Info. Security News News
Hackingarticles
136

Image Credit: Hackingarticles
OSINT : User Privacy in Linux
- Linux telemetry involves gathering and sending data from a Linux-based system to an external server or service.
- To make secure the Ubuntu OS, it is recommended to use POP!_OS designed by System76.
- To enhance security, some packages should be removed or disabled, e.g., apport, apport-symptoms, ubuntu-report and more.
- Various settings need to be changed such as diagnostics reporting, lock screen notifications, tracking of recent files and more.
- Tools can be used to make the system more secure like BleachBit for system cleaning, KeePassXC for password management, ClamAV for anti-virus and more.
- The user can remove metadata by using MAT2 and browse securely using Tor Browser and VPN and even block websites using NextDNS.
- The article concludes that using these methods and tools, user privacy can be safeguarded while significantly reducing the exposure to unwanted data collection.
Read Full Article
8 Likes
Kaspersky
300

Image Credit: Kaspersky
Is technology increasing potential threats in relationships? | Kaspersky official blog
- The rise of online dating makes it easier for manipulation and people tend to share personal details or intimate images before knowing the person they are sharing with. 39% of people aged 25-34 shared intimate images with someone they’ve never met in real life. There are three main threats online daters should be careful of while dating: intimate image abuse, or “revenge porn”, stalkerware, and deepfakes.
- Intimate image abuse is a harmful form of digital abuse. As so many people share personal images, nearly half of the Naked Truth survey respondents reported experiencing or knowing someone who’d been affected by intimate image abuse. How to protect yourself? Think twice before sharing, stay informed, and manage your passwords wisely.
- Stalkerware is software that secretly tracks a person’s location, messages, and daily activities. In 2023, over 31,000 cases of stalkerware were identified globally. To protect yourself, be vigilant, avoid tampering with stalkerware and update your privacy settings.
- Deepfake technology is used to create hyper-realistic fake images, videos, and audio recordings. In romantic contexts, deepfakes can be used to create fake compromising imagery. To protect yourself, know the warning signs, report deepfakes, and stay informed.
- Education is key to reducing online dating risks. Consent in the digital world must be ongoing. Many men believe receiving an intimate image means they own it, highlighting a serious issue around digital privacy. By understanding these risks and taking steps to protect ourselves, we can help protect our devices from threats like stalkerware and other malware.
- Kaspersky Premium is a comprehensive security solution that can help protect devices from threats like stalkerware and other malware. For more details, read the report and safe dating guide.
Read Full Article
18 Likes
Amazon
68

Image Credit: Amazon
How AWS WAF threat intelligence features help protect the player experience for betting and gaming customers
- The betting and gaming industry is a rich data landscape and draws the attention of sophisticated bots.
- Aggressive web scraping, account creation and takeovers, and denial-of-service tactics are common automated threats.
- AWS WAF offers intelligent threat mitigation features to protect customers against automated threats.
- The AWS WAF Common Bot Control managed rule group is designed to block known bot behavior.
- CAPTCHA and challenge rule actions in AWS WAF require users to solve puzzles to prove they are human.
- AWS WAF provides various types of client application integration for intelligent threat mitigation.
- AWS WAF Targeted Bot Control expands on Common Bot Control by adding targeted detection for sophisticated bots.
- AWS WAF Fraud Control features help prevent fraudulent account creation and account takeover.
- A layered approach to managing bots is essential with differentiated tooling to specific bot tactics.
- GS WAF, AWS WAF Bot Control, and AWS Shield are recommended tools to mitigate bot threats to gaming platforms.
Read Full Article
4 Likes
Qualys
350

Image Credit: Qualys
Enhancing Cloud-Native Security: Qualys Introduces Scanning for Container-Optimized OS in Google Kubernetes Engine
- Qualys has introduced a tool to scan Google cloud’s Container-Optimized OS instances directly, using the Qualys Cloud Agent, to enhance cloud-native security by offering comprehensive visibility into both the host OS and container.
- Containers bring added complexity and require a fresh approach to security, as vulnerabilities can quickly spread across systems and visibility into containerized applications is often limited.
- Securing containerized applications on Containers-Optimized OS poses challenges and lack of asset visibility, actionable intelligence and the need among other industries with stringent regulatory requirements for security auditing.
- Qualys addresses these challenges through host scanning Qualys Cloud Agent, Qualys TotalCloud CSPM and Qualys Container Security.
- With a comprehensive security solution, Qualys addresses these challenges by performing in-depth host scanning and Container Security scans container workloads in Google Cloud’s Container-Optimized OS, offering complete view of the cloud environment and empowering organizations to enforce security policies.
- Qualys targets Container-Optimized OS instances, ensuring vulnerabilities are swiftly detected and addressed and synchronized with instances running in GKE.
- Google Container-Optimized OS is open-source and designed to offer an immutable operating system with an emphasis on heightened security and scalability.
- Qualys Cloud Agent for Container-Optimized OS is containerized, lightweight and provides comprehensive host scanning to identify and remediate vulnerabilities effectively.
- Qualys TotalCloud CSPM offers a holistic view of cloud infrastructure with automated policy enforcement while Qualys Container Security offers comprehensive vulnerability management, malware detection, and actionable insights for threat mitigation.
- Qualys is the first and only solution capable of scanning Container-Optimized OS with the Qualys Cloud Agent.
Read Full Article
21 Likes
Securityaffairs
314

