Info. Security News News
Medium
289
Image Credit: Medium
I Know Which Device You Used Last Summer: Fingerprinting WhatsApp Users’ Devices
- WhatsApp's End-to-End Encryption (E2EE) protocol design suffers from some privacy issues in the Multi Device setting revealing information on the user devices.
- The disclosed information may include the devices’ operating system which can allow attackers to gain needed information about their victims.
- WhatsApp exposes-private information about the devices used by its users and does not provide any controls or settings for users to control the exposure.
- The leaked information may allow attackers to gain information such as the number of devices and changes to the setup by monitoring this data over time.
- Firewalls.com defines Operating System (OS) Fingerprinting as a way to identify different operating systems on networked devices.
- WhatsApp-Web-Plus is a popular open-source Chrome Web extension that includes a code helping to identify the sender's operating system.
- The report recommends that WhatsApp use the same message ID generation logic across all platforms and thus eliminate the fingerprinting opportunity altogether.
- Meta, the owner of WhatsApp, did not respond to the reporter's follow-up messages despite being informed of the issue.
- This information leakage may be used by attackers to install malware on their victims' devices and gain access to WhatsApp content.
- The report suggests that WhatsApp's responsiveness to researchers' reports on privacy issues found in its product is lacking and hopes that this attitude will change.
Read Full Article
17 Likes
TechCrunch
44

Image Credit: TechCrunch
Some Americans are still using Kaspersky’s antivirus despite U.S. government ban
- Despite the U.S. government ban on Kaspersky software, some Americans are still using it.
- Motivations range from skepticism about the reasons behind the ban to preferring Kaspersky over rivals.
- Users are getting around the ban by purchasing licenses before the ban and using non-U.S. servers for updates.
- Some users plan to switch to other antivirus software once their Kaspersky licenses expire.
Read Full Article
2 Likes
Infoblox
404

Image Credit: Infoblox
Beware of Domain Collisions: Are Your Internal Domains Registered Externally?
- The DNS landscape was forever changed in the fall of 2013 when ICANN approved over a thousand new gTLDs.
- This opened the door to a new set of security risks for organizations with internal domains on those new gTLDs.
- Malicious actors have been registering internal domains to perform attacks, phish for data, or exploit vulnerabilities.
- Organizations should identify and protect their internal domains registered externally to mitigate risks.
Read Full Article
24 Likes
Siliconangle
48

Image Credit: Siliconangle
Tenable brings intelligent data and AI resource security risk management to the cloud
- Tenable Inc. has added security posture management capabilities for data and artificial intelligence solutions to its Tenable Cloud Security platform.
- The addition of data security posture management (DSPM) and AI security posture management (AI-SPM) will help reduce customer risk of exposure to misconfigurations and vulnerabilities.
- The DSPM and AI-SPM tools provide agentless scanning to discover, classify, and analyze sensitive data in the cloud, with the ability to identify access exposures and provide remediation guidelines.
- The new features are available for all customers of Tenable Cloud Security and Tenable One, the company's exposure management platform.
Read Full Article
2 Likes
Sentinelone
249

Image Credit: Sentinelone
Quantifying Vulnerability Risk | Identify & Remediate CVEs with Exploit-Driven Prioritization
- Over 29,000 new Common Vulnerabilities and Exposures (CVEs) were reported to the National Vulnerability Database (NVD) in 2024, making it impossible for security teams to address every vulnerability.
- Vulnerability prioritization, however, is complex because traditional scoring systems lack critical context about real-world exploitability.
- CISA’s KEV Catalog is a curated list of vulnerabilities that pose immediate and significant risks due to active exploitation.
- The Exploit Prediction Scoring System (EPSS) emphasizes exploitability potential and predicts the likelihood of vulnerabilities being exploited in the near future.
- Integrating CISA’s KEV Catalog with EPSS provides a comprehensive threat landscape view, enabling organizations to prioritize vulnerabilities that pose the most significant threats and streamline remediation efforts.
- SentinelOne has integrated EPSS and CISA’s KEV Catalog support into Singularity Vulnerability Management to streamline prioritization processes, reduce risk exposure, and make more informed decisions about vulnerability remediation.
- Singularity Vulnerability Management has launched a new vulnerability scoring system designed to provide a comprehensive assessment of vulnerabilities by incorporating multiple data sources.
- By incorporating vulnerability intelligence sources, security teams can focus their efforts on vulnerabilities that are not just severe but are likely to be or are already being exploited by attackers.
- Singularity Vulnerability Management helps to allocate resources where they matter most, providing a comprehensive assessment of each vulnerability.
- Organizations can take control with vulnerability management solutions designed to keep ahead of emerging risks, contact SentinelOne today.
Read Full Article
14 Likes
Schneier
213

