Malware News
Securityaffairs
339
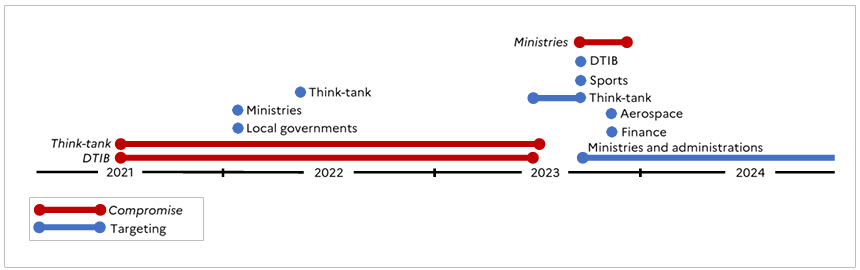
Image Credit: Securityaffairs
France links Russian APT28 to attacks on dozen French entities
- France attributes cyberattacks on a dozen entities to Russia-connected APT28.
- APT28 targeted French government bodies, local governments, DTIB, aerospace, research, think-tanks, and financial entities since 2021.
- The cyber espionage group APT28, also known as Fancy Bear, operates out of Russia's GRU military unit 26165.
- APT28's attack techniques involve phishing, brute-force attacks, and zero-day exploits, frequently targeting Roundcube email servers.
Read Full Article
20 Likes
Cybersecurity-Insiders
170

DragonForce Ransomware behind Mark and Spencer digital outage
- Marks & Spencer (M&S) experienced a cyber attack by the DragonForce group, causing significant disruption to their operations.
- DragonForce is known for employing 'double extortion' tactics, where they steal and encrypt data, demanding ransom in cryptocurrency.
- M&S has been working to restore systems following the attack, but customers still face online booking issues and website glitches.
- The lack of an official statement from M&S raises concerns about the extent of the attack and recovery time.
- Cyber attacks like these not only disrupt business operations but also harm a company's reputation and consumer trust.
- Paying ransom in such situations is strongly advised against by law enforcement agencies due to the risks involved.
- Theft of sensitive company data in ransomware attacks can lead to long-term security risks and impacts on customers' safety.
- Companies should report cyber attacks to law enforcement and enhance their cybersecurity measures to prevent future breaches.
- The incident highlights the growing threat of cybercrime and the need for businesses to prioritize cybersecurity defenses.
- Proactive planning and cooperation with law enforcement are crucial in mitigating the damage caused by cybercriminal activities.
Read Full Article
10 Likes
Infoblox
371

Image Credit: Infoblox
The Essential Role of Zero Trust DNS in Modern Security
- Microsoft has announced the public preview of Zero Trust DNS (ZTDNS) in Windows 11 Insider builds
- ZTDNS enforces domain-name-based network access controls and integrates Windows DNS client with trusted Protective DNS (PDNS) servers
- Zero Trust DNS is important to enhance security and adhere to the 'deny by default' principle of Zero Trust
- PDNS preemptively blocks threats by leveraging DNS-focused threat intelligence, reducing the likelihood of successful breaches
Read Full Article
22 Likes
Cybersecurity-Insiders
443

Insider Threat alert as Cybersecurity firm CEO plants malware into hospital network
- CEO of Veritaco, a cybersecurity company, arrested for planting malware into Saint Anthony Hospital's network.
- Jefferey Bowie charged with violating the Oklahoma Computer Crimes Act for compromising sensitive systems.
- Bowie gained access to the hospital's network under the guise of reviewing medical investigation reports.
- This incident highlights the growing threat of insider attacks in the healthcare sector, emphasizing the need for proactive measures to protect critical systems.
Read Full Article
26 Likes
Siliconangle
439

Image Credit: Siliconangle
Recorded Future launches Malware Intelligence to automate malware detection and response
- Threat intelligence firm Recorded Future has launched a new platform called Malware Intelligence.
- Malware Intelligence aims to automate the detection of emerging malware threats, speed up threat hunting, and streamline incident response.
- The platform connects malware samples to threat actor infrastructure and the global threat landscape to provide real-time insights to security teams.
- Malware Intelligence combines AI-driven detection with features like AutoYARA and dynamic analysis to stay ahead of evolving malware variants.
Read Full Article
26 Likes
Securelist
434

Image Credit: Securelist
Outlaw cybergang attacking targets worldwide
- Outlaw (also known as “Dota”) is a Perl-based crypto mining botnet that targets Linux environments by exploiting weak or default SSH credentials.
- The threat actor behind Outlaw uses tactics like downloading first-stage scripts, monitoring processes, and maintaining persistence on infected machines.
- The malware used by Outlaw includes an IRC-based botnet client acting as a backdoor, supporting malicious activities like DDoS attacks, file operations, and command execution.
- Outlaw gang's activities have been identified in countries like the United States, Germany, Italy, Thailand, Singapore, Taiwan, Canada, and Brazil.
- Recommendations to protect against Outlaw include hardening SSH servers with key-based authentication, custom configurations, and additional security parameters.
- Outlaw's techniques include obfuscation, malicious XMRig miners, customized malware, and a diverse range of malicious activities.
- Security practitioners can adopt measures like limiting SSH access, using tools like Fail2Ban, and monitoring for suspicious processes to mitigate the Outlaw threat effectively.
- The Outlaw gang employs various tactics, techniques, and procedures (TTPs) categorized under execution, persistence, defense evasion, credential access, discovery, lateral movement, collection, command and control, exfiltration, and impact.
- Indicators of Compromise (IoCs) related to Outlaw include cryptographic hashes, specific file names, IP addresses, Monero wallet information, and more.
Read Full Article
26 Likes
TechCrunch
376

