Info. Security News News
Hackingblogs
75

Image Credit: Hackingblogs
Cisco Was Breached critically : Investigation Claims Made For Data Breach
- Cisco Systems, Inc. is investigating claims made by hackers about a recent cyberattack.
- The hacker, known as IntelBroker, claimed to have breached Cisco's data on October 6, 2024.
- Several major companies, including Apple, Google, Microsoft, and Amazon Web Services, are said to be among the victims.
- The exposed data includes source code, credentials, certificates, API tokens, and more.
Read Full Article
4 Likes
Securityaffairs
31

Image Credit: Securityaffairs
Finnish Customs dismantled the dark web drugs market Sipulitie
- Finnish Customs dismantled the dark web drugs market Sipulitie.
- The Tor marketplace Sipulitie was shut down and its servers seized.
- The marketplace was used for selling narcotics anonymously.
- Finnish Customs identified the main operator, moderators, and users.
Read Full Article
1 Like
Infoblox
319

Image Credit: Infoblox
Cybersecurity Awareness Month: Secure Our World with DNS
- The Domain Name System (DNS) can be a valuable tool for stopping attacks and preventing attacks from happening.
- Whenever a new domain name is registered, that information is stored in DNS.
- DNS footprints are visible, if you know what to look for—five of the seven steps in the Cyber Kill Chain use DNS in one way or another.
- DNS can be used proactively to find suspicious domains before they are active and before they are seen in a network during an attack.
- DNS-powered investigations can find clusters of domains all at once.
- DNS matters for everyone and can be used to stop attacks on individuals or enterprises.
- Governments around the world are exploring options to provide protective DNS to their citizens.
- Infoblox Threat Intel uses DNS to find and track suspicious domains and Traffic Distribution Systems (TDSs).
- DNS complements other security tools but also provides the opportunity to stop attacks before they ever begin.
- The power, simplicity, and pervasiveness of DNS makes it a tool that can improve security for everyone.
Read Full Article
19 Likes
Qualys
239

Image Credit: Qualys
Oracle Critical Patch Update, October 2024 Security Update Review
- This quarter's Oracle Critical Patch Update contains patches for 334 security vulnerabilities, with Oracle Communications receiving the highest number of patches.
- 244 of the 334 security patches provided by the October Critical Patch Update are for non-Oracle CVEs.
- The security updates cover numerous product families like Oracle Database, Oracle Java SE, Oracle Financial Services Applications, etc.
- Qualys has released five QIDs mentioned to cover the security vulnerabilities patched.
- In Oracle Communications products, there are several critical severity vulnerabilities addressed, which a remote attacker might exploit in low-complexity network attacks.
- Oracle MySQL also has critical severity vulnerabilities addressed that may be exploited without user credentials.
- Oracle Fusion Middleware's patch update contains 32 security patches, with a few vulnerabilities joined to different products.
- The Oracle Financial Services Applications patch includes a total of 20 security patches, with 15 vulnerabilities that a remote attacker may exploit without user credentials.
- Oracle Commerce and Oracle Enterprise Manager updates include nine and seven security patches, respectively, with a few vulnerabilities that a remote attacker may exploit without user credentials.
- Oracle Analytics and Oracle Systems have security patches with critical severity vulnerabilities addressed, which may be exploited without user credentials.
Read Full Article
14 Likes
Securityintelligence
412

Image Credit: Securityintelligence
Navigating the ethics of AI in cybersecurity
- Artificial intelligence has become increasingly commonplace and is used for everything from personal recommendations to incident response automation. As its use grows in cybersecurity, to detect insider threats or screen employee awareness via simulated emails, transparency, ethical considerations and a central focus on accountability are essential to prevent the technology's misuse and falling foul of legal restrictions. There are concerns that malicious hackers are already resorting to using AI, resulting in phising content. Genuine companies need to recognise that while AI can be a useful tool in counter-cybercrime, it also carries with it ethical responsibilities and potential privacy breaches.
- Large companies may use AI to train algorithms which can detect weaknesses and enable penetration in apparatus. However, cyber criminals hijacking these programmes or using them for the cloud, can have serious public information compromise implications. For this reason, security solution providers must ensure data protection and privacy are maintained, in adherence to data rights legislation such as the GDPR.
- In cybersecurity, AI has developed several ethical and privacy challenges. It is crucial that technology companies incorporate transparency and accountability ethics in these services, to prevent harm. Data quality should be high, anonymising and safeguarding confidential information while following frameworks such as TEVV, which entails Testing, Evaluation, Validation and Verification controsl. Cybersecurity-specific uses of AI carry the risk of profiling and targeting specific groups, bringing about potentially unjust actions. The models of many AI products often lack the explainability needed to gain transparency and accountability in AI- driven decision-making.
- People training AI systems impart unintentional biases that may end up being amplified by the machine. Companies using AI as a shortcut for human resources and who fail to reinvest in training and AI-adjacent roles run the risk of amplifying AI's limitations, creating AI Drift.
Read Full Article
24 Likes
Socprime
285

