Info. Security News News
Dataprivacyandsecurityinsider
394

Image Credit: Dataprivacyandsecurityinsider
NYDFS Issues Industry Letter on Risks Arising from Artificial Intelligence
- The New York Department of Financial Services (DFS) has issued an Industry Letter on the risks arising from artificial intelligence (AI).
- The letter aims to assist regulated entities in understanding and assessing cybersecurity risks related to AI and providing strategies to mitigate those risks.
- It highlights risks such as AI-enabled social engineering, AI-enhanced cybersecurity attacks, and exposure or theft of nonpublic information.
- The guidance suggests implementing controls and measures such as risk assessments, vendor management, access controls, and cybersecurity training.
Read Full Article
23 Likes
Dataprivacyandsecurityinsider
31

Image Credit: Dataprivacyandsecurityinsider
TikTok’s Legal Woes from State AGs Continues
- At least 11 more states have joined the legal battle against TikTok.
- The Attorneys General allege that TikTok mislead the public about safety and harms young people's mental health.
- The Texas Attorney General has filed a separate lawsuit, accusing TikTok of violating a state law regarding sharing minors' information.
- More states are expected to join the legal fight against TikTok.
Read Full Article
1 Like
Dataprivacyandsecurityinsider
243

Image Credit: Dataprivacyandsecurityinsider
Privacy Tip #417 – Scammers Using Hurricane Relief Aid to Commit Fraud
- Scammers are using hurricane relief aid to commit fraud.
- Fraudulent charities imitate names of legitimate disaster-related charities.
- Scammers impersonate government officials to obtain personal information or money.
- Price gouging for essential goods and services is a common scam.
Read Full Article
14 Likes
Hackingarticles
336
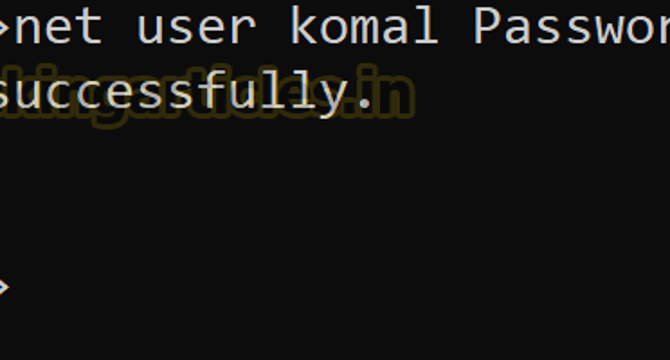
Image Credit: Hackingarticles
Abusing AD-DACL : Generic ALL Permissions
- In this post, we explore the exploitation of Discretionary Access Control Lists (DACL) using the Generic ALL permission in Active Directory environments.
- The “Generic ALL” privilege is one of the most powerful in AD because it grants complete control over the target object.
- Here’s how an attacker can leverage the “Generic ALL” privilege to compromise Active Directory:
- Weak DACLs can lead to unauthorized access or privilege escalation if not properly configured.
- Abusing DACL using the Generic ALL permission can enable various attacks like Kerberoasting, password resets, and account manipulation.
- Bloodhound or PowerView tools are used for identifying objects where attackers have Generic ALL privileges.
- Detection mechanisms such as Active Directory DACL can be used to identify and mitigate these vulnerabilities.
- A prerequisite to execute these attacks is to have a lab environment set up using Windows Server as Active Directory, Kali Linux, and Windows 10/11 clients.
- In Active Directory (AD), a DACL is a component of an object’s security descriptor that specifies which users or groups are allowed (or denied) access to the object and what actions they are permitted to perform.
- Kerberoasting is an attack technique that targets service accounts in Active Directory environments, where an attacker with Generic ALL permissions on a user can exploit the ability to request service tickets (TGS).
Read Full Article
20 Likes
Infoblox
252

