Info. Security News News
Socprime
164

Image Credit: Socprime
Earth Baxia Attack Detection: China-Backed Hackers Use Spear-Phishing, Exploit the GeoServer Vulnerability (CVE-2024-36401), and Apply a New EAGLEDOOR Malware to Target APAC
- China-backed Earth Baxia APT group have targeted a state agency in Taiwan and potentially other countries in the APAC region.
- APT groups from regions such as China, North Korea, Iran, and Russia demonstrated notably sophisticated and innovative adversary methods.
- Adversaries relied on spear-phishing, exploited a newly patched critical RCE vulnerability in OSGeo GeoServer GeoTools tracked as CVE-2024-36401, and leveraged a novel custom backdoor dubbed EAGLEDOOR.
- State-sponsored Chinese hackers are emerging in the forefront of nation-backed cyber threats.
- To detect Earth Baxia Attacks, security engineers might rely on SOC Prime Platform for collective cyber defense.
- China-backed Earth Baxia APT increasingly targets Taiwan and countries in the APAC region using GeoServer flaw (CVE-2024-36401) and EAGLEDOOR malware.
- Researchers suggest that government agencies, telecommunications firms, and energy industries in the Philippines, South Korea, Vietnam, Taiwan, and Thailand are likely the main targets.
- The compromise ultimately results in the deployment of either a custom backdoor dubbed EAGLEDOOR or a rogue installation of the red-team tool Cobalt Strike.
- The group leverages public cloud services to host its malicious files and currently shows no clear ties to other known APT groups.
- By leveraging SOC Prime’s Attack Detective SaaS solution, organizations can gain from real-time data and content audits for comprehensive threat visibility and improved detection coverage.
Read Full Article
9 Likes
Securityaffairs
237
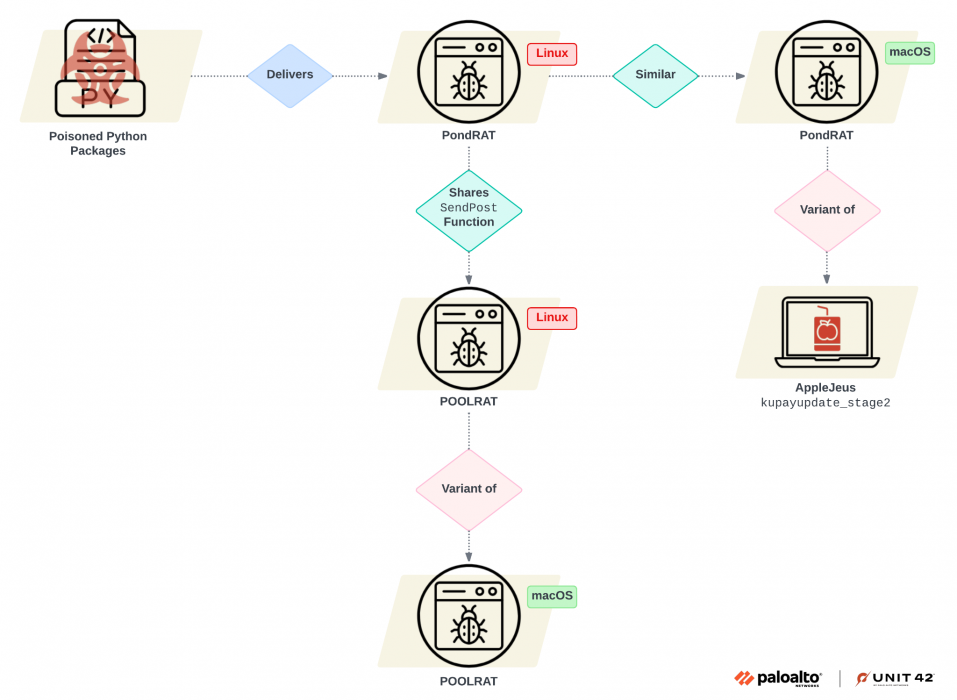
Image Credit: Securityaffairs
North Korea-linked APT Gleaming Pisces deliver new PondRAT backdoor via malicious Python packages
- North Korea-linked APT group Gleaming Pisces is distributing a new malware called PondRAT through tainted Python packages.
- The campaign aims to compromise developers' systems and supply chain vendors.
- PondRAT is closely related to the macOS remote access tool POOLRAT, previously distributed by Gleaming Pisces.
- The weaponization of legitimate-looking Python packages poses a significant risk to organizations.
Read Full Article
14 Likes
Securityaffairs
360
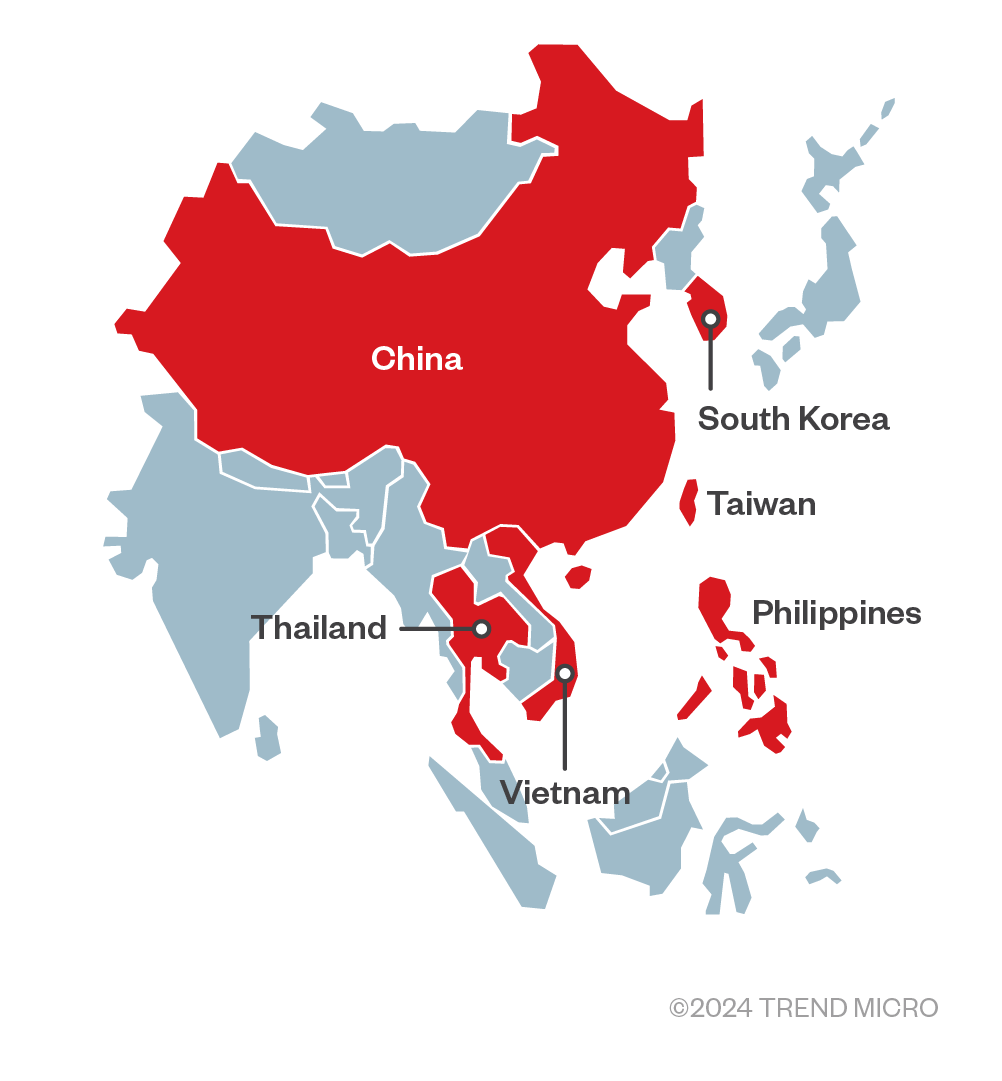
Image Credit: Securityaffairs
Chinese APT Earth Baxia target APAC by exploiting GeoServer flaw
- Suspected China-linked APT Earth Baxia targeted a government organization in Taiwan by exploiting a recently patched OSGeo GeoServer GeoTools flaw.
- Trend Micro researchers reported that China-linked APT group Earth Baxia has targeted a government organization in Taiwan and potentially other countries in the Asia-Pacific (APAC) region.
- The threat actor used spear-phishing emails and exploited the recently patched GeoServer vulnerability CVE-2024-36401.
- Earth Baxia primarily targeted government agencies, telecommunication businesses, and the energy industry in the Philippines, South Korea, Vietnam, Taiwan, and Thailand.
Read Full Article
21 Likes
Hackingblogs
364

