Info. Security News News
Kaspersky
412
Image Credit: Kaspersky
How scammers exploit genuine Microsoft business notifications
- Scammers are exploiting genuine Microsoft business notifications to send phishing emails to potential victims.
- Cybercriminals insert custom text into legitimate thank-you messages from Microsoft to trick recipients.
- The scammers replace billing information in the emails with their phone numbers, prompting victims to call for 'assistance.'
- Victims who call the provided phone number may be tricked into installing malware, highlighting the need for employee training and robust security measures.
Read Full Article
24 Likes
Securityaffairs
281
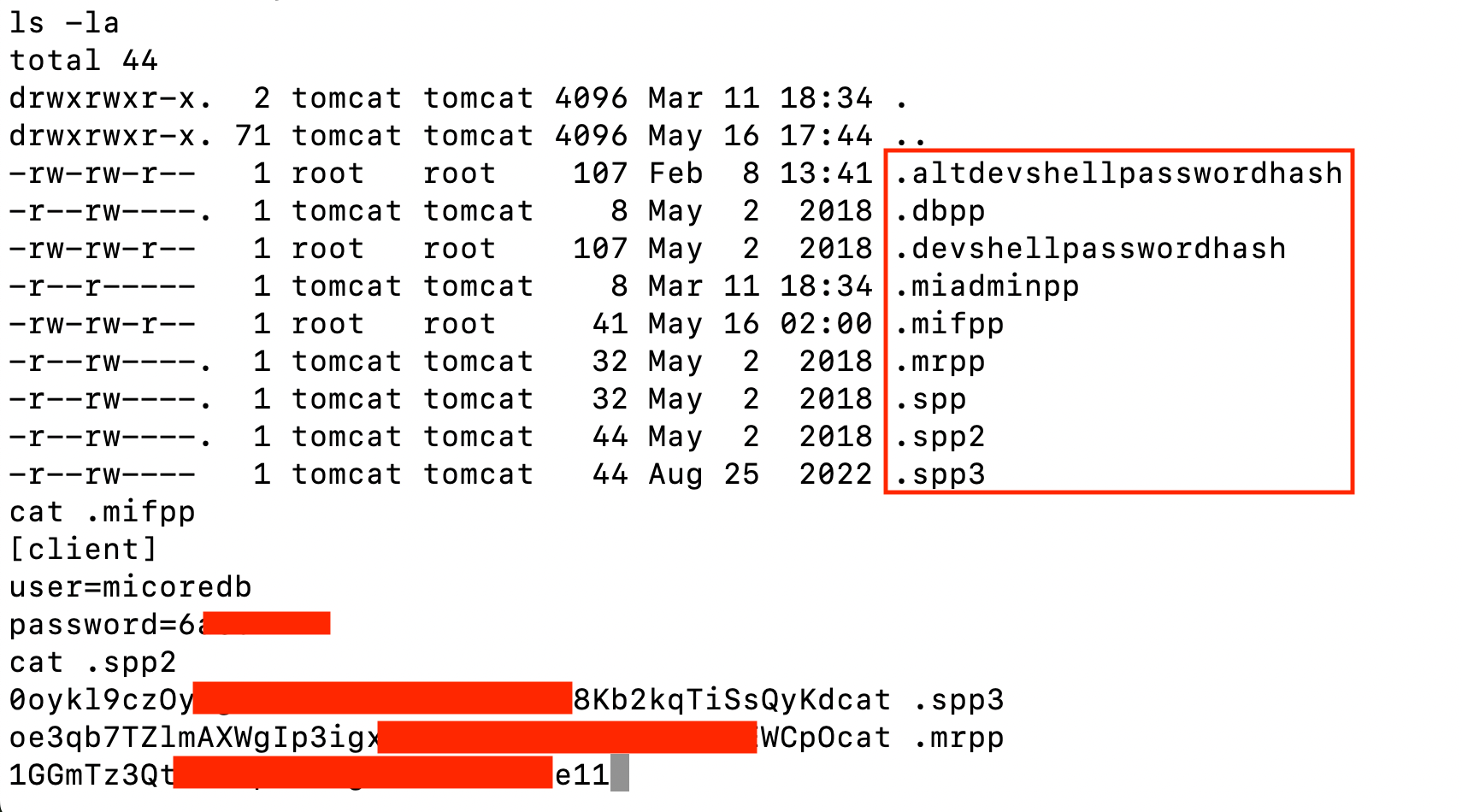
Image Credit: Securityaffairs
China-linked APT UNC5221 started exploiting Ivanti EPMM flaws shortly after their disclosure
- China-linked APT group exploits two Ivanti EPMM flaws, CVE-2025-4427 and CVE-2025-4428, to target organizations in Europe, North America, and Asia-Pacific.
- The flaws include an authentication bypass and a remote code execution vulnerability, allowing attackers to access protected resources and execute arbitrary code.