Image Credit: Infoblox
NIS 2 Implementing Regulation and the importance of DNS Security
- The European Union's Network and Information Systems Directive (NIS 2) is scheduled to be implemented into law in October 2024, with further technical guidance expected to be released in the coming months.
- The recently adopted NIS 2 Implementing Regulation outlines technological requirements for entities subject to NIS 2. One of these requirements is for the implementation of best practices for DNS security.
- Experts predict that ENISA will define best practices based on three key areas: securing the DNS platform, securing the DNS protocol, and implementing DNS as a cybersecurity control.
- Organizations are expected to have a robust and resilient DNS architecture in place that is accounted for in business continuity plans and processes, as DNS is a foundational networking service that users and applications rely on.
- NIS 2 is expected to drive regulated entities to formalize strategies and processes to secure their external-facing, authoritative domains, as DNS is widely abused by threat actors to carry out cyber attacks.
- Protective DNS, a DNS service that intercepts requests from clients to resolve malicious DNS domains, has become a widely accepted best practice, as it provides a highly scalable and pervasive security control that is simple to deploy and based on a recognized DNS standard.
- Regulated entities may need to perform DNS architecture assessments to address risks such as insufficient patch management or architecture resiliency before instituting processes to proactively maintain their DNS infrastructure.
- Infoblox performs DNS security assessments and security workshops that can help organizations transform their DNS architecture into a robust cybersecurity enforcement platform.
- Using secure DNS can reduce the ability for 92% of malware attacks from a command-and-control perspective.
- NIS 2 requires entities to implement best practices for DNS security, so it is important for legal, compliance, and cybersecurity practitioners to understand the requirements and prepare accordingly.
Read Full Article
15 Likes
Adamlevin
106

Image Credit: Adamlevin
Are Creatives Fleeing Instagram Due to AI?
- Meta AI, the generative AI platform developed by Meta, is using content from Facebook and Instagram to train its AI algorithms.
- This move has caused frustration among visual artists who fear their work may be processed and synthesized into competing products.
- Many artists have announced their intention to leave Instagram for other platforms with better intellectual property protections.
- However, switching platforms comes with the cost of losing followers and potential exposure to wider audiences.
Read Full Article
6 Likes
Securityintelligence
186

Image Credit: Securityintelligence
The cybersecurity skills gap contributed to a $1.76 million increase in average breach costs
- IBM has found that staffing shortages in cybersecurity have contributed to increased data breach costs in recent years.
- The company's Cost of a Data Breach Report 2022 found that organizations with insufficiently staffed security teams faced an average breach cost of $4.56m.
- The cybersecurity skills gap also contributed to a $1.76m increase in average breach costs according to IBM's 2024 report.
- The report found that more than half of breached organizations faced severe security staffing shortages, a skills gap that increased by double digits from the previous year.
- The ever-expanding attack surface is also a factor in the skills gap, with new technologies, such as generative AI, creating the need for specialized skills faster than the development of professionals to possess them.
- Burnout caused by rising incidents and intensifying workloads due to the pandemic-related shift to remote work is another factor contributing to cybersecurity staffing shortages.
- IBM recommends approaches to addressing cybersecurity skills shortages, such as managed security services, simplifying environments, training and development, incentivizing the upskilling and reskilling of existing IT staff, competitive compensation and benefits packages, and stronger identity security.
- AI and automation can partially offset the impact of staffing shortages by improving efficiency and reducing the need for repetitive tasks.
- The widespread adoption of AI is expected to create even greater pressure on cybersecurity teams.
- Organizations can help to alleviate the skills gap by fostering relationships with local universities, offering placements and providing a graduate entry route into their organization.
Read Full Article
11 Likes
Krebsonsecurity
416

Sudanese Brothers Arrested in ‘AnonSudan’ Takedown
- The U.S. government has arrested two Sudanese brothers accused of running the cybercrime business, Anonymous Sudan (AnonSudan).
- AnonSudan is known for launching powerful distributed denial-of-service (DDoS) attacks against various targets, including hospitals, news websites, and cloud providers.
- The younger brother could face life in prison for allegedly seeking to kill people with his attacks.
- Additionally, AnonSudan offered DDoS-for-hire services and extorted victims for money in exchange for calling off attacks.
Read Full Article
25 Likes
Amazon
336

