Programming News
Dev
248

Image Credit: Dev
Build an LLM Web App in Python from Scratch: Part 2 (Streamlit & FSM)
- The article discusses building an AI-powered image generator via an interactive web application where users can generate images from text prompts and provide feedback within a user-friendly interface.
- Python tools used include Streamlit for web app conversion, PocketFlow for workflow management, and Finite State Machine (FSM) for tracking the process.
- Streamlit is highlighted for simplifying web app development without requiring HTML/CSS skills and its 'rerun' model that re-executes the Python script each time a user action occurs.
- An example of a simple click counter web app using Streamlit is provided.
- PocketFlow is used to organize the workflow with Nodes acting as building blocks for different steps like getting user input, AI image generation, and user feedback.
- The article also introduces the concept of Finite State Machines (FSMs) for managing interactive web states, providing a framework to guide the app through different screens or modes.
- The FSM ensures the app remains responsive and helps in transitioning between different states based on user actions.
- A complete working example integrating PocketFlow, Streamlit, and FSM is offered for reference.
- The FSM approach enhances the interactive user experience of the PocketFlow workflow and allows for seamless transitions between states.
- The article concludes by emphasizing the power of the FSM approach, clean code maintenance, Streamlit compatibility, and user-friendliness in AI app development.
- The future direction of the tutorial series includes adding real-time features with FastAPI and WebSockets for live interactions and updates.
Read Full Article
14 Likes
Nordicapis
108

How Model Context Protocol (MCP) Impacts APIs
- The Model Context Protocol (MCP) is reshaping API and AI consumption and design by providing a structured and context-rich way for LLMs and AI agents to consume services and resources.
- MCP is an emerging standard that creates a metadata model for connecting LLM-based tools with remote services and data sources, enhancing interactions and streamlining connections.
- APIs are not becoming obsolete with MCP but are fundamental in the background of digital interactions while MCP simplifies the connection process between models, data sources, and services.
- MCP acts as an abstraction layer, enabling models to utilize APIs without constant human guidance, improving flexibility and performance within a standard framework.
- MCP enables agentic API consumption by standardizing metadata for model use, reducing hard-coded integrations for higher portability, and enhancing access controls and security.
- While MCP offers solutions, it also brings threats such as vulnerabilities to specific attack vectors and risks related to interconnected MCP servers.
- MCP is a new paradigm in API evolution for the AI age, providing a standard approach for AI-driven interactions and integration, not as a replacement but as an enhancement.
- API practitioners should embrace MCP as an opportunity to future-proof their APIs for the agentic AI era, realizing that not all services require MCP and that it caters to AI-specific problems.
- APIs remain crucial for modular solutions in various industries, and MCP ensures their consumability in the evolving AI landscape.
Read Full Article
6 Likes
Dev
411

Image Credit: Dev
Nx Monorepo Guide: React & Node Fullstack App
- A monorepo consolidates code for multiple projects in one version control repository, simplifying shared code distribution and speeding up development.
- Nx is a smart monorepo tool designed for managing JavaScript and TypeScript projects efficiently.
- Nx offers features like project structure understanding, time-saving computation caching, code generators, clean testing setup, and support for popular frameworks.
- Comparing Nx to other tools like Lerna and Turborepo showcases Nx's comprehensive approach and active maintenance.
- Nx workspace setup involves using CLI commands like create-nx-workspace to initiate a powerful development environment.
- Essential Nx configuration files like nx.json, package.json, and tsconfig files play crucial roles in defining project structures and settings.
- Nx CLI commands such as generate, serve, build, test, lint, graph, and affected facilitate efficient workspace management.
- Creating Node.js backend apps and React components within an Nx monorepo is streamlined, promoting code reuse and clean architecture.
- Nx's hot reloading and development workflow, along with its dependency graph visualization, ensure fast feedback loops and efficient builds.
- Enforcing module boundaries and import restrictions, managing dependencies centrally, and understanding app vs. library usage are key concepts in Nx workspace architecture.
Read Full Article
24 Likes
Dev
293

