Info. Security News News
Kaspersky
335

Image Credit: Kaspersky
57 suspicious Chrome extensions with millions of installs | Kaspersky official blog
- Cybersecurity researchers found 57 suspicious extensions in the Chrome Web Store with over six million users.
- The extensions had alarming permissions that didn’t match their descriptions and were hidden from searches.
- Browser extensions can pose security risks and compromise privacy, even if downloaded from official stores.
- The suspicious extensions requested broad permissions, such as access to cookies, potentially allowing for data theft.
- These extensions could track user actions, change search engines, inject scripts, and activate advanced tracking.
- An investigation started with one extension, Fire Shield Extension Protection, which led to the discovery of more suspicious plugins.
- Most of these extensions claimed to block ads or improve search results, but lacked the necessary code to do so.
- The plugins were linked to a suspicious domain and shared common traits, suggesting they belong to the same family of spyware.
- Users are advised to check for and delete suspicious extensions, download only necessary ones, and use reliable security software.
- The extensions appeared to be part of a spyware or data-stealing program family, emphasizing the importance of cautious extension usage.
Read Full Article
20 Likes
Securityaffairs
92
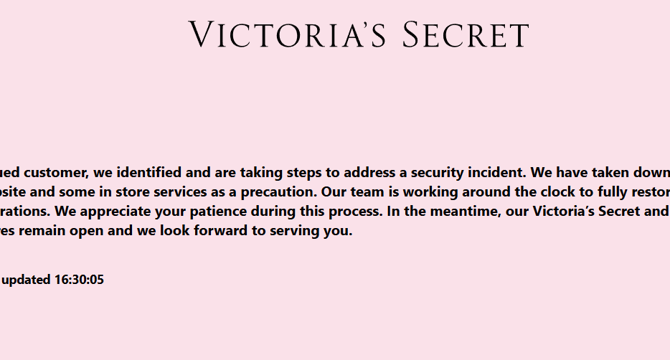
Image Credit: Securityaffairs
Victoria’s Secret ‘s website offline following a cyberattack
- Victoria's Secret took its website offline after a cyberattack that impacted customer care and distribution center operations.
- The company's CEO mentioned that recovery from the cyberattack will take some time as the incident affected email access for some staff.
- After the security incident, Victoria's Secret shares dropped by 6.9%, and the company did not disclose technical details about the attack.
- Recent data breaches in major brands like Dior and Adidas, along with UK retailers facing cyberattacks, indicate a rising threat against retailers globally.
Read Full Article
5 Likes
Dev
171

Image Credit: Dev
Cybersecurity Tips for Users
- Using weak and common passwords makes you an easy target for hackers. Use a password manager and create unique, complex passwords for better security.
- Enable Two-Factor Authentication (2FA) on all your accounts to add an extra layer of security and prevent unauthorized access.
- Be cautious of clicking on suspicious links, as they could lead to phishing scams and compromise your data. Always verify the sender before clicking.
- Avoid using public Wi-Fi without a VPN to protect your sensitive information from potential hackers who may exploit vulnerabilities in public networks.
