Info. Security News News
Securityaffairs
403
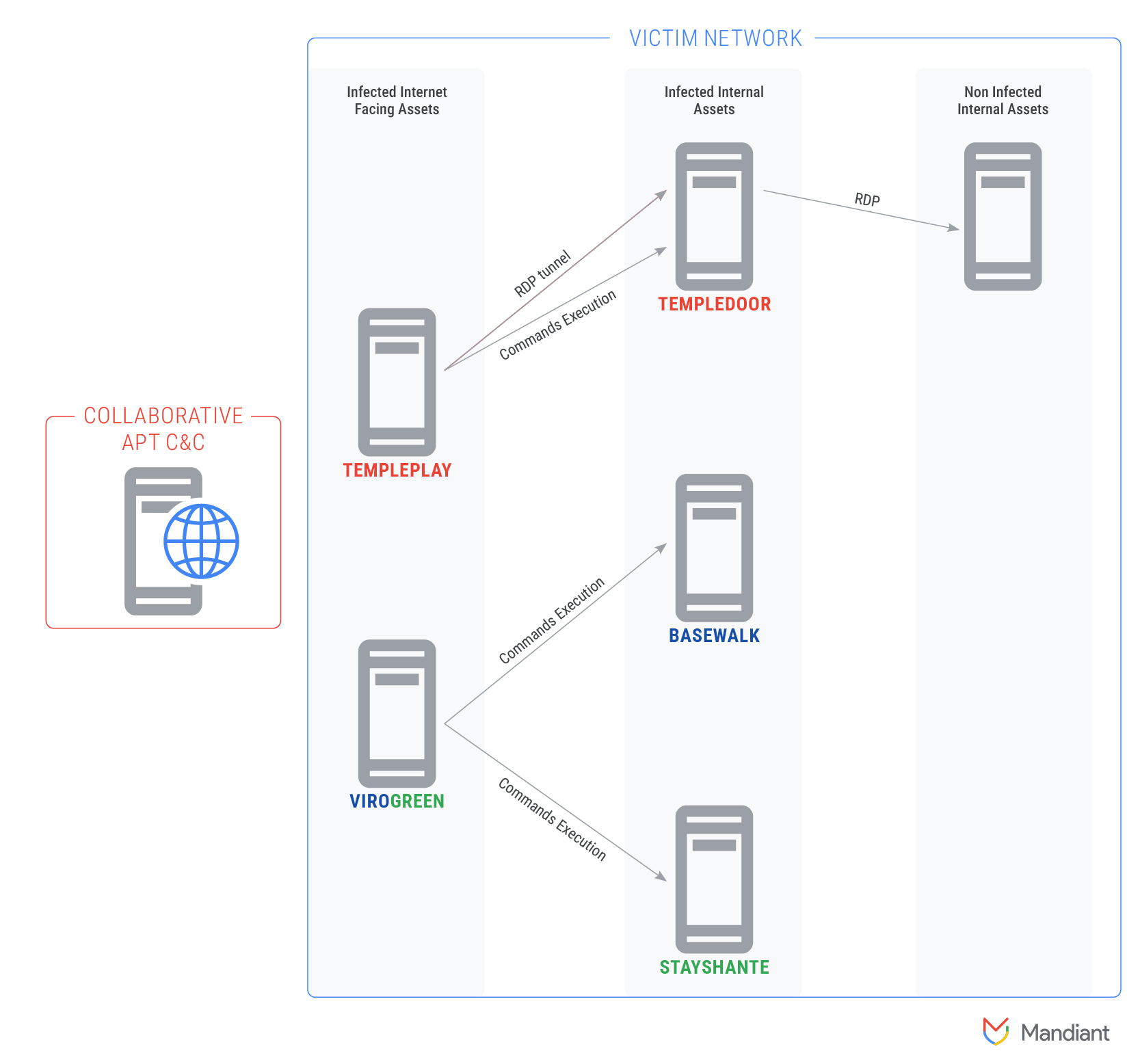
Image Credit: Securityaffairs
UNC1860 provides Iran-linked APTs with access to Middle Eastern networks
- Iran-linked APT group UNC1860 is operating as an initial access facilitator that provides remote access to Middle Eastern Networks.
- UNC1860 specializes in using customized tools and passive backdoors to gain persistent access to high-profile networks in the government and telecommunications sectors across the Middle East.
- The group shares tactics with other Iran-linked threat groups and may support state-sponsored hackers in performing lateral movement.
- UNC1860's arsenal includes a wide range of passive tools and backdoors supporting initial access, lateral movement, and data gathering.
Read Full Article
24 Likes
Sentinelone
434

