Malware News
Cybersecurity-Insiders
243

New Chimera Malware Emerges, Using AI to Outsmart Anti-Malware Solutions and Demand Ransom
- Chimera malware, utilizing advanced AI tools, poses a new threat by being challenging to detect with conventional anti-malware systems.
- It targets multiple platforms like Windows and MacOS, making it more adaptable and dangerous for businesses with diverse operating systems.
- Chimera specifically attacks Point of Sale (POS) systems, encrypts data, and steals sensitive information, increasing risks for businesses.
- The rise of advanced malware threats like Chimera and new strains from Venom Spider highlights the need for enhanced cybersecurity measures to combat evolving cybercrime tactics.
Read Full Article
14 Likes
Silicon
355

Image Credit: Silicon
NCSC Warns UK Retailers After Spate Of Cyberattacks
- UK retailers are being warned by the NCSC to strengthen their cyber defenses following a series of cyberattacks on high street retailers.
- Major retailers like Marks & Spencer, Co-op, and Harrods have all been targeted by cyberattacks, leading to disruptions in their online operations and IT systems.
- The NCSC is working with affected organizations to understand the nature of these attacks and provide expert advice to enhance cyber defenses.
- NCSC CEO Dr. Richard Horne emphasizes the importance of organizations implementing appropriate measures to prevent, respond, and recover from cyberattacks, urging leaders to follow the guidance on the NCSC website.
Read Full Article
21 Likes
Securityaffairs
284
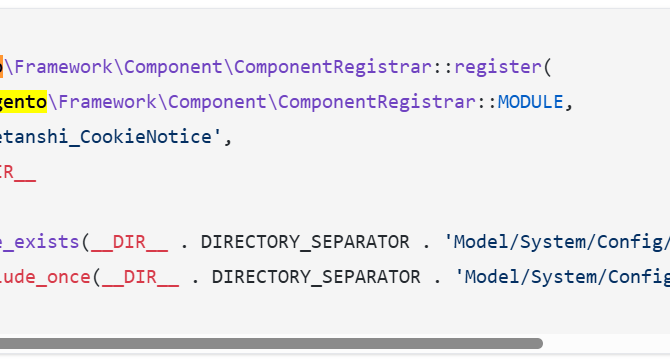
Image Credit: Securityaffairs
Sansec uncovered a supply chain attack via 21 backdoored Magento extensions
- Supply chain attack via 21 backdoored Magento extensions affected 500–1,000 e-stores, including a $40B multinational e-store.
- Researchers at Sansec uncovered a coordinated supply chain attack where a backdoor was hidden in 21 applications, lingering undiscovered for 6 years.
- The malicious code injection was recently discovered after threat actors compromised e-commerce servers through the backdoored extensions.
- Impacted vendors include Tigren, Magesolution (MGS), and Meetanshi, with varied responses received when contacted by Sansec.
Read Full Article
17 Likes
Securityaffairs
204
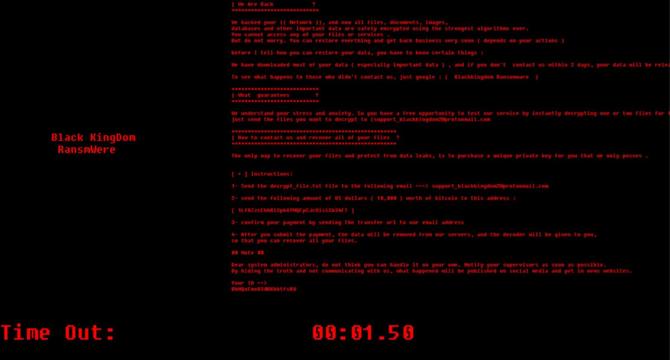
Image Credit: Securityaffairs
US authorities have indicted Black Kingdom ransomware admin
- 36-year-old Yemeni man indicted in the U.S. for 1,500 attacks on Microsoft Exchange servers as an admin of Black Kingdom ransomware.
- FBI investigating the case with the help of the New Zealand Police.
- The man demanded ransom payments of $10,000 in Bitcoin from the victims and is believed to be residing in Yemen.
- If convicted, the man faces up to five years in federal prison for each charge related to deploying Black Kingdom ransomware on vulnerable Exchange mail servers.
Read Full Article
12 Likes
Securityaffairs
333
Image Credit: Securityaffairs
Malicious Go Modules designed to wipe Linux systems
- Researchers discovered 3 malicious Go modules containing hidden code to wipe a Linux system's main disk, making it unbootable.
- The malware-laced modules fetch destructive payloads to execute a shell script, permanently destroying data on the primary disk.
- Attackers exploit Go ecosystem's decentralized nature to create confusion, making it hard for developers to distinguish between legitimate and malicious modules.
- Experts emphasize the importance of strong supply chain security and recommend proactive code audits and continuous monitoring to combat such sophisticated threats.
Read Full Article
20 Likes
Securityaffairs
222

