Info. Security News News
Socprime
305

Image Credit: Socprime
CyberLock, Lucky_Gh0$t, and Numero Detection: Hackers Weaponize Fake AI Tool Installers in Ransomware and Malware Attacks
- Hackers are using fake AI tool installers to spread ransomware and malware, including CyberLock, Lucky_Gh0$t, and Numero.
- Adversaries exploit AI technology to compromise business assets, emphasizing the need for stronger cybersecurity measures.
- Defenders can use tools like SOC Prime Platform and Uncoder AI to enhance detection and defense against AI-driven attacks.
- Cisco Talos researchers uncovered these threats, highlighting risks posed by fake AI software like OpenAI ChatGPT and InVideo.
- CyberLock encrypts files, Lucky_Gh0$t is a variant of Yashma ransomware, and Numero disrupts victims' Windows systems.
- CyberLock ransomware disguises itself as AI software, Lucky_Gh0$t is distributed as a premium ChatGPT version, and Numero poses as InVideo AI.
- Security experts advise verifying software sources and avoiding downloads from unknown vendors to reduce infection risks.
- By utilizing SOC Prime Platform and ethical AI practices, organizations can bolster their cybersecurity defenses against evolving threats.
- It is crucial to stay vigilant against the intersection of AI advancement and cyber threats to safeguard systems and data effectively.
- Implementing proactive defense strategies and leveraging trusted security technologies are vital in combating the ever-expanding attack landscape.
Read Full Article
18 Likes
Securityaffairs
254

Image Credit: Securityaffairs
Google fixed the second actively exploited Chrome zero-day since the start of the year
- Google released out-of-band updates to address three vulnerabilities in Chrome, including one actively exploited in the wild (CVE-2025-5419).
- The actively exploited vulnerability allows an attacker to trigger heap corruption via a crafted HTML page.
- In addition, Google addressed another medium-severity flaw in the Blink rendering engine (CVE-2025-5068).
- This is the second actively exploited Chrome zero-day fixed by Google since the beginning of the year.
Read Full Article
15 Likes
Securityaffairs
254
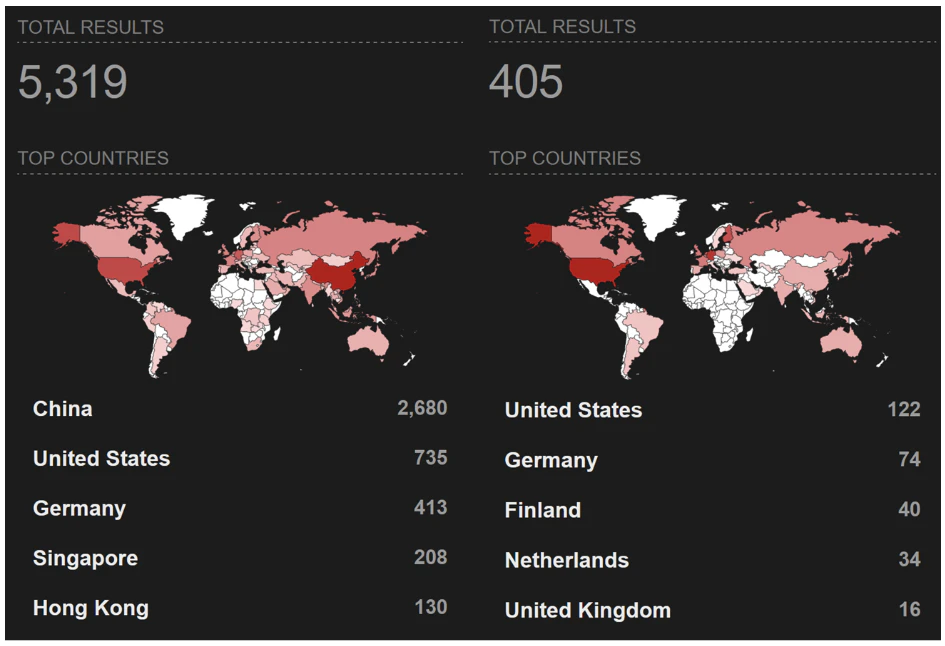
Image Credit: Securityaffairs
Cryptojacking campaign relies on DevOps tools
- A cryptojacking campaign, known as JINX-0132, is targeting exposed DevOps servers like Docker and Gitea to mine cryptocurrency secretly.
- The threat actors exploit misconfigurations and vulnerabilities in tools like Nomad, Consul, Docker, and Gitea to deliver the miner.
- The attackers rely on public GitHub tools and XMRig versions instead of custom malware, making attribution and clustering difficult.
- This campaign highlights the importance of securing DevOps tools properly, as 25% of cloud environments use these technologies, with 5% exposed directly to the internet and 30% of those misconfigured.
Read Full Article
15 Likes
Hackersking
346
Image Credit: Hackersking
Janitor AI: What is a Proxy and Why Should it Matter
- In the realm of artificial intelligence, chatbots like Janitor AI are making waves, with personas as realistic as interacting with real individuals.
- Understanding the term 'proxy' in the context of Janitor AI is crucial for users to comprehend its significance and role.
- Janitor AI is an AI chatbot platform known for complex interactions, roleplaying, and engaging conversations across various genres.
- Janitor AI uses external AI models like OpenAI’s GPT, Kobold, or others, relying on proxies to establish connections effectively.
- A proxy server acts as an intermediary between your device and another server, ensuring secure and anonymous transmission of data.
- Proxies play a vital role for Janitor AI by bypassing restrictions, reducing costs, enhancing privacy, and improving speed and load balancing.
- Types of proxies used with Janitor AI include reverse proxies, API proxies, self-hosted proxies, and public or community proxies.
- Configuring a proxy for Janitor AI involves selecting a model, joining a proxy server, inputting the proxy URL, and testing the connection.
- While proxies offer benefits like privacy and cost savings, there are risks such as security concerns and potential policy violations.
- Utilizing a proxy with Janitor AI can optimize interactions with AI models, enabling seamless and enriched chatbot experiences.
Read Full Article
20 Likes
Sentinelone
101

