Malware News
Cybersecurity-Insiders
225

Image Credit: Cybersecurity-Insiders
Ransomware Resurgence: 5 Lessons from Healthcare’s Cyber Frontlines
- Healthcare organizations faced a surge in ransomware attacks in 2024, with recovery costs averaging over $2.5 million per incident.
- Ransomware-as-a-service has made attacks more accessible, with healthcare being targeted due to the critical nature of operations.
- Patient data is highly valuable and often sold on the dark web, contributing to the attractiveness of healthcare systems to cybercriminals.
- Legacy systems and connected devices in healthcare present security risks that can be exploited by ransomware attackers.
- Ransomware attacks not only incur financial costs but also severely impact patient care and safety, leading to delayed treatments and diverted emergency services.
- Healthcare organizations need to bolster cybersecurity measures, with many still allocating less than 10% of their IT budget to cybersecurity.
- Recommendations for strengthening resilience include regular risk assessments, advanced cybersecurity tools, staff training, secure backups, and access controls.
- Ransomware attacks pose a threat to patient safety and public health, necessitating proactive cybersecurity measures in healthcare.
- The sophistication of ransomware groups and their focus on healthcare systems emphasize the importance of investing in solutions for network defense and operational continuity.
- Cybersecurity is crucial for patient outcomes in healthcare, requiring investments in proactive defense measures to combat escalating cyber threats.
Read Full Article
13 Likes
Qualys
322

Image Credit: Qualys
Inside LockBit: Defense Lessons from the Leaked LockBit Negotiations
- The LockBit ransomware gang recently faced a data breach with dark web panels defaced, leading to a MySQL database dump.
- The leaked data includes victim negotiation messages and bitcoin addresses from LockBit's affiliate panel.
- LockBit has evolved since 2019, releasing versions like LockBit 2.0 and LockBit 3.0 with expanded capabilities.
- LockBit operates on an affiliate model, where core developers create ransomware and affiliates execute attacks.
- Their attacks involve initial access, lateral movement, data exfiltration, encryption, and ransom note delivery.
- Leaked chats indicate LockBit demands ransom payment in Bitcoin and offers discounts for payments in Monero.
- The article highlights critical CVEs exploited by LockBit that organizations should prioritize patching or mitigating.
- Systems beyond traditional endpoints like Veeam, vCenter, ESXi, NAS devices, and file transfer tools are also targeted by LockBit.
- Recommendations include patching known vulnerabilities, securing backup infrastructure, and enforcing strong credentials.
- Understanding LockBit's tactics and enhancing security hygiene are crucial to bolster defenses against ransomware threats.
Read Full Article
19 Likes
Securityaffairs
379
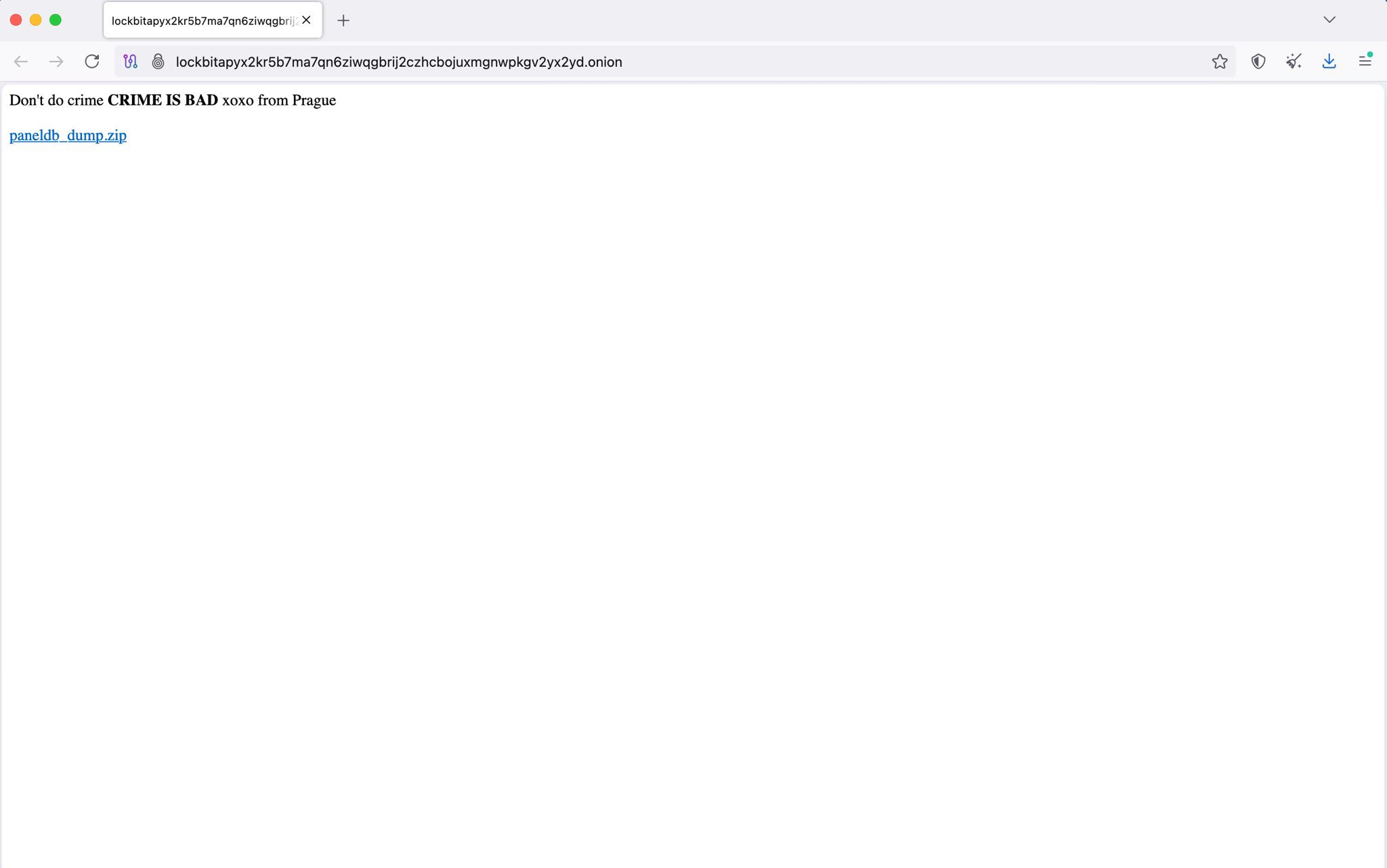
Image Credit: Securityaffairs
The LockBit ransomware site was breached, database dump was leaked online
- The LockBit ransomware group's dark web site was compromised, leading to the leak of data from the backend infrastructure.
- Hackers defaced the dark web site and posted a message along with a link to a dump of the MySQL database containing various data, including victim chat logs and user data.
- BleepingComputer analyzed the leaked database, revealing 20 tables with information such as BTC addresses, victim chat logs, and user data with plaintext passwords.
- Italian cybersecurity expert Emanuele De Lucia extracted over 60k addresses from the dump, indicating the potential presence of critical data for developing decryption tools. The chat logs showed ransom amounts ranging from $50,000 to $1,500,000.
Read Full Article
22 Likes
Cybersecurity-Insiders
22

