Info. Security News News
Hackersking
45

Image Credit: Hackersking
Indown.io: The Ultimate Tool for Downloading Videos Online Instantly
- Indown.io is an online tool that allows users to effortlessly download videos from various social media platforms without the need to install apps or register for an account.
- This tool supports multiple platforms including Instagram, Facebook, TikTok, Twitter, and YouTube, and provides high-quality downloads in HD and SD formats.
- Indown.io is fast, lightweight, mobile-friendly, and doesn't require any registration, making it convenient for users to save videos.
- Users can simply copy the video URL, paste it on Indown.io, select the download option, choose the preferred video resolution or format, and save the video to their device.
- In terms of safety, Indown.io is ad-free and safe for personal use, but users should follow copyright policies to ensure ethical usage.
- Users appreciate Indown.io for being a free service, not requiring software installation, operating on all platforms, and providing fast download speeds.
- Some alternatives to Indown.io include SnapSave, SaveFrom, Y2Mate, and SSSTikTok, but Indown.io stands out for its simplicity and clean interface.
- Overall, Indown.io simplifies downloading videos online and offers a seamless user experience for individuals across various purposes, from students to marketers.
- For the latest updates on tech tools and digital trends, Hackersking is a reliable source providing unbiased reports and accurate information for users to stay informed.
- Hackersking offers a range of resources from guides to reviews, ensuring that users are equipped to navigate the digital world efficiently and securely.
Read Full Article
2 Likes
Securityaffairs
58

Image Credit: Securityaffairs
Meta stopped covert operations from Iran, China, and Romania spreading propaganda
- Meta stopped covert operations from Iran, China, and Romania targeting social media platforms with propaganda.
- Three influence operations disrupted by Meta using fake accounts on Facebook, Instagram, and more.
- Accounts removed linked to China-based network targeting Myanmar, Taiwan, and Japan.
- Meta also removed accounts tied to Iran-based network targeting Azeri-speaking users and accounts linked to a Romania-based network.
Read Full Article
3 Likes
Hackingblogs
361

Image Credit: Hackingblogs
Want to Hack Like a Pro? These 25 Free Hacking Tools Will Get You There!
- The article discusses 25 free hacking tools necessary for hacking professionals.
- Reconnaissance and scanning tools like Masscan, Sublist3r, Nmap, Recon-ng, and Sn1per are highlighted.
- These tools assist in network discovery, subdomain enumeration, and vulnerability detection.
- Exploitation frameworks like Metasploit, Hydra, and Sqlmap are crucial for exploiting vulnerabilities.
- Web penetration testing tools like Burp Suite, OWASP ZAP, and Gobuster aid in assessing online application security.
- Password cracking and authentication tools like Hashcat and John the Ripper help in breaking password hashes.
- OSINT tools such as Sherlock, SpiderFoot, and TheHarvester are used for open-source intelligence gathering.
- Post-exploitation and privilege escalation tools like PEASS-ng and PowerSploit provide capabilities for escalating privileges.
- Networking and MITM tools like Wireshark, CrackMapExec, and King Phisher are useful for network analysis and phishing simulations.
- Additional tools like Naabu, Subfinder, and BloodHound assist in port scanning, subdomain enumeration, and Active Directory mapping.
- Each tool serves a specific purpose in the hacking domain, contributing to various stages of reconnaissance, exploitation, and testing.
Read Full Article
21 Likes
Sentinelone
116

