Info. Security News News
Securityaffairs
408

Image Credit: Securityaffairs
VMware failed to fully address vCenter Server RCE flaw CVE-2024-38812
- VMware failed to fully address a remote code execution flaw, tracked as CVE-2024-38812, in its vCenter Server platform.
- The vulnerability is a heap-overflow vulnerability that resides in the implementation of the DCERPC protocol.
- During a hacking contest in China, the flaw was demonstrated, indicating possible exploitation.
- VMware has updated its advisory and released new patches to fully address the vulnerability.
Read Full Article
24 Likes
Amazon
149

Image Credit: Amazon
170 AWS services achieve HITRUST certification
- Amazon Web Services (AWS) has announced that 170 AWS services have achieved HITRUST certification for the 2024 assessment cycle.
- The certification includes 12 services that were certified for the first time.
- Customers can view and download the 2024 HITRUST certification through AWS Artifact.
- AWS HITRUST certification allows customers to inherit controls and deploy solutions to the AWS Cloud with added security and compliance.
Read Full Article
8 Likes
Securityaffairs
167

Image Credit: Securityaffairs
Cisco states that data published on cybercrime forum was taken from public-facing DevHub environment
- Cisco confirms that data published by IntelBroker on a cybercrime forum was taken from the company DevHub environment.
- IntelBroker claimed to have gained access to various Cisco assets, including source code, credentials, customer information, and confidential documents.
- Cisco launched an investigation into the alleged security incident and found no evidence of their systems being compromised.
- Public access to DevHub has been disabled as a precautionary measure while Cisco continues the investigation.
Read Full Article
10 Likes
Infoblox
22

Image Credit: Infoblox
Elevate Your Network: The Power of Infoblox NIOS-X as a Service
- Infoblox NIOS-X as a Service is a modern approach designed to relieve Enterprise IT leaders of the complexities of deploying critical network services.
- NIOS-X as a Service offers an infrastructure-free way to deliver managed critical network services for DNS and DHCP.
- It provides the agility, scalability, reliability, and cost savings that cloud-native technology promises.
- It eliminates the need for physical DDI hardware at branch or office locations, increasing the agility of networking teams.
- Managing these services becomes easy with the Infoblox Portal by providing integrated management of DDI operations, DNS security, and comprehensive logging.
- NIOS-X as a Service empowers businesses to embrace modernization and accelerate their operations.
- NIOS-X Physical Servers and NIOS-X Virtual Servers are also available for local survivability scenarios.
- It simplifies enterprise-grade DDI management making it a cost-effective solution.
- NIOS-X as a Service provides reliability with an impressive 99.999% service uptime.
- Join Infoblox Exchange 2024 to discover game-changing innovations that empower you to tame complexity, eliminate silos, stop threats earlier, and scale elastically across cloud and on-premises infrastructure.
Read Full Article
1 Like
Securityaffairs
17

Image Credit: Securityaffairs
Internet Archive was breached twice in a month
- The Internet Archive was breached again through its Zendesk email support platform.
- Attackers used stolen GitLab authentication tokens to access the Zendesk platform.
- The breach exposed API keys and personal identification documents of users.
- No one has claimed responsibility for the breaches.
Read Full Article
1 Like
Amazon
409

Image Credit: Amazon
How to build a Security Guardians program to distribute security ownership
- This post explains how to build a Security Guardians program similar to AWS Security Guardians that trains, develops, and empowers builder teams to make security decisions about the software that they create.
- The first step to building a successful Security Guardians program is to set the vision, mission, and goals of the program and align them with executive support.
- The next step is to identify developer teams that can pilot the new program and choose Security Guardians who can exhibit well-informed and decisive judgement, advocate for security needs and hold a high-security bar.
- Defining the expected behaviors for Security Guardians, developer, and security teams is important to articulate the measurable behaviors and responsibilities of Security Guardians and how they interact to ensure the successful launch of a secure product.
- Maintaining interest is an important aspect of keeping the Security Guardians engaged along with providing clear training and learning paths and opportunities for career advancement.
- Measuring the success of the program is an important step to verify if the desired outcomes are being achieved and to provide feedback to Security Guardians.
- The best ways to maintain interest and measure success depend on the culture of the organization.
- To develop your own Security Guardians program, contact your AWS account representative to connect with a specialist who can help you develop your program.
- Regularly inspecting the outcomes delivered by the Security Guardians program and making incremental improvements as the program matures is crucial.
- Training individuals to become Security Guardians is one way to distribute security ownership, while another approach is to embed security engineers directly with product development teams.
Read Full Article
24 Likes
Kaspersky
427

