Malware News
TechCrunch
110
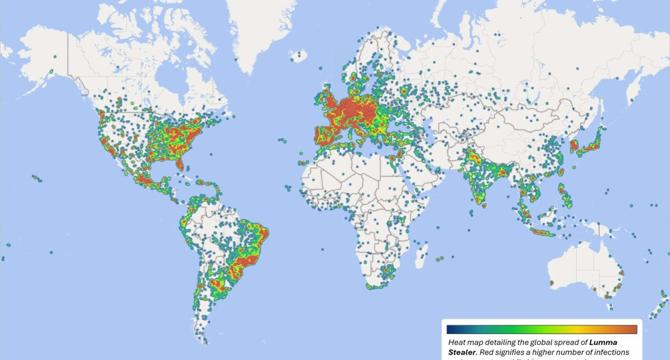
Image Credit: TechCrunch
Microsoft says Lumma password stealer malware found on 394,000 Windows PCs
- Microsoft and law enforcement conducted a court-authorized takedown of Lumma, an info-stealer malware operation found on over 394,000 Windows PCs worldwide, mainly in Brazil, Europe, and the United States.
- Civil action was taken by Microsoft to seize 2,300 domains serving as the malware's command and control servers, while the Justice Department seized five domains linked to the Lumma infrastructure.
- Lumma password stealer is typically hidden in illegitimate games or cracked applications downloaded online, stealing logins, passwords, credit cards, and cryptocurrency wallets to sell to other hackers. It can also provide a backdoor for further malware installation like ransomware.
- Such password-stealing malware, including Lumma, has been associated with cyberattacks targeting tech firms like PowerSchool and Snowflake, resulting in substantial data theft.
Read Full Article
6 Likes
TechJuice
4

Image Credit: TechJuice
Microsoft Hits Back After Lumma Stealer Affects Thousands of PCs
- The FBI, Europol, and Microsoft collaborated to shut down the Lumma Stealer malware network that infected around 10 million devices globally.
- Lumma Stealer operated on a malware-as-a-service model, allowing cybercriminals to buy access through subscription plans, making it easier for less-skilled attackers to deploy powerful malware.
- Authorities seized 2,300 malicious domains critical to Lumma Stealer's command-and-control infrastructure, cutting off communication between infected systems and its operators.
- The takedown of Lumma Stealer is a significant win against cybercrime networks, disrupting their tool for stealing sensitive information and showcasing the power of global collaboration in cybersecurity.
Read Full Article
Like
TechJuice
217