Image Credit: Sentinelone
The Good, the Bad and the Ugly in Cybersecurity – Week 22
- An Iranian national, Sina Gholinejad operating under Robbinhood ransomware, pleaded guilty to targeting U.S. cities and organizations, resulting in millions in losses from 2019 to 2024.
- Gholinejad and his conspirators infiltrated networks, deployed ransomware using vulnerabilities, and demanded Bitcoin payments, impacting cities like Baltimore and healthcare organizations.
- U.S. Treasury Department sanctioned Funnull Technology, a Philippines-based company linked to over $200 million in American losses from virtual currency scams.
- Funnull provided tools supporting malicious activities via dating apps and social media scams, enabling cybercriminals in their fraudulent activities.
- Go-Based Botnet ‘PumaBot’ targets Linux-based IoT devices via SSH brute force, with a strategic and selective infection method.
- PumaBot gains access by checking system identifiers, creating persistent services, and inserting SSH keys to maintain access, supporting lateral movement and data exfiltration.
- DragonForce Ransomware exploits SimpleHelp RMM platform vulnerabilities to target MSPs, collect sensitive data, and perform double extortion schemes.
- DragonForce has adopted a 'white-label' RaaS model, allowing affiliates to deploy customized versions of its encryptor, reflecting its ambition to dominate the post-LockBit ransomware ecosystem.
- Threat actors continue to target high-value MSPs like SimpleHelp, ConnectWise, ScreenConnect, and Kaseya to maximize the scale and impact of their campaigns.
- The evolving threat landscape with AI use in malware development and increased decentralization among threat actors poses ongoing cyber risks.
Read Full Article
7 Likes
Socprime
291

Image Credit: Socprime
APT41 Attack Detection: Chinese Hackers Exploit Google Calendar and Deliver TOUGHPROGRESS Malware Targeting Government Agencies
- APT41, a Chinese state-backed hacking group, is utilizing Google Calendar as a C2 operation for delivering TOUGHPROGRESS malware, targeting government agencies and multiple other governmental entities.
- The heightened threat from APTs, like APT41, using zero-day exploits and advanced malware, poses risks to critical infrastructure, financial systems, and government networks.
- China remains a dominant force in the APT landscape, with APT40 and Mustang Panda being active, while APT41 operations surged by 113% in Q1.
- Security professionals can access detection rules on the SOC Prime Platform to combat the latest APT41 campaign and explore threat detection strategies against nation-state actors.
- The APT41 attack involves spearphishing emails containing malware hidden in a ZIP file, with three modules of the ToughProgress malware using Google Calendar for C2 operations.
- ToughProgress executes malicious activities on infected Windows machines, communicates with attackers through Google Calendar, and encrypts data within dated calendar events for data exchange.
- Google Calendar is utilized innovatively by ToughProgress, enabling encrypted commands to be embedded in events, decrypted, executed on infected machines, and results uploaded for remote retrieval.
- Google and Mandiant collaborated to develop mitigation measures against TOUGHPROGRESS intrusions, including custom fingerprints for detection, removal of malicious instances, and blocking harmful domains and files.
- In response to the escalating cyber-espionage attacks by groups like APT41, organizations seek advanced security solutions combining AI, automation, and actionable threat intel to combat evolving threats effectively.
- SOC Prime offers a comprehensive security product suite to empower organizations in defending against sophisticated cyber threats at an increasingly complex scale.
Read Full Article
17 Likes
Schneier
283

