Info. Security News News
Pymnts
282

Image Credit: Pymnts
Report: China-Connected Hackers Breach US Broadband Networks
- Hackers with ties to China's government have breached American internet service providers.
- The hacking campaign, known as Salt Typhoon, targeted sensitive information.
- This hack is part of a series of attacks linked to China.
- Investigators are looking into the extent of the breach and potential access to critical information.
Read Full Article
16 Likes
Securityaffairs
13
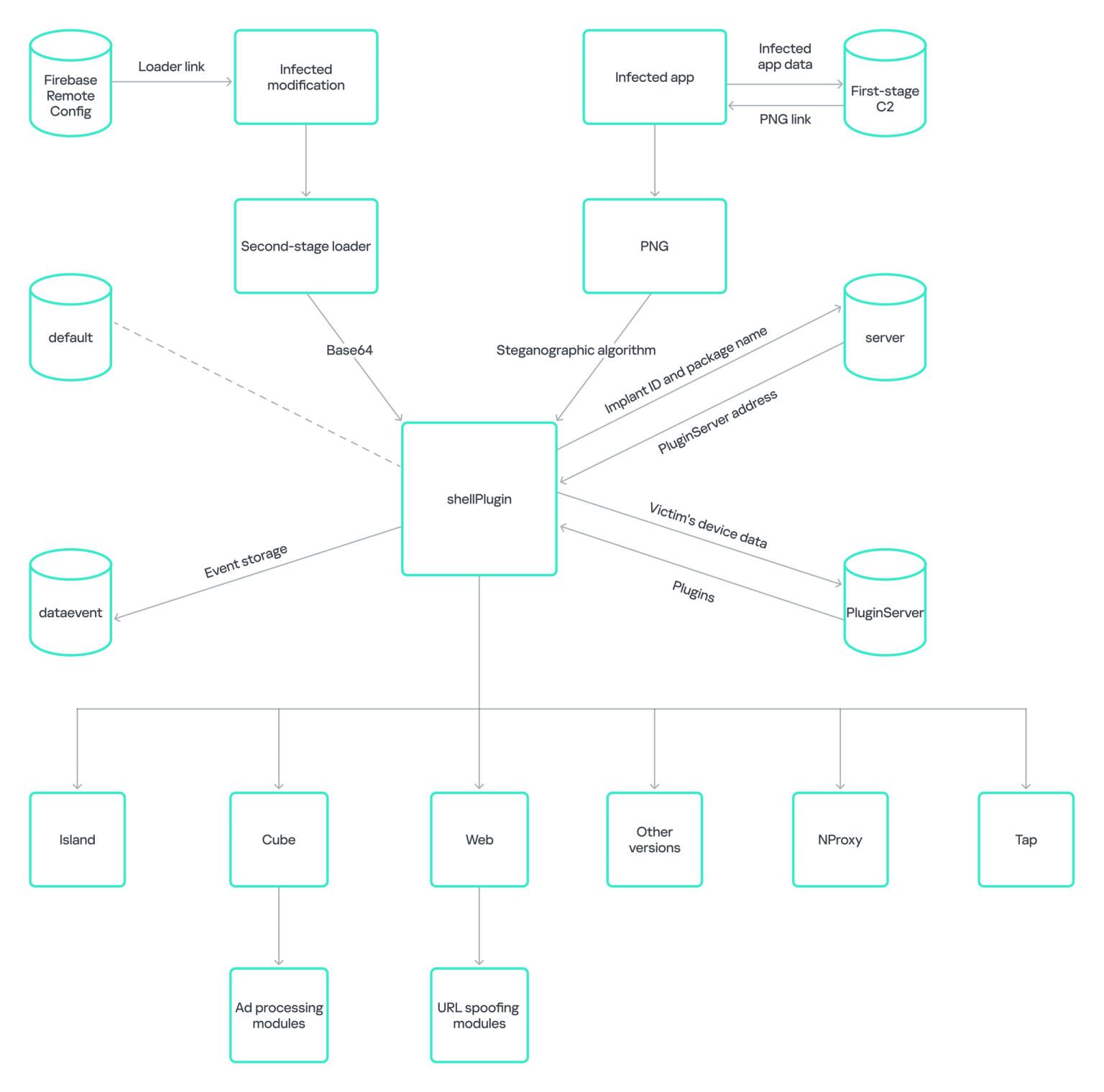
Image Credit: Securityaffairs
New variant of Necro Trojan infected more than 11 million devices
- A new variant of the Necro Trojan has infected more than 11 million devices through fake versions of legitimate Android apps.
- The malware was found in popular applications and game mods on the Google Play store.
- The new version of the Necro loader uses obfuscation and steganography techniques to evade detection and can perform various malicious actions.
- Security experts believe the malware entered the Play Store through a tainted software developer kit (SDK).
Read Full Article
Like
Amazon
282