Image Credit: Securityaffairs
Security Affairs newsletter Round 522 by Pierluigi Paganini – INTERNATIONAL EDITION
- Rhysida Ransomware gang claims hack of the Government of Peru & DragonForce group claims data theft after Co-op cyberattack.
- U.S. CISA adds multiple new vulnerabilities to its Known Exploited Vulnerabilities catalog, including Yii Framework, Commvault Command Center, SonicWall SMA100, and Apache HTTP Server flaws.
- Luxury department store Harrods and Canadian electric utility Nova Scotia Power suffer cyberattacks. Pro-Russia hacktivist group targets Dutch organizations.
- Various cybersecurity incidents reported, including phishing domains associated with LabHost PhaaS platform, critical vulnerabilities actively exploited in the wild, and emergence of new malware strains targeting different sectors.
Read Full Article
13 Likes
Securityaffairs
405

Image Credit: Securityaffairs
Rhysida Ransomware gang claims the hack of the Government of Peru
- The Rhysida Ransomware gang claims responsibility for hacking the Government of Peru through the Gob.pe platform.
- The group has published images of documents allegedly stolen from the Peruvian government platform and is demanding a ransom of five bitcoins within seven days.
- Rhysida ransomware group has been active since May 2023, targeting numerous organizations across various sectors, including education, healthcare, manufacturing, information technology, and government.
- In response to the attacks, the FBI and CISA issued a joint Cybersecurity Advisory warning about Rhysida ransomware and providing information on tactics, techniques, and procedures associated with the group.
Read Full Article
24 Likes
Securityaffairs
249

Image Credit: Securityaffairs
DragonForce group claims the theft of data after Co-op cyberattack
- Hackers claiming to be DragonForce revealed that they stole major customer and employee data from the recent Co-op cyberattack, providing proof to the BBC.
- Initially, Co-op stated there was no evidence of customer data compromise, but later confirmed that current and past members' data was accessed by threat actors.
- The attackers accessed Co-op's internal Teams, leaked staff credentials, and obtained 10,000 customer records containing personal details like names, addresses, emails, and phone numbers.
- DragonForce group, also responsible for attacks on M&S, claimed to have information on 20 million Co-op members, indicating potential risk to Co-op's membership scheme.
Read Full Article
15 Likes
Cybersafe
106

Image Credit: Cybersafe
U.S. indicts Black Kingdom Ransomware Operator for Microsoft Exchange Attacks
- 36-year-old Rami Khaled Ahmed, a Yemeni national, indicted for operating Black Kingdom ransomware targeting Microsoft Exchange servers in over 1,500 attacks worldwide.
- Ahmed and co-conspirators infected systems of various victims, demanding $10,000 in Bitcoin for decryption.
- Black Kingdom ransomware exploited ProxyLogon vulnerabilities in Microsoft Exchange servers to gain access, compromising around 1,500 servers.
- Ahmed faces federal charges that could lead to 15 years in U.S. federal prison if convicted. He is believed to be currently in Yemen.
Read Full Article
6 Likes
Sentinelone
98

Image Credit: Sentinelone
DragonForce Ransomware Gang | From Hacktivists to High Street Extortionists
- DragonForce ransomware group has been targeting UK retailers, causing major disruptions to businesses like Harrods and Marks and Spencer.
- The group has targeted various entities worldwide and operates a multi-extortion model, threatening with data leaks and reputational damage.
- Initial access is gained through phishing, vulnerabilities, or stolen credentials, utilizing tools like Cobalt Strike and Remote Management tools.
- DragonForce operators have exploited vulnerabilities like Apache Log4j2 Remote Code Execution and Ivanti Connect Secure Authentication Bypass.
- Ransomware payloads evolved from LockBit to a bespoke version based on the Conti v3 codebase, offering customization for affiliates.
- Affiliates can customize DragonForce ransomware, manage multiple variants for different platforms, and utilize a range of encryption modes.
- DragonForce introduced a 'white-label' branding service, allowing affiliates to disguise the ransomware and share ransom payouts with the group.
- The group's evolution towards a 'Ransomware Cartel' model signifies a shift towards increasing profitability and expanding operations.
- SentinelOne Singularity Platform provides protection against DragonForce ransomware, detecting malicious behaviors and payloads.
- Recent attacks emphasize the importance of strong cybersecurity practices and incident response procedures for businesses.
Read Full Article
5 Likes
Securityaffairs
196

