Info. Security News News
Securityintelligence
432

Image Credit: Securityintelligence
AI hallucinations can pose a risk to your cybersecurity
- AI hallucinations are inaccurate answers provided by large language models and pose a risk to cybersecurity due to compromised decision-making and brand reputation.
- The biggest reason for hallucination is incorrect data the model uses for training AI, and input bias is also a significant cause.
- Organizations increasingly use generative AI for cybersecurity, such as training on real-time data and responding to a specific threat with the best action.
- AI hallucinations in cybersecurity may cause an organization to overlook potential threats and create false alarms, prolonging the recovery process and increasing the risk of attack.
- Reducing the impact of AI hallucinations can be accomplished by training employees on prompt engineering, focusing on data cleanliness, and incorporating fact-checking into the process.
- Using generative AI tools to fight cyber crime can make organizations more resilient by leveling the playing field.
Read Full Article
25 Likes
Securityaffairs
8
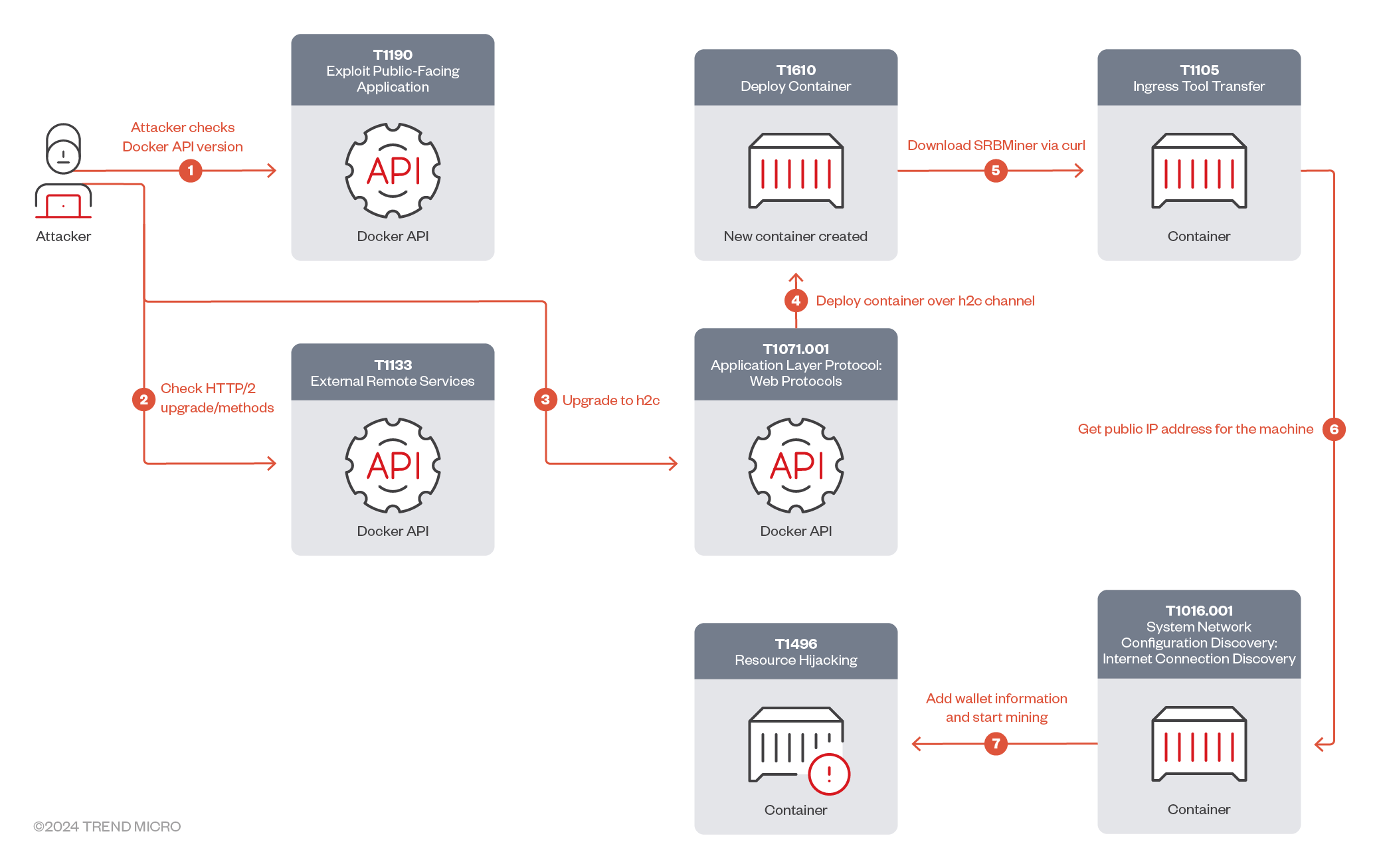
Image Credit: Securityaffairs
Crooks are targeting Docker API servers to deploy SRBMiner
- Threat actors are targeting Docker remote API servers to deploy SRBMiner crypto miners on compromised instances.
- Attackers bypass security by using the gRPC protocol over h2c to execute crypto mining on Docker hosts.
- After scanning for public-facing Docker API hosts and checking for HTTP/2 upgrades, attackers manipulate Docker functionalities via gRPC methods.
- SRBMiner is downloaded and deployed from GitHub, with attackers mining cryptocurrency to their wallet and masking their public IP address.
Read Full Article
Like
Securityaffairs
412