Image Credit: Sentinelone
The Good, the Bad and the Ugly in Cybersecurity – Week 38
- The U.S. Department of the Treasury sanctioned five executives and an entity tied to the Intellexa Consortium, known for developing the controversial Predator spyware.
- Europol and law enforcement from nine countries seized a communication platform called “Ghost” used by organized crime groups for money laundering and drug trafficking.
- Chinese national, Song Wu, has been indicted by the FBI for a years-long spear phishing campaign targeting NASA, U.S. military agencies, and research universities.
- GitHub is again being abused to distribute the info-stealing malware Lumma Stealer that is targeting open source project repositories and those subscribed to them.
- A new report by cybersecurity researchers details a sophisticated botnet called “Raptor Train” that has been operating since May 2020.
- The botnet has infected over 200,000 endpoints worldwide, including small office/home office (SOHO) routers, IoT devices, IP cameras, and network-attached storage (NAS) servers.
- Raptor Train has yet to launch any DDoS attacks, it has been weaponized to execute reconnaissance and exploitation efforts against the military, government, defense industrial base (DIB), telecommunications, and IT sectors.
- The FBI has successfully dismantled the botnet following a court-authorized operation.
- However, the agency warns that the Chinese government will continue to target organizations in critical sectors in intelligence-gathering campaigns.
- Users are advised to be cautious, avoid clicking suspicious links, and continue reporting these issues to GitHub for investigation.
Read Full Article
26 Likes
Securityintelligence
146

Image Credit: Securityintelligence
New cybersecurity advisory highlights defense-in-depth strategies
- CISA has released its SILENTSHIELD assessment report detailing red-team findings after a breach of an FCEB organization, which has a renewed focus on defense-in-depth strategies.
- The red team was successful in lateral movement and persistence through exploiting trust relationships and deploying defense evasion techniques.
- CISA shared four key findings with the FCEB organization after the collaboration phase, including: insufficient controls, failure to effectively collect and analyze network logs, poor communication between network defenders due to decentralized structure, and failed breach detection of new threat actors.
- CISA recommends that businesses use defense-in-depth principles, apply robust network segmentation, establish baselines of network traffic, application execution, and account authentication, and make sure their business is prepared for a cyber breach.
- Organizations need to adopt a more holistic strategy for cybersecurity, including firewalls, intrusion detection and prevention systems, and antivirus and antimalware tools.
- Benchmarking current network traffic patterns can provide an easier recognition of anomalies that could point to malicious activities, allowing for the response teams to address threats before they become significant issues.
- IBM X-Force Cyber Range can help organizations better prepare their defenses by providing immersive simulations.
- Proactive planning can significantly benefit IT teams, ensuring their security protocols are hardened and ready to face modern cyber threats.
- CISA’s recent assessment is an example of the importance of effective security and breached preparedness planning.
- IBM X-Force Cyber Range can provide the tools and techniques businesses need to keep their organization secure.
Read Full Article
8 Likes
Securityaffairs
54

Image Credit: Securityaffairs
U.S. CISA adds new Ivanti Cloud Services Appliance Vulnerability to its Known Exploited Vulnerabilities catalog
- U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Ivanti Cloud Services Appliance Vulnerability to its Known Exploited Vulnerabilities catalog.
- The vulnerability, tracked as CVE-2024-8963, is actively exploited in attacks against a limited number of customers.
- An attacker could exploit the vulnerability to access restricted functionality and execute arbitrary commands on the appliance.
- CISA orders federal agencies to fix this vulnerability by October 10, 2024.
Read Full Article
3 Likes
Siliconangle
333

