Info. Security News News
Dataprivacyandsecurityinsider
211

When Satire Meets Statute: The Onion’s VPPA Class Action
- A Video Privacy Protection Act (VPPA) class action lawsuit has been filed against Global Tetrahedron, LLC, the owner of The Onion, alleging improper installation of Meta Pixel for tracking users' video consumption habits.
- The complaint states that Meta Pixel collects user data and transmits personally identifiable information to Meta, including the user's browsing activity and Facebook user ID.
- The lawsuit creatively uses screenshots of a ChatGPT conversation to show how an average user can understand the data being disclosed to Meta by inspecting website network traffic using developer tools.
- This case highlights the growing trend in VPPA litigation targeting third-party tracking technologies on websites with video content, potentially increasing risk for publishers offering video streaming services.
Read Full Article
12 Likes
Dataprivacyandsecurityinsider
296

Is Your Website a Legal Target? Why Chatbots, Cookies + AdTech Are Drawing Lawsuits Under an Old California Law
- The California Invasion of Privacy Act (CIPA) from 1967 is being used in lawsuits targeting businesses over alleged privacy violations related to digital website tools like chatbots, website analytics, ad tracking, and social media plugins.
- Plaintiffs argue that modern technologies like cookies, IP address collection, session replays, and chatbots violate CIPA by acting as modern-day forms of wiretapping and surveillance devices.
- To avoid such claims, businesses are advised to update their privacy policies, provide clear notice and obtain consent for tracking technologies, review chat tools for data handling disclosures, and carefully vet third-party vendors for compliance.
- This wave of privacy litigation under CIPA signifies a broader trend impacting the ad tech ecosystem, urging businesses to prioritize privacy, transparency, and proactive measures to mitigate legal risks.
Read Full Article
17 Likes
Dataprivacyandsecurityinsider
111

State Lawmakers Oppose Proposed 10 Year Freeze on AI Laws + Regulations
- A bipartisan group of 260 state lawmakers oppose a proposed ten-year freeze on any state or local regulation of artificial intelligence (AI) as part of the tax and budget reconciliation bill.
- The lawmakers express strong opposition to the provision in the bill, stating that it would undermine ongoing state efforts to address the impact of AI and cut short democratic discussion on AI policy.
- The preemption of state laws on AI regulation threatens to wipe out existing state laws that protect consumers and address pressing digital issues. State legislators have made significant efforts to protect constituents from AI-related harms.
- The proposed federal moratorium on AI policy is criticized as paternalistic and contradictory to the idea of allowing states to legislate for their citizens. The letter urges constituents to call their members of Congress to reject provisions that preempt state and local AI legislation.
Read Full Article
6 Likes
Dataprivacyandsecurityinsider
331

DJI Says “Bring It On” to U.S. Drone Security Scrutiny
- DJI, the world’s largest drone manufacturer, is embracing the prospect of tighter U.S. restrictions on Chinese drone companies.
- The Trump administration is finalizing orders that may require companies like DJI to undergo national security reviews before selling new drones in the U.S.
- DJI has a track record of passing security audits, but faces scrutiny with Section 1709 of the FY2025 NDAA potentially impacting its market access.
- DJI has introduced features like Local Data Mode and third-party software compatibility to address data privacy concerns and emphasizes transparency amidst legal challenges.
Read Full Article
19 Likes
Dataprivacyandsecurityinsider
250

Privacy Tip #446 – Department of Motor Vehicles Warns Drivers About Smishing Text Surge
- Scammers are sending smishing text messages pretending to be from the Department of Motor Vehicles across the country.
- The messages contain false threats of license suspension, fines, and legal penalties to trick recipients into clicking on malicious links and sharing personal or financial information.
- The Rhode Island Division of Motor Vehicles issued an alert warning about one of these messages claiming to be a 'final notice' from the DMV, which includes fake legal codes and links to fraudulent websites.
- Tips to avoid falling victim to these scams include not clicking on links or replying to suspicious texts, not providing personal or financial information, and reporting fraudulent messages to authorities.
Read Full Article
15 Likes
Socprime
304
Image Credit: Socprime
IOC-to-CSQL Detection for Gamaredon Domains
- The feature in Uncoder AI translates threat intelligence into CrowdStrike CSQL for immediate use in Falcon Endpoint Search.
- AI-driven rules are dynamically generated by Uncoder AI, utilizing field mapping and syntax expectations to create effective detection queries.
- Uncoder AI validates queries in real-time for correct syntax, grouping, and use of operators to prevent errors and ensure safe deployment in production.
- By automating query structure and syntax validation, Uncoder AI simplifies the process for detection engineers to identify and validate Gamaredon domains efficiently.
Read Full Article
18 Likes
Socprime
231