Image Credit: Amazon
Managing identity source transition for AWS IAM Identity Center
- AWS IAM Identity Center manages user access to Amazon Web Services (AWS) resources, including both AWS accounts and applications.
- Organizations might change the configuration of their identity source in IAM Identity Center for various reasons. These include switching identity providers (IdPs), expanding their identity footprint, adopting new features, and so on.
- Understanding these identity source options can help you choose the source that best fits your user management needs based on your existing infrastructure and authentication requirements.
- When you change the identity source, the work required varies depending on the original and new sources.
- This deployment covers permission sets and application assignments’ backup and restore.
- Assignments can be backed up by running the backup.py file from GitHub.
- The target will become the new authoritative identity source. When done, verify that the group memberships and attributes have been correctly transferred.
- Update your IAM Identity Center configuration to point to the new source.
- Assignments can be restored by running the restore.py file from GitHub.
- By following these steps, you can streamline the transition process, providing a smooth and efficient transfer of user access with minimal downtime.
Read Full Article
16 Likes
Krebsonsecurity
9

Timeshare Owner? The Mexican Drug Cartels Want You
- The FBI is warning timeshare owners to be wary of a prevalent telemarketing scam involving a violent Mexican drug cartel that tries to trick people into believing someone wants to buy their property.
- The Dimitruks, a retired couple from Ontario, Canada reportedly lost over $50,000 to an ongoing timeshare scam that spans at least two dozen phony escrow, title and realty firms.
- The phone scammers attempt to trick elderly individuals into paying money to sell off their timeshares.
- The FBI warns the timeshare fraud schemes have been linked to the Jalisco New Generation drug cartel in Mexico.
- In July 2024, the FBI and the Treasury Department’s Financial Crimes Enforcement Network (FinCEN) warned the Jalisco cartel is running boiler room-like call centers that target people who own timeshares.
- The fraudulent timeshare offers are part of a larger scheme to launder money for the drug trade.
- It is unclear whether the Dimitruks were robbed by people working for the Jalisco cartel, but it is clear that whoever is responsible for managing many of these domains recently compromised their computer with information-stealing malware.
- Escshieldsecurity pitches itself as a solution to timeshare closing scams.
- If you are the victim of a timeshare scam like this, please consider filing a report with the FBI’s Internet Crime Complaint Center (IC3), at ic3.gov.
- The feds will bust up one of these scam operations and seize funds that were stolen from victims.
Read Full Article
Like
Hackersking
27

Image Credit: Hackersking
Instagram Password Cracking With Insta-Breaker On Linux
- Insta-Breaker is an open-source brute-force password cracking tool designed for Instagram accounts.
- It is used for ethical hacking purposes and testing the security of Instagram accounts.
- Insta-Breaker is easy to install on Linux and has features like brute-force attack using password list.
- It's important to use Insta-Breaker responsibly and legally for legitimate security testing purposes.
Read Full Article
1 Like
Qualys
54

Image Credit: Qualys
Addressing Cloud Identity Risks With TotalCloud CIEM
- With thousands or tens of thousands, potentially even millions of machine identities to manage, ensuring each has the right level of access becomes increasingly complex.
- Cloud Infrastructure Entitlement Management (CIEM) is designed to address the security risks associated with cloud identities and permissions.
- CIEM helps organizations gain visibility into their cloud identities and ensures that these identities adhere to the principle of least privilege, granting the minimum level of access necessary to perform a task.
- CIEM provides visibility into all identities across cloud environments. This inventory helps organizations monitor and manage cloud permissions effectively.
- The CIEM functionality in TotalCloud enhances the existing CSPM capabilities by extending visibility into cloud identities and entitlements, helping organizations optimize cloud permissions and reduce their attack surface.
- CIEM strengthens cloud security by ensuring that identity-related risks are identified and mitigated before they can be exploited.
- TotalCloud TruRisk Insights aggregates data from various sources, including CSPM, CWP, CDR, and now CIEM, to provide a holistic view of the cloud security posture.
- The combination of CIEM and TruRisk Insights offers improved identity hygiene, reduced insider threats, streamlined compliance, and faster response to threats.
- By integrating CIEM into your existing cloud security strategy, you can reduce your attack surface, enhance compliance, and improve overall cloud security.
- Qualys TotalCloud platform has introduced CIEM into its CNAPP offering, enabling organizations to monitor and manage identity risks in tandem with configuration security.
Read Full Article
3 Likes
Sentinelone
427