- Ivanti has released updates addressing the vulnerabilities after threat actors actively exploited them to achieve remote code execution without authentication.
- The attacks are linked to China-linked group UNC5221, which targeted critical sectors and used techniques like Java Reflection and KrustyLoader malware for espionage campaigns.
Read Full Article
16 Likes
Securityaffairs
217
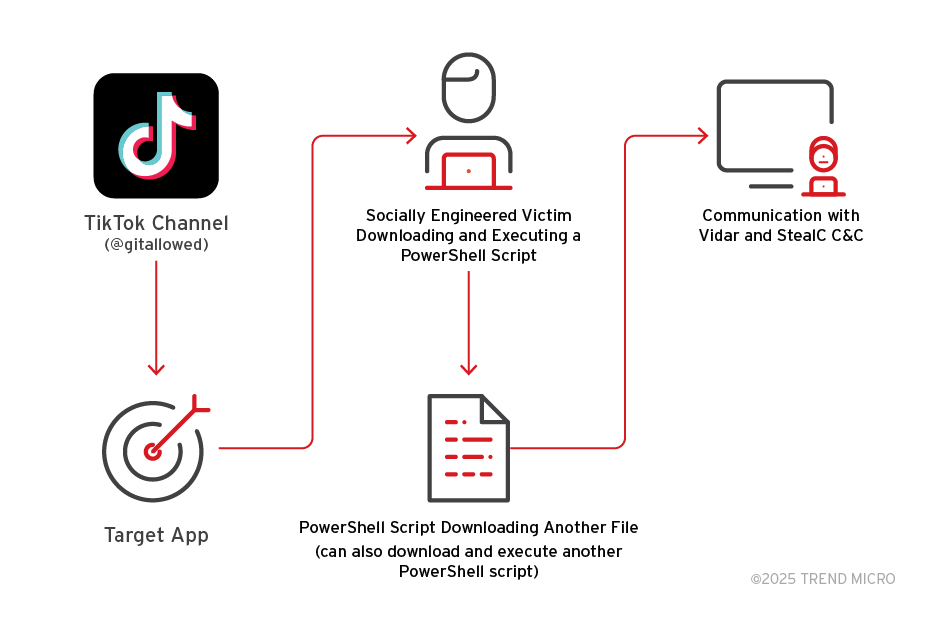
Image Credit: Securityaffairs
Fake software activation videos on TikTok spread Vidar, StealC
- Cybercriminals are using AI-generated TikTok videos to spread Vidar and StealC malware in ClickFix attacks.
- The videos trick users into executing PowerShell commands disguised as software activation steps, reaching over 500,000 views.
- Malware-laden TikTok videos provide step-by-step instructions to download Vidar or StealC malware, connecting to command-and-control servers after infection.
- Traditional security controls focusing on malicious code detection are less effective against social media-based malware distribution, highlighting the need for a more holistic defense approach.
Read Full Article
13 Likes
Pymnts
465

