Programming News
Self-Learning-Java
239

Image Credit: Self-Learning-Java
How to Explore All Available Metrics in Prometheus UI (Step-by-Step Guide)?
- Understanding available metrics is crucial when working with Prometheus for querying and insights.
- Navigate to http://localhost:9090 to open the Prometheus UI.
- Locate the Expression Bar and click on the three dots next to the query box to select 'Explore metrics.'
- In the 'Explore metrics' panel, you can view a searchable list of all metrics scraped by Prometheus.
Read Full Article
14 Likes
Medium
407

Image Credit: Medium
Renaming and Moving assets in Unreal Engine
- Renaming assets in Unreal Engine, like plugins, can be a complex process that requires careful attention to avoid breaking the project.
- Always backup your project before renaming or moving assets to prevent potential project-breaking errors.
- Different editors like JetBrains Rider and Visual Studio have varying processes for renaming assets, with JetBrains Rider offering a more seamless experience.
- When renaming assets, such as Blueprints, ensuring that redirectors are properly updated and references are fixed is crucial to maintaining project integrity.
Read Full Article
24 Likes
Self-Learning-Java
366
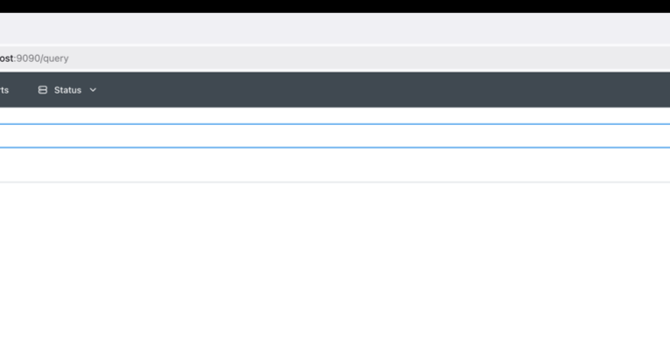
Image Credit: Self-Learning-Java
Start Prometheus by Supplying a Config File
- To start Prometheus by supplying a config file when installed via Homebrew on macOS, follow these steps:
- Check where Prometheus binary is installed using 'which prometheus' command to confirm the installation location.
- Create a basic configuration file named 'prometheus.yml' with global configurations and scrape configurations for targets.
- Start Prometheus with the new config file by running 'prometheus --config.file={PATH TO prometheus.yml}' command and can query metrics using the Prometheus UI.
Read Full Article
22 Likes
Medium
444

Image Credit: Medium
The Full Stack Illusion: Jack of All, Master of None
- The concept of full stack developers is popular, but they may not be experts in both frontend and backend technologies as expected.
- Full stack developers might compromise depth for breadth in covering various aspects of development.
- Expecting one person to master both frontend and backend completely may not yield the best results for complex projects.
- It is essential to recognize the limits of full stack developers and encourage them to specialize to create more robust products.
Read Full Article
26 Likes
Discover more
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Dev
371

Image Credit: Dev
Introducing a new command to the Python Polylith tool
- The Python tools for Polylith Architecture have introduced a new command called poly test, which includes a sub-command poly test diff.
- Polylith is an architecture that supports having multiple Microservices in a Monorepo and allows code sharing between services.
- The poly test command helps identify bricks and projects affected by changes in tests, similar to the existing poly diff command.
- This new command provides a structured way to identify affected bricks and projects when automated tests are updated.
Read Full Article
22 Likes
Dev
239

Image Credit: Dev
Top .NET Interview Questions for 2024-2025
- The article lists the top .NET interview questions for 2024-2025 based on real-world experiences and trusted sources.
- Questions cover .NET basics, architecture, advanced C# and OOP concepts, advanced concepts and optimization, ASP.NET Core and Web API, database and Entity Framework, as well as tools and best practices.
- Topics include differences between .NET Framework and .NET Core, CLR responsibilities, LINQ benefits, MVC pattern in ASP.NET, implementation of RESTful API, Entity Framework advantages, NuGet package manager, performance optimization, and common design patterns in .NET.
- The questions aim to help .NET developers prepare for technical interviews by covering various essential topics and concepts in the field.
Read Full Article
14 Likes
Dev
18

Image Credit: Dev
Process to Create a Movie Recommender in the Terminal
- The movie recommender program was created in the terminal by focusing on using class and different data structures in Python.
- The data structure for the movie database consisted of nodes containing a dictionary with key-value pairs for movie information like name, genre, rating, actors, and synopsis.
- Data was sourced from RottenTomatoes, compiled into a CSV file, and initialized into Movie class objects in the program.
- The user interface allowed users to add filters to their search preferences, saved in a dictionary and used in a simple linear search algorithm to display recommended movies based on criteria like rating, actors, and genres.
Read Full Article
1 Like
Python Blogs
72
Image Credit: Python Blogs
TikTok Engagement Rate Calculator: Why the Numbers Matter!
- TikTok engagement rate is a score that measures how much people are interacting with your content, including likes, comments, shares, and saves.
- Engagement rate is crucial for attracting sponsorship deals, gaining visibility on TikTok's algorithm, and growing your audience faster.
- The formula to calculate engagement rate is (Likes + Comments + Shares) ÷ Total Views × 100. A rate of 5%-10% is considered good.
- Factors that can impact your engagement rate include video quality, hook, captions, timing, and trendiness. Using a TikTok engagement rate calculator can simplify tracking and comparing your video performances.
Read Full Article
4 Likes
Dev
18

