Info. Security News News
Socprime
404

Image Credit: Socprime
IOC-to-Query Generation for Google SecOps (Chronicle) in Uncoder AI
- Uncoder AI automates IOC extraction from threat reports, saving manual effort by parsing domains, URLs, IPs, hashes, and filenames.
- The tool generates Google SecOps-ready UDM queries using the extracted domains, facilitating tasks like hunting, rule-building, and investigation.
- Benefits include saving time, reducing errors with proper UDM field names, and enabling immediate actionable insights for security teams.
- Operational use cases include detecting phishing campaigns, monitoring traffic to attacker-controlled infrastructure, and responding to security incidents efficiently.
Read Full Article
24 Likes
Socprime
184

Image Credit: Socprime
AI-Driven IOC Conversion for Palo Alto Cortex XSIAM Queries
- Uncoder AI translates threat intelligence into Cortex XSIAM detection logic by ingesting structured IOCs and extracting relevant execution behaviors.
- Auto-generates Cortex XQL (XSIAM Query Language) detection logic targeting real-world execution patterns based on telemetry from winEventLog.
- Uncoder AI automates the creation of behavioral rules in Cortex XSIAM by recognizing execution syntaxes and correlating specific IOCs with known malware campaigns.
- Security teams using Cortex XSIAM benefit from accelerated rule creation, precision IOC-to-Telemetry mapping, and improved detection coverage with the help of Uncoder AI.
Read Full Article
11 Likes
Sentinelone
159

Image Credit: Sentinelone
The Good, the Bad and the Ugly in Cybersecurity – Week 21
- Global crackdowns on cybercrime saw arrests, malware takedowns, and data theft charges in Week 21.
- Matthew D. Lane, involved in the PowerSchool attacks, agreed to plead guilty after compromising data of 70 million individuals.
- Infrastructure of Lumma, a widespread malware-as-a-service, was seized, hindering its data exfiltration capabilities.
- Europol's Operation RapTor resulted in 270 arrests across ten countries, seizing cash, crypto, drugs, and firearms.
- Cyberattackers exploit abandoned cloud subdomains to spread scams and malware, with 'Hazy Hawk' hijacking valuable resources.
- Hazy Hawk exploits forgotten DNS CNAME records to control subdomains of trusted entities, distributing malicious content.
- Victims clicking on malicious links are directed to scams, fake alerts, phishing pages, and adult content portals.
- Russian APT28 targets international aid organizations supporting Ukraine in a multi-year cyberespionage campaign.
- APT28 conducts attacks across various sectors using tactics like spearphishing, exploiting VPNs, and leveraging vulnerabilities.
- APT28 employs tactics like compromising internet-connected cameras and SOHO devices to track aid shipments and stay undetected.
Read Full Article
9 Likes
Kaspersky
180

Image Credit: Kaspersky
Vulnerability in the Rubetek Home smart-home app | Kaspersky official blog
- Smart homes are now common, allowing residents to control various devices through a single app.
- A vulnerability in the Rubetek Home app allowed for potential security risks, but has been fixed.
- The vulnerability involved sending sensitive data, including personal information and access tokens, via the Telegram Bot API.
- The issue could have led to attackers gaining access to a wide range of user data sent to the developer.
- Potential risks included comprehensive surveillance, remote control of devices, and financial losses for users.
- Users of both Android and iOS apps were at risk of exploitation through this vulnerability.
- Recommendations for securing smart homes include changing router settings, creating dedicated networks, using strong passwords, and updating firmware.
- Regular monitoring and awareness of potential risks are crucial to safeguarding smart home devices.
- Taking necessary precautions can prevent unauthorized access and potential breaches in smart home security.
- Vigilance and proactive measures are key to protecting smart home networks and devices from malicious actors.
Read Full Article
10 Likes
Hackingblogs
1k