GitLab Duo AI Vulnerability Exposes Developers to Code Theft
- GitLab’s AI-powered coding assistant, Duo, faced a significant security issue due to prompt injection vulnerability.
- Attackers could manipulate Duo by embedding hidden prompts in code comments, commit messages, or merge-request descriptions.
- Exploiting this vulnerability could lead to harmful code changes, redirection to malicious websites, or leakage of sensitive data.
- GitLab has patched the flaws, emphasizing the importance of maintaining security in AI-integrated development workflows.
Read Full Article
13 Likes
Securityaffairs
405
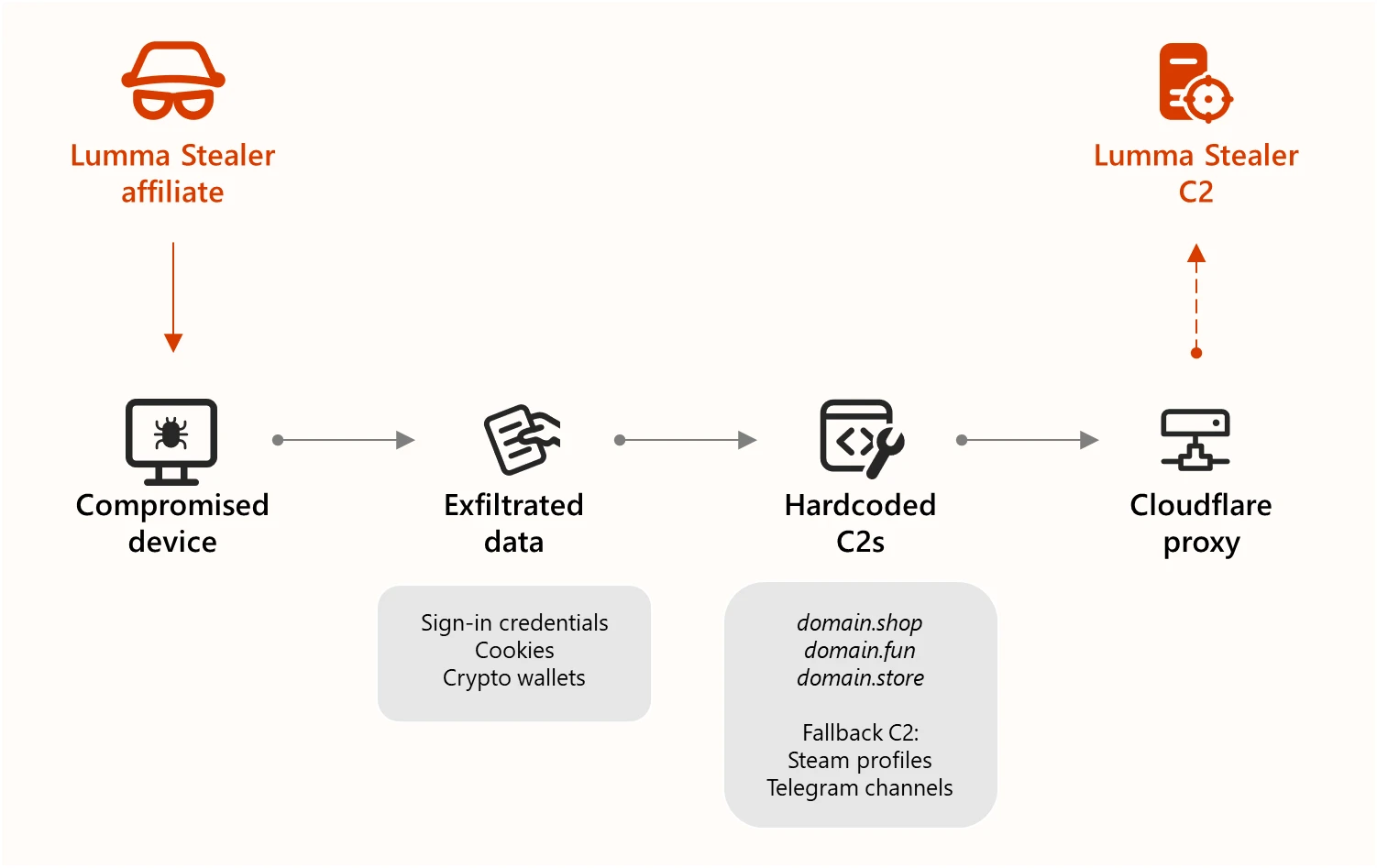
Image Credit: Securityaffairs
Law enforcement dismantled the infrastructure behind Lumma Stealer MaaS
- Law enforcement, with the help of Microsoft, Europol, and Japan’s JC3, dismantled the infrastructure behind Lumma Stealer Malware-as-a-Service (MaaS) operation, seizing 2,300 domains used for command-and-control.
- The malware, known as Lumma Stealer, targeted over 394,000 Windows systems, including those of global manufacturers, to steal sensitive data like passwords, credit card information, and crypto wallet keys.
- Microsoft's Digital Crimes Unit sinkholed over 1,300 domains used by Lumma Stealer to reroute victims to safe servers for analysis and cleanup, showcasing the collaboration between law enforcement and tech companies against cyber threats.
- The FBI and US CISA released a joint advisory containing tactics, techniques, and procedures associated with Lumma Stealer, along with indicators of compromise (IOCs), emphasizing the importance of public-private partnerships in combating cybercrime.
Read Full Article
24 Likes
Securityaffairs
123
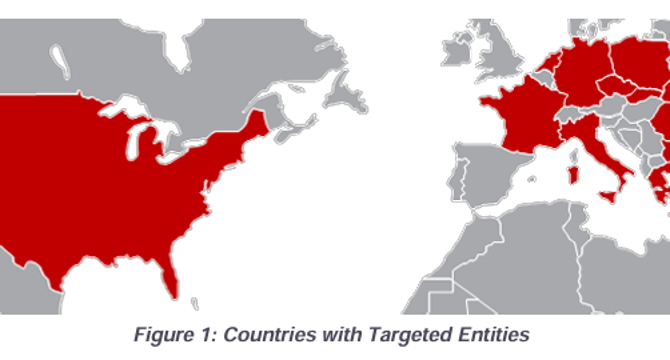
Image Credit: Securityaffairs
Russia-linked APT28 targets western logistics entities and technology firms
- CISA warns that Russia-linked APT28 is targeting Western logistics and technology companies aiding Ukraine, posing a heightened threat to supply chains.
- APT28, also known as Fancy Bear, has been active since at least 2007 and has targeted governments, militaries, and security organizations globally, including the 2016 Presidential election.
- The group operates from Russian military unit 26165 of GRU 85th Main Special Service Center, targeting Western logistics and tech firms linked to Ukraine aid across 13 countries using various tactics like spear-phishing and exploiting vulnerabilities.
- GRU Unit 26165 used tactics such as spearphishing with fake login pages, exploiting Outlook and Roundcube vulnerabilities, deploying custom malware like HEADLACE and MASEPIE, and exfiltrating data using PowerShell and APIs, targeting Western logistics and IT sectors.
Read Full Article
7 Likes
Siliconangle
4