Image Credit: Socprime
UAC-0050 Attack Detection: russia-Backed APT Performs Cyber Espionage, Financial Crimes, and Disinformation Operations Against Ukraine
- The UAC-0050 hacking collective known for its extensive offensive operations against Ukraine is back into the cyber threat arena.
- The UAC-0050 group focuses on three key directions, including cyber espionage and financial crimes, and disinformation operations tracked under the “Fire Cells Group” brand.
- Organizations require reliable detection resources to proactively defend against potential intrusions as cyber-attacks by Russia-affiliated hacking collectives against Ukrainian entities become more frequent and sophisticated.
- SOC Prime Platform equips security teams with the entire detection stack to proactively thwart cyber-attacks covered in the related CERT-UA research.
- Financially motivated cyber crimes, which were recently observed, are also affiliated with the UAC-0006 hacking group.
- UAC-0050 is a Russia-linked hacking group that primarily targets Ukrainian state bodies, using phishing campaigns to distribute Remcos RAT malware, often posing as the Security Service of Ukraine and sending emails with malicious attachments.
- UAC-0050 mainly focuses on cyber espionage, financially motivated threats, and the “Fire Cells Group” brand's cyber activity, as observed in a recent CERT-UA report.
- UAC-0050 attempted at least 30 cases of unauthorized access to accountants' computers using REMCOS/TEKTONITRMS software to steal funds in the past few months.
- To mitigate UAC-0050 attacks, financial institution clients are advised to implement technical methods to verify payment actions, including using additional authentication through a mobile app.
- Leveraging MITRE ATT&CK(SM) gains detailed insight into the context of the most offensive operations associated with UAC-0050, and SOC Prime has a comprehensive set of dedicated Sigma rules addressing the corresponding ATT&CK tactics, techniques, and sub-techniques.
Read Full Article
17 Likes
Kaspersky
395

Image Credit: Kaspersky
Security and privacy settings in Nike Run Club | Kaspersky official blog
- Configuring privacy settings in fitness apps is crucial to protect sensitive information, including location data.
- Nike Run Club app's privacy settings can be found under the profile initials icon in the top left corner. Users should check profile visibility, prevent data sharing for personalized advertising, and restrict Nike from using workout data.
- Other running apps like Strava, MapMyRun, adidas Running, and ASICS Runkeeper also have privacy guides available.
- Kaspersky Premium is recommended for maximizing privacy and protecting against digital identity theft.
Read Full Article
23 Likes
Securityaffairs
22

Image Credit: Securityaffairs
U.S. CISA adds Microsoft Windows Kernel, Mozilla Firefox and SolarWinds Web Help Desk bugs to its Known Exploited Vulnerabilities catalog
- U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Windows Kernel, Mozilla Firefox and SolarWinds Web Help Desk bugs to its Known Exploited Vulnerabilities catalog.
- CISA updated its Known Exploited Vulnerabilities (KEV) catalog with the following vulnerabilities:
- - CVE-2024-30088: Microsoft Windows Kernel TOCTOU Race Condition Vulnerability
- - CVE-2024-9680: Mozilla Firefox Use-After-Free Vulnerability
Read Full Article
1 Like
Hackersking
337

Image Credit: Hackersking
Can I Pursue Cybersecurity After the 12th?
- The cybersecurity industry is rapidly growing and in constant demand of skilled professionals to protect digital assets.
- You can pursue cybersecurity after the 12th, and it is a wise career choice due to a booming industry with competitive salaries and diverse career options.
- Educational pathways include diploma programs in cybersecurity, a Bachelor's degree in cybersecurity or related fields like computer science, or professional certifications like CEH and CISSP.
- To succeed in cybersecurity, you need technical proficiency, problem-solving abilities, knowledge of ethical hacking, and a willingness to continuously learn.
- There are many career opportunities in cybersecurity after 12th, such as ethical hacking, network security, cybersecurity analyst, penetration tester, and incident responder.
- To get started in cybersecurity after the 12th, identify your interests, enroll in the right courses, develop practical experience through internships or projects, and stay informed with the latest trends in the industry.
Read Full Article
20 Likes
Global Fintech Series
204

Image Credit: Global Fintech Series
Doxim Appoints Matthew Yacoub as Chief Information Officer
- Doxim appoints Matthew Yacoub as Chief Information Officer.
- Yacoub brings over 25 years of industry experience in IT and security leadership.
- His expertise includes modernizing technology platforms, establishing data standards, and embedding a security-first approach.
- Yacoub aims to foster operational excellence and ensure security and regulatory compliance at Doxim.
Read Full Article
12 Likes
Securityaffairs
435

Image Credit: Securityaffairs
GitHub addressed a critical vulnerability in Enterprise Server
- GitHub addressed a critical vulnerability, CVE-2024-9487, in its Enterprise Server.
- The vulnerability allowed unauthorized access to affected instances by exploiting a cryptographic signature verification flaw.
- To exploit the vulnerability, the attacker required direct network access and a signed SAML response or metadata document.
- GitHub also addressed an information disclosure vulnerability, CVE-2024-9539, in Enterprise Server.
Read Full Article
26 Likes
Cybersecurity-Insiders
359

