Info. Security News News
Kaspersky
381

Image Credit: Kaspersky
How to solve the cybersecurity talent shortage | Kaspersky official blog
- The coronavirus pandemic led to demand for cybersecurity professionals growing faster than the supply.
- ISC2 reported a global staffing shortage in cybersecurity industry stands at four million employees.
- A study of over a thousand cybersecurity professionals from 29 countries showed not all experts in cybersecurity studied the field at university.
- The availability of specialized cybersecurity courses in colleges and universities was rated as poor, and responses to whether higher education is necessary for a cybersecurity career were mixed as well.
- The problem with formal cybersecurity education is that it often lags behind real-world developments.
- Surveyed cybersecurity specialists note that higher education often does not provide sufficient hands-on training or help develop skills for a career in the field, leaving young professionals unprepared for the job.
- The lack of hands-on experience means many aspiring professionals can make poor decisions that can have serious consequences for employers.
- To mitigate the shortage, companies can give entry-level employees opportunities to fill gaps in their theoretical and practical knowledge, especially as technology and threats evolve quickly.
- Lastly, companies can invest in trainings and IT services to help mitigate the burden on their infosec department.
- Managed Detection and Response and Incident Response are third-party services companies can seek help from.
Read Full Article
22 Likes
Securityaffairs
90

Image Credit: Securityaffairs
Cyber vandalism on Wi-Fi networks at UK train stations spread an anti-Islam message
- UK police are investigating a cyberattack that disrupted Wi-Fi networks at several train stations across the country.
- Passengers attempting to log onto the Wi-Fi were exposed to an anti-Islam message.
- The Wi-Fi service has been suspended as a precaution, and no passenger data was compromised.
- The incident is being investigated by British Transport Police.
Read Full Article
5 Likes
TroyHunt
263

Image Credit: TroyHunt
The Data Breach Disclosure Conundrum
- The legal necessity for data breach disclosure depends on the country or region but often refers to the responsibility to report to the regulator rather than individuals.
- Organisations are not always obligated to notify individuals whose personal information they have exposed, which can lead to organisations never knowing about a breach.
- The difficulty lies in deciding to disclose the incident to impacted individuals, and the organisations will face the potential backlash of not disclosing the breach.
- The conundrum forces breached organizations to decide whether to either disclose to impacted individuals or never them know.
- Non-disclosure is intended to protect the brand and the shareholders, not the customers.
- Public disclosure allows the breached organisation to set the narrative and address any inaccuracies or misunderstandings.
- All data breaches have a turning point where the truth comes out and organisations are judged not for being breached but how they handled the breach.
- It is crucial to notify victims of data breaches, and failure to do so often results in a negative public reaction.
- The expectation for data breach disclosure is undoubtedly a priority for impacted individuals and governments.
- Disclosing promptly and showing respect for impacted customers is the proper approach to data breach problems.
Read Full Article
15 Likes
Hackingblogs
140
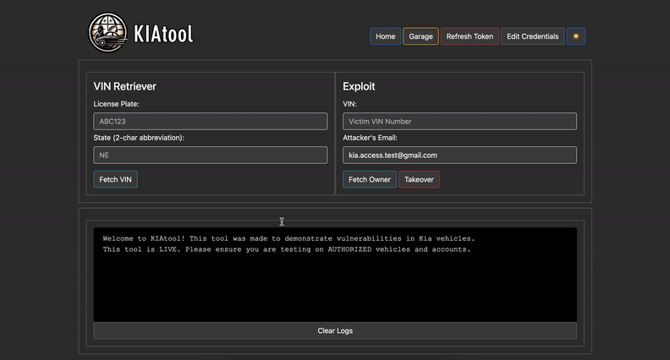
Image Credit: Hackingblogs
Million of Kia Cars Could Be Hacked Just Using There License Plate : Indepth Analysis
- Critical vulnerabilities in Kia's dealer site were found, allowing hackers to find and steal millions of Kia vehicles by using the license plate.
- Sensitive personal information of vehicle owners was also exposed through these vulnerabilities.
- The vulnerabilities have been patched by Kia after being identified by security researchers.
- The researchers created a tool to demonstrate the impact, showing that an attacker could remotely control a Kia vehicle by entering its license plate.
Read Full Article
8 Likes
TechCrunch
340