Image Credit: Cybersecurity-Insiders
Ransomware news headlines trending on Google
- The LockBit ransomware group, known for its cybercriminal activities, recently became a victim of a data breach, leading to the exposure of sensitive data.
- Oettinger Breweries, a German beer producer, was targeted by the Ransom House ransomware group, resulting in the compromise of critical company data.
- The Play Ransomware group is exploiting Windows vulnerabilities to launch attacks on businesses in various sectors, aiming to encrypt data and gather intelligence from compromised networks.
- These incidents highlight the increasing threats posed by cybercriminals, with rivals targeting each other and forming alliances, emphasizing the critical need for robust cybersecurity measures and collaboration between public and private entities.
Read Full Article
1 Like
Securityaffairs
424

Image Credit: Securityaffairs
Play ransomware affiliate leveraged zero-day to deploy malware
- The Play ransomware gang exploited a Windows Common Log File System flaw in zero-day attacks to deploy malware, gaining SYSTEM privileges on compromised systems.
- The vulnerability, CVE-2025-29824, allowed attackers to elevate privileges locally, leading to confirmed exploits in the wild by the Play ransomware gang.
- Microsoft addressed the flaw in April's Patch Tuesday security updates, after it was added to the Known Exploited Vulnerabilities catalog by CISA.
- The exploit was used by multiple threat actors before being patched, with connections to malware like PipeMagic and Storm-2460, used by Balloonfly cybercrime group.
Read Full Article
25 Likes
Cybersecurity-Insiders
150

Image Credit: Cybersecurity-Insiders
NSO group slapped with $168m penalty for spreading Pegasus Malware
- After a six-year legal battle, Meta wins a $168 million penalty against NSO Group for spreading the Pegasus malware, targeting WhatsApp and Instagram users.
- Meta's collaboration with Citizen Lab revealed over 1,400 WhatsApp users were affected by the spyware, leading to the substantial penalty.
- The court also ordered NSO Group to pay $444,000 to Meta, amplifying the victory for privacy advocates and tech industry concerning digital surveillance.
- NSO Group's Pegasus malware, associated with high-profile spying incidents, including Jeff Bezos and Amazon.
- Meta's lawsuit accused NSO Group of breaching privacy rights and compromising the security of its platforms with illegal surveillance tactics.
- Pegasus allows for remote access to phones, data theft, location tracking, and invasive monitoring through cameras and microphones.
- Meta's legal win sets a precedent for accountability in digital surveillance, emphasizing the need for stricter regulations to protect user privacy.
- Collaboration between companies like Meta and research groups like Citizen Lab is vital in combatting cyber-espionage and safeguarding user data.
- The ruling underscores the importance of privacy protection as surveillance tools advance, urging collective efforts to defend against unauthorized spying.
- Meta's triumph signals a call for action to uphold digital rights and deter illegal surveillance practices in the evolving landscape of cybersecurity.
Read Full Article
9 Likes
Socprime
336