Image Credit: Socprime
AI-Validated Hostname Filtering for Chronicle Queries
- Uncoder AI can analyze and validate Chronicle UDM queries involving multiple domain-based conditions.
- The platform automatically identifies the detection logic using field-level comparison on target.hostname.
- Uncoder AI provides real-time, AI-powered validation and optimization for Chronicle queries, reducing manual efforts.
- This feature enables faster detection engineering, higher confidence in query quality, and improved performance readiness for security teams in Google SecOps environments.
Read Full Article
13 Likes
Socprime
324
Image Credit: Socprime
AI-Assisted Domain Detection Logic for Carbon Black in Uncoder AI
- Uncoder AI feature enables instant creation of detection queries for VMware Carbon Black Cloud using structured threat intelligence.
- AI automates both IOC extraction and the detection rule generation, understanding the required schema for Carbon Black to map threat intel into platform-specific syntax.
- Unique live AI-driven validation of query syntax ensures correct usage of field-value pairs, operators, and schema alignment to reduce misconfiguration chances.
- Operational benefits include accelerating query creation for known adversary infrastructure, reducing errors, enabling proactive threat hunting, and improving consistency of query formatting.
Read Full Article
19 Likes
Socprime
108
Image Credit: Socprime
URL-Based IOC Validation for Microsoft Defender KQL
- Uncoder AI demonstrates how to validate URL-based detection logic for Microsoft Defender for Endpoint using KQL.
- The KQL query filters events by the RemoteUrl field and matches against attacker-controlled URLs linked to malicious activities.
- Uncoder AI automates the validation process, ensuring syntax accuracy, field existence, and performance considerations in KQL queries.
- Operational benefits include accurate threat filtering, optimized detection design, and SOC-ready validation before deployment.
Read Full Article
6 Likes
Kaspersky
313

Image Credit: Kaspersky
Commercial vs. open-source SIEM: pros and cons | Kaspersky official blog
- Open-source solutions are commonly used in the IT market, including for building SIEM systems.
- Setting up a SIEM system using open-source tools like Logstash, Elasticsearch, and Kibana offers flexibility and cost savings.
- Building a custom OSS SIEM requires time, specialized skills, and ongoing support from a dedicated team.
- Implementing a self-built SIEM or OSS solution can significantly extend the time to deliver real value compared to ready-made solutions.
- Shortages in specialized skills for high-load system design and content creation can be a challenge for SIEM builders.
- Compliance efforts are more demanding for self-built SIEMs compared to commercial solutions with built-in certification processes.
- Vendor lock-in and employee dependence are key considerations when deciding between open-source and commercial SIEM solutions.
- Open-source SIEMs may offer simplicity in customization but can lead to higher long-term total cost of ownership due to maintenance expenses.
- Commercial SIEM solutions provide regular updates, threat intelligence feeds, and support, reducing the burden on in-house security teams.
- Choosing an open-source SIEM involves careful evaluation of hardware costs and architectural decisions that can impact operational expenses.
Read Full Article
18 Likes
Qualys
116

Image Credit: Qualys
Ensure PCI 4.0 Readiness with File Integrity Monitoring for Containers
- PCI DSS 4.0 introduces stricter requirements for vulnerability management and file integrity monitoring (FIM) in dynamic environments like Kubernetes and containerized workloads.
- Compliance is now a continuous operational requirement under PCI 4.0, emphasizing the need for real-time monitoring of sensitive file changes across all environments.
- Qualys addresses the challenge of file integrity monitoring (FIM) in containers and bridges the gap to stay continuously audit-ready for PCI DSS 4.0.
- Traditional FIM approaches fall short in containers due to lack of real-time coverage, siloed monitoring tools, high operational overhead, and limited audit visibility.
- Qualys Runtime FIM for Containers offers seamless, scalable, and real-time monitoring solutions leveraging eBPF technology to ensure continuous visibility and unified coverage.
- Qualys FIM provides actionable insights, automated reporting for audit-readiness, and ensures compliance needs are met with out-of-the-box policies, reducing audit overhead.
- Qualys helps organizations simplify PCI DSS compliance for containers, offering real-time tracking, agility in modernized applications, reduced compliance gaps, and audit-ready reports.
- Moving beyond FIM, Qualys focuses on continuous audit confidence by mapping data to compliance frameworks, automating evidence collection, and streamlining workflows across ITSM, GRC, and SecOps.
- Qualys Runtime FIM for Containers enhances visibility, unifies risk and compliance posture, and provides automated insights, making compliance a smart, scalable, and cost-effective aspect of security.
- Qualys Runtime FIM for Containers is a catalyst for continuous audit confidence, offering visibility between scans, unified risk posture, automation, and reduced time and cost.
- Take control of compliance with Qualys Runtime FIM for Containers to ensure continuous audit confidence, smart security, and cost-effective solutions.
Read Full Article
6 Likes
Socprime
11