Image Credit: TechCrunch
Iranian hackers charged with hacking Trump campaign to ‘stoke discord’
- The U.S. Department of Justice has charged three Iranian hackers from the Islamic Revolutionary Guard Corps (IRGC) with a four-year-long hacking campaign.
- The hackers targeted the Trump campaign, former White House officials, members of Congress, and engaged in a hack-and-leak operation.
- The operation was reportedly launched in retaliation for the killing of Iranian General Qasem Soleimani and aimed to influence the upcoming 2024 presidential election.
- The indictment stated that phishing lures were used to compromise online accounts and steal campaign material for potential leaks to the media.
Read Full Article
20 Likes
Qualys
172

Image Credit: Qualys
Qualys Ranked as a “Strong Performer” Among Top Vendors in Forrester Wave™ for Attack Surface Management
- Qualys CyberSecurity Asset Management is ranked as a strong performer among top vendors in the market of Attack Surface Management.
- Forrester published their review of the Attack Surface Management vendor market, where Qualys appears as a Strong Performer and tied for the third-highest ranking in the current offering category.
- Qualys focuses on unified attack surface inventory and cyber risk assessment as the foundation for a security program.
- Qualys continues to invest in attack surface management coverage, risk-based vulnerability management, and actionable cyber risk quantification.
Read Full Article
10 Likes
Cybersecurity-Insiders
49

Image Credit: Cybersecurity-Insiders
Growing data security concerns Over Facebook and Instagram Scam
- A scam circulating on Facebook and Instagram has raised data security concerns.
- The scam suggests that users can prevent Facebook and Instagram from using their personal information by reposting a message.
- Meta, the parent company, has disavowed the claim, stating it doesn't require user-driven promotions for its AI development.
- Meta was fined €91 million by the Data Protection Commission of Ireland for improper storage of user data in plaintext.
Read Full Article
3 Likes
Infoblox
190

Image Credit: Infoblox
Introducing Our Revolutionary DDI Services for the Hybrid, Multi-Cloud Era
- Companies that leverage a hybrid, multi-cloud infrastructure can access the newest technologies and be more agile.
- 91%* of organizations use two or more public cloud providers in an effort to lower costs, realize faster innovation, and achieve greater scalability.
- However, organizations are struggling to manage critical network services like DNS, DHCP, and IP address management (DDI).
- There are five common scenarios associated with the challenges of managing multiple DNS systems, leading to human mistakes and outages.
- To address these challenges, Infoblox has launched a new product suite, the Infoblox Universal DDI Product Suite- revolutionary solutions that unify critical network services management across hybrid, multi-cloud environments, providing in-depth visibility and insights with infrastructure-free deployment.
- The Infoblox Universal DDI Product Suite offers three products: Infoblox Universal DDI Management, Infoblox Universal Asset Insights offers an unrivaled breadth of discovery sources, and NIOS-X as a Service.
- The services empower enterprises to navigate the multi-cloud maze confidently, ensuring seamless operations and robust protection in an ever-evolving digital landscape.
- The product suite has created significant improvements for companies dealing with high latency and maintenance issues, operational inefficiencies, and outage risks in their hybrid multi-cloud setup.
- With the introduction of Infoblox Universal DDI Management, Infoblox Universal Asset Insights and NIOS-X as a Service, Infoblox is transforming operational hurdles into efficiency, security, and growth opportunities.
- Infoblox Universal DDI Product Suite offers powerful tools, enhancing collaboration, speeding up application deployment, and dramatically simplifying operations.
Read Full Article
11 Likes
Securityaffairs
436