Image Credit: Sentinelone
Securing the Quantum Frontier: S Ventures’ Investment in Infleqtion
- SentinelOne aims to secure organizations through AI-driven cybersecurity to combat evolving threats in the computing landscape.
- Computing has evolved through mainframes, PCs, and the cloud, with GPUs enabling new possibilities in graphics and AI.
- SentinelOne, through S Ventures, is investing in Quantum computing with Infleqtion, promising fundamental changes in computation mechanics.
- Quantum computing utilizes quantum particles to represent multiple states simultaneously, enabling unprecedented computation speeds.
- The rise of Quantum computing will benefit various sectors but also pose cybersecurity threats due to its immense processing power.
- Infleqtion focuses on neutral atom quantum tech, offering scalability and stability for practical quantum computing in various industries.
- Infleqtion's quantum products like sensors and clocks bridge scientific research with practical applications, enhancing security and precision.
- SentinelOne sees synergy between their cybersecurity mission and Infleqtion's quantum innovation, aiming to enhance security through autonomous systems.
- Investing in Quantum computing is crucial for digital innovation, offering advancements in AI, optimization, simulation, and cybersecurity.
- SentinelOne supports innovative companies like Infleqtion to build a secure and quantum-secure technological future.
Read Full Article
6 Likes
Amazon
109

