Malware News
Cryptopotato
152

Image Credit: Cryptopotato
North Korean Hackers Set Up US Shell Companies to Target Crypto Developers: Report
- North Korean hackers linked to the state’s notorious Lazarus Group have set up shell companies within the United States to target crypto developers.
- The hackers posed as legitimate employers offering jobs in the crypto industry, using fake names, addresses, and documentation.
- They used fake professional profiles and job postings on platforms like LinkedIn to approach developers, inviting them to 'interviews' where they were encouraged to download malware.
- The FBI has seized one of the shell companies' domains and confirmed the use of North Korean malware in the campaign.
Read Full Article
9 Likes
Securityaffairs
193

Image Credit: Securityaffairs
CEO of cybersecurity firm charged with installing malware on hospital systems
- CEO of cybersecurity firm Veritaco, Jeffrey Bowie, charged with violating Oklahoma's Computer Crimes Act.
- Bowie allegedly installed malware on employee computers at Oklahoma City St. Anthony Hospital on August 6, 2024.
- Security footage shows Bowie attempting to access multiple offices and installing malicious software to capture and transmit screenshots.
- No patient data was accessed, and the unauthorized attempt was quickly contained with the assistance of law enforcement.
Read Full Article
11 Likes
Securityaffairs
112
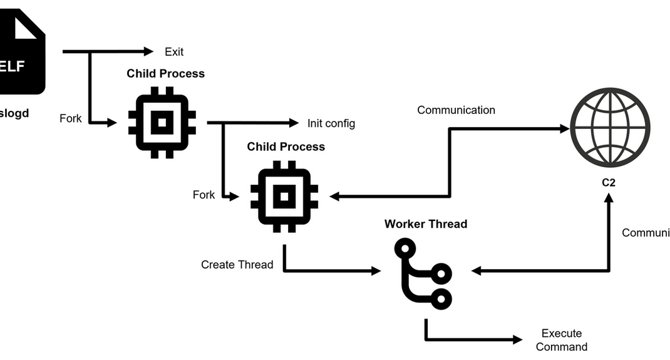
Image Credit: Securityaffairs
JPCERT warns of DslogdRAT malware deployed in Ivanti Connect Secure
- Researchers identified a new malware, named DslogdRAT, deployed after exploiting a now-patched flaw in Ivanti Connect Secure (ICS).
- JPCERT/CC researchers reported that a new malware, dubbed DslogdRAT, and a web shell were deployed by exploiting a zero-day vulnerability during attacks on Japanese organizations in December 2024.
- The vulnerability, tracked as CVE-2025-0282 (CVSS score: 9.0), is a stack-based buffer overflow that impacts Ivanti Connect Secure before version 22.7R2.5, Ivanti Policy Secure before version 22.7R1.2, and Ivanti Neurons for ZTA gateways before version 22.7R2.3.
- DslogdRAT spawns two child processes: one stays idle in a loop, while the second handles core functions like C2 communication and command execution via the pthread library.
Read Full Article
6 Likes
Mjtsai
368

Virus Protection for Phone
- Virus Protection for Phone is an app that claims to be trusted by millions of users worldwide.
- The app ranks #88 in the free utilities category in the US App Store and is the #43 top grossing utility.
- Despite being a free app, Virus Protection for Phone offers expensive subscription options.
- Due to iOS app sandboxing, it is unlikely that a virus protection app for iPhone is effective, raising concerns about the app's claims.
Read Full Article
22 Likes
Securityaffairs
315
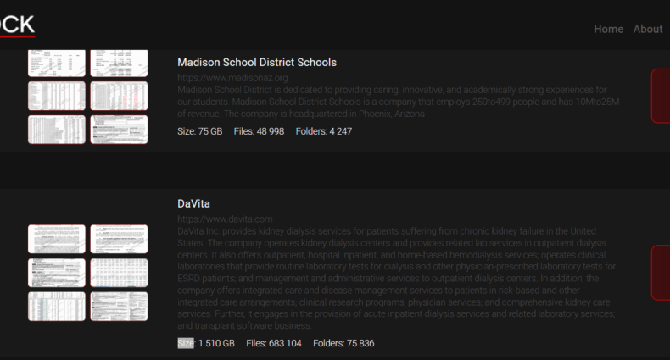
Image Credit: Securityaffairs
Interlock ransomware gang started leaking data allegedly stolen from leading kidney dialysis firm DaVita
- The Interlock ransomware gang claimed responsibility for the attack on the leading kidney dialysis company DaVita and leaked alleged stolen data.
- DaVita Inc. provides kidney dialysis services worldwide and is currently investigating and addressing a recent cybersecurity incident that disrupted certain internal operations.
- The Interlock ransomware gang claimed to have stolen 1510 GB of sensitive data, including patient records, insurance, and financial information.
- DaVita's network was encrypted by InterLock Ransomware and the gang leaked the alleged stolen files on their data leak site.
Read Full Article
18 Likes
Pymnts
279

