Info. Security News News
Securityaffairs
4

Image Credit: Securityaffairs
DragonForce operator chained SimpleHelp flaws to target an MSP and its customers
- Sophos reports that a DragonForce ransomware operator exploited three vulnerabilities in SimpleHelp software to target a managed service provider.
- The vulnerabilities in SimpleHelp software (CVE-2024-57727, CVE-2024-57728, and CVE-2024-57726) allowed attackers to gain initial access and carry out various malicious activities.
- These vulnerabilities enabled unauthorized downloading and uploading of files, remote code execution, and privilege escalation, posing a serious security risk to customer machines.
- Arctic Wolf observed a campaign targeting SimpleHelp servers utilizing the disclosed vulnerabilities. Sophos identified an attacker using a legitimate SimpleHelp tool from an MSP to access client networks and extract sensitive information.
Read Full Article
Like
Amazon
376

Image Credit: Amazon
How to use the new AWS Secrets Manager Cost Allocation Tags feature
- AWS Secrets Manager is a service for managing, retrieving, and rotating credentials and secrets throughout their lifecycles.
- The new AWS Secrets Manager Cost Allocation Tags feature allows for better visibility and control over costs.
- Cost allocation tags can be used to categorize and track costs by assigning key-value pairs to AWS resources.
- The process involves creating, attaching, activating tags, filtering them in Cost Explorer, and creating cost categories.
- By using cost allocation tags, users can break down Secrets Manager costs by various dimensions for improved cost allocation.
- The feature enables itemized usage tracking in Cost Explorer and cost and usage reports.
- Steps include creating user-defined tags, assigning them to secrets, and activating them in the AWS Billing console.
- AWS CLI can also be used to create and activate tags for cost allocation purposes.
- After activation, users can view usage and charges by tags in Cost Explorer for detailed insights.
- The feature allows for better cost allocation across departments and organizations, enhancing cost visibility and management.
Read Full Article
22 Likes
Amazon
321

Image Credit: Amazon
Elevate your AI security: Must-see re:Inforce 2025 sessions
- AWS re:Inforce 2025 offers security experts and industry leaders addressing challenges and opportunities in generative AI security.
- Sessions cover topics like data protection, model security, identity management, and AI agent resilience.
- Attendees can learn from AWS security experts, successful customers, and industry-leading partners.
- Innovation Talks by top AWS executives discuss advancements in generative AI and cloud security strategies.
- Breakout sessions, chalk talks, and lightning talks provide in-depth insights and practical knowledge.
- Interactive sessions like builders' sessions, code talks, and workshops offer hands-on learning experiences.
- Topics range from incident response, threat modeling, compliance, to building secure AI agents using AWS services.
- Register for re:Inforce 2025 to learn from experts and discover strategies for securing AI implementations.
- Speakers include AWS security specialists like Margaret Jonson and Matt Saner, offering valuable industry insights.
Read Full Article
19 Likes
VentureBeat
300

Image Credit: VentureBeat
What Salesforce’s $8B acquisition of Informatica means for enterprise data and AI
- Salesforce announced an $8B acquisition of Informatica, aiming to enhance its data foundation for deploying agentic AI.
- Informatica, a data-focused vendor founded in 1993, has evolved with cloud, SaaS, and generative AI offerings.
- Salesforce's previous acquisitions like Slack and Tableau have proven successful, expanding its capabilities.
- The Informatica acquisition fills a gap in Salesforce's data management capabilities, elevating its position in data management.
- The integration of data and AI is crucial for AI-ready enterprises, as seen in this acquisition.
- Salesforce aims to deliver a unified customer data fabric for AI and analytics with this move.
- The intersection of data and agentic AI makes Informatica appealing to Salesforce.
- Informatica brings updated and comprehensive data management capabilities, complementing Salesforce's portfolio.
- Salesforce's acquisition grants strength in metadata and data cataloging for agentic AI workflows.
- Customers of both Salesforce and Informatica can expect faster, more innovative, and personalized experiences at scale.
Read Full Article
18 Likes
Amazon
203