Image Credit: Hackingblogs
US (FTC) Report: Major Social Media and Streaming Platforms Under Investigation for User Surveillance and Weak Privacy for Kids
- A recent investigation by the US Federal Trade Commission (FTC) reveals major social media and streaming platforms are under scrutiny for user surveillance and weak privacy protection for kids.
- The investigation focuses on how these platforms acquire and use user data for profit without prioritizing online safety, particularly for children and teenagers.
- The FTC sent orders to nine companies, including Twitch, TikTok, YouTube, Twitter, Snap Inc., Facebook, and WhatsApp, seeking information on data gathering, usage, tracking, advertising practices, and impact on minors.
- The report highlights concerns about the uncontrolled data handling processes and the potential dominance of businesses that collect extensive user data, impacting customer privacy and competition.
Read Full Article
21 Likes
Hackersking
191
Image Credit: Hackersking
Telnet (Telecommunication Network) For Penetration Testing | Quick Guide
- Telnet is a protocol that allows users to remotely access another device over a network. It is still a powerful tool for penetration testers and hackers. Telnet operates on port 23, allowing you to establish communication with the server and analyze the offered services. Telnet can help uncover vulnerabilities & test services like HTTP, FTP, SMTP, POP3, and more. Port scanning and version detection are vital to understanding a network or service. Banner grabbing can be performed to get a banner that contains valuable information. Knowing the OS running on a system can provide crucial information for selecting the right attack methods.
- Through Telnet, ethical hackers can identify vulnerabilities, gather information, and launch attacks on networks, making it a valuable skill for penetration testing. Banner grabbing is one of the most common uses of Telnet in Pentesting that can provide details such as server type, operating system, service information, and other related metadata. Telnet still serves as a valuable tool for ethical hackers and penetration testers, irrespective of its age and security.
- Telnet is unencrypted, meaning it is not safe to use over public networks without tunneling the traffic through a more secure protocol like SSH. As a hacker or penetration tester, you should also be aware of the legal implications of its usage for testing and ensure that you have explicit permission from the system owner. Knowing the OS helps penetration testers and ethical hackers tailor their attacks on identified vulnerabilities and misconfigurations.
- Telnet's simplicity allows you to gather information about a network's infrastructure without any complex setups. In a network, it enables more efficient communication by establishing and maintaining an organized interaction. Learning how to use Telnet effectively is crucial to expanding your penetration testing skills.
- Port Version Detection with Telnet is the first step in understanding a network or service, and after identifying open ports, version detection is next critical. Banner grabbing, Port Version Detection, and OS Detection are some functionalities of Telnet that provide an array of options for gathering information and uncovering vulnerabilities. Ethical hacking helps secure systems and does not involve breaking into them without permission.
Read Full Article
11 Likes
Hackersking
447