Image Credit: Securityaffairs
A cyberattack on MoneyGram caused its service outage
- American peer-to-peer payments and money transfer company MoneyGram confirmed that a cyberattack caused its service outage.
- The company informed customers of a network outage impacting connectivity to several systems.
- MoneyGram has taken systems offline to contain the attack, suggesting a ransomware incident.
- The company is working to restore systems and resume normal operation.
Read Full Article
18 Likes
Hackersking
232
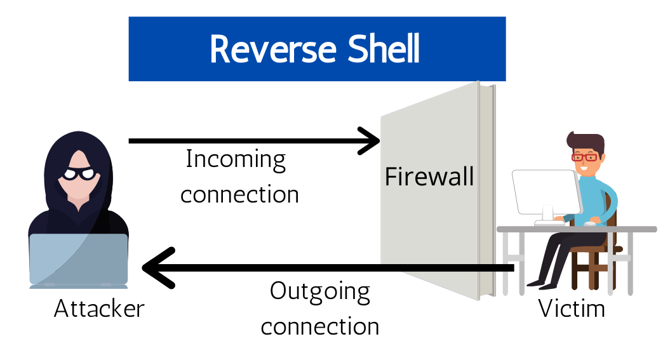
Image Credit: Hackersking
Setting Up a Reverse Shell with Netcat | Quick Guide
- Netcat, also known as the "Swiss Army knife" of networking, is a powerful command-line tool for data communication over networks.
- A reverse shell is a technique used in penetration testing to bypass firewalls or network restrictions by establishing a connection from the target machine to the attacker's machine.
- Various methods can be used with Netcat to set up a reverse shell, including Netcat simple shell, Netcat with mkfifo, Python, MSFvenom (Metasploit), PowerShell, and Ruby.
- Netcat can also be used for file transfer, UDP mode for sending and receiving UDP packets, port forwarding, and port redirection.
Read Full Article
13 Likes
Amazon
9

Image Credit: Amazon
Six tips to improve the security of your AWS Transfer Family server
- AWS Transfer Family is a secure transfer service that lets you transfer files directly into and out of Amazon Web Services (AWS) storage services using popular protocols
- There are multiple security configuration options that you can activate to fit your needs and provide instructions for each one
- Newly created Transfer Family servers use the strongest security policy to reduce risks of known vulnerabilities such as CVE-2023-48795
- Use slashes in session policies to limit access and set session policies on S3 bucket prefixes to avoid granting access to unwanted buckets
- Creating a session policy for an S3 bucket with appropriate access using IAM managed policies provides extra protection against accidental changes to logical directory mappings
- Avoid using Network Load Balancers (NLBs) in front of your Transfer Family server to maintain auditability, better performance, and fewer restrictions
- Protect your API Gateway instance with AWS Web Application Firewall (WAF) to create access control lists (ACLs) for only AWS and anyone in the ACL for your API Gateway instance
- FTPS customers should use TLS session resumption to help protect client connections as they hand off between the FTPS control port and the data port. Transfer Family endpoints provide options for session resumption
- Transfer Family offers many benefits to help secure your managed file transfer (MFT) solution as the threat landscape evolves.
Read Full Article
Like
Securityintelligence
159

