Malware News
Securityaffairs
0

Image Credit: Securityaffairs
Sarcoma Ransomware Unveiled: Anatomy of a Double Extortion Gang
- The Cybersecurity Observatory of the Unipegaso’s malware lab published a detailed analysis of the Sarcoma ransomware.
- Sarcoma Ransomware, first detected in October 2024, has become one of the most active and dangerous ransomware groups, targeting over 100 victims primarily in the USA, Italy, Canada, and Australia.
- The gang is known for its aggressive tactics, including zero-day exploits and remote monitoring tools, with high-profile breaches like the 40 GB data theft from Smart Media Group Bulgaria showcasing its advanced capabilities.
- In response to the escalating threat, the Cybersecurity Observatory of Unipegaso has initiated an extensive investigation to analyze Sarcoma’s methods and promote stronger defensive measures, emphasizing the importance of timely patching, network segmentation, and user awareness.
Read Full Article
Like
Cybersecurity-Insiders
361

Image Credit: Cybersecurity-Insiders
UK Cyber Crime takes a new turn towards TV show the Blacklist
- Cybercriminals in the UK are now targeting retailers, drawing inspiration from the TV show The Blacklist and using similar names for their groups.
- Ransomware gangs like DragonForce are increasingly sophisticated, demanding ransom and selling stolen data on the dark web, leading to financial losses for companies and CEOs.
- NHS England is urging companies to bolster cybersecurity defenses, particularly as threats from groups like DragonForce pose multi-strike risks to public and private entities.
- The Co-Op experienced digital disruptions initially denied as a cyberattack, highlighting the need for enhanced cybersecurity measures amidst evolving ransomware threats.
Read Full Article
21 Likes
Cybersecurity-Insiders
202

Image Credit: Cybersecurity-Insiders
Ransomware’s Next Target: Strengthening Critical Infrastructure Against Emerging Cyber Threats
- Ransomware poses a growing threat to critical infrastructure, with over 66% of US organizations experiencing attacks in the past year.
- Exploiting vulnerabilities in security practices and systems, ransomware targets sectors like energy, transportation, and healthcare.
- Legacy systems in energy and healthcare sectors make them vulnerable to ransomware attacks, resulting in significant financial costs and service disruptions.
- Ransomware tactics have evolved to include sophisticated operations, using AI and ML for automation and maximizing damage.
- Proactive defense strategies such as Zero Trust Architecture and AI-powered threat detection are crucial in combating ransomware.
- Quantum computing poses a future threat to cybersecurity, prompting the need for post-quantum cryptography and security measures.
- Organizations must focus on cyber resilience by planning for operations during attacks, testing backup systems, and implementing network segmentation.
- Collaboration between governments, industries, and cybersecurity firms is essential to establish cybersecurity standards and innovative defense solutions.
- A multi-layered approach combining proactive defense, cyber resilience, and quantum security preparation is key to protecting critical infrastructure.
- Continuous vigilance, adaptation to new attack methods, and security integration at every stage of design are crucial in staying ahead of cyber threats.
Read Full Article
12 Likes
Medium
125

Building Ransomware Resilience: Why Product Strategies Must Prioritise Comprehensive Recovery Plans
- The April 2025 ransomware attacks on major retailers exposed vulnerabilities, leading to data theft and disruptions in operations.
- Recovery plans are crucial in dealing with modern ransomware, requiring more than just backups for data restoration.
- To enhance ransomware resilience, product managers must integrate recovery plans at every stage of product development.
- Key best practices include rapid system isolation, building alternative systems for failover, prioritizing secure backups, embedding incident response tools, training employees, and testing recovery plans.
Read Full Article
7 Likes
Securityaffairs
255