Image Credit: Dev
Next-Gen API Documentation: Game-Changing AI Trends for Developers by 2025🔥
- API documentation is undergoing a radical transformation that will change how developers interact with APIs by 2025.
- Quality documentation transforms developers into power users and serves as a marketing powerhouse for APIs.
- Interactive documentation allows real-time experimenting, reducing the learning curve and speeding up API adoption.
- AI-powered documentation assistants provide contextual guidance, reducing support burden and accelerating integration.
- Collaborative documentation platforms enable real-time collaboration among stakeholders for comprehensive and evolving resources.
- Improved documentation leads to faster API adoption, competitive advantage, and inclusivity for developers of varying expertise.
- Emerging technologies like personalized documentation, augmented reality, and blockchain could further revolutionize API documentation.
- Apidog is at the forefront of API documentation innovation, offering interactive exploration, automated code generation, and integrated mocking.
- Apidog's MCP Server connects AI directly to API specifications for precise guidance, enhancing development experiences.
- The documentation renaissance is empowering developers with dynamic, intelligent resources that actively shape the development process.
Read Full Article
17 Likes
Discover more
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Analyticsindiamag
284

Image Credit: Analyticsindiamag
Mistral Rolls Out AI Coding Assistant to Challenge Claude and Copilot
- Mistral AI has launched Mistral Code, a new AI-powered coding assistant for enterprises.
- Mistral Code offers deployment flexibility and full-stack control, open for private beta for JetBrains IDEs and VSCode.
- The product integrates four models for code autocomplete, retrieval, development tasks, and chat-based help.
- Early adopters of Mistral Code include Abanca, SNCF, and Capgemini, with the platform positioning itself as a single-vendor alternative for AI dev tools.
Read Full Article
17 Likes
PlanetPython
4

Glyph Lefkowitz: I Think I���m Done Thinking About genAI For Now
- The author reflects on their cognitive tendencies resembling Monkesque neuroticism rather than Holmesian deduction in dealing with problematic ideas.
- Despite being a genAI skeptic, the author is exposed to genAI discourse constantly, finding it relentless and exhausting.
- The author discusses the recent wave of anti-anti-genAI articles that straw-man skeptics and fail to engage with substantial criticisms.
- Concerns are raised about the decay of critical thinking skills in individuals using genAI technology intensively.
- The author delves into the aesthetic unpleasantness and inefficiency of interacting with genAI systems, particularly in software development.
- The article explores the negative impact of genAI on productivity, causing demoralization and potential burnout in programmers.
- The author expresses concerns about the impending economic crash due to overinvestment in genAI technology.
- The escalating energy usage, educational impact, invasion of privacy, and training data theft issues related to genAI are highlighted.
- The challenges of experimentation, obfuscation in productization, and inherent resistance in proving genAI's negative aspects are discussed.
- The author contemplates surrendering on the topic of genAI due to the complexity, lack of rigorous evidence, and overwhelming industry support.
Read Full Article
Like
Javacodegeeks
248

Image Credit: Javacodegeeks
Build an AI Chatbot in React with LangChain.js and OpenAI
- Learn how to create a dynamic AI chatbot using React, LangChain.js, and OpenAI with streaming responses, memory management, and action plugins.
- Set up your React application by initializing a project with Vite and installing LangChain.js and OpenAI dependencies.
- Configure your OpenAI API key in a .env file and understand the chatbot architecture flow between React frontend, LangChain.js logic layer, OpenAI, and external APIs.
- Implement chat memory using LangChain's RunnableWithMessageHistory and enhance chatbot capabilities with action plugins like fetching weather information.
Read Full Article
14 Likes
Medium
158