Image Credit: Securityintelligence
SANS Institute: Top 5 dangerous cyberattack techniques in 2024
- SANS Institute's annual report identifies the most dangerous cyberattack techniques of 2024.
- During the RSA conference keynote, five new cyberattack techniques were discussed.
- AI-powered child sextortion is among the new attack techniques and requires careful education and awareness.
- Use of generative AI can negatively impact public trust in political campaigns, thereby requiring increased security protocols.
- Offensive cyber operations can also be automated with AI, leading to quicker exploitation of vulnerabilities.
- Technical debt is becoming increasingly critical in enterprise cybersecurity, posing challenges to the security infrastructure.
- The decreasing cost of creating deepfakes is complicating identity verification, requiring a risk-based approach.
- Collaboration between tech companies, political parties, academia, and grassroots organizations is important for ensuring accountability.
- Leveraging automation and intelligence on the defensive side is recommended to combat offensive cyber operations
- Organizations need to assess the likelihood of cyber breaches and invest in appropriate identity verification measures.
Read Full Article
9 Likes
Securityaffairs
328
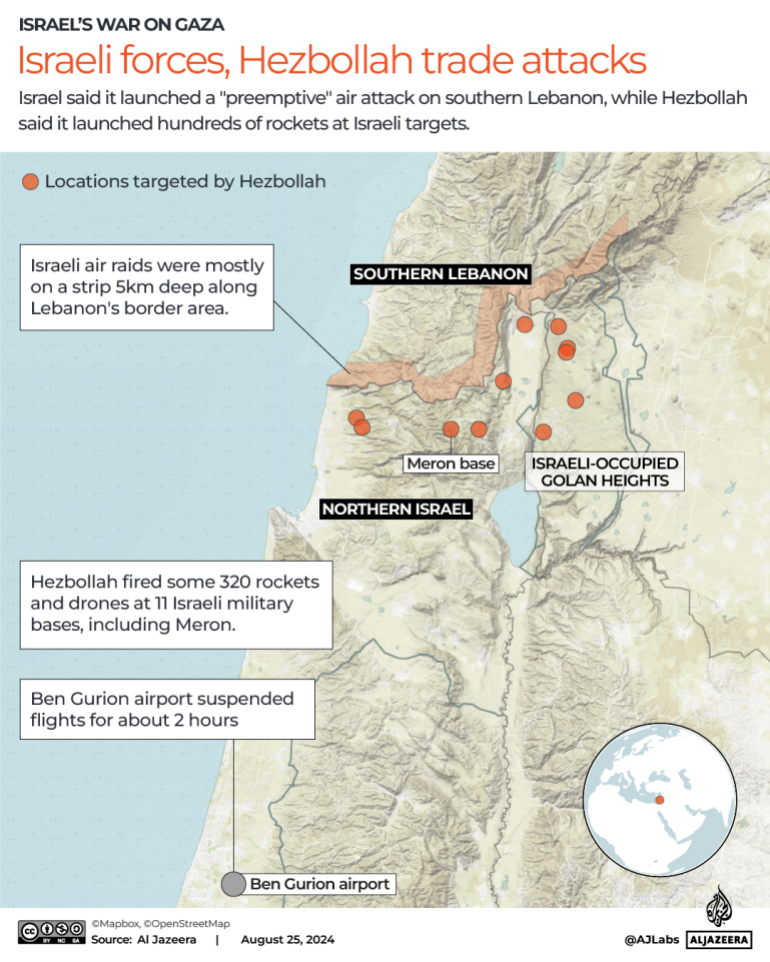
Image Credit: Securityaffairs
Did Israel infiltrate Lebanese telecoms networks?
- Israel has been sending text messages, recordings, and hacking radio networks to warn Lebanese citizens to evacuate certain areas.
- Israeli intelligence has been gathering data on Lebanon's citizens for years and may have infiltrated Lebanese telecom networks.
- Residents in southern Lebanon and parts of Beirut received messages and phone calls urging them to stay away from areas hosting Hezbollah.
- The warnings have sparked concerns about escalating conflict in the region.
Read Full Article
19 Likes
Socprime
245

Image Credit: Socprime
Vendor-Agnostic Cybersecurity: Adapting to the Future of Threat Detection
- Organizations need the agility to adapt, migrate, and use multiple security solutions without being tied down by proprietary formats for managing their security operations in today's fast-moving technological landscape.
- Adopting cross-platform and supplier-independent threat detection frameworks such as Sigma and Roota rules and Uncoder AI becomes crucial for organizations to address the challenges related to platform-specific tools for threat detection and response.
- Vendor lock-in can lead to lack of flexibility for organizations in adapting to changing security needs, technological obsolescence, and rising costs, and hence vendor-agnostic approach for threat detection becomes important.
- SIEM vendors have shifted towards subscription-based services, cloud-only models, various segmented offerings, and mergers, and hence a vendor-neutral approach is needed for organizations.
- Sigma and Roota rules and Uncoder AI make detection logic portable and free from being locked into a security provider's product or format, allowing organizations to switch between vendors and technologies without disruptions.
- Decoupling detection logic from a specific security solution allows security teams to focus on actual threat detection and mitigation. Using tools like Uncoder AI enables better knowledge sharing, rapid response time, fosters better collaboration across teams in security operations.
- By adopting a vendor-agnostic approach, organizations can break free from the constraints of vendor lock-in, reduce operational costs, and future-proof their theta detection capabilities.
- Modern cybersecurity requires flexibility, scalability, and the ability to operate across multiple platforms, and hence organizations need to embrace tools that allow them to be nimble, efficient, and ready for whatever comes next.
Read Full Article
14 Likes
Hackingblogs
814