Image Credit: Securityaffairs
Security Affairs newsletter Round 524 by Pierluigi Paganini – INTERNATIONAL EDITION
- US Government officials targeted with texts and AI-generated deepfake voice messages impersonating senior U.S. officials
- New botnet HTTPBot targets gaming and tech industries with surgical attacks
- Google fixed a Chrome vulnerability that could lead to full account takeover
- Coinbase disclosed a data breach after an extortion attempt
Read Full Article
15 Likes
Securityaffairs
390
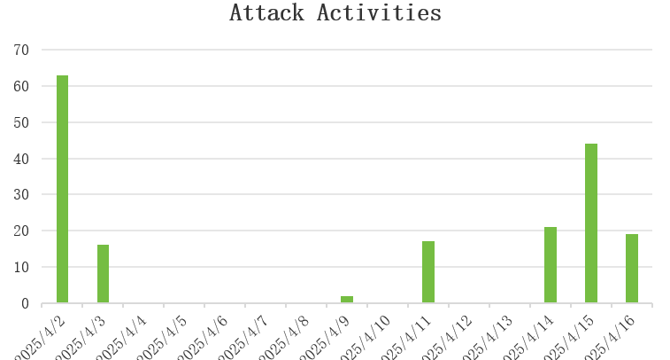
Image Credit: Securityaffairs
New botnet HTTPBot targets gaming and tech industries with surgical attacks
- A new botnet named HTTPBot is targeting China’s gaming, tech, and education sectors, as discovered by cybersecurity researchers.
- HTTPBot, a Go-based botnet detected in August 2024, intensified its activities by April 2025, engaging in highly targeted attacks using advanced DDoS tactics.
- The botnet employs various HTTP-based attack methods to conduct precise transactional DDoS attacks on critical interfaces, posing a systemic threat to industries reliant on real-time interaction.
- HTTPBot features 7 built-in DDoS attack methods, evades detection through techniques like Base64 encoding, and specifically targets the Windows platform, making it a significant threat in the cybersecurity landscape.
Read Full Article
23 Likes
Kaspersky
243

Image Credit: Kaspersky
Ransomware group uses ClickFix to attack businesses
- Ransomware group Interlock is using the ClickFix technique to target businesses, posing as the Advanced IP Scanner website.
- Interlock lures victims to a fake CAPTCHA page imitating Cloudflare, tricking them into executing a malicious PowerShell command.
- Once the command is executed, a fake PyInstaller installer launches, allowing Interlock to collect system information and deploy malware like a remote access Trojan.
- To protect against ClickFix attacks, it is recommended to raise employee awareness, install reliable protection on devices, monitor for suspicious activities, and consider external threat hunting services.
Read Full Article
14 Likes
Cybersecurity-Insiders
52

Image Credit: Cybersecurity-Insiders
Ransomware attacks on education sector go unreported for months
- Countries like the United Kingdom, the United States, Australia, and Canada have cyber laws mandating organizations to report ransomware incidents within 48 to 72 hours.
- A study by Comparitech reveals that U.S. educational institutions take an average of 4.8 months to disclose ransomware data breaches, sometimes waiting up to six months.
- Many ransomware incidents in the education sector are only discovered when stolen data appears on the dark web, as institutions often remain silent until external exposure.
- Delayed disclosure of breaches raises ethical and legal concerns, putting students, parents, and educators at risk of identity theft and cyber-related harm.
Read Full Article
3 Likes
Cybersecurity-Insiders
47

Image Credit: Cybersecurity-Insiders
Dior likely hit by ransomware attack
- Dior, the renowned French luxury fashion brand, has fallen victim to a ransomware attack, compromising sensitive customer information.
- The breach exposed personal details like names, mobile numbers, email addresses, and purchase history but did not include financial information.
- Dior is actively investigating the breach, implementing security measures, and warning customers about potential phishing scams.
- This incident highlights the growing trend of cybercriminals targeting retail brands for personal data, emphasizing the importance of online security measures.
Read Full Article
2 Likes
Securityaffairs
278

Image Credit: Securityaffairs
Coinbase disclosed a data breach after an extortion attempt
- Coinbase disclosed a data breach after rogue contractors stole customer data and demanded a $20M ransom.
- The breach, affecting under 1% of users, was reported to the SEC after a ransom demand was received on May 11, 2025.
- The unauthorized access was detected in previous months, leading to termination of involved personnel and implementation of heightened fraud-monitoring measures.
- Compromised data includes contact details, partial SSNs and bank info, ID images, account history, and limited internal documents but did not expose passwords, private keys, or customer funds.
Read Full Article
16 Likes
Securitysales
43

Image Credit: Securitysales
Ransomware Landscape Shifts as Attackers Target New Victims
- The global ransomware landscape is evolving with smaller, unpredictable attackers targeting less-defended organizations as major players have been dismantled due to law enforcement crackdowns.
- Out of the 150 ransomware groups tracked, 96 remained active, with 52 new groups emerging in the past year, indicating a more chaotic and unpredictable field.
- Small and mid-sized businesses are now the primary targets, leading to a significant increase in reported ransomware victims over the last two years.
- Manufacturing, professional services, and healthcare sectors are the most targeted, with healthcare seeing a shift towards smaller practices as primary targets.
Read Full Article
2 Likes
Securelist
313