Image Credit: Amazon
An unexpected discovery: Automated reasoning often makes systems more efficient and easier to maintain
- Automated reasoning finds formally verified code to be more performant. It offers confidence to explore additional optimizations for improving system performance even further. It results in less late-night log analysis and debugging sessions.
- At AWS, automated reasoning helps verify complex distributed systems that process billions of requests per second. It verifies system behavior under any possible scenario and achieve the same effect quickly and efficiently.
- Automated reasoning is used to prevent bugs. Amazon Simple Storage Service (S3) uses it to detect and fix subtle bugs that escape detection, particularly in large-scale, fault-tolerant architectures.
- The AWS Identity and Access Management (IAM) service uses formal specification and proves to make its core authorization piece more performant. The optimized IAM authorization engine is now 50% faster than its predecessor.
- Optimizing encryption for better performance is complex. AWS uses automated reasoning to make RSA faster and deploy faster.
- As adoption of automated reasoning tools increases, it becomes easier for AWS to improve the usability and scalability of automated reasoning tools. AWS is delivering higher performant code to customers faster, translating into cost savings for customers.
- Automated reasoning could prove for large-scale cloud architectures the critical properties like security, compliance, availability, durability, and safety.
- Byron founded the Amazon Automated Reasoning Group in 2015 and currently serves as Vice President and Distinguished Scientist of Automated Reasoning at AWS. His interests include computer and network security, program analysis and verification, theorem proving and biological systems.
Read Full Article
20 Likes
Socprime
13

Image Credit: Socprime
How MSSPs and MDRs Can Maximize Threat Detection Efficiency with Uncoder AI
- Managing detection rules across multiple security solutions in the environments of current and potential clients poses a significant challenge to service providers.
- Detection engineers, SOC analysts, and SIEM administrators in MDR/MSSPs face daily challenges managing detections across diverse client infrastructures.
- A vendor-agnostic approach to detection engineering might greatly simplify the process.
- Tools like Uncoder AI significantly ease the amount of manual work required to maintain detection efficiency by enabling engineers to convert detection logic across various SIEM formats quickly.
- Relying heavily on manual work in multiple processes can lead to errors, inefficiencies in detection, and other bottlenecks in the detection pipeline.
- Uncoder AI enables teams to leverage automation capabilities to quickly and seamlessly translate detection rules across various SIEM platforms.
- Minimizing the Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) metrics is crucial for demonstrating the effectiveness of their services.
- With Uncoder AI, detection engineers can swiftly generate SIEM-specific queries from raw IOCs and further simplify the process by applying the custom data schema and automated deployment by their choice.
- Using Uncoder AI, teams can streamline the routine processes of translating and customizing generic detection rules into 44 SIEM, EDR, XDR, and Dala Lake technologies.
- Uncoder AI greatly simplifies the process of adapting the detection logic from one SIEM format to another by automating cross-platform translations.
Read Full Article
Like
Hackersking
36
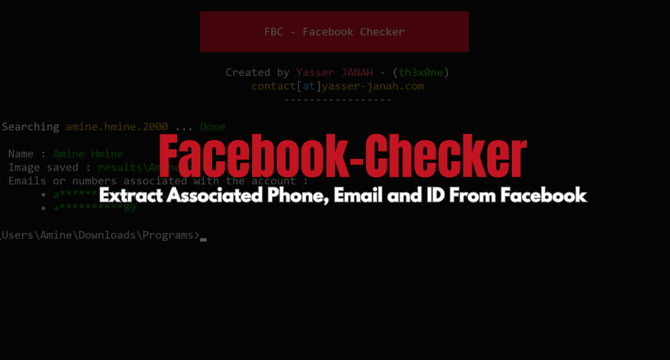
Image Credit: Hackersking
Check If Any Phone Number and Email Is Associated With A Facebook Account
- A straightforward tool called Facebook Checker allows users to extract information directly from Facebook.
- The tool can be helpful in gathering information about a suspicious Facebook account or uncovering the real person behind a fake account.
- Facebook Checker is a go language-based tool that retrieves or extracts information such as phone number, email, ID, and username associated with a target on Facebook.
- To use the tool, the user needs to install Go language, install the Facebook Checker tool, and provide the Facebook ID, username, email, or phone number of the target.
Read Full Article
2 Likes
Securityaffairs
177

Image Credit: Securityaffairs
A critical flaw in Kubernetes Image Builder could allow attackers to gain root access
- A critical flaw in Kubernetes Image Builder could allow attackers to gain root access.
- The vulnerability affects Kubernetes clusters with nodes using VM images from the Image Builder project and its Proxmox provider.
- The flaw was discovered by cybersecurity researcher Nicolai Rybnikar.
- To mitigate the issue, rebuild images with the patched Image Builder version and re-deploy them.
Read Full Article
10 Likes
Hackersking
407