Image Credit: Kaspersky
Security and privacy settings in MapMyRun | Kaspersky official blog
- Configuring privacy settings in MapMyRun is essential to protect your personal data and prevent unauthorized access to your location.
- To access privacy settings in MapMyRun, tap the three dots in the bottom right corner for iOS or the three-line menu in the top left corner for Android, then select Settings and choose Privacy.
- In Privacy settings, ensure that Profile Sharing, Route Sharing, and Workout Sharing are set to 'My Friends' or 'Only me' to control who can view your information.
- Additionally, disabling unnecessary push notifications and considering deleting your account if you stop using MapMyRun are recommended steps to enhance privacy.
Read Full Article
25 Likes
Hackingblogs
303
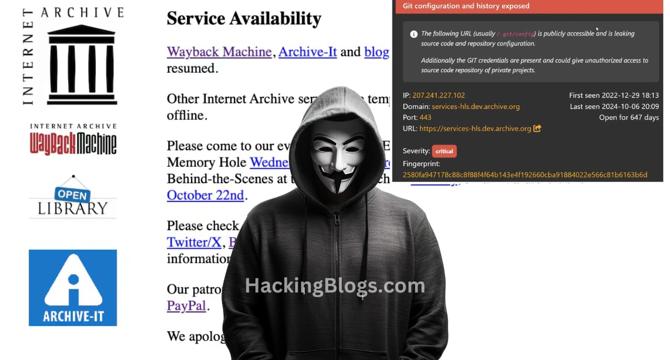
Image Credit: Hackingblogs
Internet Archive Is Hacked Again for the 3rd Time : Stealing exposed GitLab authentication tokens
- Internet Archive has been hacked again, this time through their Zendesk email support platform.
- Hackers exploited a vulnerability caused by Internet Archive's failure to change stolen GitLab authentication credentials.
- 33 million people's personal information was stolen, and a pro-Palestinian group launched a DDoS attack.
- The motive behind the attack appears to be a demonstration of power rather than political or financial gain.
Read Full Article
18 Likes
Schneier
162

AI and the SEC Whistleblower Program
- The U.S. SEC runs a whistleblower program that has paid out over $2 billion
- The program has attracted private for-profit whistleblower firms at the expense of staff at the SEC
- The SEC has paid as much as $279 million to an individual whistleblower – almost one-third of the funding of the agency’s entire enforcement division
- Whistleblower complaints can be used as weapons of corporate warfare, e.g. by rival companies and ransomware groups who threaten to tell the SEC
- The use of AI will increase the number of whistleblowers reporting potential violations, which will decrease the program's efficiency
- AI could lower the cost of whistleblowing firms and increase reliance on a few seasoned, trusted firms
- Firms could use AI to help cover up their own violations by deluging the SEC with legitimate, if minor, tips about potential wrongdoing throughout the industry
- Submitting whistleblower complaints to the SEC will continue to be a viable business model for as long as it remains profitable
- AI is not the solution to the problems created by the runaway growth, but it should give policymakers pause to reconsider the balance of public and private ownership of regulatory enforcement
- The real challenge is to reduce incentives of Tax farming and Whistleblower firms by exploring ways to increase direct government staffing and investment in regulatory enforcement
Read Full Article
9 Likes
Socprime
268

Image Credit: Socprime
Detect Brute Force and Credential Access Activity Linked to Iranian Hackers: The FBI, CISA, and Partners Warn Defenders of Growing Attacks Against Critical Infrastructure Organizations
- Iran-linked adversaries are aimed at stealing credentials and network information, which can be sold to cybercriminals to facilitate further access.
- U.S. state agencies and international partners warns of a surge in credential access and brute-force attacks by Iranian state-sponsored adversaries.
- Iranian-backed hackers are creating significant challenges for the global cybersecurity landscape through persistent attack strategies.
- Adversaries apply multiple brute-force attack techniques and credential access activity to target critical infrastructure organizations.
- Iranian hackers have been employing brute force techniques, including password spraying and MFA “push bombing” to compromise user accounts and gain access to organizations.
- Iranian hackers also leveraged RDP for lateral movement and employed open-source tools and methods like Kerberos SPN enumeration and directory dumps via the Active Directory Microsoft Graph API.
- SOC Prime Platform offers a complete product suite for advanced threat detection, AI-powered detection engineering, and automated threat hunting.
- To mitigate the risks of brute force attacks and credential access operations affiliated with the Iran-backed adversary activity, cyber defenders recommend ensuring IT helpdesk password management follows company policies.
- It is crucial to bolster proactive cyber defense measures against Iranian hackers.
- SOC Prime Platform for collective cyber defense equips progressive organizations with a feasible solution to proactively thwart emerging and existing threats launched by state-sponsored APT groups, ransomware affiliates, and any kinds of attacks.
Read Full Article
16 Likes
Hackersking
356