Image Credit: Securityaffairs
CUPS flaws allow remote code execution on Linux systems under certain conditions
- An unpatched vulnerability affecting Linux systems has been disclosed by security researcher Simone Margaritelli. Margaritelli announced plans to disclose an unauthenticated remote code execution (RCE) vulnerability affecting all GNU/Linux systems within two weeks. The issue received a critical rating and a CVSS score of 9.9. However, no CVE had been assigned and no one was working to resolve it.
- The vulnerability chain involves four vulnerabilities, including IPP attribute sanitisation, command execution, and packet trust issues. By exploiting these vulnerabilities together, a remote unauthenticated attacker can execute arbitrary code, leading to the theft of sensitive data and damage to critical production systems.
- To execute the attack, the attacker needs to gain access to a vulnerable server through unrestricted public internet access or gaining access to an internal network where local connections are trusted. The attacker then attempts to print from the compromised device to execute arbitrary code on the victim's machine.
- The vulnerabilities are yet to be addressed by CUPS developers, who have reportedly admitted that the vulnerabilities cannot be easily fixed. The CUPS security team suggests some temporary mitigation measures which include running two commands to disable vulnerable services or blocking all traffic to UDP port 631 and DNS-SD traffic.
- Red Hat cautioned that a chain of these vulnerabilities could lead to remote code execution, resulting in data theft or damage to critical production systems. The issues were rated as having Important severity impact. While all versions of RHEL are affected, it is important to note that affected packages are not vulnerable in their default configuration.
- The technical details and a PoC exploit of this vulnerability were disclosed by Margaritelli on September 26th, 2024. The disclosure followed a poor response to responsible disclosure according to the researcher.
- For temporary mitigation, users can prevent vulnerable systems from starting up by running two commands, stopping a vulnerable service, and disabling cups-browsed.
- Margaritelli spent three weeks of his sabbatical working full-time on this research, reporting and coordinating this disclosure to help resolve the issue.
- The vulnerabilities may allow an unauthenticated remote attacker to achieve arbitrary code execution by replacing IPP URLs with a malicious one.
- Blocking DNS-SD traffic and all UDP traffic to port 631 can potentially mitigate the attacks.
Read Full Article
26 Likes
Hackersking
345

Image Credit: Hackersking
Automate Entire Process Of Reconnaissance with ReconFTW
- Reconnaissance, or recon, is the first step in any successful hacking or penetration testing.
- With the help of ReconFTW, a robust open-source tool, you can automate the entire recon process, saving hours of manual work while increasing accuracy.
- ReconFTW is built to handle tasks that would typically require multiple recon tools.
- ReconFTW comes with popular tools like Amass, Nmap, Subfinder, and others, automating subdomain enumeration, port scanning, vulnerability detection, and more.
- The installation process of ReconFTW includes cloning the tool from GitHub, installing dependencies, and configuring API keys.
- With ReconFTW, you can automate subdomain enumeration, port scanning, vulnerability detection, and more.
- Results are stored in a structured format in the /results directory, and include subdomain lists, port details, and vulnerability reports.
- ReconFTW is known for its full automation, comprehensive tool integration, API key support, and easy setup.
- Issues that may come up include missing API keys, dependency errors, and performance issues.
- Practical tips for maximizing ReconFTW include using a powerful system, automating API key usage, running in phases, and saving results.
Read Full Article
20 Likes
Sentinelone
390

Image Credit: Sentinelone
The Good, the Bad and the Ugly in Cybersecurity – Week 39
- The US government has indicted a Russian money launderer and imposed sanctions on two illegal virtual currency exchanges that have links to ransomware operations and other threat actors, including brokers and darknet vendors.
- PM2BTC, one of the exchanges, has long-standing ties with Russia and Russian-affiliated financial institutions many of which are also sanctioned, and provides convertible virtual currency-to-ruble exchange services with no anti-money laundering or KYC programmes in place.
- Cryptex, the second exchange, was found to have processed $51.2m in ransomware-derived funds and handled over $720m in suspicious transactions tied to Russian cybercriminals.
- The Department of State has issued a $10m reward for information leading to the arrest of Sergey Sergeevich Ivanov, who has allegedly facilitated hundreds of millions in virtual transactions using various payment processors to do business with malicious parties.
- Mallox ransomware affiliate TargetCompany has now turned to a version of Kryptina ransomware to target Linux machines, showing the ever-evolving tactics within the ransomware ecosystem.
- Initially launched as a low-cost ransomware-as-a-service platform for Linux, in February 2024, the platform’s alleged administrator leaked its source code for free, leading to various ransomware actors to repurpose Kryptina’s code.
- The new version, dubbed Mallox Linux 1.0, retains Kryptina’s core source code, encryption mechanisms and command line functions. Experts warn that ransomware groups will continue to cross-pollinate toolsets and codebases in order to advance.
- North Korean-tied threat group Kimsuky has developed two new malware strains, KLogEXE and FPSpy, both of which are being delivered through targeted spear-phishing emails designed to look like legitimate communications.
- KLogEXE is a variant of a previously documented PowerShell-based keylogger, while FPSpy can enumerate files, drives and folders and execute further payloads; researchers have noted similarities in the source code of both strains, leading to the idea of a common author.
- While Kimsuky attacks remain extremely targeted and focused on specific industries and regions, its use of both KLogEXE and FPSpy illustrates the group's ongoing effort to enhance its malware arsenal and expand its operational reach.
Read Full Article
23 Likes
Securityintelligence
118