Image Credit: Pymnts
FBI: US Ransomware Attacks Up 9%, Crypto Fraud up 66%
- Ransomware attacks in the US have increased by 9% compared to the previous year, according to the FBI's Internet Crime Complaint Center (IC3).
- Critical infrastructure organizations, including manufacturing, financial services, IT, healthcare, and government facilities, were targeted the most, accounting for nearly half of all ransomware complaints.
- In 2024, reported cyber and scam-related losses in the US reached $16.6 billion, marking a 33% increase from the previous year. Adults aged 60 and older were the most impacted demographic.
- There was also a significant rise in cryptocurrency fraud, with reported losses of at least $9.3 billion in 2024, a 66% increase from the previous year.
Read Full Article
16 Likes
Securityaffairs
31

Image Credit: Securityaffairs
Crooks exploit the death of Pope Francis
- Crooks exploit the death of Pope Francis, using public curiosity and emotion to launch scams and spread malware.
- Cybercriminals are ready to exploit any event of global interest, it has already happened in the past during events like Queen Elizabeth II’s death or the COVID-19 pandemic.
- Disinformation and fake news spread like wildfire during these events, with cybercriminals using AI-generated images and videos to fuel conspiracy theories and draw clicks and shares.
- To protect oneself, it is advised to keep the browser and OS up to date, use trusted web protection tools, be skeptical of sensational headlines, avoid clicking on suspicious links, and invest in a comprehensive security suite.
Read Full Article
1 Like
Securelist
405