Image Credit: Hackersking
Can Cybersecurity Hack Your Phone?
- Smartphones are prime targets for cyberattacks due to the vast amount of personal and financial data they store.
- Cybersecurity can ethically hack phones through penetration testing to identify vulnerabilities and strengthen security.
- Methods used by hackers to compromise phones include phishing scams, malware applications, public Wi-Fi attacks, and outdated software.
- To secure your phone, keep software updated, enable two-factor authentication, install trusted security apps, avoid public Wi-Fi without protection, be cautious of suspicious links, and regularly back up your data.
Read Full Article
21 Likes
Securityaffairs
317
Image Credit: Securityaffairs
Unknown threat actors exploit Roundcube Webmail flaw in phishing campaign
- Unknown threat actors have exploited a now-patched vulnerability in the Roundcube webmail software.
- The attack was part of a phishing campaign targeting Roundcube users to steal their credentials.
- The vulnerability, tracked as CVE-2024-37383, allowed for XSS attacks via SVG animate attributes.
- Roundcube Webmail, commonly used by government agencies, continues to be a target for hackers.
Read Full Article
19 Likes
Qualys
171
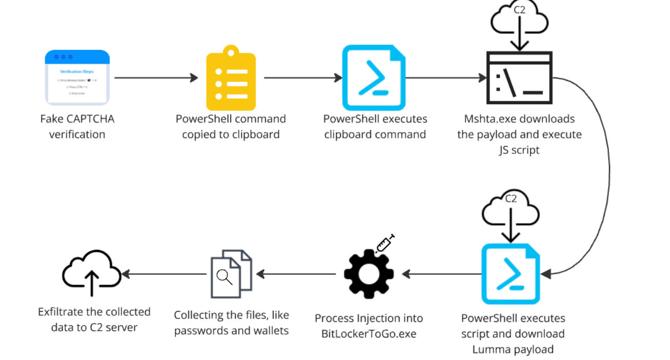
Image Credit: Qualys
Unmasking Lumma Stealer : Analyzing Deceptive Tactics with Fake CAPTCHA
- Lumma Stealer is a Malware-as-a-Service (MaaS) used for stealing sensitive data like passwords, browser information, and cryptocurrency wallet details, using advanced deceptive methods like fake CAPTCHA verification.
- The Qualys Threat Research Unit (TRU) has monitored this active malware campaign. Recently, fake CAPTCHA pages trick unsuspecting users into payload execution, using muti-stage fileless techniques.
- The malware uses PowerShell, mshta.exe and fileless methods to deliver payloads, exploiting common tools and process injection to carry out its operations.
- Qualys EDR identifies and prevents fileless malware attacks at the pre-execution stage, stopping the download of malicious payloads. For instance, it can terminate PowerShell instances to break the chain of initial attack and prevent further payloads' download.
- The IOCs include C2 server domains with the '.shop' top-level domain (TLD) and files like K1.zip, K2.zip and .exe files VectirFree.exe and Voyuer.pif.
- Qualys EDR also allows the viewing of executed obfuscated scripts' de-obfuscated code and detects early prevention crucial in protecting against sensitive data leakage and exfiltration.
- The investigation revealed an evolving threat landscape characterized by the malware’s ability to adapt and evade detection and employs a variety of tactics.
- Analysts can incorporate some threat detection and hunting queries into their playbooks to detect and prevent such threats in real-time effectively.
- The investigation showed Lumma Stealer to be a persistent challenge for security teams, utilizing legitimate software and deceptive delivery methods, and is an ever-evolving threat.
- Qualys EDR detects fileless malware attacks during pre-execution stages and allows for detection and hunting queries to investigate such threats effectively.
Read Full Article
10 Likes
Securityaffairs
216

Image Credit: Securityaffairs
Security Affairs newsletter Round 494 by Pierluigi Paganini – INTERNATIONAL EDITION
- U.S. CISA adds Veeam Backup and Replication flaw to its Known Exploited Vulnerabilities catalog
- North Korea-linked APT37 exploited IE zero-day in a recent attack
- Omni Family Health data breach impacts 468,344 individuals
- Iran-linked actors target critical infrastructure organizations
Read Full Article
13 Likes
Hackersking
35

Image Credit: Hackersking
Can Cybersecurity Track You?
- Cybersecurity primarily aims to protect users from threats like malware, hacking, and data breaches, but some tools can monitor or track user activities in certain situations.
- Encryption, firewalls, antivirus software, and intrusion detection systems are core components of cybersecurity that help safeguard information without directly tracking individuals.
- Network monitoring is a key cybersecurity practice used to observe and analyze traffic within a network, but it mainly focuses on ensuring the security of the entire network.
- EDR tools track activities on endpoint devices to detect and respond to potential threats, but this tracking is primarily focused on detecting and mitigating cyber threats, not invading privacy.
- DLP tools monitor data movement across a network to ensure that confidential information isn't accidentally or maliciously leaked, and the goal is to protect sensitive data.
- UBA tools analyze user behavior to detect abnormal patterns that could signal a cyber threat, but this tracking is aimed at identifying risks and preventing cyber threats, especially insider threats, where someone within the organization poses a danger.
- Privacy regulations impose strict rules on how organizations can monitor and collect personal data. Companies must balance their need to protect data with users' right to privacy.
- Tracking is justified when it’s necessary to protect sensitive data and prevent security breaches, and in such cases, organizations must ensure that tracking is used responsibly and transparently, without compromising personal privacy.
- To safeguard your privacy, you can use a VPN, adjust privacy settings on your devices and accounts, regularly update your software, and only share personal information when absolutely necessary and ensure you’re using secure networks.
- In conclusion, while cybersecurity measures can sometimes track users, the primary goal of these tools is to safeguard networks and prevent cyber threats, not to infringe on personal privacy.
Read Full Article
2 Likes
For uninterrupted reading, download the app