Image Credit: Amazon
A deep dive into data protection sessions at AWS re:Inforce 2025
- AWS re:Inforce 2025 will feature a Data Protection track focusing on protecting data in the age of quantum, AI, and digital sovereignty.
- Sessions will cover next-gen cryptography, trusted AI, privacy-enhancing technologies, and best practices for data protection.
- The conference offers insights for organizations of all sizes, addressing regulatory compliance, data transfers, and multi-cloud data protection.
- Topics include ransomware defense, post-quantum cryptography, cryptographic controls with AWS CloudHSM, and data migration strategies.
- Sessions also discuss data protection for AI, risk management, and secrets management strategies.
- Attendees can participate in workshops to strengthen cybersecurity posture, implement encryption, and manage cryptographic operations.
- Various sessions highlight real-world customer use cases and practical solutions led by AWS experts.
- Attendees can reserve seats in sessions through the attendee portal for preferred session access.
- re:Inforce aims to empower security professionals to enhance their organization's security posture and drive business growth in the digital era.
- The conference will provide attendees with valuable insights and strategies from certified AWS speakers.
Read Full Article
6 Likes
Securityaffairs
77
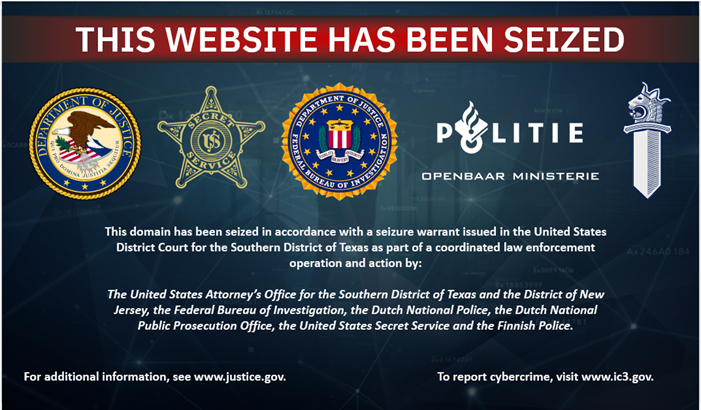
Image Credit: Securityaffairs
Police took down several popular counter-antivirus (CAV) services, including AvCheck
- On May 27, 2025, authorities seized crypting service sites (including AvCheck, Cryptor, and Crypt.guru) used by cybercriminals to test malware evasion capabilities.
- An international law enforcement operation, spearheaded by the U.S. Department of Justice, dismantled an online cybercrime syndicate providing encryption services to help malware evade detection.
- The operation, named Endgame, involved global efforts from U.S., Dutch, Finnish, and other national police forces to shut down malware services. The seized domains offered counter-antivirus tools for cybercriminals.
- CAV services like AVCheck enable cybercriminals to test their malware against antivirus programs discreetly, allowing them to gain unauthorized access to computer systems undetected. Undercover agents confirmed the services were linked to ransomware groups behind attacks in the U.S. and abroad.
Read Full Article
4 Likes
Kaspersky
272

Image Credit: Kaspersky
Kaspersky research: what interests kids in 2025 | Kaspersky official blog
- Kaspersky Safe Kids conducted a study to understand kids' online activities and interests, including searches on YouTube, favorite games, music preferences, and influencers followed.
- Memes, music, influencers, and cartoons are some popular search categories on YouTube for kids, with brainrot memes being particularly trendy.
- Music is the most searched category by children on YouTube, with genres like phonk and nightcore being popular, along with artists like Jennie from BLACKPINK.
- Gaming content is highly sought after, with Minecraft, Brawl Stars, Fortnite, Roblox, and Sprunki being among the favorite games for kids.
- Children globally share common interests in games, influencers, music, and memes, and are quick to adopt new technologies like neural networks and chatbots.
- It's crucial for parents to guide kids in online spaces, using tools like Kaspersky Safe Kids to monitor and protect them from inappropriate content and potential cyber threats.
- Kaspersky Cybersecurity alphabet and reliable device protection are recommended for children's online safety, along with staying informed about potential risks through resources like Telegram channels.
- Parents are advised to read the full report by Kaspersky to gain deeper insights into children's online activities and interests.
- Kaspersky Safe Kids offers features like content control, device monitoring, geofencing, and activity reports to enhance children's online safety.
- Additional articles by Kaspersky provide insights on children's safety online, including discussions about Apple's child safety initiatives, kids' first gadgets, cybersecurity discussions, and threats in school environments.
- It is important for parents to educate themselves and engage with their children on digital safety topics to ensure a secure online experience for the younger generation.
Read Full Article
16 Likes
Securityaffairs
179

Image Credit: Securityaffairs
A cyberattack hit hospitals operated by Covenant Health
- A cyberattack hit three hospitals operated by Covenant Health, leading to a shutdown of all systems to contain the incident.
- The cyberattack impacted services at St. Mary’s Health System and St. Joseph Hospital, requiring adjustments in outpatient lab services.
- Covenant Health Systems, a non-profit Catholic regional health care system, experienced the cyberattack, starting on May 26, 2025.
- At this time, no ransomware group has claimed responsibility for the attack, while previous cyberattacks have targeted healthcare organizations in the U.S.
Read Full Article
10 Likes
Securityaffairs
114