Image Credit: Securelist
Operation SyncHole: Lazarus APT goes back to the well
- The Lazarus group conducted the "Operation SyncHole" attack campaign targeting South Korean organizations, combining a watering hole strategy and vulnerability exploitation in South Korean software.
- At least six organizations in South Korea's software, IT, financial, semiconductor, and telecommunications sectors were affected, with a focus on exploiting vulnerabilities in key software.
- Lazarus used variants of malicious tools like ThreatNeedle, Agamemnon downloader, and SIGNBT during the campaign, exploiting a vulnerability in Cross EX software to compromise organizations.
- The campaign involved a combination of watering hole attacks and exploitation of the Innorix Agent for lateral movement, impacting more organizations beyond the initially identified six.
- Multiple malware execution chains were observed, involving ThreatNeedle, wAgent, SIGNBT, and COPPERHEDGE, indicating the group's evolving strategies and advanced capabilities.
- The attackers leveraged vulnerabilities in South Korean software, such as Cross EX and Innorix Agent, for privilege escalation, lateral movement, and delivery of additional malware.
- Detailed analysis revealed the actor's post-exploitation tactics, Windows command execution, infrastructure setup using compromised C2 servers, and their mistake in using the taskkill command.
- The Lazarus group's evolving malware, asymmetric encryption use, and operational structure demonstrate a sophisticated and ongoing threat to South Korean entities, with a focus on supply chain attacks.
- Mitigation efforts involved reporting vulnerabilities to KrCERT, monitoring and analyzing malware behavior, and swift response to minimize damage and prevent further exploitation by the group.
- Kaspersky products detect the exploits and malware used in the attack, providing indicators of compromise to help organizations identify and remediate potential threats.
Read Full Article
24 Likes
Securityaffairs
81
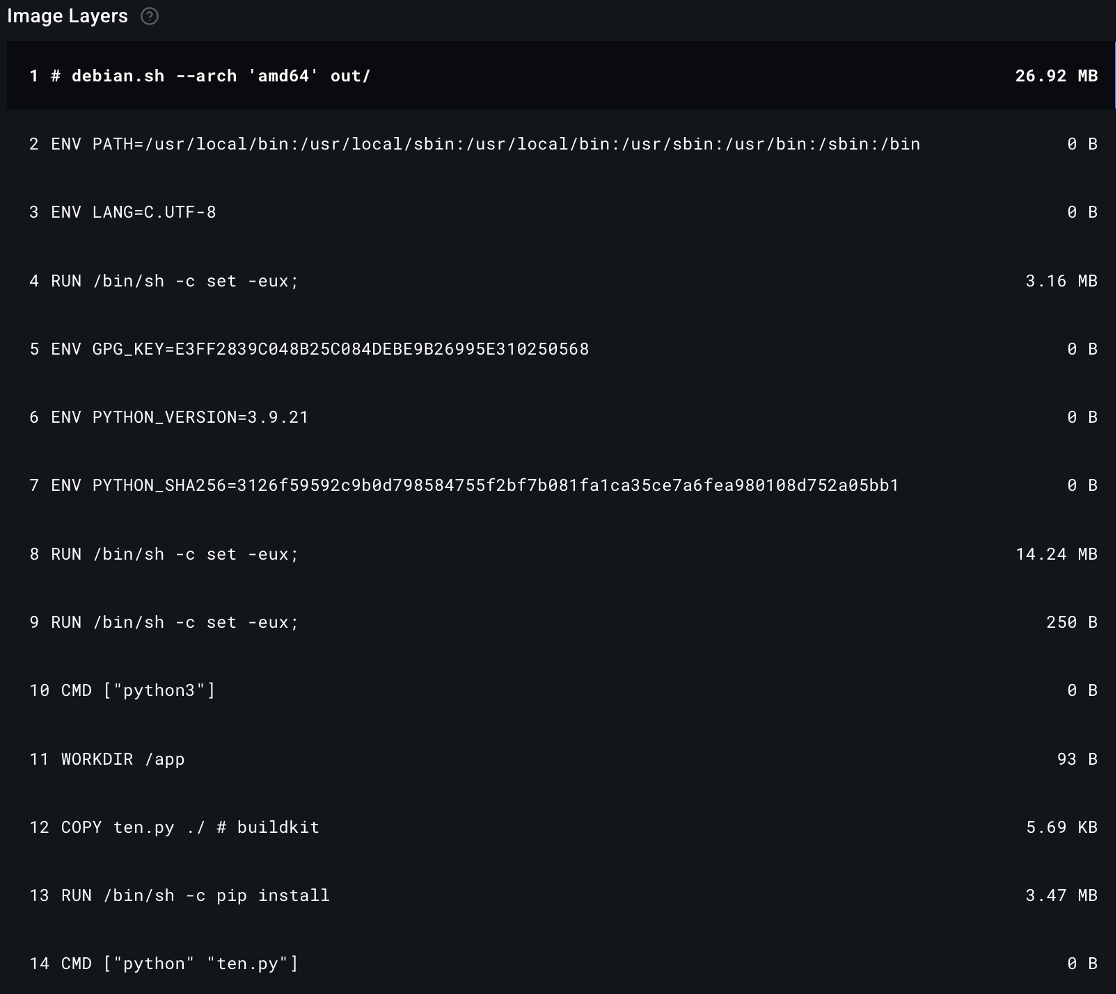
Image Credit: Securityaffairs
Crypto mining campaign targets Docker environments with new evasion technique
- A new malware campaign has been discovered that targets Docker environments to secretly mine cryptocurrency.
- The campaign deploys a malicious node connected to Teneo, a decentralized infrastructure network, to covertly monetize social media bandwidth.
- The malware uses an obfuscated script in the Docker image, which requires multiple iterations to reveal the actual malicious code.
- The attacker's DockerHub profile suggests a pattern of abuse, utilizing alternative methods of generating crypto with a Nexus network client.
Read Full Article
4 Likes
Cybersecurity-Insiders
67

Fog Ransomware Gang Now Demands $1 Trillion: A Curious Twist Tied to DOGE and Elon Musk
- The Fog Ransomware gang is now demanding a staggering $1 trillion from victims, inspired by Elon Musk's DOGE initiative.
- In a peculiar twist, similarities are drawn between the ransom note and a directive from Musk to federal employees in March 2025.
- The hackers demand victims to write an essay on their 'work accomplishments,' echoing Musk's unorthodox approach to productivity.
- Security experts suspect a deliberate connection between the ransom demands and Musk's initiatives to create a psychological impact.
- The cybercriminals behind Fog Ransomware may be imitating Musk's language to align their attack with his work efficiency tactics.
- There are divided opinions on whether this attack aims to tarnish Musk's reputation or exploit his cultural significance.
- The repetition of Musk's language in the ransom notes could be seen as an attempt to mock his government efficiency policies.
- This intersection of ransom demands and corporate governance highlights how hackers adapt to current events to enhance their attacks.
- The Fog Ransomware gang's $1 trillion demand resonates the evolving landscape of cybercrime in shaping public perception.
- This incident emphasizes that cybercrime is not solely about financial gain but also about manipulating public opinion in the digital age.
Read Full Article
4 Likes
Infoblox
112

