Malware News
Silicon
332
Image Credit: Silicon
Marks & Spencer Warns Customers Over Data Theft
- Marks & Spencer informed online customers of data theft during a cyber-attack on 25 April.
- The stolen data included contact details, dates of birth, and online order history.
- No card details, payment information, or account passwords were compromised.
- Customers are advised to change passwords as a precaution, and M&S is working on resolving the issue.
Read Full Article
20 Likes
Cybersecurity-Insiders
275

Image Credit: Cybersecurity-Insiders
Now ransomware starts infecting Central Processing Units aka CPUs
- Ransomware is now targeting Central Processing Units (CPUs), a critical component of computing devices.
- This new form of malware infects the CPU itself, making it difficult to remove even after hardware changes.
- Malicious actors can manipulate the microcodes of a processor, potentially compromising the entire system.
- The development of CPU-targeting malware represents a significant evolution in cybercriminal tactics, posing new challenges for cybersecurity professionals.
Read Full Article
16 Likes
Socprime
65

Image Credit: Socprime
Noodlophile Stealer Detection: Novel Malware Distributed Through Fake AI Video Generation Tools
- Adversaries are using fake AI-powered tools to distribute the Noodlophile information-stealing malware through fake Facebook groups and viral posts, targeting over 62,000 users.
- Defenders are facing the challenge of detecting Noodlophile Stealer, a new malware spread through fake AI generation tools that steal sensitive data from compromised systems.
- Security engineers can utilize the SOC Prime Platform to access Sigma rules for Noodlophile Stealer detection, enriched with actionable metadata and AI-powered Uncoder AI for advanced capabilities.
- The Noodlophile Stealer malware is distributed through fake AI-generated videos, targeting users seeking AI-based video and image editing tools, and combines browser credential theft, wallet exfiltration, and optional remote access deployment.
Read Full Article
3 Likes
Securityaffairs
43

Image Credit: Securityaffairs
Moldovan Police arrested a 45-year-old foreign man participating in ransomware attacks on Dutch companies
- A 45-year-old foreign man was arrested in Moldova for participating in ransomware attacks on Dutch companies in 2021.
- The arrest was a result of a joint international operation involving Moldovan and Dutch authorities, with the suspect wanted for cybercrimes including ransomware attacks and money laundering.
- The suspect was linked to a ransomware attack on the Netherlands Organization for Scientific Research, resulting in €4.5 million in damages, attributed to the DoppelPaymer ransomware operation.
- In a related development, Europol announced an international operation targeting key members of the DoppelPaymer ransomware group in March 2023.
Read Full Article
2 Likes
Cybersecurity-Insiders
280

Image Credit: Cybersecurity-Insiders
Malware emerging from AI Video generation tools
- Cybercriminals are exploiting AI video generation platforms to distribute malware, with the recent emergence of the Noodlophile malware, an info-stealer targeting sensitive user data.
- Recent investigations by cybersecurity researchers reveal that hackers are leveraging seemingly legitimate AI video tools to infect users' devices with malware, aiming to generate income through ad revenue and malware distribution.
- To attract users, cybercriminals promote fake AI tools like Luma Dreammachine AI and gratislibros on social media, making it crucial for users to be cautious and avoid clicking on suspicious links.
- Authorities are facing challenges in combating malware embedded within popular applications and websites, highlighting the need for users to be vigilant, download software from reputable sources, and avoid engaging with dubious services promoted on social media.
Read Full Article
16 Likes
Cybersecurity-Insiders
381