Read Full Article
10 Likes
Securityaffairs
281
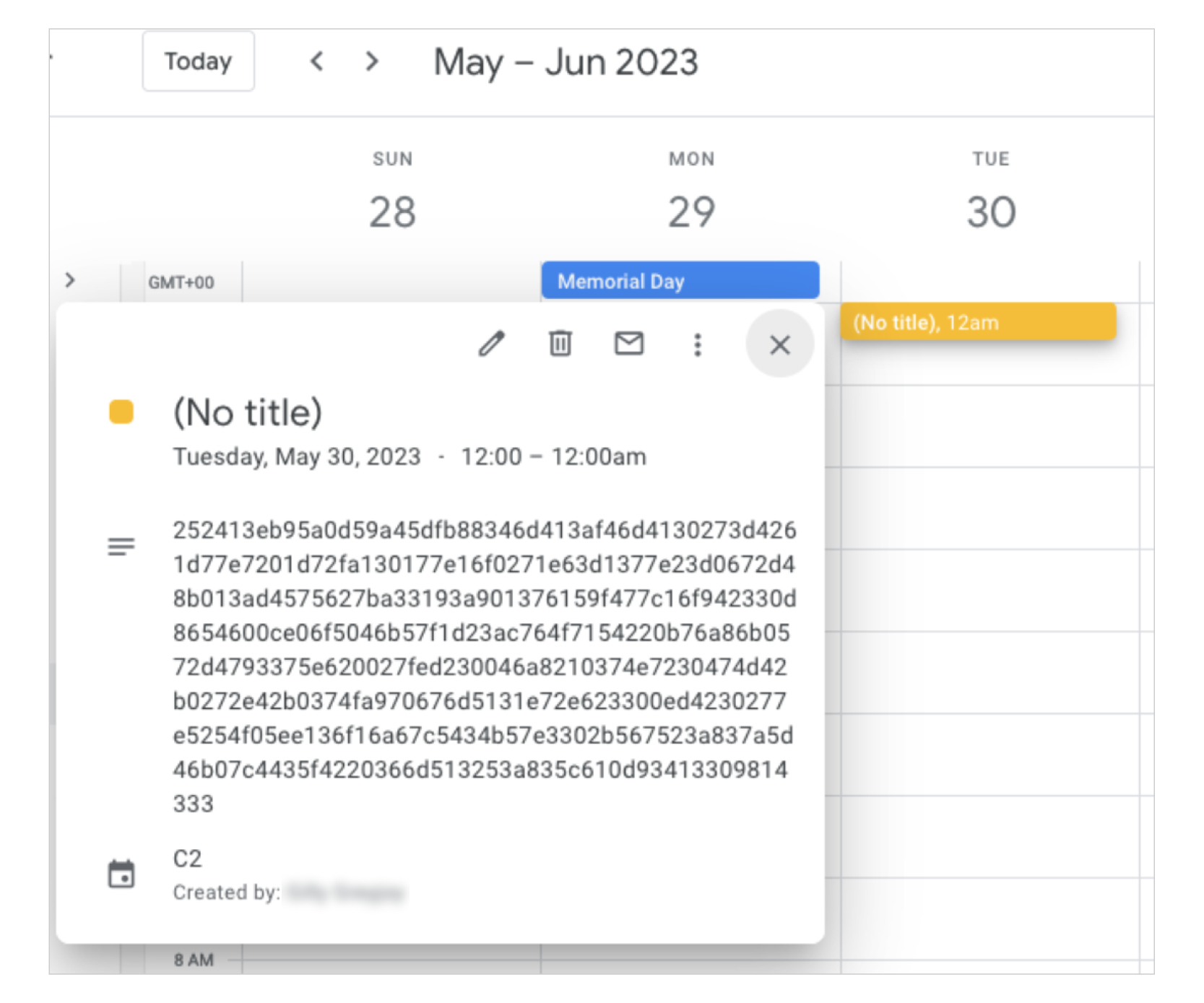
Image Credit: Securityaffairs
China-linked APT41 used Google Calendar as C2 to control its TOUGHPROGRESS malware
- China-linked group APT41 used Google Calendar as a command-and-control (C2) channel to control its TOUGHPROGRESS malware, targeting government entities through a compromised website.
- APT41 used spear phishing emails with a ZIP file hosted on a hacked government site to distribute the TOUGHPROGRESS malware, which operates in three stealthy stages with advanced evasion tactics.
- TOUGHPROGRESS decrypts and runs stages in memory, uses process hollowing for injection, and communicates with operators through Google Calendar to exfiltrate data and receive commands.
- Google has developed custom fingerprints to disrupt APT41 and TOUGHPROGRESS malware, terminated attacker-controlled projects, updated file detections, and shared threat intel with affected organizations.
Read Full Article
16 Likes
Vista InfoSec
370

Image Credit: Vista InfoSec
Test Form Submission Blog
- SOC 2 certification evaluates an organization’s controls related to security, availability, processing integrity, confidentiality, and privacy, crucial for service providers managing customer data in the cloud.
- Businesses offering third-party IT services seek SOC 2 compliance from secure vendors to protect data and demonstrate security practices.
- Benefits of SOC 2 Certification include enhancing brand reputation, gaining a competitive edge, and marketing differentiation.
- Undergoing a SOC 2 Audit improves security measures, operational efficiency, and overall services of an organization.
- SOC 2 Certification assures customers of implemented security measures to prevent breaches and secure data.
- Preference for working with SOC 2 certified vendors is high, making it crucial for organizations to obtain SOC 2 certification.