Image Credit: Siliconangle
Global law enforcement and Microsoft take down Lumma malware infrastructure
- A global law enforcement operation, supported by Microsoft Corp., has disrupted the infrastructure behind Lumma, a popular malware-as-a-service tool known for widespread information theft.
- The U.S. Department of Justice coordinated the takedown of Lumma, leading to the seizure of domains used for Lumma distribution, enabling cybercriminals to steal sensitive data globally.
- Lumma, which emerged in December 2022, was widely used due to its affordability and ease of deployment. It allowed low-skilled threat actors to conduct sophisticated attacks, targeting various data types.
- Despite the takedown, concerns remain about potential reemergence of Lumma or similar threats, as threat actors often adapt quickly with rebrands, new delivery methods, and rebuilt infrastructure.
Read Full Article
Like
Adamlevin
64

Keren Elazari Decrypts the Ransomeware Nightmare
- Ransomware is a malicious software used by hackers to hijack data on devices or networks, targeting critical entities like hospitals and banks.
- Cybersecurity expert Keren Elazari discussed the persistent threat of ransomware attacks on essential infrastructure, such as telecommunications and water systems.
- The Tinfoil Swan delves into the pwnagotchi, a hacking gadget highlighting the importance of maintaining good cyber hygiene to prevent cyber attacks.
- The article decrypts ransomware nightmares and sheds light on the ongoing battle against cyber threats.
Read Full Article
3 Likes
Silicon
291
Image Credit: Silicon
M&S Cyberattack To Cost £300m And Upheaval To Last Into July
- Marks & Spencer (M&S) confirms financial and operational impact of recent cyberattack, revealing customer data theft and disrupted operations.
- M&S estimates £300m impact on Group operating profit for 2025/26 due to cyberattack, with online disruption expected to continue into July.
- UK's National Crime Agency identifies cyber-criminal collective Scattered Spider as key focus, known for ransomware attacks using DragonForce platform.
- Leader of Scattered Spider, Tyler Buchanan, arrested in Spain, while other alleged members include Noah Michael Urban and Remington Ogletree, with global arrests made in connection with previous hacks.
Read Full Article
17 Likes
Securelist
12

Image Credit: Securelist
Dero miner zombies biting through Docker APIs to build a cryptojacking horde
- A new Dero mining campaign involves infected containers exploiting insecurely published Docker APIs to create a cryptojacking horde.
- Malicious containers were detected during a compromise assessment project, leading to the discovery of a threat actor exploiting Docker APIs.
- Two malware implants, nginx and the Dero crypto miner, written in Golang, are used in an automated attack vector to infect new victims.
- The nginx malware ensures persistence, spreads without a command-and-control server, and targets insecure Docker APIs to infect new networks.
- The malware propagates by scanning IPv4 subnets, identifying open Docker API ports, creating new malicious containers, and compromising existing ones.
- The malware infects containers by installing dependencies, transferring malicious implants, and maintaining persistence for continuous mining activities.
- The cloud malware encrypts configuration details, including wallet and Dero node addresses, aiming to sophisticate the malware.
- The attack campaign emphasizes the threat posed to containerized environments and the importance of monitoring and protecting container infrastructures.
- Security measures like using efficient monitoring tools and proactively hunting for threats are recommended to safeguard container environments.
- Indicators of compromise, such as file hashes, paths, and specific addresses, are provided to help in detecting and mitigating such malicious activities.
Read Full Article
Like
Securityaffairs
424

Image Credit: Securityaffairs
SK Telecom revealed that malware breach began in 2022
- SK Telecom revealed that the security breach disclosed in April began in 2022.
- SK Telecom, South Korea's largest wireless telecom company, detected a malware attack in April affecting 27 million users.
- The breach exposed data like phone numbers, IMSIs, SIM keys, and HSS-stored info of users.
- Investigations found that the breach began in 2022, went undetected for nearly three years, and involved 25 malware types across 23 servers.
Read Full Article
25 Likes
Cybersecurity-Insiders
180