Image Credit: Securityaffairs
Experts published a detailed analysis of Cisco IOS XE WLC flaw CVE-2025-20188
- Details of a critical vulnerability, tracked as CVE-2025-20188, impacting Cisco IOS XE WLC have been made public.
- An unauthenticated, remote attacker could exploit the flaw to upload arbitrary files, perform path traversal, and execute arbitrary commands with root privileges.
- The vulnerability impacts various Cisco products such as Catalyst 9800 Series Wireless Controllers and Embedded Wireless Controller on Catalyst APs.
- Users are urged to disable the Out-of-Band AP Image Download feature as a mitigation while awaiting a fix, as no workaround exists.
Read Full Article
6 Likes
Hackersking
278

Image Credit: Hackersking
Instagram Account Details By Username: A Complete Guide Of 2025
- Instagram has become more than a photo-sharing platform, serving various purposes like showcasing lives, promoting businesses, networking, and building careers.
- Ways to obtain Instagram account details include checking basic profile information like username, bio, and profile picture, examining posts and captions, analyzing followers and following insights, exploring Instagram Stories and Highlights, and checking linked external accounts and contact options.
- Ethical methods involve using Instagram's built-in features like search bar, followers list, and Instagram Stories, along with manual search techniques on Google, and third-party tools like Noxinfluencer, Social Blade, IGLookup, and Phantombuster for public info.
- Reverse image search can help in verifying a user's profile picture, while checking comments and likes can provide insights into a user's social interactions.
Read Full Article
16 Likes
Pymnts
229

Image Credit: Pymnts
Hacking Ringleader ‘Stern’ Identified by Law Enforcement
- Law enforcement in Germany has identified the leader of hacking gang Trickbot, known as 'Stern', as Vitaly Nikolaevich Kovalev, a 36-year-old Russian.
- Kovalev is wanted in Germany for allegedly being the 'ringleader' of a 'criminal organisation', according to a recently issued Interpol red notice.
- As one of the most noteworthy figures in the Russian cybercriminal underground, Stern's real name had been unknown for years despite his involvement in Trickbot and previous hacking activities.
- In other cybersecurity news, data breaches involving third parties have doubled from 15% in 2023 to 30% in the following year, with a surge in lawsuits filed related to such breaches.
Read Full Article
13 Likes
Pymnts
65

Image Credit: Pymnts
Scattered Spider Chases Clout via Social Engineering Scams
- The hacking group known as “Scattered Spider” has been active, targeting companies like Marks & Spencer and conducting social engineering scams to obtain passwords.
- Their attacks have caused significant financial losses, such as up to $403 million for M&S and disruptions at MGM Casinos and Resorts.
- Scattered Spider seeks attention and clout rather than just financial gain, as mentioned by Charles Carmakal, chief technology officer at Mandiant Consulting.
- The group has targeted various companies and industries through impersonation tactics, with cybersecurity professionals being alert to this threat.
Read Full Article
3 Likes
Securityaffairs
254

Image Credit: Securityaffairs
Security Affairs newsletter Round 526 by Pierluigi Paganini – INTERNATIONAL EDITION
- Two Linux flaws found can expose sensitive data. Meta stopped covert operations from Iran, China, and Romania spreading propaganda.
- US Treasury sanctions Funnull Technology for cyber scam facilitation. ConnectWise faces cyberattack from a sophisticated nation-state actor.
- Victoria’s Secret website offline due to a cyberattack. APT41 uses Google Calendar for malware control.
- New AyySSHush botnet compromises 9,000 ASUS routers. Czech Republic accuses China’s APT31 for a cyberattack.
Read Full Article
15 Likes
Hackersking
177

Image Credit: Hackersking
SOA OS23: Know About the Latest Update in System-Oriented Architecture
- SOA OS23 is the latest version of the SOA Operating System, focusing on system integration, flexibility, and data flow in distributed systems.
- Key features of SOA OS23 include greater control over APIs, microservices support augmentation, cyber defense mechanisms, cloud-native features adaptation, AI technology integration, and efficiency improvements.
- SOA OS23 cares about service reusability, interoperability, scalability, and maintenance, ensuring optimal assistance for developers and IT professionals.
- Industry applications of SOA OS23 include usage in telecom for billing systems, finance for transaction processing, healthcare for data exchange, and e-commerce for platform scaling.
Read Full Article
10 Likes
For uninterrupted reading, download the app