- SOC 2 requirements are similar to ISO27001 certification, facilitating the process of achieving ISO27001 after obtaining SOC 2 certification.
- SOC 2 Audit demonstrates a strong commitment to IT security and ensures regulatory compliance along with valuable insights into risk and security posture.
- Clearing a SOC 2 Audit enhances business reputation, ensures continuity, and provides a competitive advantage in the industry.
- VISTA InfoSec specializes in helping clients with SOC 2 Audit & Attestation processes, offering easy and hassle-free compliance solutions.
Read Full Article
22 Likes
Securityaffairs
62
Image Credit: Securityaffairs
New AyySSHush botnet compromised over 9,000 ASUS routers, adding a persistent SSH backdoor.
- GreyNoise researchers discovered the AyySSHush botnet compromising over 9,000 ASUS routers by adding a persistent SSH backdoor.
- The attackers used stealthy tactics like auth bypasses and abusing legit settings to avoid detection, gaining durable control over the routers.
- GreyNoise identified an ongoing exploitation campaign targeting specific ASUS router models, ensuring persistent backdoor access through firmware updates.
- Nearly 9,000 ASUS routers have been compromised, with only 30 related requests observed over three months, indicating the stealthiness of the campaign.
Read Full Article
3 Likes
Amazon
197

Image Credit: Amazon
Application security at re:Inforce 2025
- AWS re:Inforce 2025 offers a focus on key security areas, including application security (AppSec).
- Key themes for 2025 include organizational strategies for secure and speedy shipping, secure design principles, pipeline security, and security testing methodologies.
- Exciting sessions in the AppSec track cover topics such as scaling security with Security Guardians, improving code quality with Amazon Q Developer, and building verifiable apps using automated reasoning and generative AI.
- Sessions also explore DevSecOps in action, IaC security with AI, and the importance of memory-safe applications.
- Workshops focus on securing generative AI agents, red-teaming LLM security, and applying AWS services and open source tools for application security.
- Attendees can participate in threat modeling for builders workshops, learn to secure generative AI applications on AWS, and boost developer productivity with AI tools.
- The conference aims to provide practical insights and hands-on experiences in the field of application security.
- Register for re:Inforce 2025 to engage with these AppSec sessions and explore a wide range of security tracks available.
- Speakers at the event include experts like Daniel Begimher and Danny Cortegaca, offering valuable insights into cloud security and application security solutions.
- Daniel Begimher, a Senior Security Engineer, is known for his expertise in cloud security and incident response solutions.
- Danny Cortegaca, a Security Specialist Solutions Architect, partners with organizations to navigate security and regulatory challenges, emphasizing application security.
Read Full Article
11 Likes
Securityaffairs
58

Image Credit: Securityaffairs
Czech Republic accuses China’s APT31 of a cyberattack on its Foreign Ministry
- The Czech Republic has accused China's APT31 of a cyberattack on its Foreign Ministry, linking the cyber espionage group to a cyberattack on its critical infrastructure.
- Czech intelligence agencies conducted a joint investigation attributing the attack to China with a high degree of certainty.
- The EU, its Member States, and NATO Allies expressed support and solidarity with Czechia following the cyberattack, urging China to adhere to international norms and principles in cyberspace.
- APT31, also known as Zirconium or Judgment Panda, has a history of cyber espionage activities targeting diplomatic cables, industrial designs, and political documents in Europe, North America, and Asia.
- The US and UK have unsealed criminal charges and sanctions against members of APT31 for facilitating China's political and economic intelligence objectives.
- The Czech government's announcement received backing from the EU and NATO, highlighting concerns regarding malicious cyber activities originating from China.
- China has denied the allegations of involvement in the cyberattack, despite APT31 being linked to multiple cyber espionage operations targeting various countries.
- APT31 has been previously reported for using tools such as Jian, identified as a clone of the NSA Equation Group's hacking tool, demonstrating advanced cyber capabilities.
- The cyber espionage group has targeted organizations in the EU, US, Canada, and other countries in previous campaigns, indicating a widespread reach in its malicious activities.
- France's national cyber-security agency also warned of ongoing attacks by APT31 against French organizations, with the group hijacking home routers for concealing attack infrastructure.
Read Full Article
3 Likes
Krebsonsecurity
0

Pakistan Arrests 21 in ‘Heartsender’ Malware Service
- Authorities in Pakistan have arrested 21 individuals accused of operating the 'Heartsender' malware dissemination service.