Image Credit: Securityaffairs
Why DSPM is Essential for Achieving Data Privacy in 2024
- Data Security Posture Management (DSPM) helps organizations address evolving data security and privacy requirements by protecting and managing sensitive information.
- The proliferation of cloud workloads and data creates a complex web of data sprawl that is difficult to manage.
- DSPM allows security and privacy teams to discover sensitive data, identify its security and compliance postures, and mitigate risks.
- DSPM offers a comprehensive view of an organization's data security posture, compliance position, security, and privacy risks.
- A robust DSPM solution is necessary due to high volumes of dark and unstructured data containing sensitive information being a primary target for data breach attacks.
- It becomes challenging for organizations to have comprehensive visibility of their data, making them vulnerable to various privacy and security threats.
- Data classification plays a critical role in giving organizations insights into the privacy risks associated with their personal or sensitive data.
- DSPM gives insights into which data stores contain sensitive data and privacy risks associated with those data stores, allowing organizations to protect their most critical data stores first.
- DSPM can help covered entities to comply with HIPAA regulations by identifying PHI across an entity's data stores, SaaS services, and other cloud environments.
- DSPM is a necessary tool in an organization's data management and protection arsenal.
Read Full Article
24 Likes
Securityaffairs
131

Image Credit: Securityaffairs
SEC fined 4 companies for misleading disclosures about the impact of the SolarWinds attack
- The SEC fined Unisys, Avaya, Check Point, and Mimecast for misleading disclosures about the impact of the SolarWinds attack.
- The SEC charged the companies for downplaying the impact of the attack in their public disclosures.
- Unisys, Avaya, Check Point, and Mimecast were fined $4M, $1M, $995K, and $990K respectively.
- Companies agreed to stop future violations, pay penalties, and improve cybersecurity controls.
Read Full Article
7 Likes
Kaspersky
166