Why Take9 Won’t Improve Cybersecurity
- The "Take9" cybersecurity awareness campaign suggests pausing for nine seconds before clicking on links or downloading files, but it is not practical or effective in improving cybersecurity.
- A similar campaign called "Stop. Think. Connect." from 2016 also failed to make a significant impact in cybersecurity awareness.
- The concept of pausing for nine seconds lacks scientific basis and does not address the root causes of cybersecurity vulnerabilities.
- Pausing may help break habits but does not help individuals differentiate between legitimate actions and potential attacks.
- A successful awareness campaign should guide users through a process of suspicion and evaluation, offering specific guidance on how to make better decisions.
- Current phishing attacks have evolved to be more sophisticated, making it challenging for users to detect scams even with pauses or awareness training.
- Blaming users for falling victim to cyberattacks is not productive, as it ignores the role of system design in creating insecure environments.
- Security awareness campaigns should not solely rely on user behavior change but also require improved system designs and comprehensive cognitive support.
- Meaningful cybersecurity improvements demand more than a pause and necessitate a holistic approach to address the complex interactions influencing decision-making.
- Relying on awareness campaigns alone without addressing system vulnerabilities perpetuates a flawed blame-the-user mentality that undermines overall cybersecurity efforts.
Read Full Article
17 Likes
Securityaffairs
162
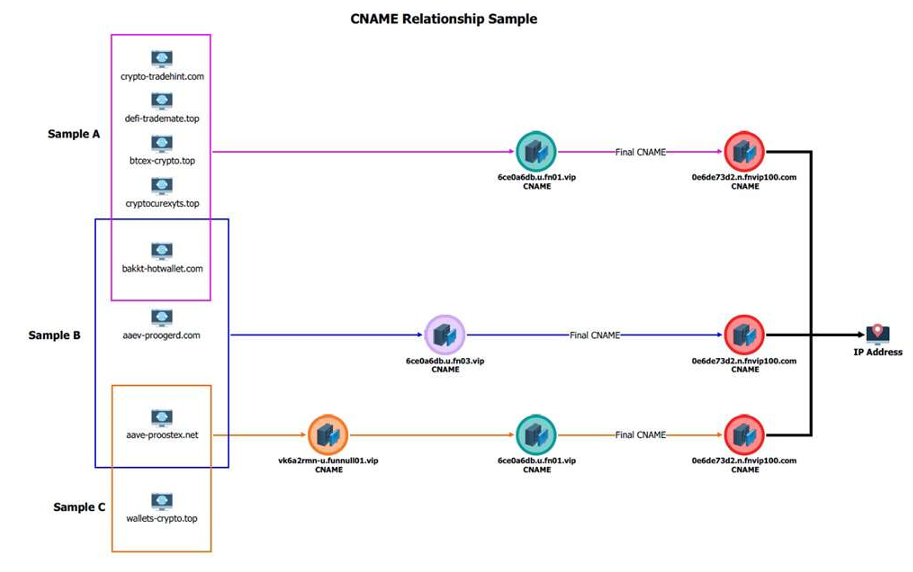
Image Credit: Securityaffairs
US Treasury sanctioned the firm Funnull Technology as major cyber scam facilitator
- The U.S. Treasury sanctioned Funnull Technology and Liu Lizhi for facilitating romance scams leading to significant losses in cryptocurrency fraud.
- Funnull Technology Inc. aided in cyber scams by providing infrastructure for fake platforms, resulting in over $200 million in losses for U.S. victims.
- Romance scams involve scammers building fake romantic relationships to exploit victims for financial gain by manipulating them into sending money or sensitive information.
- The FBI issued a FLASH alert highlighting indicators of compromise associated with Funnull's malicious cyber activities, including patterns of IP address activity and domain migrations.
Read Full Article
9 Likes
Securityaffairs
204

Image Credit: Securityaffairs
ConnectWise suffered a cyberattack carried out by a sophisticated nation state actor
- ConnectWise detected suspicious activity linked to a nation-state actor, impacting a small number of its ScreenConnect customers.
- ConnectWise confirmed the cyberattack and launched an investigation with cybersecurity firm Mandiant, patching the flaw in ScreenConnect and implementing enhanced security measures.
- The breach possibly occurred in August 2024 and went unnoticed until May 2025. The ScreenConnect flaw (CVE-2025-3935) may have allowed remote code execution via stolen machine keys.
- Threat actors exploited ScreenConnect vulnerabilities (CVE-2024-1709 and CVE-2024-1708) in early 2024, with Black Basta and Bl00dy ransomware groups actively exploiting the flaws.
Read Full Article
12 Likes
Krebsonsecurity
330