- Heartsender, a popular spam and malware service, catered mainly to organized crime groups trying to trick victim companies into making payments.
- The arrests were made after raids in Lahore’s Bahria Town and Multan in May, with connections to losses exceeding $50 million in the United States alone.
- The alleged ringleader, Rameez Shahzad, and others were involved in various cybercrime activities, later rebranding as WeCodeSolutions, and were apprehended by authorities.
Read Full Article
Like
Socprime
370
Image Credit: Socprime
AI-Generated Carbon Black Detection Rule for DarkCrystal RAT Campaign
- Uncoder AI processes threat reports like CERT-UA#14045 on DarkCrystal RAT and generates Carbon Black-compatible detection logic.
- Detection logic includes capturing process names, MD5 file hashes, URLs, and destination IPs associated with the DarkCrystal campaign.
- Uncoder AI simplifies the process of writing detection rules for Carbon Black by auto-aggregating threat intelligence and generating production-ready rules.
- The operational value includes accelerated IOC-to-rule pipeline, high-fidelity threat matching, improved C2 discovery, and making threat intel actionable in Carbon Black.
Read Full Article
22 Likes
Securityaffairs
299
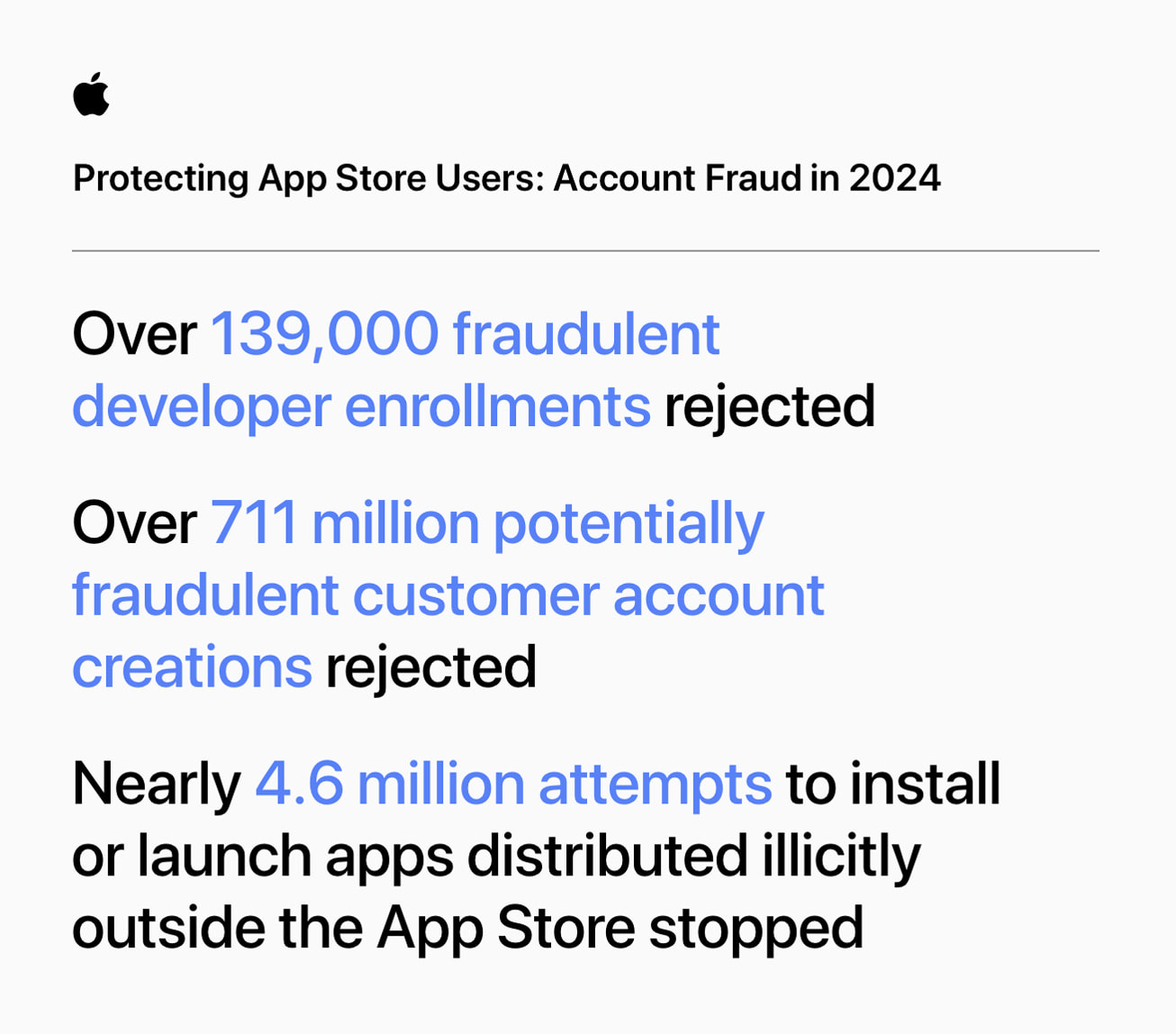
Image Credit: Securityaffairs
App Store Security: Apple stops $2B in fraud in 2024 alone, $9B over 5 years
- Apple has blocked over $9 billion in fraud in the past five years, with $2 billion blocked in 2024 alone, preventing various scams on the App Store.