Image Credit: Cybersecurity-Insiders
What should we learn from International Anti Ransomware Day
- International Anti-Ransomware Day is observed annually on May 12th to raise awareness and promote prevention measures against ransomware attacks.
- Lessons from the day include emphasizing prevention through regular updates and strong security measures, highlighting the importance of secure backups, raising awareness about cybersecurity for all users, and discouraging ransom payments.
- The day commemorates the WannaCry attack and underscores the need for collaboration among governments, agencies, and organizations to combat cybercrime effectively.
- Education on cybersecurity and the implementation of policies to enhance cyber resilience are crucial in mitigating ransomware threats, emphasizing that cybersecurity is a shared responsibility for individuals and organizations.
Read Full Article
22 Likes
Securityaffairs
70
Image Credit: Securityaffairs
Threat actors use fake AI tools to deliver the information stealer Noodlophile
- Threat actors are using fake AI tools to distribute the information stealer Noodlophile, as warned by Morphisec researchers.
- Attackers exploit the AI hype through viral posts and Facebook groups to trick users into downloading Noodlophile Stealer, a new malware that steals browser credentials and crypto wallets.
- Noodlophile Stealer, a previously undisclosed malware, is being sold on cybercrime forums as part of malware-as-a-service schemes and is often bundled with tools for credential theft.
- Fake AI tools like 'Dream Machine' or 'CapCut' spread through social media, attracting users seeking free video/image editors, but instead delivering malware like Noodlophile or XWorm.
Read Full Article
4 Likes
Kaspersky
258

Image Credit: Kaspersky
The ransomware landscape in 2025 | Kaspersky official blog
- Ransomware incidents show low quality of decryptors; attackers may not send decryptors or provide inefficient tools.
- Cybercriminals often specialize in encryption, not decryption, leading to slow and faulty decryptors.
- Ransomware attackers engage in repeated attacks, switching between groups and affiliates to continue extortion.
- Legislation is tightening globally to combat ransomware, requiring companies to report incidents promptly.
- Companies face risks and legal consequences for paying ransoms, as it can lead to long-term repercussions.
- Paying ransoms does not guarantee data confidentiality, as data may still be leaked or disclosed.
- Law enforcement actions and evolving laws have changed ransomware landscape, decreasing ransom amounts paid.
- Ransomware groups are now more focused on espionage and mixed motives, complicating victim understanding.
- Paying ransomware operators can worsen the problem; having a response plan in place is crucial for recovery.
- Organizations should prepare detailed response plans and implement monitoring solutions to counter ransomware attacks effectively.
Read Full Article
15 Likes
Cybersecurity-Insiders
66

Image Credit: Cybersecurity-Insiders
DragonForce Ransomware targeting M&S vows not to target Russia or Soviet Union
- DragonForce Ransomware, responsible for attacking Marks & Spencer, urges cybercriminals to avoid targeting businesses in Russia and the former Soviet Union.
- Speculations arise about DragonForce's ties to Russia or possible funding from the post-Soviet region, leading them to show loyalty to these territories.
- DragonForce emphasizes its policy of solely extorting money and not deleting valuable business data, aiming to preserve technology use in certain regions.
- The group has targeted 90 companies across sectors, issuing warnings to rival groups like Scattered Spider not to attack networks in Russia, setting new boundaries in cybercrime operations.
Read Full Article
3 Likes
Securityaffairs
250