Image Credit: TechCrunch
Government hackers are leading the use of attributed zero-days, Google says
- Government hackers were responsible for the majority of attributed zero-day exploits used in real-world cyberattacks last year, according to Google.
- Google's report shows a decrease in zero-day exploitation, but at least 23 zero-day exploits were linked to government-backed hackers.
- Among the attributed zero-days, 10 were attributed to hackers working directly for governments, including 5 linked to China and 5 to North Korea.
- The remaining 11 attributed zero-days were likely exploited by cybercriminals, such as ransomware operators targeting enterprise devices.
Read Full Article
22 Likes
Cybersecurity-Insiders
107

Akira Ransomware attack on Hitachi Vantara Servers
- Hitachi Vantara, a subsidiary of Hitachi, experienced a cyberattack by Akira Ransomware gang.
- To contain the malware, several Hitachi Vantara servers were taken offline.
- The company is engaging with cybersecurity experts to recover from the attack.
- The Akira Ransomware group has targeted nearly 300 organizations and collected over $42 million in ransom payments.
Read Full Article
6 Likes
Securityaffairs
188

Image Credit: Securityaffairs
Earth Kurma APT is actively targeting government and telecommunications orgs in Southeast Asia
- Earth Kurma APT carried out a sophisticated campaign against government and telecommunications sectors in Southeast Asia.
- Threat actors used custom malware, rootkits, and cloud storage for espionage, credential theft, and data exfiltration.
- The campaign primarily targeted the Philippines, Vietnam, Thailand, and Malaysia, posing a high business risk.
- Earth Kurma is a new APT group targeting Southeast Asian government and telecom sectors, remaining highly active and adaptable.
Read Full Article
11 Likes
Silicon
161
Image Credit: Silicon
M&S Tells Distribution Centre Staff To Stay At Home
- Marks & Spencer tells agency staff at its distribution center to stay at home due to a cyberattack.
- The company stopped online and app orders and has fallen 8% since the attack was disclosed.
- Around 200 agency staff were affected by the decision and the company is working with experts to resolve the issue.
- Customer data has not been compromised, but experts advise maintaining vigilance against phishing attempts.
Read Full Article
9 Likes
TechCrunch
403

Image Credit: TechCrunch
Citizen Lab says exiled Uyghur leaders targeted with Windows spyware
- Unknown hackers targeted exiled Uyghur community leaders using Windows spyware.
- Citizen Lab, a digital rights research group, uncovered the espionage campaign.
- Hacking campaign targeted World Uyghur Congress (WUC) members.
- The campaign involved phishing emails and impersonation of trusted contacts.
Read Full Article
24 Likes
Medium
170

Image Credit: Medium
The Relentless Grip of Ransomware
- The rise of ransomware incidents is a major concern, with ransomware involved in nearly half of all data breaches.
- While the median ransom payment decreased to $115,000 in 2024, a growing number of victim organizations are choosing not to pay the ransom.
- Small and medium-sized businesses (SMBs) are particularly vulnerable, with ransomware being present in 88% of breaches affecting these organizations.
- The costs associated with recovery, downtime, reputational damage, and potential regulatory fines can outweigh the ransom demand itself.
Read Full Article
10 Likes
Securityaffairs
71

Image Credit: Securityaffairs
PoC rootkit Curing evades traditional Linux detection systems
- Researchers created a PoC rootkit named Curing that uses Linux's io_uring feature to evade traditional system call monitoring.
- Curing is a proof-of-concept rootkit that utilizes io_uring for performing tasks without syscalls, making it undetectable by security tools.
- io_uring is a Linux API for asynchronous I/O that bypasses system calls, making syscall-based security tools ineffective.
- Many Linux EDRs are unable to monitor io_uring-based activity, posing a risk to current Linux security solutions.
Read Full Article
4 Likes
Securityaffairs
76

Image Credit: Securityaffairs
Security Affairs newsletter Round 521 by Pierluigi Paganini – INTERNATIONAL EDITION
- African multinational telco giant MTN Group disclosed a data breach
- CEO of cybersecurity firm charged with installing malware on hospital systems
- JPCERT warns of DslogdRAT malware deployed in Ivanti Connect Secure
- SAP NetWeaver zero-day allegedly exploited by an initial access broker
Read Full Article
4 Likes
Cybersecurity-Insiders
404

A Comprehensive Review of BlackFog’s ADX Platform for Ransomware Defense
- Ransomware has evolved into a major societal crisis, impacting essential services, economies, and communities, as seen in the Colonial Pipeline attack of 2021.
- Ransomware attacks have become more targeted, affecting critical services like healthcare, education, government, and supply chains.
- The threat of ransomware is escalating towards critical infrastructure such as water treatment facilities and energy providers.
- BlackFog's ADX technology focuses on preventing data exfiltration rather than just detecting intrusions, providing real-time threat neutralization.
- Key features of BlackFog's platform include proactive blocking, AI-driven threat analysis, on-device protection, real-time geofencing, and air gap protection.
- BlackFog's multi-layered approach offers enterprises robust defense against ransomware, ensuring business continuity and data protection.
- By stopping data exfiltration, BlackFog prevents ransomware attacks at the source and safeguards sensitive information and trade secrets.
- BlackFog's ADX technology stands out by preventing data loss and extortion in real-time, cutting off cybercriminals' ability to profit from ransomware.
- BlackFog's innovative approach challenges the status quo by focusing on preventing data exfiltration, rendering ransomware threats powerless.
- Founded in 2015, BlackFog is a global AI-based cybersecurity company that specializes in on-device ADX technology, offering comprehensive protection against ransomware and data loss.
Read Full Article
24 Likes
For uninterrupted reading, download the app