Image Credit: Sentinelone
Continuous Innovation & Customer Commitment | SentinelOne is a Leader Again in the 2024 Gartner® Magic Quadrant™
- SentinelOne is recognized as a Leader in the Gartner Magic Quadrant for Endpoint Protection Platforms for the fourth year in a row.
- With SentinelOne’s AI-powered Singularity Platform, organizations can achieve cyber resiliency with real-time protection across endpoints, identities, and cloud environments.
- SentinelOne continues to lead the cybersecurity industry with its deep investment in AI innovation.
- The Unified Security Platform streamlines security operations, unifies native and third-party security tools to deliver increased efficiency and reduced risk.
- SentinelOne pushes the boundaries of security innovation with a relentless focus on customer feedback.
- SentinelOne delivers a scalable and flexible security platform that meets the diverse needs of organizations and service providers globally.
- Nearly 13,000 customers trust SentinelOne to protect their most critical assets.
- In addition to being named a Leader in the 2024 Gartner Magic Quadrant for Endpoint Protection Platforms, SentinelOne also earned “Customers’ Choice” recognition in the 2024 Gartner Peer Insights Voice of the Customer for Endpoint Protection Platforms.
- SentinelOne is the fastest-growing endpoint cybersecurity company today.
- SentinelOne has also launched several emerging solutions, including Singularity AI SIEM, Purple AI, Singularity Cloud Security, and Singularity MDR, to drive significant growth.
Read Full Article
25 Likes
Amazon
445

Image Credit: Amazon
2024 H1 IRAP report is now available on AWS Artifact for Australian customers
- Amazon Web Services (AWS) releases the IRAP report (2024 H1) on AWS Artifact.
- The report includes an additional seven AWS services assessed at the PROTECTED level.
- Newly assessed services include AWS App Runner, Amazon Bedrock, Amazon DataZone, and more.
- AWS offers an IRAP documentation pack and welcomes feedback for upcoming assessments.
Read Full Article
26 Likes
Socprime
159

Image Credit: Socprime
SnipBot Detection: A New RomCom Malware Variant Leverages a Custom Code Obfuscation Method and Sophisticated Evasion Techniques
- A new variant of the RomCom malware family called SnipBot has been discovered.
- SnipBot uses advanced evasion techniques and a custom code obfuscation method to move laterally within networks and exfiltrate data.
- It is actively deployed by the Tropical Scorpius group for Cuba ransomware distribution.
- SnipBot indicates a shift in focus from financial gain to cyber-espionage operations, primarily targeting Ukraine and its allies.
Read Full Article
9 Likes
Kaspersky
131

Image Credit: Kaspersky
How to make offline backups of documents, photos, music, and videos from websites and online services | Kaspersky official blog
- Online data is not always stored safely and forever; backups are necessary to protect important information from ransomware and spyware.
- Data loss can occur in various ways due to redesigns, copyright issues, shut-downs, cyberattacks, and more.
- There are two distinct types of online content loss: (1) when one can no longer find publicly available information and (2) when one loses their own data, such as photos and documents.
- To prepare for data loss, one should create a list of all important data in the digital world, sorting them in descending order of importance and making backup copies.
- Several backup options for different types of information include downloading files to your drive, exporting from online services, using specialized software, storing backups in multiple online services, setting up automatic backups to another service, and data portability backed by law.
- For files that are stored online, backing up photos, documents, and other files that can be easily opened on a computer is the simplest way to back up.
- Online applications and services allow you to export data, or create an archive or backup; users should also explore different formats available for exported data.
- There are dedicated online services for creating web page backups for personal use, such as Pocket, archive.is, and web.archive.org.
- Storing backups in multiple online services at the same time, setting up automatic backups to another service, and data portability backed by law are other options for backing up data online.
- The article suggests readers download reliable protection to avoid picking up malware when searching for specialized export tools or software.
Read Full Article
7 Likes
Dev
400