Empowering the Future of Web3 Education The Vision of the XIIID AI Project
- The article discusses the current challenges in education, such as centralization, outdated curricula, exclusivity, and lack of transparency.
- The XIIID AI Project aims to revolutionize education by offering a decentralized, peer-driven, and AI-powered learning experience.
- Key aspects of the XIIID project include AI integration, NFTs for credentials, incentivized participation, and decentralized governance.
- Benefits of XIIID include global access to knowledge, language inclusivity, empowerment of self-learners, and ownership of identity and learning data.
- The ecosystem of XIIID features AI learning assistants, a token economy, modular learning paths, and community-driven governance through a DAO.
- The vision of XIIID is to create an intelligent, equitable, and open decentralized learning network accessible to all globally.
- Long-term goals include decentralized AI training hubs, Web3 campus DAO networks, and soulbound credentials and identity.
- Real-life scenarios illustrate how XIIID can benefit individuals worldwide by offering personalized learning paths and verifiable credentials.
- To be involved in the XIIID community, individuals can visit their website, Twitter, Discord, Mirror Blog, and GitHub.
- The XIIID AI Project represents a vision for a future of education where knowledge is decentralized, identity is sovereign, and effort is rewarded.
- By embracing Web3 technologies, AI, and decentralized governance, XIIID paves the way for a brighter future in global learning.
Read Full Article
9 Likes
Dev
6k

Image Credit: Dev
From JVM to Native Compilation with Spring Boot: What It Means and Why It Matters
- Java developers can now compile Spring Boot applications into native executables using tools like Spring Native and GraalVM.
- Native compilation results in binaries that start in milliseconds, consume less memory, and run as fast and light as Quarkus.
- This shift from JVM-based to native compilation is particularly beneficial for modern applications like microservices and serverless functions.
- Spring Boot 3.x officially supports AOT + native image compilation, enabling the creation of self-contained binaries for Spring Boot apps.
Read Full Article
15 Likes
Siliconangle
1.5k

Image Credit: Siliconangle
Mistral AI introduces Code programming assistant
- Mistral AI has launched Mistral Code, a programming assistant that uses four AI models to help developers write code faster.
- The tool is based on an open-source project named Continue and offers features like programming advice, search capabilities, autocomplete, and a chatbot interface.
- Mistral Code utilizes AI models like Codestral Embed for search, Codestral for autocomplete, Devstral for complex tasks, and Mistral Medium for the chatbot interface.
- Customers can customize the underlying algorithms of Mistral Code, providing a level of control not available in closed copilots tied to proprietary APIs.
Read Full Article
7 Likes
Logrocket
352