Image Credit: Amazon
Navigating the threat detection and incident response track at re:Inforce 2025
- AWS re:Inforce 2025 is an upcoming event focusing on cloud security, offering over 250 sessions across various security topics.
- The threat detection and incident response track at the event covers topics like unified cloud security, vulnerability management, threat intelligence, and more.
- Key sessions within this track include innovations in AWS detection and response, multi-stage threat detection using GuardDuty and MITRE, and building secure generative AI security tools.
- Breakout sessions and chalk talks provide insights on scaling threat intelligence, vulnerability management using Amazon Inspector, and enterprise security strategies like SAP's AWS Blueprint.
- Interactive sessions and workshops offer hands-on experiences in threat detection, incident response, and securing container workloads using AWS security services.
- The focus on generative AI and security aims to streamline security operations and enhance threat detection capabilities.
- Attendees can participate in workshops like the AWS Security Incident Response Challenge and learn about active defense strategies using AWS AI/ML services.
- The event aims to equip participants with the latest best practices in threat detection and incident response to effectively manage workloads and applications on AWS.
- Nisha Amthul, a Senior Product Marketing Manager, specializes in detection and response solutions at AWS Security.
- Nisha enjoys cake decorating, strength training, and spending time with her kids outside of work.
- Register today to join the re:Inforce event in Philadelphia and stay updated on cloud security best practices.
Read Full Article
12 Likes
Qualys
228
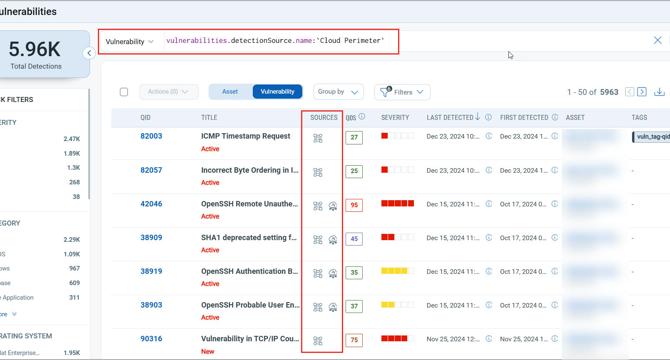
Image Credit: Qualys
Eliminate Risk with Precision: Introducing Vulnerability Detection Sources in VMDR
- The introduction of Vulnerability Detection Sources in Qualys VMDR aims to provide precise insights to eliminate risks efficiently.
- Understanding the source of vulnerability detection is crucial for better context, prioritization, and remediation efforts.
- VMDR's feature reveals where each vulnerability was identified, improving root cause analysis and targeted actions.
- TruRisk Score integration enhances risk prioritization, emphasizing external threats that require immediate attention.
- Detection source visibility includes Cloud Agent, perimeter scans, internal scanners, and more supported methods.
- Enhanced visibility allows grouping vulnerabilities by detection source for focused remediation.
- New search tokens and API access enable detailed tracking of vulnerability lifecycles and custom reporting.
- Vulnerability Detection Sources feature facilitates smarter decision-making, improved remediation, and reduced attack surface.
- TruRisk Eliminate strategy goes beyond traditional patching to proactively address threats and exploit vulnerabilities.
- Policy Audit support with detection source visibility enhances compliance control failure identification and corrective actions.
Read Full Article
13 Likes
Securityaffairs
46

Image Credit: Securityaffairs
Russia-linked APT Laundry Bear linked to 2024 Dutch Police attack
- A new Russia-linked APT group known as Laundry Bear has been linked to a security breach at Dutch police in September 2024.
- The breach exposed officers' work-related contact details, prompting the Dutch police to implement security measures and report the incident to the Data Protection Authority.
- The Dutch intelligence services blamed a 'state actor' for the breach and issued a joint advisory warning organizations about Laundry Bear attacks, highlighting the group's evasion tactics.
- Laundry Bear has targeted Western governments, defense contractors, cultural groups, and digital service providers since 2024, focusing on entities connected to Russia's war in Ukraine.
Read Full Article
2 Likes
Socprime
143
Image Credit: Socprime
AI-Powered SPL Rule Generation for WRECKSTEEL IOC Detection
- Uncoder AI converts complex threat intelligence into Splunk’s Search Processing Language (SPL) for direct deployment in security analytics workflows.
- It parses IOC-rich reports to generate multi-index SPL queries aligned with Splunk’s native event and network telemetry.
- Uncoder AI automates the correlation of IOC strings with telemetry sources, detects PowerShell cradle activity, and streamlines Splunk rule authoring for rapid threat rule deployment.
- Operational value includes rapid threat rule deployment, enhanced behavioral and IOC coverage, and the ability to uncover historical matches across environments by deploying AI-converted SPL.
Read Full Article
8 Likes
Socprime
93