Image Credit: Pymnts
Adidas: Customer Contact Info Stolen in Data Breach
- Adidas has reported a data breach involving a customer service provider where cybercriminals accessed customer contact information.
- The breach did not include passwords or credit card data, and Adidas is informing potentially affected consumers.
- This breach is part of a series of data breaches the company has faced recently, and it is unclear if they are connected.
- Nearly a third of data breaches involve a third party, as highlighted by the Verizon 2025 Data Breach Investigations Report.
Read Full Article
13 Likes
Securityaffairs
46

Image Credit: Securityaffairs
Security Affairs newsletter Round 525 by Pierluigi Paganini – INTERNATIONAL EDITION
- Silent Ransom Group targeting law firms, FBI warns.
- Leader of Qakbot cybercrime network indicted in U.S. crackdown.
- Operation RapTor results in arrest of 270 dark web vendors and buyers.
- Chinese threat actors exploit Trimble Cityworks flaw to breach U.S. local government networks.
Read Full Article
2 Likes
Securityaffairs
328

Image Credit: Securityaffairs
Operation ENDGAME disrupted global ransomware infrastructure
- Operation ENDGAME coordinated by Europol and Eurojust dismantled global ransomware infrastructure from May 19 to 22, taking down 300 servers, 650 domains, and seizing €21.2M in crypto.
- Law enforcement efforts included Europol setting up a Command Post in The Hague with investigators from various countries, leveraging Eurojust's support for effective judicial cooperation.
- Authorities also seized €3.5M in cryptocurrency, targeting initial access malware strains like Bumblebee, Lactrodectus, Qakbot, and issuing 20 international arrest warrants for key operators.
- Germany will list 18 suspects on the EU Most Wanted list, accused of providing tools for ransomware attacks, showcasing law enforcement's adaptability in disrupting ransomware services.
Read Full Article
19 Likes
Hackersking
334

Image Credit: Hackersking
Trump Administration Cybersecurity Funding Cuts: A Risky Gamble?
- The Trump administration's cybersecurity funding cuts during Donald Trump's presidency raised concerns among experts and officials, posing a potential threat to national security.
- The 2021 budget proposal included significant reductions to the Department of Homeland Security's Cybersecurity and Infrastructure Security Agency (CISA), impacting cybersecurity research, incident response, and inter-agency coordination.
- Programs crucial for defending against cyberattacks saw funding cuts, potentially limiting emergency responses and infrastructure security updates, especially concerning election security ahead of the 2020 U.S. Presidential elections.
- Criticism from lawmakers and cybersecurity analysts highlighted the risks of emboldening nation-state actors like Russia, China, and Iran, as the U.S. lagged behind in global cybersecurity investments, emphasizing the importance of continuous investment in cybersecurity.
Read Full Article
20 Likes
Hackersking
363

Image Credit: Hackersking
How Most Cyber Attacks Begin: The Hidden Dangers of Credential-Based Threats
- Cyber threats are increasing in quantity and sophistication, posing risks of data breaches and financial losses.
- More than 55% of breaches stem from credential attack vectors, including phishing, brute force attacks, and MFA bypass techniques.
- Phishing attacks are the most dangerous aspect of cybersecurity, targeting user login information and financial data.
- MFA bypass techniques involve methods like man-in-the-middle attacks and token pilfering to circumvent multi-factor authentication.
- Brute force attacks involve continuously guessing combinations of usernames and passwords to gain unauthorized access.
- Malware, zero-day exploits, and misconfigurations are other common cyber attack vectors.
- Recommendations for protection include regular user training, complex password policies, and adoption of multiple layers of security.
- Behavior analytics, software updates, and secure remote access are emphasized for enhanced security measures.
- Understanding cyber threats and implementing proactive defense measures are crucial in safeguarding against credential-based attacks.
- Hackersking provides resources for cybersecurity training and comprehensive cyber defense strategies.
Read Full Article
21 Likes
Hackingblogs
12
Image Credit: Hackingblogs
⚠️ WARNING: TikTok Videos Offering Free Software Are Actually Hiding Deadly Vidar & StealC Malware!
- Trend Micro discovered a dangerous campaign on TikTok where cybercriminals are tricking users into downloading harmful malware like Vidar and StealC through viral videos.
- Scam videos offer free software downloads, but actually execute PowerShell commands to download and run malicious programs like StealC or Vidar, changing registry keys for persistence and erasing temporary folders to avoid detection.
- Cybercriminals are now using AI-generated, deepfake-like videos on platforms like TikTok, YouTube, Instagram to distribute malware, as they are more convincing to users and pose dangers like extracting login info, cookies, and cryptocurrency data.
- To protect against such threats, users are advised to avoid free software activation tutorials, use trustworthy antivirus programs, monitor account activities, and utilize breach monitoring services for data security.
Read Full Article
Like
Medium
401

Image Credit: Medium
The Cybersecurity Frontier of 2025: AI, Privacy, and the New Digital Defense
- Global IT spending in 2025 is projected to reach $5.61 trillion, while data breach damages per incident surged to $4.8 million in 2024.
- Key emerging threats in cybersecurity include increasingly sophisticated ransomware attacks, AI-powered threats, and executive-targeted social engineering.
- AI is now a crucial element in cybersecurity defense, enhancing speed and scale in threat response and analysis.
- Individuals are urged to take proactive steps like using strong passwords, limiting social media sharing, and leveraging advanced protection measures like VPNs for personal privacy defense.
Read Full Article
22 Likes
Securityaffairs
59