Image Credit: Securityintelligence
Access control is going mobile — Is this the way forward?
- Last year, cyberattacks using valid credentials increased by 71% from 2022.
- Organizations are turning to mobile credentialing to prevent unauthorized access.
- Mobile credentialing reduces the risk of stolen credentials and offers cost and administration savings.
- Challenges include personal device requirements and the need for operational devices.
Read Full Article
7 Likes
Schneier
90

NIST Recommends Some Common-Sense Password Rules
- NIST's second draft of its “SP 800-63-4“—its digital identify guidelines—contains rules about passwords.
- Passwords should be a minimum of eight characters in length and preferably 15 characters.
- Passwords can be up to 64 characters long and can include ASCII and Unicode characters.
- There should be no other composition rules for passwords, and periodic password changes are not required.
Read Full Article
5 Likes
Securityaffairs
281

Image Credit: Securityaffairs
U.S. sanctioned virtual currency exchanges Cryptex and PM2BTC for facilitating illegal activities
- The U.S. government sanctioned the virtual currency exchanges Cryptex and PM2BTC for facilitating cybercrime and money laundering.
- Russian national Sergey Ivanov has been charged with conspiracy to commit bank fraud and money laundering for operating multiple money laundering services catering to cybercriminals.
- Blockchain analysis revealed that Ivanov's services handled around $1.15 billion in transactions, with 32% of the traced bitcoin linked to criminal activity.
- The U.S. Secret Service seized the domains associated with the UAPS and PM2BTC websites, and the U.S. Department of State announced a reward of up to $10 million for information on Sergey Ivanov.
Read Full Article
16 Likes
Qualys
299

Image Credit: Qualys
Critical Unauthenticated RCE Flaws in CUPS Printing Systems
- A new set of critical unauthenticated Remote Code Execution (RCE) vulnerabilities were revealed in CUPS.
- These vulnerabilities can allow a remote attacker to execute arbitrary code on a target system without valid credentials or prior access.
- Major organizations like Canonical and Red Hat have confirmed this flaw, assigning it a high severity with a CVSS score of 9.9 out of 10.
- More than 75k publicly exposed assets are affected by the flaws, and a huge majority of these assets were found on the default IPP port 631. Of these, more than 42k publicly exposed assets accept unauthenticated connections.
- CUPS is the standard printing system for many Unix-like operating systems, such as GNU/Linux distributions and macOS. CVE vulnerabilities have affected several CUPS versions.
- These vulnerabilities involve multiple components of the CUPS printing system, allowing an unauthenticated attacker to replace existing printers URLs with malicious ones silently.
- The vulnerabilities exploit by directing a malicious UDP packet to port 631 on the target system, leading to remote code execution.
- Enterprises are advised to assess the exposure risk of CUPS systems. They should limit network access, deactivate non-essential services and implement strict access controls.
- The Qualys Threat Research Unit is releasing QIDs to detect these vulnerabilities.
- Organizations can inventory their infrastructure using the QID 38199: CUPS service Detected to mitigate these risks.
Read Full Article
18 Likes
For uninterrupted reading, download the app