Image Credit: Dev
How Does WAF Prevent OS Command Injection Attacks
- OS command injection is a type of security vulnerability that allows an attacker to execute arbitrary operating system (OS) commands on a server running an application.
- Command injection attacks can lead to unauthorized access and control of the underlying system, potentially compromising the entire server.
- Examples of OS Command Injection include applications that perform ping and web apps that take filename and plot contents as output.
- Prevention of OS Command Injection is achieved by applying principles of least privilege and input validation and sanitization.
- Web Application Firewall helps prevent OS command injection by using detection and mitigation techniques to inspect, filter and block malicious requests before they reach the web application.
- SafeLine WAF is a web application firewall which combined prevention techniques and provides robust defense against OS command injection attacks.
Read Full Article
24 Likes
Securityaffairs
50

Image Credit: Securityaffairs
U.S. CISA adds Ivanti Virtual Traffic Manager flaw to its Known Exploited Vulnerabilities catalog
- The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a vulnerability in Ivanti Virtual Traffic Manager (vTM) to its Known Exploited Vulnerabilities catalog.
- The vulnerability, CVE-2024-7593, allows attackers to bypass authentication and create rogue administrator accounts on vTM appliances.
- Ivanti has released patches to address the flaw and recommends limiting admin access to the management interface.
- Federal agencies have been ordered by CISA to fix this vulnerability by October 15, 2024.
Read Full Article
3 Likes
Securityaffairs
40
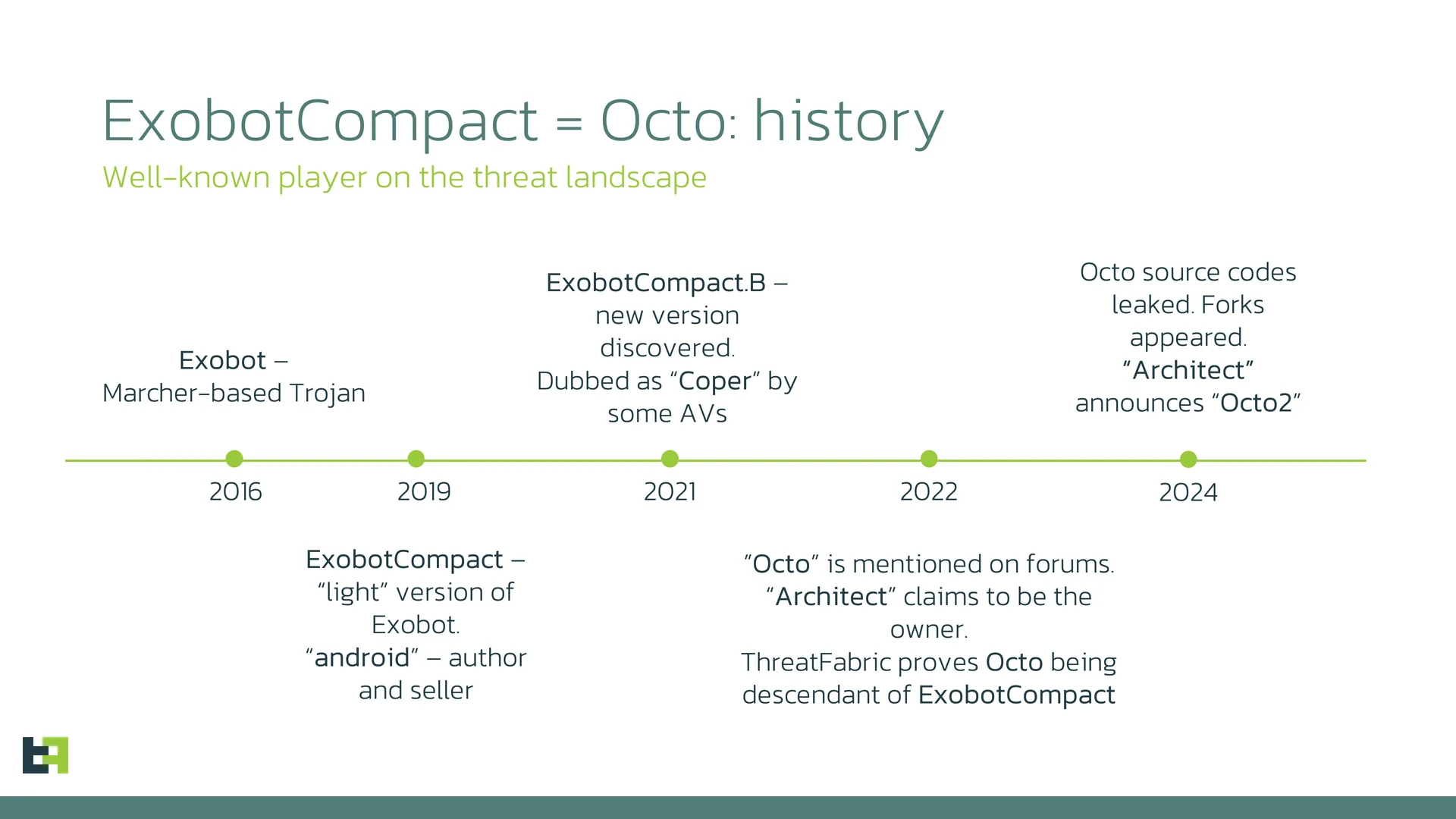