Image Credit: Socprime
BadSuccessor Detection: Critical Windows Server Vulnerability Can Compromise Any User in Active Directory
- A critical security vulnerability in Windows Server 2025, known as BadSuccessor, allows attackers to gain control over any Active Directory user account.
- This vulnerability exploits the delegated Managed Service Account (dMSA) feature and can lead to complete domain control by attackers.
- Security professionals can detect BadSuccessor attacks using detection rules available on the SOC Prime Platform with AI-powered detection engineering and threat hunting capabilities.
- The BadSuccessor vulnerability poses a significant threat to Active Directory environments and could enable lateral movement and devastating attacks like ransomware.
- Exploiting dMSAs in Windows Server 2025 allows attackers to escalate privileges and gain control over high-privilege accounts, such as Domain Admins.
- The vulnerability impacts a wide range of AD-dependent organizations, with 91% of environments analyzed found to be susceptible.
- By manipulating dMSAs, attackers can exploit the BadSuccessor vulnerability to take over an entire domain without traditional administrative restrictions.
- Despite Microsoft's acknowledgment of the issue, there is currently no official patch available for BadSuccessor, emphasizing the need for organizations to restrict dMSA creation rights and tighten permissions.
- To mitigate risks, Akamai has provided a PowerShell script on GitHub to identify users with dMSA creation rights.
- Organizations are advised to leverage the SOC Prime Platform for comprehensive threat detection and mitigation against BadSuccessor and other emerging cyber threats.
Read Full Article
5 Likes
Kaspersky
360

Image Credit: Kaspersky
The ChoiceJacking attack: stealing smartphone photos and data while charging via USB | Kaspersky official blog
- Smartphone data can be accessed or erased when charging via public USB ports due to potential JuiceJacking or ChoiceJacking attacks.
- ChoiceJacking attacks bypass safeguards by tricking victims into authorization for data transfer during charging.
- Various methods of ChoiceJacking attacks target different smartphone models and OS versions.
- Apple and Google have patched these vulnerabilities in their recent OS updates to require biometric authentication for USB data transfer confirmation.
- Users are advised to connect their phones only to trusted chargers, use USB data blockers, update to the latest OS versions, and be cautious while using public charging stations.
- Using USB data blockers or charge-only cables can protect against unauthorized data access during charging but may impact charging speed.
- Law enforcement agencies have warned about USB data theft attacks, urging users to take precautions when charging devices in public places.
- Remaining vigilant while charging and selecting 'Charging only' when prompted for connection type can help prevent data theft via USB charging ports.
- It is recommended to update to the latest Android or iOS versions to stay protected against potential USB data theft attacks.
- Considering the risks, it is important to be cautious and take necessary steps to secure your data while charging your smartphone in public locations.
Read Full Article
21 Likes
Socprime
72