Image Credit: Hackingblogs
Biggest Infostealer malware data breach 2025 EXPOSES Everything: Facebook, Snapchat, Microsoft, Instagram, Google, and Even Your Bank Logins!
- A massive infostealer malware data breach in 2025 has exposed 184 million usernames and passwords from various platforms like Facebook, Instagram, Microsoft, Snapchat, Google, and others.
- The breach, discovered by cybersecurity expert Jeremiah Fowler, included direct logins to private accounts and was easily accessible online without encryption or protection.
- The breached data encompassed credentials for social media platforms, email services, banking websites, government and corporate accounts, among others.
- Immediate actions include monitoring leaks, updating passwords, raising awareness, and staying vigilant to mitigate the risks posed by this significant data breach.
Read Full Article
10 Likes
Securityaffairs
21
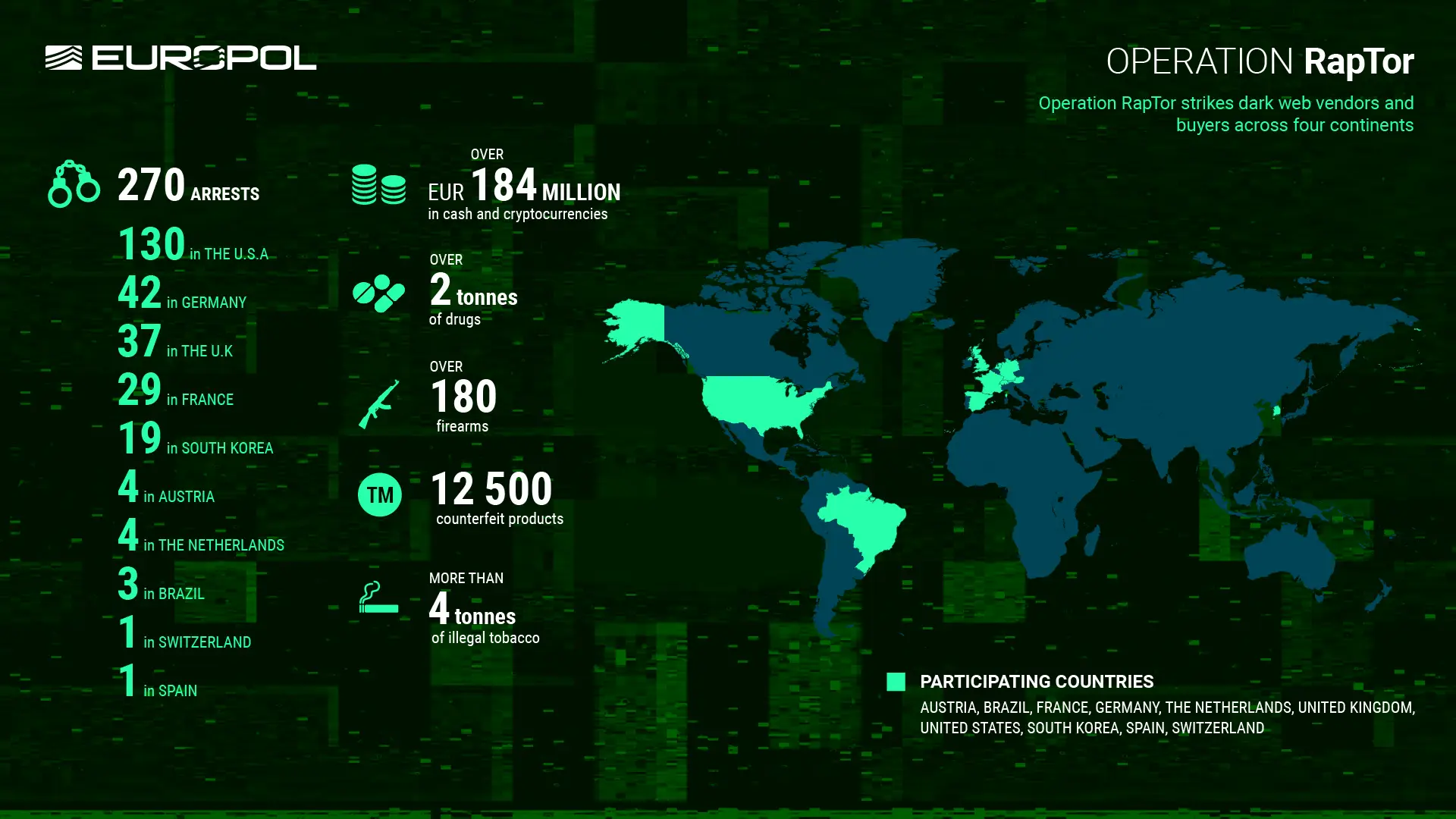
Image Credit: Securityaffairs
Operation RapTor led to the arrest of 270 dark web vendors and buyers
- Operation RapTor led to the arrest of 270 dark web vendors and buyers across 10 countries.
- The operation dismantled networks involved in trafficking drugs, weapons, and counterfeit goods.
- Europol supported the action by sharing intelligence packages with national authorities for targeted investigations.
- Authorities seized over €184M in cash and crypto, 2+ tonnes of drugs, 180+ firearms, 12,500 counterfeit items, and 4+ tonnes of illegal tobacco, striking a major blow to dark web criminal networks.
Read Full Article
1 Like
Dev
382