Image Credit: Kaspersky
Effective AI adoption for optimizing SOC analysts’ work
- Artificial Intelligence (AI) can be used to reduce the workload of cybersecurity professionals, particularly when it comes to the processing of suspicious events known as triage. By having AI handle simple cases, a more limited group of cases then needs to be addressed by humans. One such form of technology is the use of an Auto-Analyst. The Auto-Analyst aids in filtering out false positives from the SIEM system and only forwarding the ones with a high probability of a real incident to be reviewed by a human. It enables the SOC team to focus on more complex tasks with around 30% of alerts filtered by the AI system. Processes need to be put in place to allow AI to work effectively and accurately when it comes to cybersecurity, including controlling training data, prioritizing incoming data and interpreting the results. The Kaspersky Managed Detection and Response service provides continuous threat hunting, detection, and response for organizations, giving businesses a technological advantage while reducing their workload.
- AI cannot replace cybersecurity professionals, but it can certainly make their jobs easier.
- AI is particularly useful for processing suspicious events, known as triage.
- Kaspersky MDR has developed an Auto-Analyst that filters out false positives from the SIEM system and only forwards ones with a high probability of a real incident to be checked by a human.
- Processes must be put in place for AI to work effectively and accurately when it comes to cybersecurity, including controlling training data, prioritizing incoming data, interpreting results, selective review of results, and excluding AI analysis for certain alerts.
- The Kaspersky Managed Detection and Response service offers cybersecurity services that can reduce the workload of SOC teams, allowing them to focus on complex tasks.
- The Auto-Analyst is trained through supervising machine learning systems and CatBoost, which allows it to distil millions of alerts about potential threats into a smaller number of alerts.
- The AI system filters around 30% of alerts, freeing the SOC team to tackle more complex issues.
- By prioritizing incoming data, processes enable AI to work effectively when it comes to cybersecurity.
- The Kaspersky Managed Detection and Response service can be an advantage for businesses, enabling them to reduce team workloads while maintaining a high degree of cybersecurity best practice.
Read Full Article
10 Likes
TechCrunch
70

Image Credit: TechCrunch
Researchers link Polyfill supply chain attack to huge network of copycat gambling sites
- FUNNULL used the domain to essentially carry out a supply chain attack.
- Researchers at Silent Push say they mapped out a network of thousands of Chinese gambling sites and linked it to FUNNULL.
- FUNNULL was using its access to Polyfill.io to inject malware and redirect website visitors to that malicious network of casino and online gambling sites.
- Around 40,000 mostly Chinese-language websites hosted by FUNNULL are identified which appeared to impersonate online gambling and casino brands including Sands, the Grand Lisboa in Macau, and online gambling portals Bet365 and Bwin.
- FUNNULL is operating what appears to be one of the largest online gambling rings on the internet.
- FUNNULL claims to have “more than 30 data centers on the continent”, likely referring to mainland China.
- The suspicious network of sites is hosted on FUNNULL’s content delivery network with office addresses in Canada, Malaysia, the Philippines, Singapore, Switzerland and the United States.
- FUNNULL could have launched much more dangerous attacks, but they were apparently trying to monetize a network of spammy sites.
- These kinds of supply chain attacks are increasingly possible because the web is now a complex global network of websites that are often built with third-party tools.
- ACB Group claimed to own FUNNULL on an archived version of its official website, which is now offline.
Read Full Article
4 Likes
Securityaffairs
263

Image Credit: Securityaffairs
Samsung zero-day flaw actively exploited in the wild
- Google's Threat Analysis Group (TAG) warns of a Samsung zero-day vulnerability, tracked as CVE-2024-44068 (CVSS score of 8.1), which is exploited in the wild.
- The vulnerability is a use-after-free issue, where attackers could exploit the flaw to escalate privileges on a vulnerable Android device.
- Samsung addressed the vulnerability with the release of security updates in October 2024.
- The fact that Google TAG discovered the flaw suggests that commercial spyware vendors may have used the exploit to target Samsung devices.
Read Full Article
15 Likes
Hackersking
17
Image Credit: Hackersking
All In One Facebook Toolkit To Get Data From Facebook Account
- We have discussed different information-gathering tools to get details of any Facebook profile using their username, email, and phone number.
- The Facebook Toolkit++ tool offers a complete set of features to extract information from Facebook profiles.
- The toolkit allows users to access and extract various data points such as account information, ID, email, name, birthday, gender, location, URL profile, mobile number, religion, username, bio, and more.
- To install the Facebook Toolkit++, users can follow the instructions provided and run the tool on their Linux system.
Read Full Article
1 Like
Securityintelligence
52