Image Credit: Securityaffairs
Luxury department store Harrods suffered a cyberattack
- Luxury department store Harrods confirmed a cyberattack, making it the third major UK retailer targeted in one week.
- The cyberattack involved attempted unauthorized access to some of Harrods' systems, prompting immediate proactive steps from the IT security team.
- Harrods restricted internet access at its sites but maintained operations, including its Knightsbridge store and online platform.
- Technical details of the attacks on Harrods were not disclosed, and it remains uncertain if a data breach occurred. The attacks on Marks and Spencer and the Co-op were also mentioned in the context of recent retail cyberattacks.
Read Full Article
11 Likes
Krebsonsecurity
236

Alleged ‘Scattered Spider’ Member Extradited to U.S.
- A 23-year-old Scottish man, Tyler Robert Buchanan, believed to be a member of the Scattered Spider cybercrime group, has been extradited to the United States from Spain.
- Buchanan is facing charges of wire fraud, conspiracy, and identity theft for allegedly hacking into numerous companies and controlling over $26 million in stolen funds.
- The Scattered Spider group is known for breaking into major technology companies globally and Buchanan was arrested in Spain last year for SMS-based phishing attacks in 2022.
- He fled the UK in 2023 after his home was invaded by a rival cybercrime gang, leading to his arrest in 2024 while attempting to board a flight to Italy.
- Although tied to the Scattered Spider group who carried out ransomware attacks in 2023, Buchanan's case focuses on SMS phishing campaigns and SIM-swapping attacks.
- Investigations revealed Buchanan's connection to phishing domains used in the 2022 campaign and the involvement in targeting multiple companies globally.
- FBI evidence indicated Buchanan's communication regarding proceeds of SIM swapping and cryptocurrency transactions exceeding $26 million.
- Federal charges have also been filed against four other alleged Scattered Spider members in Los Angeles, with Buchanan facing potential prison time for his crimes.
- Buchanan's attorney has not responded to comments, and he remains in custody without bail pending trial, with a preliminary hearing scheduled for May 6.
Read Full Article
14 Likes
Mjtsai
420