Image Credit: Socprime
CVE-2025-20286 Vulnerability Exploitation: Critical Cisco ISE Flaw Affects AWS, Microsoft Azure, and OCI Cloud Deployments
- Critical vulnerability (CVE-2025-20286) in Cisco's Identity Services Engine (ISE) allows unauthenticated remote attackers to exploit sensitive information and perform admin actions on cloud platforms like AWS, Azure, and OCI.
- Over 20,000 vulnerabilities disclosed in June 2025, emphasizing the need for enhanced cybersecurity vigilance to combat increasing cyber threats and zero-day vulnerabilities.
- Cisco has issued security updates to address the critical ISE vulnerability (CVE-2025-20286), which affects cloud deployments on AWS, Azure, and OCI, enabling unauthorized access and limited administrative actions.
- Mitigation measures include using Cloud Security Groups, IP-based access control, and resetting credentials, with a hotfix available for ISE versions 3.1 to 3.4, urging users to address the flaw promptly to mitigate risks.
Read Full Article
Like
Hackers-Arise
343

Image Credit: Hackers-Arise
Signal Intelligence with a Software Defined Radio (SDR): The Quiet Revolution in Cybersecurity and Cyberwarfare
- Software-Defined Radio (SDR) has revolutionized communication and warfare, impacting military operations and satellite communications.
- Modern military drones like the Turkish Bayraktar TB2 and American MQ-9 Reaper utilize advanced multi-band SDR systems for enhanced capabilities.
- SDR technology allows drones to operate in multiple frequency ranges simultaneously and switch between channels seamlessly.
- The SDR systems in military drones enable features like encrypted communication links, electronic warfare capabilities, and precision attacks.
- Satellite communication systems are vulnerable to various threats, including signal interception, physical layer attacks, and command infrastructure attacks.
- Recent security incidents like the Viasat hack have prompted improvements in satellite communication security measures.
- Artificial intelligence and machine learning are being utilized in satellite security to detect and respond to evolving threats efficiently.
- SDR technology is evolving to provide better protection against jamming and interference, adapting to changing threat environments.
- The increasing role of AI, quantum computing, and SDR technology is reshaping how we interact with the electromagnetic spectrum.
- The SDR revolution offers new possibilities in cybersecurity and cyberwarfare, showcasing its potential in modern military and civilian applications.
Read Full Article
20 Likes
Securityaffairs
89

Image Credit: Securityaffairs
Law enforcement seized the carding marketplace BidenCash
- U.S. and Dutch authorities collaborated to dismantle the BidenCash cybercrime marketplace by seizing 145 associated domains.
- The U.S. Department of Justice announced the seizure of 145 darknet and clear web domains, along with cryptocurrency funds linked to BidenCash.
- BidenCash, operational since March 2022, charged a fee for transactions and distributed millions of stolen payment cards, generating around $17 million in revenue.
- Authorities shut down 145 domains related to BidenCash, redirecting them to law enforcement servers to prevent further criminal activities.
Read Full Article
5 Likes
Securityaffairs
240
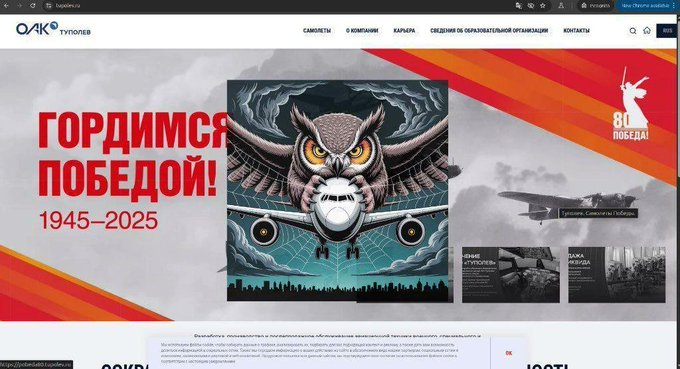
Image Credit: Securityaffairs
Ukraine’s military intelligence agency stole 4.4GB of highly classified internal data from Tupolev
- Ukraine’s military intelligence agency GUR hacked the Russian aerospace and defense company Tupolev, stealing 4.4GB of highly classified internal data.
- The breach exposed internal communications, staff details, engineers' resumes, procurement records, and confidential meeting minutes.
- Ukrainian intelligence source stated that nearly all of Tupolev's secrets are now exposed, impacting Russia's strategic aviation operations.
- Ukraine's GUR had monitored Tupolev's internal flow for months, defacing Tupolev's website symbolically and targeting Russia's defense industry.
Read Full Article
14 Likes
For uninterrupted reading, download the app