Image Credit: Securityintelligence
What NIST’s post-quantum cryptography standards mean for data security
- The National Institute of Standards and Technology (NIST) has published its first set of post-quantum cryptography (PQC) standards.
- The three PQC standards, ML-KEM, ML-DSA, and SLH-DSA, have been finalized by NIST to strengthen cryptography infrastructure for the quantum era.
- Organizations are urged to begin planning and preparing for the transition towards quantum-safe to withstand future attacks from quantum computers.
- IBM has engaged with large organizations and established quantum-safe transformational initiatives to strengthen cryptographic posture and resilience against quantum-powered risks.
Read Full Article
3 Likes
Sentinelone
426

Image Credit: Sentinelone
macOS NotLockBit | Evolving Ransomware Samples Suggest a Threat Actor Sharpening Its Tools
- Researchers at Trend Micro have discovered the first macOS ransomware sample with credible file locking capabilities, which masquerades as LockBit ransomware on encrypting a user’s files.
- The ransomware is written in Go and is distributed as an x86_64 binary, meaning it will only run on Intel Macs or Apple silicon Macs.
- NotLockBit’s public key is used to encrypt a randomly generated master key, which in turn is used in the subsequent file encryption process and written to a README.txt file deposited in each folder containing encrypted files.
- The malware attempts to use osascript to change the Desktop wallpaper and display a LockBit 2.0 banner.
- Prior to the file locking operation, the malware attempts to exfiltrate the user’s data to a remote server via AWS S3 cloud storage.
- SentinelOne has discovered a set of related Mach-O samples and provides indicators of compromise for this set of samples and discusses how they have changed across versions.
- The samples can be split into three groups and are entirely stripped of symbolic information.
- SentinelOne customers are protected from all known variants of macOS.NotLockBit through a multi-engine platform that combines static and dynamic AI, ensuring that the latest threats are stopped pre-execution and on-execution.
- Ransomware on macOS remains a small and still unlikely threat, but it is apparent that threat actors have understood that the double extortion method that works so well on other platforms is equally viable on Apple’s desktop platform.
- For now, the threat actor’s AWS accounts have been removed and there are no known victims or distribution methods in the wild.
Read Full Article
25 Likes
Hackersking
348

Image Credit: Hackersking
Can Cybersecurity Make You a Millionaire?
- The demand for cybersecurity professionals continues to rise, so do the financial opportunities for those who excel in this domain.
- Chief Information Security Officer (CISO), Security Consultants, Ethical Hackers, and Security Engineers are highly lucrative positions in cybersecurity.
- Entrepreneurship in Cybersecurity is another path to becoming a millionaire through cybersecurity by starting your own business.
- Cybersecurity experts can earn considerable sums of money through bug bounty programs run by tech giants like Google, Facebook, and Microsoft.
- Building a Personal Brand by writing books, offering online courses, speaking at conferences, and being active on social media can create additional streams of income.
- While it’s possible to become a millionaire in cybersecurity, it requires dedication, continual learning, and sometimes a bit of luck.
- The cybersecurity industry is competitive, and only those who consistently push their limits, adapt to new trends and seek out new opportunities will rise to the millionaire ranks.
- With the right mindset, determination, and a bit of creativity, cybersecurity offers ample opportunities to not only earn a high salary but potentially become a millionaire.
- The world of cybersecurity is vast and full of opportunities. For those willing to dive deep and stay ahead of the curve, financial success is within reach.
Read Full Article
20 Likes
Securityaffairs
430
Image Credit: Securityaffairs
Experts warn of a new wave of Bumblebee malware attacks
- Experts warn of a new wave of attacks involving the Bumblebee malware, months after Europol’s ‘Operation Endgame‘ that disrupted its operations in May.
- Bumblebee was developed by the TrickBot group and replaced the BazarLoader backdoor in ransomware attacks.
- The malware is distributed through phishing messages and initiates post-exploitation activities, including reconnaissance and credential theft.
- Netskope researchers detected new Bumblebee attacks, which utilize the MSI SelfReg table to execute malicious DLLs directly, making it stealthier.
Read Full Article
25 Likes
Amazon
426