Why Some Apps Sometimes Launch Extremely Slowly
- Some apps may launch extremely slowly on Macs, taking more than 30 seconds or even several minutes due to the computation of SHA-256 hashes for the contents of each item in the app's Frameworks folder.
- Long launch times are likely caused by computing hashes for protected code in the Frameworks folder, especially when those hashes have been flushed from their cache.
- Disable System Integrity Protection (SIP) and setting security mode to Permissive on Apple silicon Macs can help prevent long launch times in most cases.
- Even after passing the initial Gatekeeper check, macOS continues to recheck code that is no longer quarantined if Launch Services has no record of it or if the app has been moved.
Read Full Article
25 Likes
Securityaffairs
116
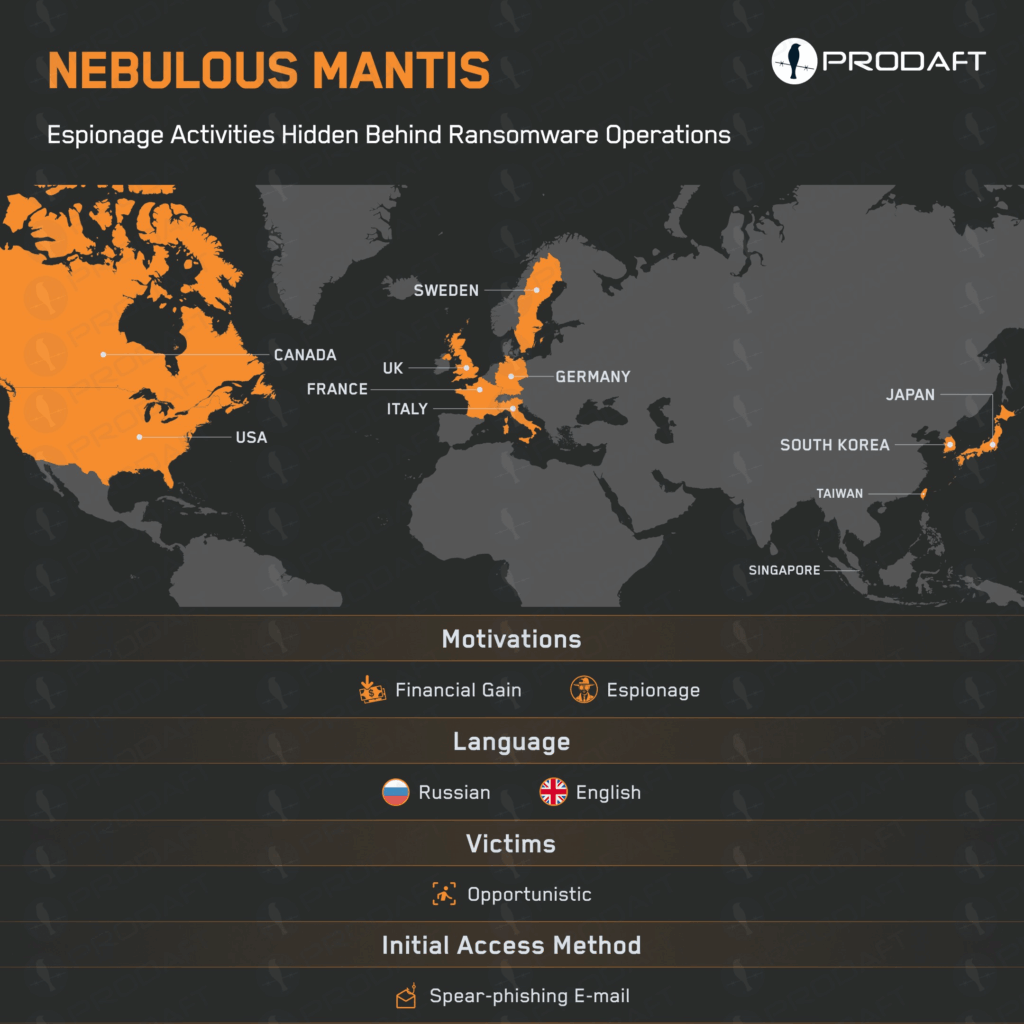
Image Credit: Securityaffairs
Russia-linked group Nebulous Mantis targets NATO-related defense organizations
- Russian-speaking cyber espionage group Nebulous Mantis, also known as Cuba, STORM-0978, Tropical Scorpius, UNC2596, has been targeting critical infrastructure, governments, and NATO-linked entities using RomCom RAT and Hancitor since 2019.
- Nebulous Mantis deploys RomCom via spear-phishing for espionage, lateral movement, and data theft. The group continuously evolves its C2 infrastructure using advanced evasion techniques and bulletproof hosting to maintain persistence and evade detection.
- The APT group imitates trusted services like OneDrive to trick victims into downloading infected files hosted on Mediafire. Their multi-phase intrusions involve initial access, privilege escalation, data exfiltration, modular malware, LOTL techniques, and evasive C2 infrastructure.
- Nebulous Mantis uses RomCom malware in multi-stage attacks involving system profiling, credential harvesting, AD/domain enumeration, lateral movement, and data staging. The group maintains persistence through registry manipulation and exhibits operational discipline in minimizing their footprint.
Read Full Article
6 Likes
Silicon
76

Image Credit: Silicon
Co-op IT System Partly Shutdown After Hack Attempt – Report
- A cyber incident at the Co-op led to a partial shutdown of its IT systems, affecting services such as stock monitoring and remote access for some employees.
- Security measures were implemented after attempts to gain unauthorized access, impacting back-office and call center services.
- Despite the disruption, Co-op assured that stores and services like home deliveries and funeral homes are operating as usual.
- This incident adds to the series of cyber attacks within the UK retail sector, with retailers like M&S, Morrisons, Tesco, and WH Smith facing cybersecurity challenges in recent years.
Read Full Article
4 Likes
For uninterrupted reading, download the app