Image Credit: Siliconangle
Google Cloud’s Kevin Mandia on the evolving role of the CISO in cybersecurity risk management
- Industries adapting to a digital landscape demands that cybersecurity risk management becomes more critical than ever with Google Cloud’s Kevin Mandia discussing the evolving role of the CISO in managing risks. The focus on cybersecurity intensifies while the rapid growth of AI is combined with complex cyber threats, pushing companies to rethink their security strategies. The role of the CISO is expanding to include not only traditional information security but also supply chain and data integrity. Companies need to be prepared for when a cyber incident occurs, emphasizing the need for resilience in the face of evolving digital threats.
- There is a growing need for CISOs to advocate for their place at the leadership table. The role of the CISO is constantly changing, including supply chain and physical security. Mandia pointed out that too many companies do not yet have centralized control, which is a growing concern as more businesses integrate technology into their operations. The way companies manage their expanding security responsibilities has raised questions.
- Regular tabletop exercises, where companies simulate a breach to test their disaster recovery plans, are important in ensuring resilience. People started becoming better after ransomware was introduced, focusing on how quickly an organisation could recover. Companies should have the ability to segment their assets, so that if someone has access or credentials, they cannot access everything, thus reducing the blast radius.
- "TheCUBE" is an important partner to the industry with over 15,000 #CubeAlumni experts, including Amazon CEO Andrew Jassy, Dell Technologies founder and CEO Michael Dell, Intel CEO Pat Gelsinger, and many more. Google Cloud Security sponsored an interview with Kevin Mandia, while neither having editorial control over content on theCUBE or SiliconANGLE.
Read Full Article
20 Likes
Securityaffairs
91

Image Credit: Securityaffairs
Ivanti warns of a new actively exploited Cloud Services Appliance (CSA) flaw
- Ivanti warns of a new Cloud Services Appliance (CSA) vulnerability (CVE-2024-8963) actively exploited in attacks.
- The vulnerability allows remote unauthenticated attackers to access restricted functionality.
- Attackers can combine this flaw with CVE-2024-8190 to bypass admin authentication and execute arbitrary commands.
- CSA 4.6 is affected, and customers are advised to upgrade to Ivanti CSA 5.0 for continued support.
Read Full Article
5 Likes
Pymnts
224

Image Credit: Pymnts
Report: Disney Cuts Ties With Slack After Data Heist
- Disney plans to stop using workplace collaboration platform Slack following a recent data breach.
- Teams at Disney are switching to streamlined enterprise-wide collaboration tools.
- A hacker stole a terabyte worth of data from Slack and leaked it online.
- The breach included financial and personal information of employees and customers.
Read Full Article
13 Likes
Krebsonsecurity
132

This Windows PowerShell Phish Has Scary Potential
- GitHub users received a phishing email warning of security holes in their code.
- Clicking the link led to a fake CAPTCHA page asking users to prove their humanity.
- The CAPTCHA involved pressing specific key combinations that downloaded password-stealing malware.
- The malware downloaded is called Lumma Stealer, designed to steal credentials from victims' PCs.
Read Full Article
7 Likes
Securityaffairs
324

Image Credit: Securityaffairs
International law enforcement operation dismantled criminal communication platform Ghost
- An international law enforcement operation infiltrated the encrypted messaging app Ghost, which was widely used by criminals, resulting in the arrest of dozens of individuals.
- The alleged administrator of the app, Jay Je Yoon Jung, was charged with supporting a criminal organization and profiting from illegal activities.
- The Ghost app supported advanced security features and was promoted in the crime ecosystem through a network of resellers.
- The operation, led by FBI and French Gendarmerie, successfully dismantled Ghost, used for serious and organized crime globally.
Read Full Article
19 Likes
Kaspersky
429

Image Credit: Kaspersky
Spearphishing tricks in mass emails | Kaspersky official blog
- Attackers continue to use spearphishing techniques in mass emails.
- A recent sample email reveals sophisticated spearphishing tricks, targeting a specific individual and organization.
- The email mimics corporate guidelines, uses ghost spoofing, and is sent through a reputable marketing company's infrastructure.
- The attackers employ an attached PDF file with concealed links and a phishing website that ultimately fails.
Read Full Article
25 Likes
Securityaffairs
84

Image Credit: Securityaffairs
U.S. CISA adds Microsoft Windows, Apache HugeGraph-Server, Oracle JDeveloper, Oracle WebLogic Server, and Microsoft SQL Server bugs to its Known Exploited Vulnerabilities catalog
- U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Microsoft Windows, Apache HugeGraph-Server, Oracle JDeveloper, Oracle WebLogic Server, and Microsoft SQL Server bugs to its Known Exploited Vulnerabilities catalog.
- CVE-2022-21445 vulnerability is a remote code execution issue in Oracle JDeveloper, allowing an attacker to compromise the system.
- CVE-2020-14644 vulnerability is a remote code execution issue in Oracle WebLogic Server, allowing an attacker to compromise the system.
- CVE-2019-1069 vulnerability is an elevation of privilege issue in Microsoft Windows Task Scheduler, enabling an attacker to gain elevated privileges on a victim system.
- CVE-2020-0618 vulnerability is a remote code execution issue in Microsoft SQL Server Reporting Services, allowing arbitrary code execution on the system.
Read Full Article
4 Likes
Schneier
50