Image Credit: Hackingblogs
The latest Necro Trojan variant may have infected millions of Android device owners
- The Necro Trojan variant has infected millions of Android device owners.
- Necro is an Android downloader that infects unofficial sources and well-known programs on the Google Play store.
- Malicious code was found in the CamScanner mobile app, affecting over 100 million Android users.
- Trojan-Dropper.AndroidOS.Necro.n, the harmful component, downloads and executes a payload from malicious servers.
Read Full Article
16 Likes
Cybersecurity-Insiders
296

Image Credit: Cybersecurity-Insiders
Addressing Data Security Concerns in Cloud Migrations
- Data security remains a paramount concern during cloud migrations.
- Key risks include data breaches, compliance violations, data loss, and vendor lock-in.
- Best practices for ensuring data security include thorough risk assessment, choosing a secure cloud provider, implementing strong encryption and access management, having backup and disaster recovery plans, monitoring and auditing, employee training, and developing a clear migration strategy.
- Organizations can leverage the benefits of cloud technology while maintaining data security and compliance.
Read Full Article
17 Likes
TechCrunch
86

Image Credit: TechCrunch
Some Kaspersky customers receive surprise forced-update to new antivirus software
- Customers of Kaspersky antivirus in the United States received an automatic update to a new software called UltraAV without prior knowledge or consent.
- Some customers expressed frustration at the forced replacement of their cybersecurity software.
- The transition to UltraAV comes after the US government banned sales of Kaspersky software.
- Kaspersky confirmed the transition and stated it partnered with UltraAV to ensure a seamless transition.
Read Full Article
5 Likes
Tech Story
442

High Severity Warning Issued for iOS, iPadOS, and macOS Users: Update Your Devices Now
- Government cybersecurity agencies have issued a high-severity warning for iOS, iPadOS, and macOS users.
- Serious vulnerabilities allow hackers to access devices and steal data.
- Users must update their devices to the latest software versions to mitigate risks.
- Importance of transparency, collaboration, and proactive security measures.
Read Full Article
26 Likes
Sentinelone
378

Image Credit: Sentinelone
PinnacleOne ExecBrief | State and Local Election Security Advisory
- The PinnacleOne ExecBrief assessed the 2024 election security threat landscape and offered free SentinelOne assistance to state and local governments until the election. U.S. elections are exposed to both cybersecurity and physical threats, with highly capable nation-state threat actors, cybercriminal groups, and motivated hacktivist groups looking to influence, disrupt, or undermine them. Russia poses the most significant threat and is focused on sowing divisive narratives. China is cautious and focuses on data collection and public opinion monitoring, while Iran looks to exploit U.S. societal tensions.
- Foreign malign influence operations, orchestrated by foreign governments including Russia, China, and Iran, exploit sociopolitical divisions to undermine confidence in democratic institutions and sway public opinion. Threat actor tactics include: disguising proxy media, using AI to fabricate recordings of public figures, hacking organisations to steal and leak sensitive information as part of influence campaigns, spreading fake reports or documents, foreign actors secretly paying influencers or media firms, and using platforms with weak content moderation to spread divisive narratives.
- CISA provides a thorough guide for election officials to safeguard election infrastructure from common cybersecurity threats like phishing, ransomware, and DDoS attacks. This checklist helps assess the current cybersecurity posture and outlines proactive measures to enhance resilience. CISA, the FBI, and state agencies should collaborate to leverage tools like cyber hygiene scanning, vulnerability assessments and threat monitoring.
- Robust email filtering, phishing detection, and MFA for all official accounts should be implemented. All election staff should be trained to recognise and respond to potential cyber threats, such as phishing or disinformation campaigns. Physical security measures should be enhanced, and emergency response plans should be prepared, including the handling of potential violence or sabotage attempts.
- SentinelOne, with its world-leading Security AI platform, strategic advisory services, and team of experts, is ready to assist state and local governments in enhancing their security posture, conducting thorough program assessments, and providing real-time threat monitoring to safeguard election infrastructure.
- SentinelOne offers free Managed Services which seamlessly integrate Vigilance MDR, WatchTower Threat Hunting, and Purple AI, the industry’s most advanced AI security analyst into the organization's existing environment. It can help detect, respond to and mitigate both known and emerging threats.
- In conclusion, election officials, state and local security teams, technology providers, federal agencies, and cybersecurity firms should take timely action to strengthen their defense and collaborative efforts to identify and mitigate potential risks before they impact election operations.
- State and local governments seeking extra assistance can visit the website: https://www.sentinelone.com/lp/securing-governments/.
Read Full Article
22 Likes
For uninterrupted reading, download the app