More Details on Israel Sabotaging Hezbollah Pagers and Walkie-Talkies
- Israeli intelligence agency Mossad, with the help of a former sales representative for a Taiwanese firm, successfully sabotaged Hezbollah pagers and walkie-talkies.
- The pagers were physically assembled in Israel under Mossad oversight, with a hidden explosive component.
- Mossad had remote access to the devices and the explosion could be triggered by a two-step procedure required for viewing secure messages.
- The use of everyday objects as weapons highlights the need for condemning the practice and setting clear public policies.
Read Full Article
12 Likes
Hackersking
53

Image Credit: Hackersking
Can I Do Cybersecurity Without Coding?
- Cybersecurity involves protecting systems, data, and networks from cyberattacks, and many cybersecurity positions do not require coding skills.
- Cybersecurity encompasses areas like risk management, compliance, security analysis, and incident response where coding isn't mandatory.
- Non-coding roles in cybersecurity include cybersecurity analyst, security auditor, governance, risk, and compliance specialist, and incident responder.
- Critical skills for non-coding cybersecurity roles include cybersecurity fundamentals, familiarity with security tools, problem-solving, communication skills, and attention to detail.
- While you don’t need coding skills to start a career in cybersecurity, basic programming languages like Python or JavaScript can be beneficial for roles like penetration testing, vulnerability assessments, and malware analysis.
- Steps to start a career in cybersecurity without coding include earning relevant certifications, gaining practical experience, staying informed, and networking.
- Staying up-to-date with industry trends is essential in cybersecurity, where many non-coding positions are available focusing on strategy, risk management, and incident response.
- Developing key skills like cybersecurity fundamentals, familiarity with security tools, problem-solving, communication skills, and attention to detail can help build a successful career in cybersecurity without ever writing a line of code.
- The cybersecurity field is constantly evolving, so finding the role that fits your strengths is the key to building a fulfilling career in protecting data and networks.
Read Full Article
3 Likes
Hackersking
333
Image Credit: Hackersking
Katana : The Powerful tool for Web Crawling
- Katana is a powerful tool for web crawling and security scanning.
- It offers fast and customizable web crawling capabilities, including JavaScript parsing and automatic form filling.
- Katana supports different input methods and provides flexible output options.
- Users can control the crawl scope and choose between standard mode and headless mode for more complex applications.
Read Full Article
20 Likes
Hackingblogs
276
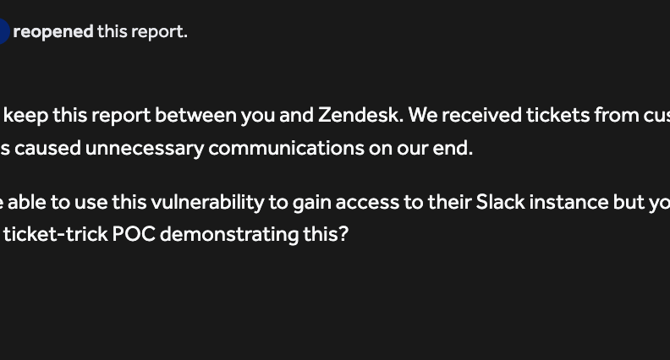
Image Credit: Hackingblogs
A 15 Year Old Hacker Found Critical Bug On Zendesk Worth $50,000+ Bounty
- A 15-year-old hacker named Daniel found a critical bug in Zendesk.
- The bug allowed anyone to view customer service tickets from any business using Zendesk.
- Daniel reported the bug to Zendesk's bug bounty program but received a poor response initially.
- He escalated the issue and eventually earned over $50,000 in bounties from various companies.
Read Full Article
16 Likes
Hackersking
165

Image Credit: Hackersking
Free White Rabbit Neo AI For Penetration Testing and Hacking
- White Rabbit Neo AI is a free, AI-driven tool designed for penetration testing and hacking.
- It automates the penetration testing process and offers features like vulnerability scanning, automated exploit generation, customizable attack scenarios, real-time reporting, and Kali Linux integration.
- The tool is accessible to anyone interested in cybersecurity and penetration testing, and it is praised for its speed, accuracy, cost-efficiency, and continuous learning abilities.
- White Rabbit Neo AI has practical applications in bug bounty hunting, red teaming, and small to medium businesses for security audits.
Read Full Article
9 Likes
Infoblox
302