Image Credit: Dev
Best WAF for Beginners in 2025: Why SafeLine Beats Traditional WAFs
- SafeLine WAF offers a powerful and practical solution for web app security in 2025, particularly suited for beginners overwhelmed by complex firewall rules and configurations.
- Traditional WAFs relying on regex for attack detection struggle with false negatives (missed attacks) and false positives (mistaken blocks), making them easy to bypass and causing disruptions to user experience.
- SafeLine stands out by utilizing semantic analysis rather than just keyword matching, allowing it to understand the structure and meaning of web traffic, resulting in more reliable threat detection.
- SafeLine supports multiple languages, offers easy installation, a user-friendly dashboard, AI-assisted detection, and is free and open source, making it an ideal choice for beginners looking to enhance their web app security.
Read Full Article
23 Likes
Securityaffairs
210

Image Credit: Securityaffairs
Chinese threat actors exploited Trimble Cityworks flaw to breach U.S. local government networks
- Chinese threat actor UAT-6382 exploited a patched Trimble Cityworks flaw to deploy Cobalt Strike and VShell.
- The CVE-2025-0994 vulnerability in Trimble Cityworks allowed remote code execution, with a CVSS v4 score of 8.6.
- UAT-6382 breached U.S. local government networks using this vulnerability since January 2025, deploying Chinese-language web shells and custom malware.
- Talos researchers identified UAT-6382 utilizing Rust-based loaders named TetraLoader, connecting to specific domains and IPs for malicious activities.
Read Full Article
12 Likes
Krebsonsecurity
180

Oops: DanaBot Malware Devs Infected Their Own PCs
- The U.S. government unsealed criminal charges against 16 individuals accused of operating and selling DanaBot, a malware specializing in credential theft and banking fraud.
- DanaBot's newer version was used for espionage, with the defendants accidentally infecting their own systems with the malware, exposing their real identities.
- The malware infected over 300,000 systems globally, leading to estimated losses of more than $50 million; the ringleaders are named as Aleksandr Stepanov and Artem Aleksandrovich Kalinkin.
- The FBI seized servers used by DanaBot authors in 2022, and industry partners are assisting in notifying victims and remediating infections.
Read Full Article
10 Likes
Dataprivacyandsecurityinsider
388

College Student Behind Cyber Extortions
- Matthew D. Lane, a 19-year-old student at Assumption University, has been charged with cyber extortion conspiracy and unauthorized access to protected computers.
- Lane conspired to extort $200,000 from a telecommunications company and threatened to release data of more than 60 million students and 10 million teachers if they did not pay a ransom of approximately $2.85 million in Bitcoin.
- If convicted, Lane could face up to five years in prison for cyber extortion charges, three years of supervised release, and a fine of up to $250,000.
- The charge of aggravated identity theft carries a mandatory two-year sentence in prison, consecutive to any other imposed sentence on the computer fraud charges.
Read Full Article
23 Likes
Dataprivacyandsecurityinsider
337