Image Credit: Socprime
AI-Generated SentinelOne DNS Query for WRECKSTEEL Detection
- Uncoder AI simplifies threat detection in SentinelOne by converting raw intelligence into executable event queries for targeting WRECKSTEEL campaign.
- The AI focuses on malicious indicators like domains and URLs, transforming them into a single EventQuery to detect DNS lookups within the SentinelOne console.
- The SentinelOne DNS query targets known C2 domains and cloud delivery services, using a language-aware approach to improve detection accuracy and automate query construction.
- This innovation by Uncoder AI streamlines the process for SOC teams using SentinelOne, enabling rapid deployment of DNS-based threat indicators and enhancing detection fidelity against campaigns like WRECKSTEEL.
Read Full Article
4 Likes
Socprime
55
Image Credit: Socprime
AI-Powered IOC Parsing for WRECKSTEEL Detection in CrowdStrike
- Uncoder AI automates the decomposition of complex IOC-driven detection logic authored in CrowdStrike Endpoint Query Language (EQL), focusing on detecting WRECKSTEEL, a PowerShell-based infostealer.
- Key components in the EQL rule include tracking event IDs, process & scripting engine detection, network IOCs, file & script artifacts, and command-line IOC matching for identifying malicious behavior.
- Uncoder AI simplifies the understanding of complex detection rules by automatically extracting logic branches, annotating components, and grouping indicators by execution phase, making rules readable and auditable.
- For detection engineers and threat intel teams in CrowdStrike, Uncoder AI offers accelerated rule auditing, precise mapping of IOCs to telemetry, and optimized rule adaptation for proactive threat detection at scale.
Read Full Article
3 Likes
Socprime
72

Image Credit: Socprime
IOC-to-Query Conversion for SentinelOne in Uncoder AI
- Uncoder AI automates IOC extraction from threat reports, identifying malicious domains linked to phishing and data exfiltration.
- It generates SentinelOne-compatible queries using DNS in contains anycase syntax for efficient threat detection.
- The feature provides operational benefits to SentinelOne users, enabling faster threat hunting and immediate IOC enforcement.
- By leveraging Uncoder AI, analysts can streamline their response time and enhance SOC efficiency in detecting APT infrastructure.
Read Full Article
4 Likes
Securityaffairs
356
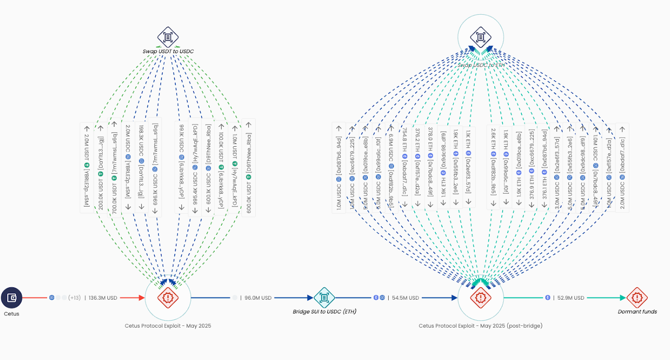
Image Credit: Securityaffairs
Crooks stole over $200 million from crypto exchange Cetus Protocol
- Cetus Protocol suffered a $223 million crypto theft and is willing to drop legal action if the stolen funds are returned.
- The platform was paused as the investigation confirmed the cyber heist last week.
- $162 million of the compromised funds have been successfully paused, and recovery efforts are underway with the Sui Foundation.
- The hack was due to a vulnerable package but has since been fixed, with the company offering a $5 million bounty for tips to identify the attacker.
Read Full Article
21 Likes
Securityaffairs
216
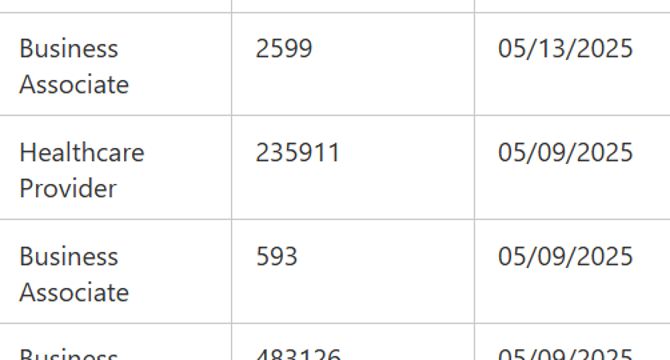
Image Credit: Securityaffairs
Marlboro-Chesterfield Pathology data breach impacted 235,911 individuals
- SafePay ransomware attacked Marlboro-Chesterfield Pathology, compromising personal data of 235,000 individuals.
- The breach occurred on January 16, 2025, leading to the unauthorized access of internal systems.
- Stolen information included names, addresses, birth dates, medical treatment details, and health insurance data.
- Marlboro-Chesterfield Pathology notified the US Department of Health and Human Services about the breach affecting 235,911 people.
Read Full Article
13 Likes
For uninterrupted reading, download the app