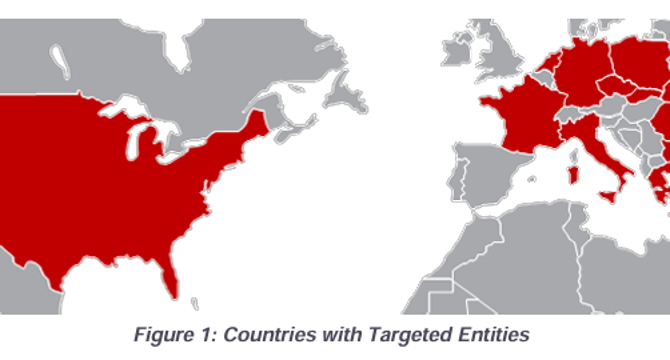
Image Credit: Securityaffairs
Russia-linked APT28 targets western logistics entities and technology firms
- CISA warns that Russia-linked APT28 is targeting Western logistics and technology companies aiding Ukraine, posing a heightened threat to supply chains.
- APT28, also known as Fancy Bear, has been active since at least 2007 and has targeted governments, militaries, and security organizations globally, including the 2016 Presidential election.
- The group operates from Russian military unit 26165 of GRU 85th Main Special Service Center, targeting Western logistics and tech firms linked to Ukraine aid across 13 countries using various tactics like spear-phishing and exploiting vulnerabilities.
- GRU Unit 26165 used tactics such as spearphishing with fake login pages, exploiting Outlook and Roundcube vulnerabilities, deploying custom malware like HEADLACE and MASEPIE, and exfiltrating data using PowerShell and APIs, targeting Western logistics and IT sectors.
Read Full Article
7 Likes
Hackersking
47
Image Credit: Hackersking
Puter The Internet OS! Free, Open-Source, and Self-Hostable
- Puter is an advanced, open-source internet operating system designed for the internet age, offering a browser-based desktop environment.
- Key features of Puter include being free, open-source, self-hostable, cross-platform compatible, lightweight, and highly customizable.
- Setting up Puter can be done locally using npm or via Docker, with instructions provided for both methods.
- Puter represents a significant advancement in operating systems, providing a flexible and user-friendly environment for various computing needs. Contribute to the project on GitHub: https://github.com/HeyPuter/puter
Read Full Article
2 Likes
Securityaffairs
199

Image Credit: Securityaffairs
A cyberattack was responsible for the week-long outage affecting Cellcom wireless network
- Cellcom, a regional wireless carrier based in Wisconsin, confirmed a cyberattack that caused a week-long outage affecting voice and text services in Wisconsin and Upper Michigan.
- The company announced it has begun restoring services and stated it had protocols in place for such incidents to address the cyberattack.
- Cellcom reported that the cyberattack impacted a network area not linked to the storage of sensitive information, and there's no evidence of customer personal or financial information being compromised.
- The company is working with external cybersecurity experts, local authorities, and aims to fully restore its services by the end of the week.
Read Full Article
11 Likes
Kaspersky
155

Image Credit: Kaspersky
What is cyber-resilience, and how to start implementing it
- Cyber-resilience is crucial for businesses to minimize the impact of cyber incidents on their primary goals and objectives.
- It involves anticipating, withstanding, recovering from, and adapting to adverse cyber conditions, according to the WEF and NIST.
- However, implementing a cyber-resilience strategy poses challenges; only 2% of companies can recover from a cyberattack within 24 hours.
- Key components include leadership, governance, risk, compliance, people, culture, business processes, technical systems, crisis management, and ecosystem engagement.
- Commonly implemented measures include backup tools, MFA, and formal response plans, but challenges lie in metrics, changing company culture, and supply chain security.
- Implementing cyber-resilience requires board-level support, collaboration between CIO and CISO, and allocation of up to 20% of cybersecurity budget to resilience projects.
- The core cyber-resilience team should be cross-functional, have the necessary authority, and bring in external experts when needed.
- Cyber-resilience is an ongoing iterative process that spans the entire organization and requires a combination of technical and organizational efforts.
- Experts stress that cyber-resilience is not a project with an endpoint but a continual process that involves multiple phases.
- Implementation involves detailed asset inventory, risk prioritization, role definition, incident playbook development, and extensive staff training.
Read Full Article
9 Likes
Qualys
194

Image Credit: Qualys
Simplifying DORA Compliance with the Qualys Enterprise TruRisk Platform
- The Digital Operational Resilience Act (DORA) establishes a unified framework for managing technology risk in the financial sector, aiming to ensure operational continuity and data protection.
- DORA requires comprehensive ICT risk management, incident reporting, digital resilience testing, third-party risk management, and information sharing.
- Qualys Enterprise TruRisk Platform helps financial institutions comply with DORA through integrated, automated security operations.
- Challenges to DORA compliance include expanding attack surfaces, tool and team silos, lack of asset visibility, manual compliance burden, and third-party complexity.
- Qualys' CyberSecurity Asset Management provides visibility into the entire IT environment, while Vulnerability Management aids in identifying and prioritizing vulnerabilities.
- Qualys Policy Audit streamlines compliance with DORA by automating system configuration assessments and reducing manual effort.
- Qualys Security Assessment Questionnaire automates internal and third-party risk assessments, while Endpoint Detection and Response facilitates incident response.
- Qualys' Patch Management helps in rapid and automated remediation of vulnerabilities, and DORA-focused dashboards enable continuous oversight and reporting.
- Qualys Enterprise TruRisk Platform simplifies compliance processes, accelerates remediation, strengthens oversight of third parties, and provides audit-ready documentation.
- Trusted in regulated environments, Qualys has the visibility, automation, and trust needed to comply with DORA and other global frameworks.
Read Full Article
11 Likes
For uninterrupted reading, download the app