Clock Ticking: DOJ’s New Data Security Rule Requires Compliance by July 8
- The DOJ's new data security rule requires U.S. companies to comply by July 8, 2025, limiting sharing sensitive personal data with certain foreign countries like China, Russia, and Iran.
- Enforcement actions after July 8 can result in fines up to $1 million and potential prison sentences of up to 20 years.
- The rule covers sensitive data types such as human genomic and biometric data, precise geolocation, health information, financial data, logs from fitness apps, and government-related location data.
- Businesses need to audit data, review contracts, evaluate foreign partnerships, assess vendor exposure, and build a compliance program to meet the new requirements before the deadline.
Read Full Article
20 Likes
Dataprivacyandsecurityinsider
177

Getting Too Personal? Illinois Court Says Family Medical History is Genetic Information
- On May 15, 2025, an Illinois district court denied a motion to dismiss a class action claim under the Illinois Genetic Information Privacy Act (GIPA) against Hospital Sisters Health System and Saint Francis (HSHS).
- GIPA regulates the use, disclosure, and acquisition of genetic information, including genetic tests, family medical history, disease manifestation, and genetic services; prohibiting employers from soliciting or using genetic information in employment decisions.
- The lawsuit alleges that HSHS required job applicants to disclose family medical histories as part of a pre-employment medical examination, arguing this violates GIPA protections regarding genetic information.
- Courts have interpreted GIPA broadly, with lenient standing requirements and a five-year statute of limitations, potentially exposing employers to class action risks if they inquire about family medical history in pre-employment exams.
Read Full Article
10 Likes
Dataprivacyandsecurityinsider
288

Data Breach Lawsuits Surge Against Chord Specialty Dental Partners
- Seven proposed class action lawsuits have been filed against Chord Specialty Dental Partners following a September 2024 data breach affecting over 173,000 individuals.
- Plaintiffs allege that the company failed to properly secure and protect patient data, breaching state and federal laws including the FTC Act and HIPAA.
- Exposed data included sensitive information such as Social Security numbers, bank details, medical records, and more, leading to potential harm for affected individuals.
- Plaintiffs seek damages and improved data protections as the legal battle unfolds, underscoring the importance of cybersecurity in healthcare and the consequences of data breaches.
Read Full Article
17 Likes
Dataprivacyandsecurityinsider
60

Florida Data Broker Fined $46,000 by California Privacy Watchdog
- Florida-based data broker Jerico Pictures, Inc. fined $46,000 by California Privacy Protection Agency for failing to register under the state's Delete Act.
- The $46,000 fine is the maximum allowed by law, imposed after the company failed to register for over 230 days and only did so when contacted during an investigation.
- California Privacy Protection Agency's head of enforcement emphasized their commitment to enforcing privacy laws and will take action against businesses violating California's privacy laws.
- The Delete Act requires data brokers to register annually and pay a fee to support the California Data Broker Registry, which will be part of the upcoming Delete Request and Opt-Out Platform (DROP) in 2026.
Read Full Article
3 Likes
Dataprivacyandsecurityinsider
357

Bipartisan Take It Down Act Becomes Law
- President Donald Trump signed the “Take It Down Act” into law on May 19, 2025, criminalizing the distribution of intimate images without consent.
- The Act requires social media platforms to remove non-consensual intimate images within 48 hours of a victim’s request.
- The law is a response to the growing concern of deepfake images being used for sextortion, revenge porn, and deepfake image abuse.
- Social media platforms have until May 19, 2026, to establish the notice-and-removal process for compliance with the Take It Down Act.
Read Full Article
21 Likes
For uninterrupted reading, download the app