Image Credit: Cybersecurity-Insiders
Cybersecurity concerns arise as Windows 10 support to end next year
- With Microsoft ending support for Windows 10 next year, cybersecurity analysts are warning about potential vulnerabilities.
- Options for users include requesting a support extension, upgrading to Windows 11, transitioning to Chrome OS or Linux, purchasing a new PC, or remaining on Windows 10.
- Continuing to use Windows 10 after support ends puts users at risk of cyberattacks, as security updates will no longer be provided.
- The decision to upgrade, switch operating systems, or invest in new hardware should be made before the deadline to ensure a secure computing environment.
Read Full Article
21 Likes
Hackingblogs
57
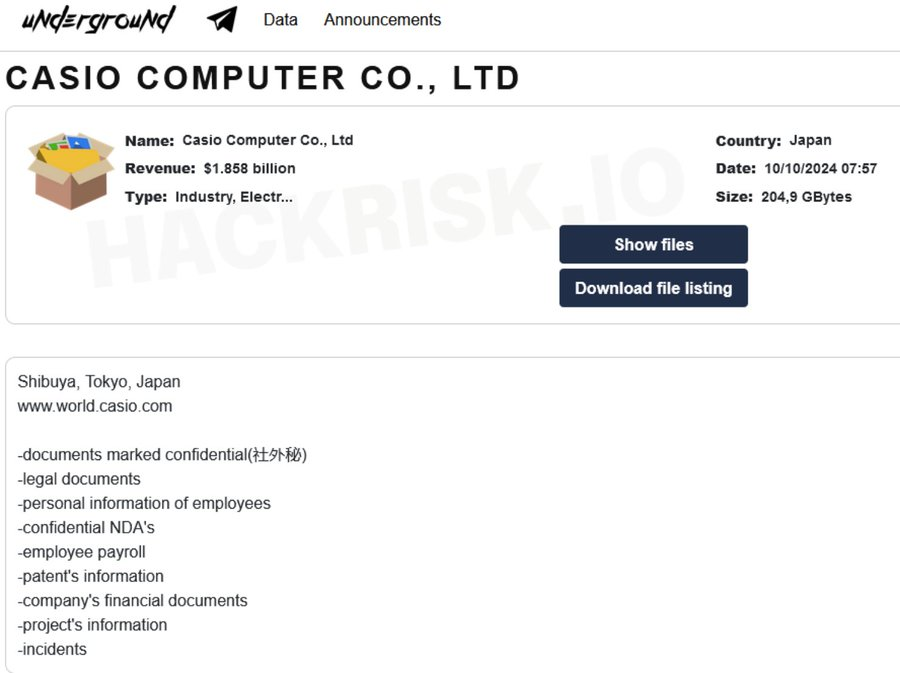
Image Credit: Hackingblogs
Casio Was Hacked : Information Leak Caused by Ransomware Attack
- Casio Computer Co., Ltd. announced a system failure due to unauthorized access and a ransomware attack.
- Sensitive personal and confidential internal information was leaked as a result of the attack.
- The attack was linked to the ransomware organization Underground.
- Services were shut down and data leakage included personal data, business partner information, and internal documents.
Read Full Article
3 Likes
Securityaffairs
80
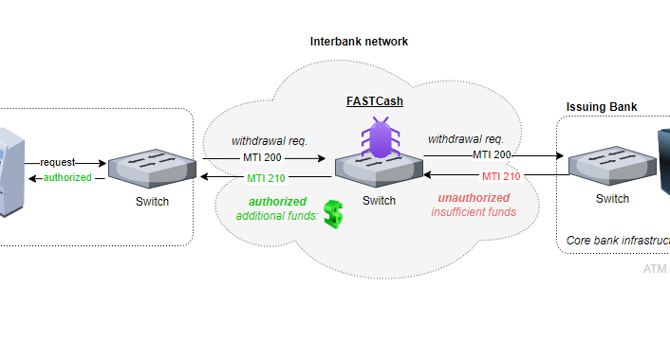
Image Credit: Securityaffairs
A new Linux variant of FASTCash malware targets financial systems
- North Korea-linked actors deploy a new Linux variant of FASTCash malware to target financial systems.
- The variant targets Ubuntu 22.04 LTS distributions and intercepts declined magnetic swipe transactions.
- The malware is used to facilitate unauthorized cash withdrawals from ATMs.
- The Linux variant highlights the need for better detection capabilities in Linux server environments.
Read Full Article
4 Likes
Qualys
151

Image Credit: Qualys
The Spanish National Security Framework (ENS) is Now Part of the Qualys Enterprise TruRisk™ Platform
- The Spanish National Security Framework (ENS) is now part of the Qualys Enterprise TruRisk™ Platform.
- ENS is a mandatory framework designed to ensure optimal security for the digital infrastructure in the Spanish public sector and critical infrastructures.
- Qualys Policy Compliance (PC) module helps assess compliance with ENS requirements and generate detailed compliance reports.
- Qualys is developing predefined policies aligned with ENS controls to facilitate implementation and ensure effective compliance.
Read Full Article
9 Likes
For uninterrupted reading, download the app