Image Credit: Securityaffairs
Security Affairs newsletter Round 523 by Pierluigi Paganini – INTERNATIONAL EDITION
- 437,329 patients' personal data exposed in Ascension cyberattack.
- Operation Moonlander dismantles cybercriminal services Anyproxy and 5socks.
- SonicWall fixes critical flaws in SMA 100.
- NSO Group ordered to pay over $167M to WhatsApp for spyware campaign.
Read Full Article
15 Likes
Securityaffairs
88
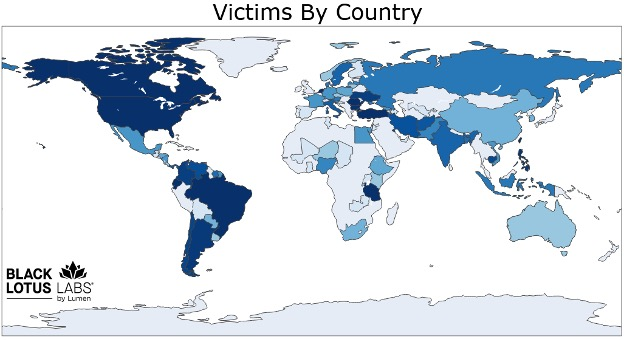
Image Credit: Securityaffairs
Operation Moonlander dismantled the botnet behind Anyproxy and 5socks cybercriminals services
- Operation Moonlander dismantled a 20-year botnet behind Anyproxy and 5socks cybercriminals services and arrested four suspects.
- U.S. Justice Department charged Russian and Kazakhstani nationals for maintaining, operating, and profiting from Anyproxy and 5socks services.
- The botnet operators enabled cryptocurrency payments and targeted IOT and SOHO devices for malicious activities like ad fraud, DDoS attacks, and brute force attacks.
- FBI released a FLASH alert warning about 5Socks and Anyproxy malicious services targeting end-of-life routers and urged replacing compromised routers or preventing infection by disabling remote admin and rebooting.
Read Full Article
5 Likes
TechCrunch
211
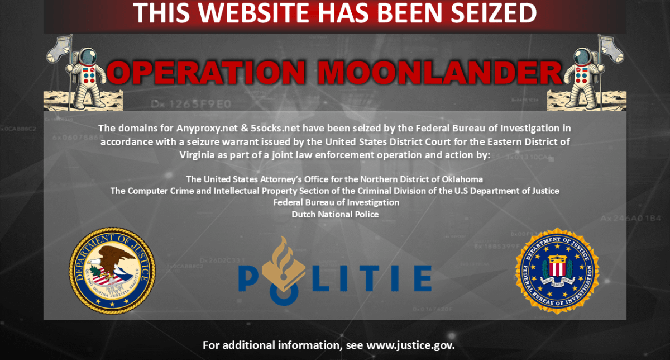
Image Credit: TechCrunch
FBI and Dutch police seize and shut down botnet of hacked routers
- FBI and Dutch police have seized and shut down botnet services involving hacked internet-connected devices, including routers.
- U.S. prosecutors indicted four individuals, including three Russians and one Kazakhstan national, for hacking into routers and running the botnet under the guise of legitimate proxy services.
- The accused individuals targeted vulnerable internet-connected devices to build a botnet, offering access through services like Anyproxy and 5Socks and making over $46 million from selling botnet access.
- Black Lotus Labs assisted in tracking the proxy networks used for malicious activities, with the botnet offering anonymity for cybercriminals and having about 1,000 weekly active proxies in over 80 countries.
Read Full Article
12 Likes
Cybersecurity-Insiders
313

Image Credit: Cybersecurity-Insiders
No cyber threat to India ATMs from Pakistan Ransomware Attack
- Tensions between India and Pakistan have risen following a terrorist attack, prompting concerns of a potential ransomware attack on Indian ATMs by Pakistan's cyber army.
- Misinformation on social media suggested that Indian ATMs would be shut down preventively, causing citizens to rush for cash withdrawals in fear of a banking crisis.
- The Indian government has officially refuted these rumors, confirming that there are no plans to shut down ATMs and reassuring the public of the nation's readiness to handle cyber threats.
- Authorities have advised citizens to use social media responsibly, conduct fact-checking, and beware of malware threats, such as the 'Dance of the Hillary' file circulating on mobile devices.
Read Full Article
18 Likes
Securityaffairs
374