Image Credit: Hackersking
Crack Password ZIP, RAR and PDF with File-Cracker Tool On Kali Linux
- This article introduces a tool called FILE-CRACKER on Kali Linux that allows users to crack passwords of ZIP, RAR, and PDF files.
- Password cracking or brute-force attack is the process of trying all possible password combinations until a valid password is found.
- FILE-CRACKER is a Python script that claims to crack passwords using a provided dictionary and can be used on Kali Linux.
- Users can clone the FILE-CRACKER tool from their official GitHub repo, install the required dependencies, and follow the instructions to use it.
Read Full Article
24 Likes
Securityaffairs
18

Image Credit: Securityaffairs
VMware fixes high-severity SQL injection flaw CVE-2024-38814 in HCX
- VMware has fixed a high-severity SQL injection flaw in HCX.
- The vulnerability, tracked as CVE-2024-38814, allowed non-admin users to remotely execute code on the HCX manager.
- The flaw was privately reported to VMware and an authenticated user with non-admin rights could exploit it by using crafted SQL queries.
- Multiple versions of the HCX platform were impacted, but the vulnerability has been fixed in the latest updates.
Read Full Article
1 Like
Securityaffairs
102
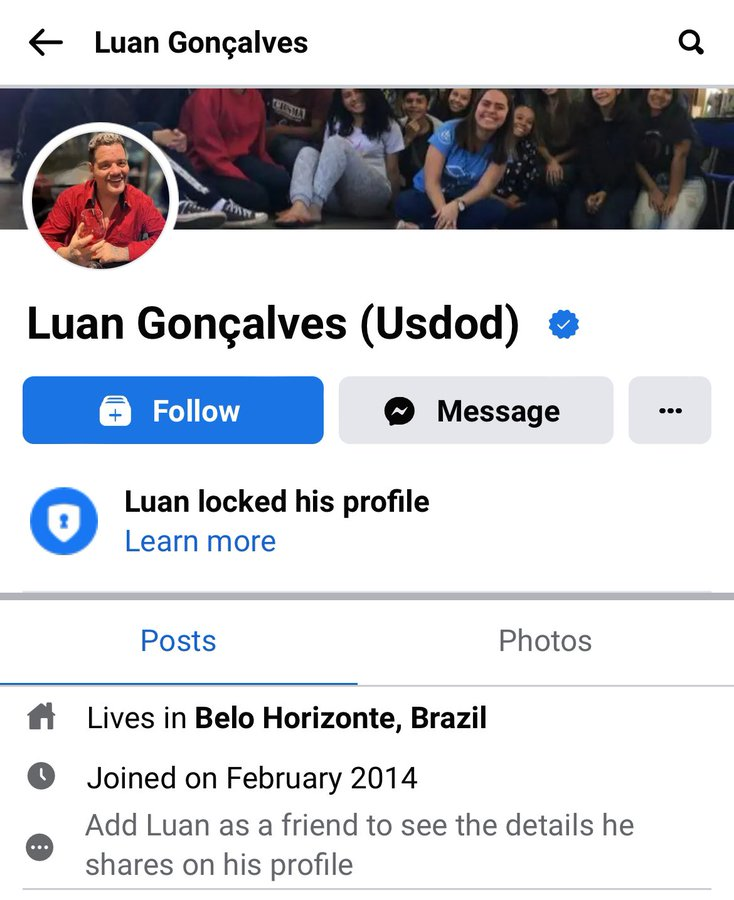
Image Credit: Securityaffairs
Brazil’s Polícia Federal arrested the notorious hacker USDoD
- Brazil's Polícia Federal has arrested the notorious hacker USDoD.
- USDoD is known for high-profile data breaches, including Airbus, FBI's InfraGard, and National Public Data.
- The hacker's identity was revealed through a CrowdStrike investigation, confirming him as Luan BG from Brazil.
- The arrest was made as part of Operation Data Breach, and the investigation is ongoing.
Read Full Article
6 Likes
For uninterrupted reading, download the app