Image Credit: Logrocket
Leader Spotlight: Helping teams navigate personal change, with Alicia Littleton
- Alicia Littleton, Director of Ecommerce at Gerber Childrenswear LLC, emphasizes empathy and flexibility in the workplace for team members experiencing life changes.
- She advocates for supporting employees through major life events like welcoming a child or handling loss, promoting adaptability and flexibility in team dynamics.
- Alicia's leadership philosophy revolves around empathy, flexibility, and advocacy, stemming from her own experiences lacking strong support during significant life changes.
- Challenges in managing team members during significant life events include addressing the temporary gap from parental leave and readjusting workload distribution post-return.
- Effective leave policies require flexibility, allowing managers to tailor solutions based on individual circumstances to support employees during transformative life events.
- Communication and documentation are crucial in preparing teams for a member going on leave, enhancing workflow continuity and facilitating workload redistribution.
- Reintegrating employees returning from leave involves treating them like new hires in some aspects, aiding their transition back into the team effectively.
- Managing coverage during leaves often involves internal solutions, though external resources may be utilized in specific roles, balancing workloads to support absent team members.
- Remaining adaptable and creative in crafting solutions for employees on extended leave, such as implementing remote work arrangements, can aid in retaining valuable talent.
- Flexible leave policies contribute to employee retention, loyalty, and enhanced problem-solving skills, fostering a supportive and trusting work environment.
Read Full Article
21 Likes
Medium
307
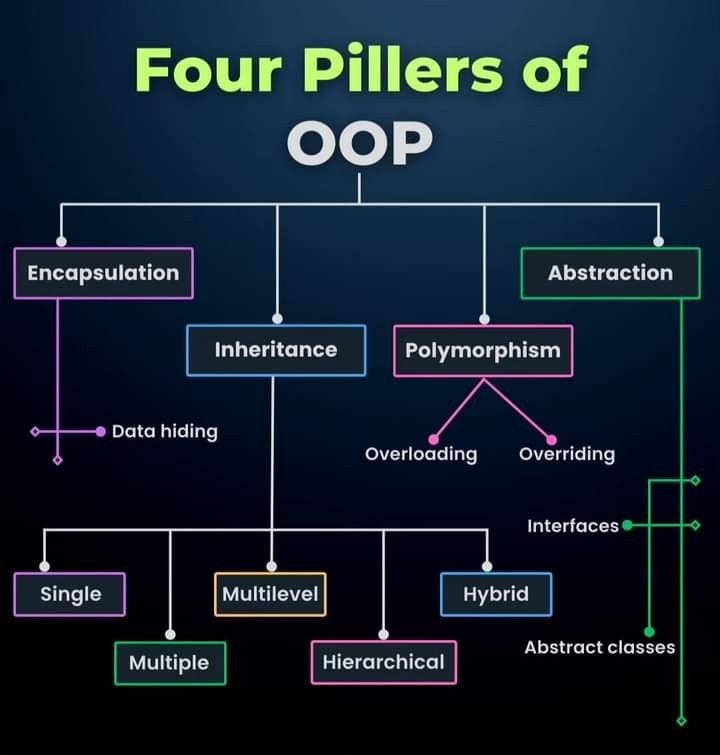
Image Credit: Medium
How Object-Oriented Programming Powers Game Development
- Object-Oriented Programming (OOP) is a programming paradigm widely used in game development to organize code around game entities like players, enemies, weapons, and levels.
- A class serves as a blueprint for creating objects with defined attributes (data) and behaviors (methods).
- Encapsulation, inheritance, polymorphism, and abstraction are core OOP principles applied in game development to structure and extend functionality efficiently.
- OOP provides a structured, maintainable approach to build complex games by managing game logic, behaviors, and interactions effectively.
Read Full Article
18 Likes
TronWeekly
0

Image Credit: TronWeekly
XRP and RLUSD Launch Triggers Financial Revolution Beyond SWIFT
- RLUSD and XRP have created a decentralized FX arbitrage network outside traditional systems, targeting SWIFT and capital control regimes.
- XRP has evolved to become a key component of global institutional liquidity flows, with major institutional and sovereign players adopting it for real-world financial infrastructure.
- RLUSD, a stablecoin merged with XRP, offers a synthetic, off-chain dollar infrastructure that is stable, decentralized, and programmable, helping compress bid/ask spreads and arbitrage mispriced currencies.
- Ripple's RippleNet and XRP are gaining traction with partnerships in cross-border payments, institutional finance, and tokenization, as well as with support from ISDA, Coinbase, CME, and other networks.
Read Full Article
Like
Medium
117

Image Credit: Medium
UI Complexity as a Factorial Theory
- UI complexity management aims to reduce factorial complexity in user interfaces, where more input orderings and dependencies lead to increased system complexity.
- A theoretical model is introduced in this article, framing UI design as a complexity problem grounded in set theory, combinatorics, and ordering logic.
- Factorial complexity in UI systems is often inevitable due to discrete interaction paths and user input freedom, highlighting the importance of understanding growth patterns for scalability.
- Different UI structures exhibit varying levels of complexity, ranging from linear wizards with O(1!) complexity to fully connected free navigation with O(n!) complexity.
Read Full Article
7 Likes
Medium
67

Image Credit: Medium
Why Python Is the Best Language to Start Your Data Analytics Journey
- Python is considered the best language to start your data analytics journey due to its beginner-friendly nature and simplicity.
- It is recommended even for those who have never written a line of code before, making it accessible for total beginners.
- Python is highlighted as the easiest and most approachable way to begin learning data analytics, providing a smooth entry point into the field.
- The article also offers a list of free resources for readers to start learning Python immediately after reading.
Read Full Article
4 Likes
For uninterrupted reading, download the app