Image Credit: Securityaffairs
Cybercriminal services target end-of-life routers, FBI warns
- The FBI warns that cybercriminal services are targeting end-of-life routers to deploy malware and sell them as proxies on 5Socks and Anyproxy networks.
- End-of-life routers are vulnerable to cyber attacks due to the lack of security updates, making them easy targets for threat actors who exploit known vulnerabilities.
- Infected routers are used to form botnets for coordinated attacks or sold as proxies, allowing threat actors persistent access and control over the compromised devices.
- The FBI recommends replacing vulnerable routers with newer models or disabling remote administration and rebooting the devices to prevent further infections, as per the published indicators of compromise (IoCs) and mitigation strategies.
Read Full Article
22 Likes
Securityaffairs
150
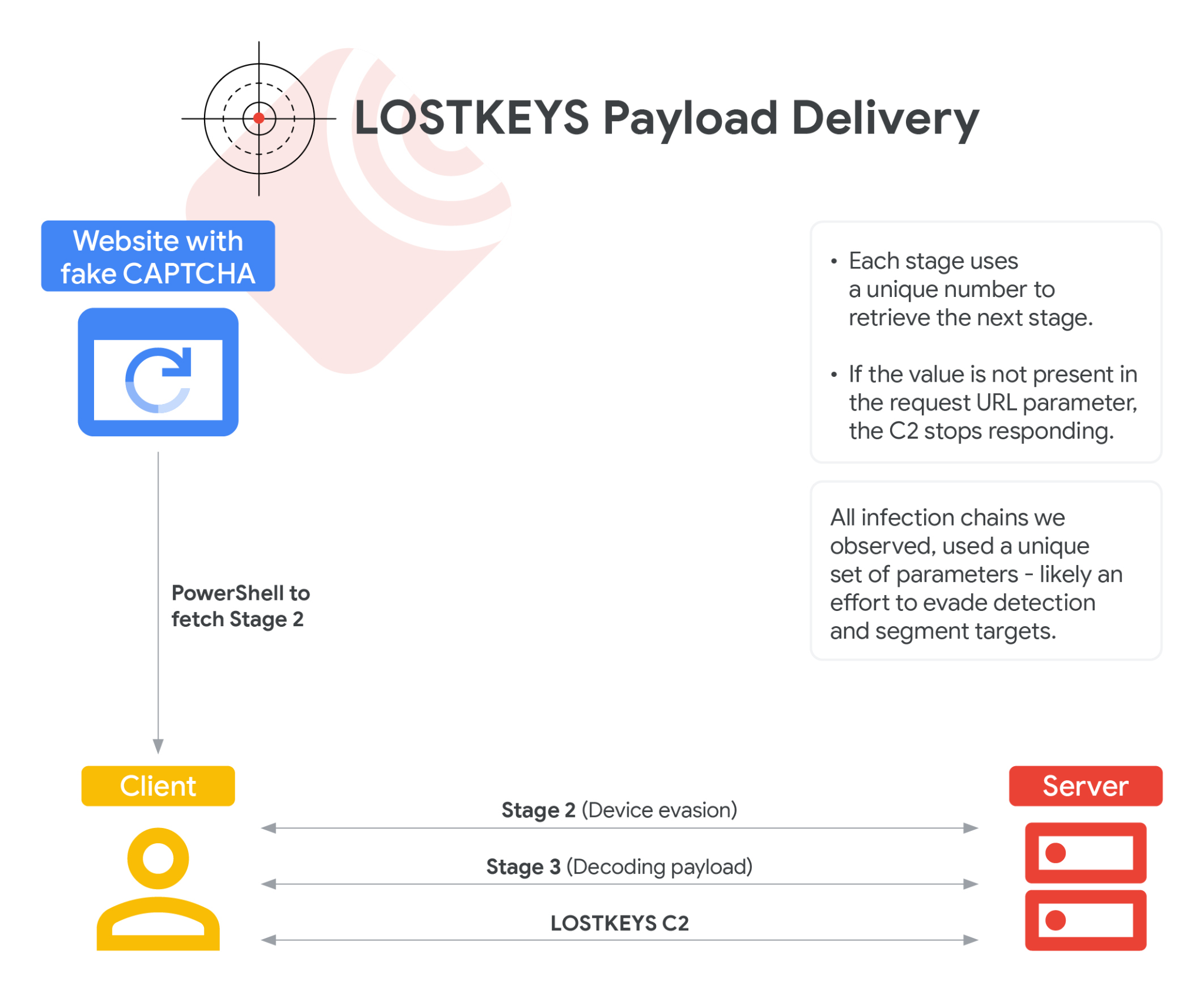
Image Credit: Securityaffairs
Russia-linked ColdRiver used LostKeys malware in recent attacks
- Russia-linked ColdRiver, also known as APT COLDRIVER, has been using LostKeys malware in recent espionage attacks on Western governments and organizations since early 2025.
- The ColdRiver APT group primarily targets NATO countries, along with the Baltics, Nordics, and Eastern Europe, including Ukraine, focusing on government officials, military personnel, journalists, and think tanks.
- LostKeys malware is deployed through a multi-step chain, starting with a fake CAPTCHA to trick users into running PowerShell scripts. It is capable of stealing files, sending system information to the attacker, and running processes.
- Google’s Threat Intelligence Group discovered LostKeys malware in selective ClickFix attacks, with victims being tricked into running malicious PowerShell scripts that led to data theft via VBS payloads. Two additional samples were found dating back to December 2023, leading to uncertainty about their relation to COLDRIVER.
Read Full Article
9 Likes
For uninterrupted reading, download the app