Image Credit: Dev
Top AI Tools and Libraries for Java Developers in 2025
- AI is transforming software development by offering tools and libraries for various applications, including machine learning and natural language processing, in the Java ecosystem.
- Deeplearning4j is a powerful deep learning library on JVM, providing scalability and integration with big data frameworks like Hadoop and Apache Spark for solving complex problems.
- Keploy is an API testing platform for creating test cases and data mocks from API calls, useful for testing AI models and ensuring consistent behavior.
- Apache OpenNLP is a Java library for natural language processing, aiding in text analysis and classification tasks.
- Weka is a popular machine learning and data mining tool for various tasks like data preprocessing, visualization, and API integration.
- Spring AI simplifies AI application development in Java by offering tools for integrating AI functionalities like chat models and text-to-image generation with ease.
- GitHub Copilot is an AI coding assistant that generates code suggestions and test cases, improving development efficiency and code quality.
- Tabnine is an AI-powered code completion tool that predicts and suggests code snippets while typing, enhancing productivity and focusing on problem-solving in Java development.
- Java's suitability for AI development lies in its robustness, platform independence, community support, and availability of libraries and frameworks tailored for AI projects.
- The future of AI in Java looks promising with advancements in libraries like Deeplearning4j and improved integration with machine learning frameworks, paving the way for smarter applications.
Read Full Article
1 Like
Medium
27
Image Credit: Medium
Python Project Structure: Why the ‘src’ Layout Beats Flat Folders (and How to Use My Free Template)
- A clear, repeatable folder structure is crucial for Python projects to avoid 'import hell' and ensure a predictable workflow.
- The 'src' layout, where all importable code is placed in a src/ folder, is recommended for medium-to-large apps and projects that ship to production.
- Placing code under src/ helps prevent import conflicts, keeps PyPI uploads clean, allows for easy package uninstallation, and provides clarity as the project grows.
- While a flat layout is suitable for small scripts and demos, transitioning to a src layout early can prevent refactoring difficulties in the future.
Read Full Article
1 Like
Dev
402

Image Credit: Dev
NumberGuessingGame with springBoot and java
- A Number Guessing Game was implemented in Java using Scanner and Random classes.
- The game randomly selects a number between 1 and 100 for the user to guess.
- The implementation involves user input, comparison with the generated number, and congratulatory message on successful guess.
- Another version of the game was developed using Spring Boot with controllers and templates for a web interface.
Read Full Article
24 Likes
Dev
108
Image Credit: Dev
Build your resume in minutes with AI-powered precision
- InstaResume.io offers an AI-powered Resume Builder for creating tailored, professional resumes.
- The tool provides AI-powered suggestions, professionally designed templates, smart formatting, and real-time content tips.
- It caters to individuals at all career stages, including fresh graduates, career switchers, senior professionals, freelancers, and creatives.
- Users have praised the platform for helping them secure interviews, saving time on formatting, and offering clean, ATS-friendly templates.
Read Full Article
6 Likes
Dev
212

Image Credit: Dev
Shallow Copy & Deep Copy in Python
- Variable assignment in Python can result in shallow copy or deep copy.
- Shallow copy creates a new object but references the same elements as the original object.
- Deep copy creates a new object and recursively adds copies of nested objects.
- Methods like .copy(), deepcopy() and list() can be used for creating shallow or deep copies in Python.
Read Full Article
12 Likes
Dev
58

Image Credit: Dev
Variable assignment in Python
- Python allows assigning one or more values to one or more variables.
- String type values cannot be changed directly, but list() and join() can be used for such operations.
- Variables in Python can hold references to lists, changing one list can affect other variables referencing the same list.
- Assigning multiple values with commas creates a tuple in Python.
Read Full Article
3 Likes
Medium
266

Image Credit: Medium
10+ Code Editors That Help with a Programming Assignment
- Programming assignments involve developing projects on selected topics, requiring presentations, code, reports, and final presentations, with assistance available from the Instant Assignment Help website.
- Learning about various languages and coding concepts through programming assignments is essential for writing code to solve specific problems and exploring different code editors and their features.
- Code editors offer benefits in syntax, formatting, error detection, and compilation, improving speed and efficiency in coding by marking mistakes in real-time and providing suggestions for correction.
- Different types of code editors address syntax, formatting, and bugs effectively with specialized features and functions, working across different languages and compilers to aid in various programming tasks.
- Examples of code editors like Visual Studio Code, Sublime Text, Notepad++, Vim, Atom, GNU Emacs, CodeSandbox, TextMate, Bluefish, NetBeans, and Acode are discussed with their unique features and benefits.
- Each code editor has specific strengths, such as Visual Studio Code's flexibility in supporting various languages, Sublime Text's customizability and shortcuts, and Notepad++'s speed and lightweight nature.
- Code editors like Atom allow real-time collaboration, GNU Emacs offers high customizability, CodeSandbox is browser-based, and Acode is specifically designed for Android devices.
- Choosing the right code editor depends on factors like ease of use, system compatibility, features required, and specific programming needs, with a variety of options available in the market to enhance coding skills and efficiency.
- By using different code editors, programmers can optimize their programming tasks, explore various features, and improve their coding experience, ultimately enhancing their overall programming skills and knowledge.
- Utilizing programming assignment help services can provide valuable insights into selecting and effectively utilizing different code editors to enhance programming tasks and learning.
Read Full Article
16 Likes
For uninterrupted reading, download the app