Image Credit: Cybersecurity-Insiders
Ransomware attack on UK Food Distributor to supermarkets
- A ransomware attack has targeted Peter Green Chilled, a UK food distributor supplying major supermarket chains like Tesco, Aldi, and Sainsbury's.
- The cyberattack on Peter Green Chilled has been reported to the National Crime Agency and efforts to recover are ongoing.
- Ransomware attacks pose a significant threat to the retail sector, leading to disruptions, product shortages, and logistical challenges.
- Experts emphasize the importance of proactive cybersecurity measures to prevent and mitigate the impact of ransomware attacks on businesses.
Read Full Article
10 Likes
Securityaffairs
73
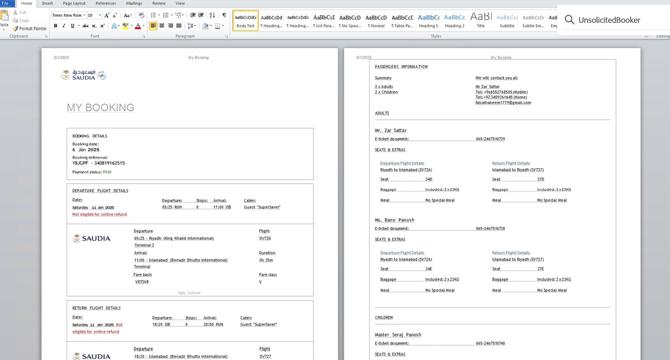
Image Credit: Securityaffairs
China-linked UnsolicitedBooker APT used new backdoor MarsSnake in recent attacks
- China-linked APT group UnsolicitedBooker used a new backdoor named MarsSnake to target an international organization in Saudi Arabia.
- The group employed spear-phishing emails with fake flight ticket lures to infiltrate systems and has a history of targeting government organizations in Asia, Africa, and the Middle East.
- UnsolicitedBooker's arsenal includes backdoors like Chinoxy, DeedRAT, Poison Ivy, and BeRAT, commonly seen in Chinese APT groups, indicating espionage and data theft motives.
- The repeated attacks on the Saudi organization in 2023, 2024, and 2025 show a persistent interest from UnsolicitedBooker in the specific target.
Read Full Article
4 Likes
Socprime
163

Image Credit: Socprime
ELPACO-Team Ransomware Attack Detection: Hackers Exploit Atlassian Confluence Vulnerability (CVE-2023-22527) to Gain RDP Access and Enable RCE
- Threat actors exploited CVE-2023-22527 in Atlassian Confluence to deploy ELPACO-team ransomware quickly.
- Ransomware recovery costs soared to $2.73 million in 2024, emphasizing the need for proactive defenses.
- Security professionals can access detection rules on SOC Prime Platform for CVE-2023-22527 exploitation.
- Rules on SOC Prime are compatible with various security solutions and mapped to the MITRE ATT&CK® framework.
- Uncoder AI, a threat detection engineering tool, is now freely available on SOC Prime to streamline investigations.
- CVE-2023-22527 exploitation by ELPACO-team ransomware involved sophisticated attacks on unpatched servers.
- Adversaries utilized advanced persistence strategies like deploying multiple backdoors and enabling RDP access.
- Attackers demonstrated deliberate actions by waiting 62 hours to deploy ransomware after compromising systems.
- Unusual tactics were used, such as creating a local admin account and altering registry settings for RDP access.
- Defenders are urged to apply timely patches, monitor system activity, and enhance remote access security against similar attacks.
Read Full Article
9 Likes
Securityaffairs
141

Image Credit: Securityaffairs
UK’s Legal Aid Agency discloses a data breach following April cyber attack
- The UK's Legal Aid Agency suffered a cyberattack in April, leading to a data breach where sensitive information of legal aid applicants was stolen.
- The cyberattack on the Legal Aid Agency, part of the UK Ministry of Justice, compromised personal data dating back to 2010, including contact details, national ID numbers, and financial information.
- The agency worked with authorities like the National Crime Agency and National Cyber Security Centre to investigate the breach and discovered that hackers accessed and downloaded significant amounts of personal data.
- In response to the breach, the Legal Aid Agency took down its online service, implemented security measures, and assured continued access to legal support for those in need.
Read Full Article
8 Likes
TechJuice
128

Image Credit: TechJuice
Hannibal Stealer Malware uses Military-Grade tactics to Evade Detection
- Hannibal Stealer is a new, modular .NET-based information-stealing malware known for its military-grade tactics to evade detection and harvest sensitive information.
- The malware leverages multi-layered obfuscation and stealth routines, dynamically downloads Merkle proofs, uses bespoke decryptors, and communicates through Telegram or dedicated C2 servers to steal data like application data, VPN setups, bitcoin accounts, and credentials.
- The makers of Hannibal Stealer actively promote it on underground forums, fake customer reviews, and Google Ads campaigns, spending over $10 million on ads to direct victims to malicious landing pages.
- The malware's modular architecture incorporates obfuscation techniques to protect its core logic, launch data theft capabilities from browsers and FTP clients, hijack cryptocurrency wallet addresses, target VPN credentials, and exfiltrate data using Telegram or dedicated C2 servers.
Read Full Article
7 Likes
For uninterrupted reading, download the app