Image Credit: Securelist
Threat landscape for industrial automation systems in Q1 2025
- The percentage of ICS computers on which malicious objects were blocked remained stable in Q1 2025, at 21.9%.
- Quarterly figures show a decreasing trend year over year, with a decrease of 2.5 pp compared to Q1 2024.
- Biometrics sector saw an increase in malicious object blocks, the only OT infrastructure type where this occurred.
- Threat levels vary regionally, with Northern Europe at 10.7% and Africa at 29.6% affected ICS computers.
- Denylisted internet resources blocked and email threats decreased in Q1 2025, hitting a low since 2022.
- Primary threats from the internet include denylisted resources, malicious scripts, and phishing pages.
- Malicious scripts, phishing pages, and documents showed an increase in blocks in Q1 2025.
- AutoCAD malware saw the lowest percentage of blocks among ICS computers and continued to decrease.
- Web miners and malicious documents blocks increased notably in Q1 2025.
- The percentage of ICS computers on which worms, viruses, and cad malware were blocked decreased in Q1 2025.
Read Full Article
18 Likes
Cybersecurity-Insiders
244

Image Credit: Cybersecurity-Insiders
Google warns of US retail cyber attacks and M & S insurance payout to cost £100m
- Google's Threat Intelligence team has issued a warning for U.S. retailers about potential cyberattacks by Scattered Spider, a sophisticated cybercriminal group.
- Scattered Spider, also known as UNC3944, is suspected of targeting major UK retailers with DragonForce ransomware and may expand its operations to the U.S.
- Mandiant, in partnership with Google, is offering a cybersecurity playbook to help businesses defend against advanced threats like Scattered Spider.
- Marks & Spencer is expected to file a £100 million insurance claim to cover recovery costs after a cyberattack linked to Scattered Spider.
- The cyberattack on Marks & Spencer led to operational disruptions, financial losses, and potential damage to the company's reputation and trust with consumers.
- The insurance claim payout for the cyberattack on Marks & Spencer is uncertain and depends on factors such as IT infrastructure preparedness.
- Cyber insurance considerations include premiums tied to cybersecurity preparedness, potential coverage exclusions for specific cyber risks, and future pricing adjustments.
- As cyber threats increase, organizations, especially in retail, must prioritize cybersecurity measures and insurance coverage to mitigate financial impacts.
- CIOs and CTOs need to reassess cyber insurance strategies as premiums rise and coverage options change due to evolving cyber threats.
- Vigilance in the retail sector is paramount to safeguard customer data and financial transactions from cybercriminals as cyber threats continue to evolve.
Read Full Article
14 Likes
Cybersecurity-Insiders
4

The End of VPNs — Part 1: Why Reachability is the New Risk
- VPNs are considered risky due to their design, which exposes vulnerabilities according to Zscaler CSO Deepen Desai.
- Legacy remote access infrastructure is failing modern enterprises, with high concerns about unpatched VPNs leading to ransomware attacks.
- VPNs grant broad network access once authenticated, making them a significant security flaw in today's hybrid and cloud-first environments.
- ThreatLabz tracked over 400 CVEs related to VPN vulnerabilities between 2020 and 2025, with attackers exploiting them faster than patches are deployed.
- The lack of segmentation and containment within VPNs has led to major outages and breaches, resulting in urgent patch cycles.
- The blueprint for VPN exploitation includes finding exposed endpoints, compromising devices, moving laterally, and exfiltrating data or deploying ransomware.
- Attackers are now using AI to automate reconnaissance, plan attacks, and generate exploits faster than traditional defense teams can patch, posing a significant threat.
- Defenders need to adopt Zero Trust architecture and simplify their infrastructure to combat automated threats effectively.
- VPN failures not only pose external threats but also burden IT, security, and end users with outages, performance issues, and internal resource drains.
- VPNs can act as backdoors for third-party risks and expose vulnerabilities during mergers and acquisitions, making them a significant security concern.
Read Full Article
Like
Securityaffairs
419

Image Credit: Securityaffairs
How Interlock Ransomware Affects the Defense Industrial Base Supply Chain
- Interlock Ransomware attack on a defense contractor exposed global defense supply chain details, risking operations of top contractors and their clients.
- Interlock Ransomware uncovered supply chain details of top defense contractors globally, leading to potential exposure of classified information and interest from foreign intelligence agencies and espionage groups.
- Numerous documents related to global defense corporations were found in the leaked dataset released by Interlock Ransomware.
- Ransomware attacks on defense contractors can have profound implications for national security, operational efficiency, financial stability, trust, and brand reputation, highlighting the need for robust cybersecurity measures and CMMC implementation.
Read Full Article
25 Likes
For uninterrupted reading, download the app