Image Credit: Infoblox
Verizon 2025 DBIR findings coincide with dangers of malicious adtech
- Infoblox Threat Intel was recognized as a contributor in the Verizon 2025 Data Breach Investigation Report (DBIR), emphasizing the risks associated with malicious adtech in cybersecurity.
- The Verizon 2025 DBIR highlighted how adversaries have expanded their operations, concentrating on traffic distribution systems (TDS) and malicious adtech to conceal and advance their activities.
- Ransomware attacks have seen a 37% surge, targeting small organizations more frequently than larger enterprises, with human vulnerabilities such as phishing and credential abuse being major initial access vectors.
- Infostealers have become a significant threat, with 54% of ransomware victims identified having their domains in infostealer logs, linking infostealers to ransomware incidents.
- The report also highlighted the vulnerability of bring-your-own-device (BYOD) programs, where unprotected devices are targeted to collect credentials, and new social engineering tactics like 'prompt bombing' have emerged.
- Malicious adtech is identified as a crucial enabler for threat actors, facilitating the delivery of malware and phishing tools while remaining undetected, emphasizing the need for protective DNS solutions.
- Threat actors exploit adtech, including Traffic Distribution Systems (TDSs), to hide their operations and launch attacks, with Infoblox uncovering actors like Vane Viper and Vacant Viper using malicious adtech for their activities.
- By leveraging protective DNS solutions, organizations and individuals can mitigate the risks posed by malicious adtech, blocking a significant percentage of threats even before the first DNS query is made, as demonstrated by Infoblox.
- Education on malicious adtech threats can be obtained through events like the 2025 RSA Conference learning lab and visiting Infoblox's Threat Intel website for further insights and protection measures.
Read Full Article
6 Likes
Silicon
284
Image Credit: Silicon
The Ransomware Business Model: The State of Cybercrime
- Ransomware has transformed into a professional, corporate-like underground industry with sophisticated operations and financial support.
- Ransomware-as-a-Service (RaaS) platforms have made cybercrime accessible to individuals with limited technical skills by providing ready-made kits.
- The profitability of ransomware is driven by low upfront investment, global scalability, and the potential for substantial returns.
- Groups like LockBit and RansomHub operate from jurisdictions like Russia or North Korea, beyond the reach of Western law enforcement.
- Cryptocurrency plays a crucial role in ransomware payments due to its anonymity, speed, and global accessibility.
- Ransomware attackers have evolved to target strategically, conducting research on victims to set ransom amounts within their ability to pay.
- Smaller and mid-sized businesses are increasingly targeted by ransomware groups due to their vulnerability and lack of robust cybersecurity measures.
- A zero-trust security model with strong identity controls, network segmentation, real-time detection, and privilege management is crucial in combating modern ransomware threats.
- AI is used by both attackers and defenders to enhance their capabilities in crafting attacks, detecting threats, and responding swiftly.
- Effective cybersecurity measures include consistent patching, multi-factor authentication, employee training, and backup resilience.
- Businesses must adopt proactive planning, incident response protocols, and crisis communication strategies to mitigate the impact of ransomware attacks.
Read Full Article
17 Likes
Securityaffairs
311

Image Credit: Securityaffairs
The popular xrpl.js Ripple cryptocurrency library was compromised in a supply chain attack
- The xrpl.js Ripple cryptocurrency library was compromised in a supply chain attack aimed at stealing users’ private keys.
- Threat actors compromised the Ripple cryptocurrency npm JavaScript library xrpl.js to harvest users’ private keys.
- The researchers investigated the supply chain attack and discovered that five xrpl package versions contained malicious code.
- Users of the xrpl.js library are urged to update to versions 4.2.5 or 2.14.3 to mitigate risks from the recent supply chain attack.
Read Full Article
18 Likes
Medium
90

Image Credit: Medium
Heap Encryption
- Heap Encryption involves storing payload in the process heap in an encrypted form.
- This technique adds an extra layer of obfuscation and helps evade static analysis tools.
- The code demonstrates the implementation of Heap Encryption using HeapAlloc in Windows OS.
- By using XOR encryption, the shellcode in memory is obfuscated and then decrypted for execution.
Read Full Article
5 Likes
Securityaffairs
446

Image Credit: Securityaffairs
Millions of SK Telecom customers are potentially at risk following USIM data compromise
- SK Telecom, South Korea's largest wireless telecom company, reported that threat actors accessed customer Universal Subscriber Identity Module (USIM) info through a malware attack.
- The company detected the infection on April 19, 2025, and promptly reported it to the Korea Internet & Security Agency (KISA), sanitized the impacted systems, and isolated the suspected hacking device.
- No cases of misuse of the information have been confirmed to date, but SK Telecom has enhanced defensive measures, blocked illegal SIM card changes, and abnormal authentication attempts.
- The company is offering impacted customers a free subscription to the 'SIM protection service' as an additional security measure.
Read Full Article
26 Likes
For uninterrupted reading, download the app