Image Credit: Securityaffairs
New Android banking trojan Octo2 targets European banks
- A new version of the Android banking trojan Octo, called Octo2, has been discovered.
- Octo2 supports advanced remote action capabilities for Device Takeover attacks.
- The trojan has targeted users in European countries, including Italy, Poland, Moldova, and Hungary.
- Octo2 is an improved version of Octo malware, which operates as a Malware-as-a-Service.
Read Full Article
2 Likes
Securityaffairs
186
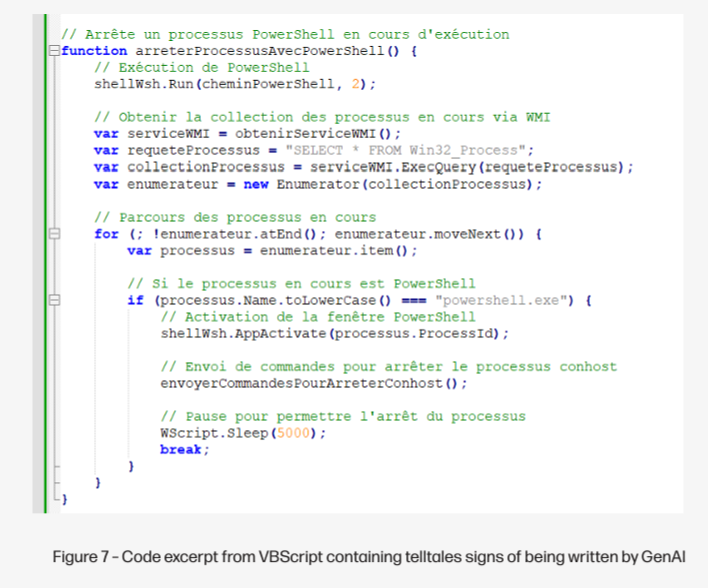
Image Credit: Securityaffairs
A generative artificial intelligence malware used in phishing attacks
- HP researchers detected a dropper that was generated by generative artificial intelligence services and used to deliver AsyncRAT malware.
- The AI-generated malware was discovered in June 2024, using an invoice-themed lure and encrypted HTML attachment to avoid detection.
- The malware utilized VBScript as a dropper for the AsyncRAT infostealer, with the attacker leaving comments throughout the code.
- The use of generative AI in creating malicious code highlights the acceleration of cyberattacks and makes it easier for criminals to develop malware.
Read Full Article
11 Likes
Hackingblogs
50

Image Credit: Hackingblogs
$230 Million Bitcoin Were Stolen Which Are Now Recovered : Hacker Under Arrest
- On August 19, 2024, 4064 BTC ($238M) were stolen in a phishing operation.
- The stolen funds were recovered, and the hackers were arrested.
- The cybercriminals used phishing techniques and remote access software to carry out the attack.
- ZachXBT, a well-known crypto investigator, played a crucial role in tracking and exposing the hackers.
Read Full Article
3 Likes
For uninterrupted reading, download the app