- The App Store has become a trusted platform with over 813 million weekly visits, focusing on user security and developer success.
- In 2024, Apple took down thousands of fraudulent developer accounts, fake customer accounts, and unauthorized apps, demonstrating its commitment to the users' safety.
- Apple's App Review team reviewed over 7.7 million submissions in 2024, rejecting 1.9 million for violating standards, and maintaining a strong focus on privacy and security.
Read Full Article
18 Likes
Securityaffairs
50
Image Credit: Securityaffairs
Crooks use a fake antivirus site to spread Venom RAT and a mix of malware
- A fake Bitdefender website has been discovered spreading the Venom RAT by deceiving users into downloading it as antivirus software.
- Researchers found a malicious campaign using the fake website to distribute Venom RAT, a Remote Access Trojan (RAT) designed for password theft and stealthy access.
- Upon clicking the fake download button, users are redirected to an Amazon S3 link to download a ZIP file containing the VenomRAT malware.
- VenomRAT, a fork of the Quasar RAT, supports remote control, credential theft, keylogging, and data exfiltration, with attackers aiming for financial gain and persistent system control.
Read Full Article
3 Likes
Securityaffairs
113

Image Credit: Securityaffairs
Iranian Man pleaded guilty to role in Robbinhood Ransomware attacks
- Iranian national Sina Gholinejad pleaded guilty to his role in a Robbinhood ransomware scheme that caused over $19 million in damages to Baltimore.
- The ransomware attack disrupted key services like billing and citations in cities like Baltimore and Greenville.
- Gholinejad and his co-conspirators utilized sophisticated methods like using VPNs and crypto mixers to demand Bitcoin ransoms and launder payments.
- Gholinejad faces up to 30 years in prison for computer and wire fraud conspiracy, with sentencing scheduled for August.
Read Full Article
6 Likes
Amazon
21

Image Credit: Amazon
Introducing new regional implementations of Landing Zone Accelerator on AWS to support digital sovereignty
- AWS has introduced new regional implementations of Landing Zone Accelerator to support digital sovereignty and compliance with specific national and regional standards.
- The Landing Zone Accelerator on AWS aligns with global compliance frameworks and best practices, such as BIO in the Netherlands and ENS in Spain.
- AWS is expanding its regional implementations to help customers meet digital sovereignty goals with a focus on tailored approaches for specific regions.
- A new regional implementation targeted at Germany will support customers with workloads in adhering to the C5 compliance objectives.
- AWS's partnership with Schellman aims to simplify C5 adoption for customers by leveraging the C5-ready Landing Zone Accelerator.
- Landing Zone Accelerator on AWS automates the implementation of security controls across geographic compliance frameworks, saving customers time and effort.
- The LZA provides configurable controls for data residency, security, and compliance, catering to different customer needs including the public sector and multinational organizations.
- With a focus on digital sovereignty, AWS regional implementations aim to simplify cloud adoption and compliance, reducing the complexity associated with migrating workloads.
- AWS's Digital Sovereignty Competency connects customers with partners to address sovereignty needs across data residency, data protection, access control, and survivability.
- AWS Sovereignty Partners, like Atos and SVA, use Landing Zone Accelerator to streamline compliance and drive innovation in regulated industries such as healthcare, financial services, and utilities.
Read Full Article
1 Like
For uninterrupted reading, download the app