FBI Shuts Down Chinese Botnet
- The FBI has shut down a botnet run by Chinese hackers.
- The botnet infected various types of internet-connected devices, including routers, cameras, and NAS drives.
- It targeted sensitive networks of universities, government agencies, telecom providers, and media organizations.
- The FBI, NSA, and Cyber National Mission Force coordinated the operation successfully.
Read Full Article
3 Likes
Qualys
22

Image Credit: Qualys
Black Basta Ransomware: What You Need to Know
- Black Basta is a ransomware group that demands payment for the decryption and non-release of stolen data, first spotted in April 2022.
- To date, 500+ organizations in North America, Europe, and Australia have been impacted by Black Basta affiliates gaining initial access through common methods like phishing, Qakbot, Cobalt Strike, and exploitation of known vulnerabilities.
- Black Basta is noted for its use of double extortion techniques, where the group demands payment for the decryption and non-release of stolen data.
- Black Basta is also known to exploit various vulnerabilities for initial access, privilege escalation, and lateral movement.
- A list of known tools that the Black Basta group abuses includes malware, adversary emulation, and legitimated tools.
- Once inside, the bad actors move laterally within the network to identify critical systems and data before deploying ransomware.
- Black Basta has been associated with the FIN7 threat actor due to similarities in custom modules for evading Endpoint Detection and Response (EDR) systems.
- The Black Basta infection chain usually starts with a spear phishing email campaign that delivers a malicious link or attachment to the victim.
- Black Basta uses the ChaCha20 algorithm to encrypt files and the ransomware binary uses vssadmin.exe to delete the shadow copy files to prevent system recovery.
- Qualys Endpoint Detection and Response (EDR) customers use hunting queries to detect suspicious activities associated with Black Basta Ransomware.
Read Full Article
1 Like
Kaspersky
306

Image Credit: Kaspersky
Kaspersky Expertise Centers | Kaspersky official blog
- Kaspersky is divided into five “centers of expertise” – Global Research and Analysis Team (GReAT), Threat Research, AI Technology Research, Security Services, and ICS CERT – each with its own set of specialties.
- Global Research and Analysis Team (GReAT) is the most well-known team of cybersecurity researchers who specialize in studying cyber espionage campaigns, APT attacks, and trends in international cybercrime. They also analyze cyber-incidents related to APT attacks and monitor the activity of over 200 APT groups, publishing exclusive Kaspersky APT & Crimeware Intelligence reports to help clients combat advanced threats.
- Threat Research includes Anti-Malware Research and Content Filtering Research. They analyze new cyberthreats to ensure that Kaspersky's products effectively identify and block them. They're responsible for secure software development life cycle (SSDLC) process, bug bounty program, and development of KasperskyOS.
- Kaspersky AI Technology Research applies data science and machine learning to detect various cyberthreats like malware, phishing and spam, on a large scale –contributing to detecting over 400k malicious objects daily. They use AI-powered automation to aid in alert triage and prioritization for their detection and response solutions.
- Kaspersky Security Services provide complimentary risk assessment, consulting services, cyber-event response, and response and impact minimization. Their Managed Detection and Response service is top-rated by customers.
- Kaspersky ICS CERT global project aims to assist manufacturers, owners and operators, and research teams in ensuring the cybersecurity of industrial automation systems and other M2M solutions. The CERT team constantly analyzes various products and technologies, evaluates their security levels and contributes to the engineering of sectoral and governmental regulations in the field of industrial cybersecurity.
- Kaspersky experts research cyberthreats relevant to even the most remote corners of the globe, constantly improving their services and solutions to identify the latest cyberthreats and counter the non-trivial attacks.
Read Full Article
18 Likes
Silicon
320
Image Credit: Silicon
AI Excites But Stresses CIOs, IDC Expereo Finds
- New research from IDC and Expereo reveals the impact and pressures CIOs are facing in managing AI ambitions of corporate businesses.
- 64% of global technology leaders find it challenging and stressful to meet technology demands.
- AI boosts personal reputation of CIOs but also creates unrealistic demands and increased job stress.
- Tech executives are excited about technology innovation, with 68% saying it's the most exciting time to be a technology leader.
Read Full Article
19 Likes
For uninterrupted reading, download the app