Image Credit: Socprime
Gunra Ransomware Detection: New Threat Targets Various Industries Globally Using Double-Extortion Tactics and Advanced Malicious Behaviors
- Ransomware recovery costs have surged to $2.73 million in 2024, marking a 500% increase over the previous year, emphasizing the financial impact of cyberattacks.
- Gunra ransomware, targeting Windows-based systems in industries like real estate and pharmaceuticals, utilizes double-extortion tactics, encrypting data and exfiltrating sensitive information to pressure victims into paying.
- As ransomware attacks increase globally, the Gunra ransomware group has emerged, employing advanced evasion and anti-analysis features to avoid detection and hinder forensic analysis.
- Gunra ransomware employs various advanced techniques like anti-debugging, anti-reversing, and detection evasion, demonstrating sophistication in the cyber threat landscape and emphasizing the need for proactive measures like regular backups and network segmentation.
Read Full Article
20 Likes
Securelist
101

Image Credit: Securelist
State of ransomware in 2025
- Kaspersky reports a decrease in ransomware detections by 18% from 2023 to 2024.
- 41.6% of incidents at organizations requiring incident response services were related to ransomware in 2024.
- Ransomware-as-a-Service (RaaS) remains dominant, simplifying attacks for cybercriminals.
- Ransomware groups diversified in 2024, targeting Windows, Linux, and VMware systems.
- While overall ransomware payments decreased, average ransom payments surged in 2024.
- Some ransomware groups shifted focus to data exfiltration alongside encryption.
- Several major ransomware groups faced disruptions in 2024, but new groups quickly emerged.
- Ransomware groups increasingly develop custom toolkits to evade detection.
- Global trends show a shift towards targeted ransomware attacks over general attacks.
- Ransomware is expected to evolve by exploiting unconventional vulnerabilities in 2025.
Read Full Article
6 Likes
Securityaffairs
8

Image Credit: Securityaffairs
NSO Group must pay WhatsApp over $167M in damages for attacks on its users
- NSO Group has been ordered by a U.S. jury to pay WhatsApp over $167 million in damages for using Pegasus spyware to target over 1,400 individuals, violating U.S. laws.
- The jury ruling came after a five-year legal battle, with NSO Group being asked to pay punitive damages exceeding $167 million and compensatory damages exceeding $444,000.
- WhatsApp's post mentioned that the decision serves as a critical deterrent against malicious activities targeting American companies and users globally, highlighting the broader industry threat.
- NSO Group plans to examine the verdict details and pursue legal remedies, potentially including appeals, as stated by the company's spokesperson, Gil Lainer.
- The U.S. court's ruling stemmed from a lawsuit filed in October 2019, accusing NSO Group of using WhatsApp to infect mobile devices with surveillance software like Pegasus.
- NSO Group was found liable for breaching WhatsApp's terms of service and utilizing the platform for malicious activities, leading to the enforcement of punitive measures by the court.
- WhatsApp's victory in the legal battle against NSO Group was hailed as a significant privacy win, emphasizing accountability for spyware firms exploiting vulnerabilities.
- NSO Group exploited a zero-day vulnerability in WhatsApp's voice calling feature (CVE-2019-3568) to install spyware like Pegasus, continuing to use such exploits even after legal actions were taken.
- The court revelation exposed how NSO Group's spyware infiltrates phones, accessing sensitive data and functionalities, targeting various platforms beyond WhatsApp and using different installation methods.
- NSO Group has been instructed to disclose detailed information about its spyware's functionality surrounding the period of alleged attacks, shedding light on its covert surveillance practices.
Read Full Article
Like
Pymnts
146

Image Credit: Pymnts
Hacking Group Linked to Vegas Disruptions Suspected in Recent UK Retail Attacks
- Scattered Spider, a hacking group previously known for disrupting the Las Vegas Strip, is suspected of being behind recent cyber intrusions targeting U.K. retailers.
- U.K. retailers like Harrods, Marks & Spencer, and Co-op have reported cyber incidents involving disruptions in online sales, payment systems, and theft of customer data.
- The group uses social engineering and other techniques to access corporate networks, steal data, lock systems, and demand extortion payments.
- NCSC and Google have issued guidance to protect against such attacks, while investigations are ongoing to determine if the recent U.K. attacks are linked to Scattered Spider.
Read Full Article
8 Likes
Siliconangle
159