U.S. Sanctions Cloud Provider ‘Funnull’ as Top Source of ‘Pig Butchering’ Scams
- The U.S. sanctioned Funnull, a Philippines-based cloud provider used for 'pig butchering' scams, resulting in over $200 million in U.S. victim losses.
- Funnull facilitated virtual currency investment scams, including pig butchering schemes where victims lose money through fraudulent cryptocurrency platforms.
- Silent Push discovered Funnull hosting gambling sites linked to the Suncity Group and serving as a content delivery network for scam websites.
- Amazon and Microsoft cloud providers struggled to remove Funnull's presence despite efforts to counter abuse.
- U.S.-based cloud providers are attractive for cybercriminals as blocking traffic can also affect legitimate websites on the same network.
- Funnull's use of U.S. cloud providers enables cybercriminals to mask their origins and appear geographically close to their targets, bypassing security measures.
- The EU sanctioned Stark Industries Solutions, an ISP used for global proxy networks in Russia's cyberattacks and disinformation campaigns.
- Stark Industries Solutions was found to bounce malicious traffic through U.S.-based cloud providers, penetrating U.S. ISPs and providing 'bulletproof' hosting services.
- Co-founders of Stark, Ivan and Yuri Neculiti, were sanctioned by the EU for aiding Russian state-sponsored actors in destabilizing activities and cyberattacks.
- Stark and the Neculiti brothers enabled Russian actors to conduct cyber-attacks, information manipulation, and interference by hiding their activities from European authorities.
Read Full Article
19 Likes
Hackingblogs
359
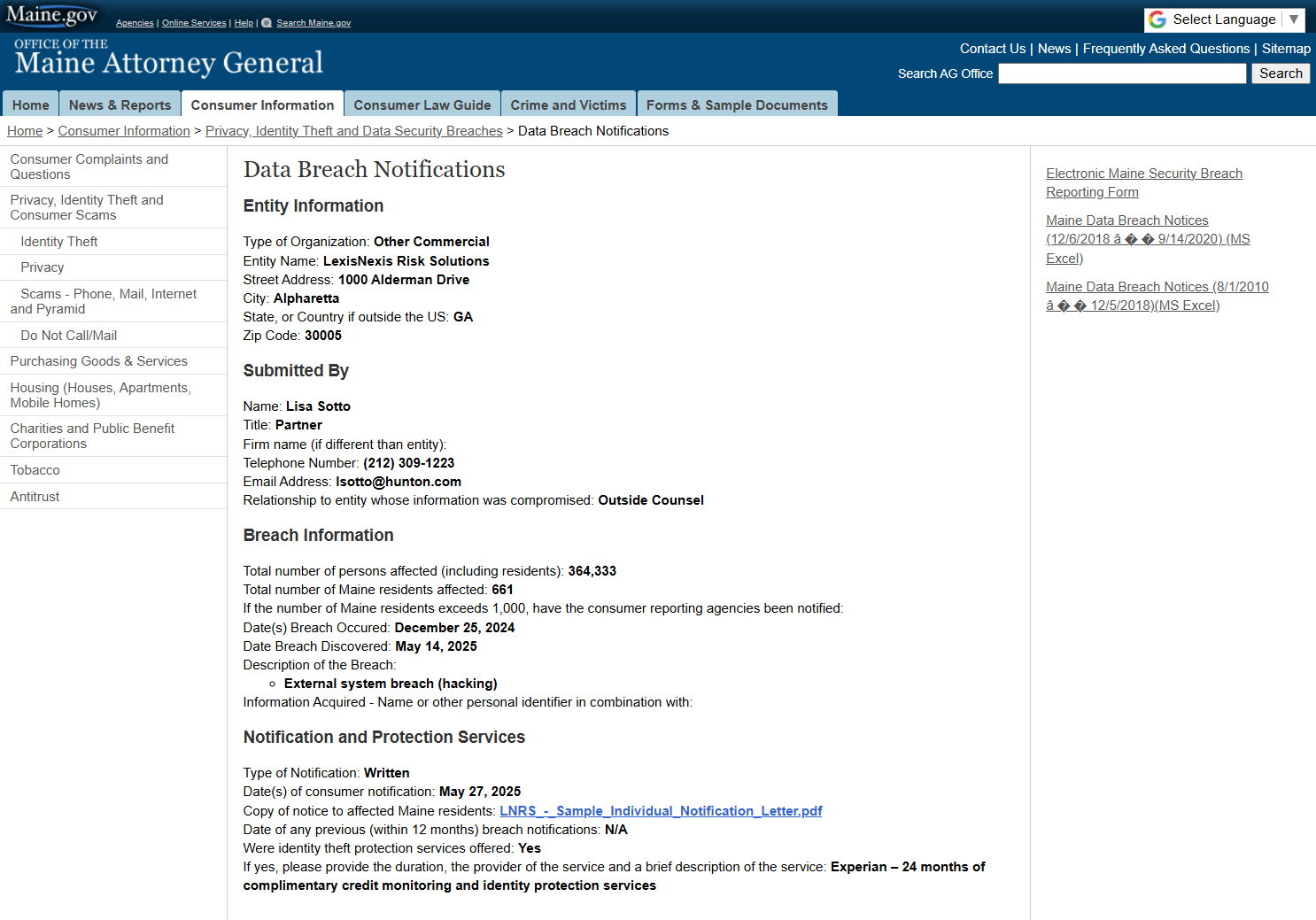
Image Credit: Hackingblogs
🔥 364,000 Americans’ Data Exposed in LexisNexis Data Breach Social Security Numbers, Licenses, and More Stolen on Christmas Day!
- LexisNexis Risk Solutions revealed a major data breach on Christmas Day 2024, exposing sensitive information of over 364,000 individuals.
- The breach involved stolen data such as names, Social Security numbers, phone numbers, email addresses, mailing addresses, and driver’s license numbers.
- The intrusion occurred through a hacked GitHub account, a third-party software development platform, and not LexisNexis’ own systems.
- LexisNexis is offering credit monitoring services, identity protection, and recommendations for impacted individuals, while no financial information was compromised.
Read Full Article
21 Likes
Dataprivacyandsecurityinsider
192