Image Credit: Infoblox
Unveiling Network Clarity: The Brilliance of Infoblox Universal Asset Insights
- Infoblox Universal Asset Insights automates the discovery and analysis of assets across major public clouds, on-premises networks, and IoT/OT devices providing detailed and near-real-time visibility into network assets.
- The fragmented approach of critical network service management in hybrid and multi-cloud environments, partner networks, and devices leads to increased operational inefficiencies and exposure to security risks.
- Organizations without a complete list of assets to track are at risk for security breaches, network management inefficiencies and additional time spent on troubleshooting activities.
- Automated discovery process is designed to capture every type of device, ranging from traditional servers and workstations to modern IoT and OT devices which ensures that no asset goes unnoticed or overlooked.
- The monitors can identify zombie assets by confidence level, unregistered assets with missing records, and non-compliant assets, enabling teams to find and act on potential issues or vulnerabilities.
- Universal Asset Insights streamlines critical network services management and offers a clear, comprehensive view of your hybrid multi-cloud network.
- Universal Asset Insights offers unparalleled cloud visibility, a critical benefit for modern organizations operating in multi-cloud environments.
- Universal Asset Insights is instrumental in enhancing organizational security by carefully identifying and categorizing all network devices, including unmanaged and non-compliant ones.
- With Universal Asset Insights, you gain clarity, efficiency, and peace of mind.
- Infoblox Universal Asset Insights cover on-premises networks, private and public clouds, IoT devices, and OT environments which makes it the first solution to combine such extensive capabilities in one package.
Read Full Article
18 Likes
Socprime
14

Image Credit: Socprime
Earth Simnavaz (aka APT34) Attack Detection: Iranian Hackers Leverage Windows Kernel Vulnerability to Target UAE and Gulf Region
- Iranian hackers, known as Earth Simnavaz APT or APT34, are targeting organizations in the UAE and Gulf regions.
- They are using advanced backdoor strains to exploit Microsoft Exchange servers and steal login credentials.
- These hackers are also exploiting a new critical Windows Kernel vulnerability (CVE-2024-30088) for privilege escalation.
- Security experts recommend using SOC Prime Platform and detection rules to detect and prevent these attacks.
Read Full Article
Like
Kaspersky
369

Image Credit: Kaspersky
Docusign-themed phishing emails | Kaspersky official blog
- Phishing emails impersonating Docusign, the world’s most popular e-signature service are currently being used by cybercriminals in phishing campaigns.
- The victim is notified that they need to electronically sign a document usually a financial one the exact purpose of which isn’t entirely clear from the text which tricks users into opening a phishing website, often on mobile devices where phishing URLs are harder to detect.
- This phishing email may or may not mention Docusign but the aim is same - usernames and passwords harvested through successful phishing attacks are often compiled into databases sold on the dark web.
- The actual process of signing a document with Docusign for the regular user is simplicity itself.
- According to Kaspersky, attackers rely on the victim not understanding how e-signing with Docusign actually works. The inattentive victim follows the link (or QR code) to the phishing page and enters their work login credentials.
- How to guard against phishing: filtering out suspicious and unwanted email at the gateway level — our comprehensive solution Kaspersky Security for Mail Servers will do this for you.
- Protecting endpoints from phishing redirects with Kaspersky Small Office Security or Kaspersky Next — depending on the size of your organization.
- Raising employee awareness of cyberthreats with specialized training. Such training is easy to deliver using our educational Kaspersky Automated Security Awareness Platform.
Read Full Article
22 Likes
Securityaffairs
187
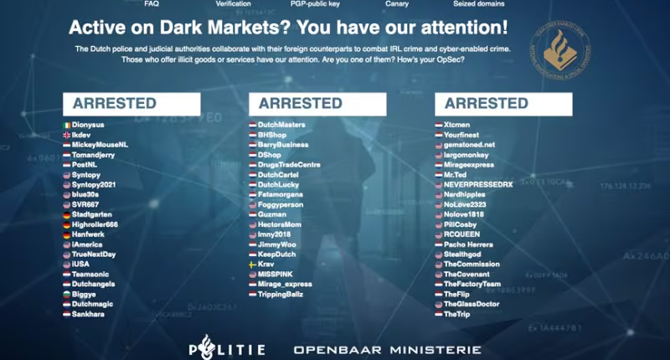
Image Credit: Securityaffairs
Dutch police dismantled dual dark web market ‘Bohemia/Cannabia’
- Dutch police dismantled Bohemia/Cannabia, two major dark web markets for illegal goods, drugs, and cybercrime services.
- Law enforcement agencies from the UK, US, and Ireland participated in the operation.
- Bohemia had 82,000 daily ads, 67,000 monthly transactions, and a turnover of €12 million in September 2023.
- The police arrested several Dutch dealers and identified administrators, seizing €8 million worth of cryptocurrency.
Read Full Article
11 Likes
Securityaffairs
200

Image Credit: Securityaffairs
Fidelity Investments suffered a second data breach this year
- US-based financial services company Fidelity Investments is notifying 77,099 individuals of a data breach.
- The breach occurred on August 17, 2024, and was discovered on August 19, 2024.
- Compromised information includes names, Social Security numbers, financial account data, and driver's license information.
- Fidelity Investments offers impacted individuals 24 months of free credit monitoring and identity restoration services.
Read Full Article
12 Likes
For uninterrupted reading, download the app