Image Credit: Siliconangle
Meta and NSO court battle over WhatsApp hack ends with Meta winning $167 million in damages
- Israeli cybersecurity company NSO Group Technologies Ltd. ordered to pay $167 million in damages to Meta after a 6-year court battle over installing spyware on WhatsApp accounts of journalists and activists.
- Meta considers the verdict a victory for privacy and security, marking a critical deterrent against illegal spyware development and use that threatened safety and privacy.
- NSO Group was found to have installed the Pegasus spyware on 1,400 WhatsApp accounts, enabling control of camera and microphone, access to location data, emails, and text messages with just a text message.
- Despite claims of sovereign immunity and preventing serious crime, NSO Group may appeal the verdict, mentioning deployment of spyware by authorized government agencies.
Read Full Article
9 Likes
Siliconangle
336

Image Credit: Siliconangle
Meta and NSO court battle over WhatsApp hack ends with Meta winning $167M in damages
- Israeli cybersecurity company NSO Group was ordered to pay $167 million in damages to Meta after a six-year court battle over installing spyware on WhatsApp accounts.
- Meta hailed the verdict as a victory for privacy and security, marking the first win against illegal spyware development and use.
- The spyware vendor, NSO Group, had installed Pegasus spyware on 1,400 WhatsApp accounts, allowing access to cameras, microphones, and messages with just a text message.
- NSO Group may appeal the verdict, claiming the software aimed to prevent serious crimes and terrorism, and was deployed responsibly by authorized government agencies.
Read Full Article
20 Likes
Cybersecurity-Insiders
132

NCSC issues alert against more ransomware attacks on retailers
- The National Cyber Security Centre (NCSC) has issued an alert against ransomware attacks targeting major British retailers like Harrods, Marks & Spencer, and Co-Op.
- NCSC warns about the increasing risk of ransomware attacks in the retail sector and expects a rise in similar attacks in the near future.
- NCSC provides guidelines for businesses to protect against ransomware attacks such as isolating and containing the threat, utilizing backup systems, reporting incidents to authorities, avoiding ransom payment, and notifying affected parties promptly.
- Prevention measures recommended by NCSC include patching vulnerabilities, training employees to recognize phishing attempts, and taking proactive security measures to prevent ransomware attacks.
Read Full Article
8 Likes
Silicon
265
Image Credit: Silicon
Co-Op Admits Member Data Compromised In Cyberattack
- The Co-op has admitted that member data has been compromised in a recent cyberattack, which is worse than initially reported.
- The hackers were able to access personal data of Co-op Group members such as names and contact details, but not passwords, bank or credit card details.
- The Co-op CEO stated that the criminals behind the attack are highly sophisticated and Co-op IT staff are working to protect the organization and understand the impact of the attack.
- The National Cyber Security Centre (NCSC) has warned British organizations to strengthen their cyber defenses following cyberattacks on high street retailers like Marks & Spencer, Co-op, and Harrods.
Read Full Article
16 Likes
Cybersecurity-Insiders
314

AI vs. the Human Mind: The New Ransomware Playbook
- Ransomware attackers are increasingly using AI to enhance their tactics, employing deepfake videos and personalized phishing emails to deceive victims.
- AI enables cybercriminals to automate attacks, collect information rapidly, and customize messages with convincing language and psychological manipulation.
- AI-driven ransom negotiations adapt in real-time based on the victim's financial profile, escalating pressure to make it harder for organizations to resist paying.
- Deepfake videos and voice messages are becoming tools for coercing victims, exemplified by an AI deepfake video used to steal $25 million from an engineering firm.
- AI-driven attacks exploit human psychology, gaining trust, inducing fear, and applying pressure, leveraging urgency for financial gain.
- AI complicates cybersecurity efforts by enabling attacks that do not display traditional red flags and allowing for the scalability of ransomware attacks.
- Groups like 'FunkSec' are utilizing AI in ransomware attacks, employing generative AI for advanced tools and a double extortion strategy to pressure victims into paying.
- Defenders can leverage AI for real-time anomaly detection and anti-data exfiltration technology to prevent unauthorized data transfers and thwart extortion attempts.
- While AI empowers attackers, organizations can use AI-powered solutions proactively to detect, prevent, and mitigate ransomware attacks, safeguarding their data and employees.
- By understanding and countering the evolving tactics of AI-enhanced ransomware, cybersecurity teams can strengthen their defenses and stay ahead of sophisticated threats.
Read Full Article
18 Likes
For uninterrupted reading, download the app