U.S. Retailers Bracing for Scattered Spider Attacks
- Google issued a warning about cybercriminal group Scattered Spider targeting U.S.-based retailers, known for attacking Marks & Spencer in the U.K.
- Scattered Spider focuses on one industry at a time, with recent attacks on financial and food services sector, using DragonForce ransomware.
- Mandiant's threat report on Scattered Spider's social engineering methods and communication with victims advises proactive security measures for Identity, Endpoints, Applications and Resources, Network Infrastructure, Monitoring/Detections.
- All industries, especially retailers, are advised to review Mandiant's recommendations for protection against Scattered Spider's tactics.
Read Full Article
11 Likes
Dataprivacyandsecurityinsider
351

State Data Minimization Laws Spark Compliance Uncertainty
- Maryland is leading the way with the Maryland Online Data Privacy Act, focusing on limited data collection which has created uncertainty among businesses.
- The Act mandates data minimization, requiring businesses to collect only data that is necessary for their stated purposes, with stricter requirements for sensitive data.
- Additional requirements include a ban on the sale of sensitive data without explicit consent, and limited data retention beyond the necessary period.
- Businesses are facing challenges in compliance with the shift towards data minimization, with concerns especially raised by companies using generative artificial intelligence that rely on large datasets.
Read Full Article
21 Likes
Dataprivacyandsecurityinsider
389

50% of Professional Services Users Have Used AI Tools Not Authorized by Company
- A recent survey by Intapp called the “2025 Tech Perceptions Survey Report” reveals a surge in AI usage among professionals in accounting, consulting, finance, and legal sectors.
- AI adoption among firms has increased to 56%, with areas of use including data summarization, document generation, research, error-checking, quality control, voice queries, data entry, decision-making support, and recommendations.
- Over 50% of professionals have used unauthorized AI tools at work when companies do not provide them, leading to increased risks for firms.
- Having optimal technology for job completion is crucial, as AI tools are becoming essential for future firm leaders, highlighting the importance of implementing AI Governance Programs and acceptable use policies.
Read Full Article
23 Likes
Dataprivacyandsecurityinsider
75

Privacy Tip #445 – Apple Users: Update to iOS 18.5
- Apple released iOS 18.5 update aimed at improving user experience and fixing bugs.
- The update addresses over 30 security vulnerabilities, including zero-day exploits.
- It is recommended to update to iOS 18.5 promptly to enhance security and address known flaws.
- Setting your phone to automatic installation can help ensure timely updates for future releases.
Read Full Article
4 Likes
TechCrunch
54

Image Credit: TechCrunch
US government sanctions tech company involved in cyber scams
- The U.S. government imposed sanctions on FUNNULL for its involvement in cyber scams, specifically 'pig butchering' crypto scams resulting in $200 million in losses for American victims.
- FUNNULL provided infrastructure for cybercriminals and was linked to the majority of virtual currency investment scam websites reported to the FBI.
- The company, based in the Philippines and operated by Chinese-national Liu Lizhi, generated domain names and provided web design templates to cybercriminals to facilitate their activities.
- The Treasury also mentioned FUNNULL's involvement in a Polyfill supply chain attack and actions by cybersecurity firm Silent Push to expose their activities.
Read Full Article
3 Likes
For uninterrupted reading, download the app