Image Credit: Securityaffairs
Silent Ransom Group targeting law firms, the FBI warns
- The FBI warns that the Silent Ransom Group, also known as Luna Moth, has been targeting U.S. law firms for 2 years using callback phishing and social engineering tactics.
- The group gains remote access to systems and steals sensitive data to extort victims. They have previously enabled Ryuk and Conti ransomware attacks through BazarCall campaigns.
- SRG started posing as IT staff in phone calls since March 2025, tricking employees into granting remote access and exfiltrating data without needing admin privileges.
- After stealing data, SRG extorts victims with ransom emails and pressures employees into negotiations. They operate a data leak site but do not always follow through on threats to publish the data.
Read Full Article
3 Likes
Hackersking
111

Image Credit: Hackersking
Strategy to Move Users Data & Chats to Google Workspace
- Assess and plan your migration to Google Workspace by evaluating existing cloud and communication channels and analyzing data to be migrated.
- Migrate data with all associated features like permissions, version history, comments, timestamps, and links to ensure seamless access and workability.
- Plan the migration of chat history from platforms like Slack to Google Chat for real-time communication using tools like CloudFuze.
- Carefully strategize the migration of email systems to Gmail using services like CloudFuze and evaluate data post-migration for accuracy and completeness.
Read Full Article
6 Likes
Securityaffairs
295

Image Credit: Securityaffairs
Leader of Qakbot cybercrime network indicted in U.S. crackdown
- U.S. authorities indicted Russian national Rustam Gallyamov for leading the Qakbot botnet, which infected over 700,000 computers and facilitated ransomware attacks.
- Qakbot, also known as QBot, is an info-stealing malware active since 2008, spread via malspam campaigns, and has been used by major ransomware gangs.
- The U.S. Justice Department filed a civil forfeiture complaint to seize over $24 million in cryptocurrency from Gallyamov as part of a multinational cybercrime crackdown.
- The FBI performed a sinkholing of the Qakbot botnet, identified over 700,000 infected computers, and seized illicit proceeds worth over $24 million, despite Gallyamov continuing attacks till January 2025.
Read Full Article
17 Likes
Hackersking
377

Image Credit: Hackersking
The Smartest Way to Build Authority and Backlinks in 2025
- Guest posting is a reliable strategy in digital marketing for boosting online presence, SEO rankings, and brand authority in 2025.
- Guest posting involves writing and publishing content on another website in exchange for a backlink to your site, providing benefits for both parties.
- Guest posting still works due to high-quality backlinks, targeted traffic, brand building, and thought leadership opportunities it offers.
- To make guest posting effective, focus on publishing on high-authority sites, offering unique content, including relevant links, and matching the host blog's tone and audience.
Read Full Article
22 Likes
Socprime
326
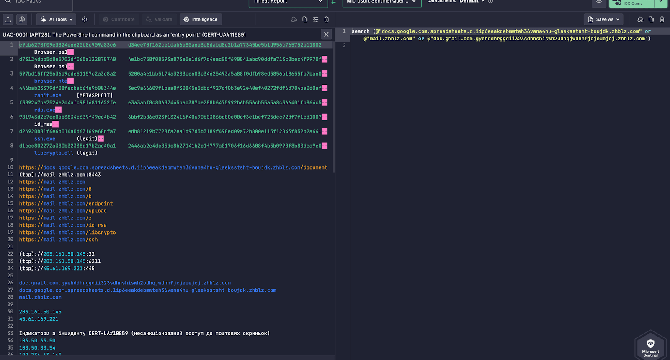
Image Credit: Socprime
IOC Query Generation for Microsoft Sentinel in Uncoder AI
- Uncoder AI automatically extracts malicious domains from threat reports used by adversaries for phishing and staging access to victim mailboxes.
- It generates Microsoft Sentinel search queries with the search operator to search across all logs ingested in Sentinel.
- The generated queries can be directly pasted into Microsoft Sentinel for threat hunting or investigation without manual formatting.
- Security teams can use this feature to identify phishing infrastructure connections, correlate endpoint behavior, and pivot from threat intel to detection efficiently.
Read Full Article
19 Likes
For uninterrupted reading, download the app