Image Credit: Amazon
How to use interface VPC endpoints to meet your security objectives
- Amazon Virtual Private Cloud (Amazon VPC) endpoints allow establishing private connectivity to supported AWS services using private IP addresses.
- VPC endpoints help achieve four security objectives: implementing networks isolated from the internet, implementing a data perimeter by using VPC endpoint policies, enabling private connectivity to AWS service API endpoints for on-premises environments, and complying with specific compliance requirements.
- Customers can implement a data perimeter by using VPC endpoint policies, allowing access to only trusted entities and resources from a particular network.
- VPC endpoints enables customers to enhance their security posture by establishing private connectivity to supported AWS, enterprise, and third-party services.
- Interface VPC endpoints allow connecting VPC to AWS services in the same region without a NAT instance or Internet Gateway.
- Customers can use interface VPC endpoints to connect AWS services privately, including more than 130 AWS services that are available over AWS PrivateLink.
- Interface VPC endpoints can help in aligning with specific compliance requirements such as GDPR, PCI DSS, and HIPAA.
- VPC Endpoints allow customers to reduce the internet-facing endpoints mitigating risk exposure by reducing the service connectivity surface area.
- Customers can use interface VPC endpoints to enforce a data perimeter, such as only allowing certain accesses of S3 buckets by EC2 instances.
- Customers can use interface VPC endpoints to enable private connectivity to AWS only from their on-premises environments, enforcing data perimeter rules.
Read Full Article
25 Likes
Securityaffairs
26

Image Credit: Securityaffairs
U.S. CISA adds ScienceLogic SL1 flaw to its Known Exploited Vulnerabilities catalog
- The U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds ScienceLogic SL1 flaw CVE-2024-9537 to its Known Exploited Vulnerabilities catalog.
- ScienceLogic SL1 contains a vulnerability related to a third-party component, which has been fixed in certain versions with patches available for older versions.
- Rackspace reported a security breach related to the ScienceLogic EM7 monitoring tool, where a threat actor exploited a zero-day vulnerability in a non-Rackspace utility.
- CISA orders federal agencies to fix the ScienceLogic SL1 flaw by November 11, 2024.
Read Full Article
1 Like
Securityintelligence
166

Image Credit: Securityintelligence
Best practices on securing your AI deployment
- Organizations are adopting generative AI to gain efficiency and productivity gains and to improve innovation in products and services,
- However, securing these AI projects is essential to ensure trustworthy AI - 82% of executives agree but only 24% of generative AI projects are secured,
- Organizations face challenges to securing AI deployment, as generative AI creates a new type of data store that can create new data based on organizational data which can have PII & sensitive information. At the same time, attacks targeting machine learning models have a high propensity to cause risk or damage,
- IBM’s framework for securing AI revolves around securing the data, model, usage and infrastructure. These security efforts should include AI governance frameworks that monitor fairness, bias and drift over time,
- To address securing data, IBM Guardium AI Security allows organizations to identify and fix vulnerabilities in the AI model and protect sensitive data. Organizations have access to the IBM Guardium Data Security Center which empowers security and AI teams to collaborate across the organization through integrated workflows and centralized compliance policies,
- AI security is a collaborative process across cross-functional teams, such as security teams, risk and compliance teams, and AI teams,
- IBM Guardium AI Security helps to continuously monitor for AI misconfiguration, detects data leakage and optimizes access control,
- Securing AI deployment requires organizations to consider regulatory compliance from the data collection and handling phase to model development and inferencing,
- Webinars, such as IBM's Guardium AI Security, help organizations understand how they can implement secure and trustworthy AI projects,
- IBM's Guardium AI Security offers comprehensive and continuous support for organizations to achieve trustworthy AI projects in a safe and reliable manner.
Read Full Article
10 Likes
For uninterrupted reading, download the app