Image Credit: Hackersking
Introduction to Linux for Blue Teaming
- This article provides an introduction to Linux commands that are helpful for blue teaming, including file system, basic command, permissions, user management, network management, system management, package management, and processes and scheduled tasks.
- As a SOC analyst, it is necessary to have a certain level of Linux knowledge since Linux is an open-source operating system used in many types of devices.
- The article explains the fundamentals of Linux, including the Linux file system hierarchy and basic terminal commands such as navigating directories, file operations, text editing, and searching files.
- Additionally, the article provides Linux commands for permissions management and user management and groups, which control access to system resources.
- The article also covers network management through configuring network interfaces for network troubleshooting, and package management and service management, which are essential for system maintenance.
- The article ends with managing processes and scheduled tasks, including automating tasks with scheduled jobs enhancing productivity.
- By learning the above commands for SOC analysts, these commands may be applied to detect and prevent attacks effectively and efficiently, saving valuable time.
- Learning Linux is crucial from a cybersecurity perspective as SOC analysts may encounter different operating systems as part of their job.
- This article provides comprehensive information on various Linux commands applicable to SOC analysts.
- Aspiring to gain hands-on hacking experience? Join the Complete Offensive-Hacking Course to become a certified hacker and receive a 10% special offer.
Read Full Article
26 Likes
Securityaffairs
9

Image Credit: Securityaffairs
Security Affairs newsletter Round 490 by Pierluigi Paganini – INTERNATIONAL EDITION
- Hackers stole over $44 million from Asian crypto platform BingXOP
- Europol dismantled phishing scheme targeting mobile users
- Ukraine bans Telegram for government agencies, military, and critical infrastructure
- Tor Project responded to claims that law enforcement can de-anonymize Tor users
- UNC1860 provides Iran-linked APTs with access to Middle Eastern networks
- US DoJ charged two men with stealing and laundering $230 Million worth of cryptocurrency
- The Vanilla Tempest cybercrime gang used INC ransomware for the first time in attacks on the healthcare sector
- U.S. CISA adds new Ivanti Cloud Services Appliance Vulnerability to its Known Exploited Vulnerabilities catalog
- Ivanti warns of a new actively exploited Cloud Services Appliance (CSA) flaw
- U.S. CISA adds Microsoft Windows, Apache HugeGraph-Server, Oracle JDeveloper, Oracle WebLogic Server, and Microsoft SQL Server bugs to its Known Exploited Vulnerabilities catalog
Read Full Article
Like
Securityaffairs
287

Image Credit: Securityaffairs
Noise Storms: Mysterious massive waves of spoofed traffic observed since 2020
- GreyNoise Intelligence has been tracking a mysterious phenomenon since January 2020 consisting of massive waves of spoofed traffic called Noise Storms.
- The purpose behind these Noise Storms is still unknown, but they could be associated with covert communications, DDoS attacks, or misconfiguration.
- The traffic originates from Brazil but appears to be obfuscated to conceal the true source, with links to Chinese platforms like QQ, WeChat, and WePay.
- These Noise Storms utilize advanced techniques such as TTL manipulation, OS emulation, and precise targeting to make detection and blocking difficult.
Read Full Article
17 Likes
Hackingblogs
50

Image Credit: Hackingblogs
Major Phishing Network Busted in Spain and Latin America, Over 480,000 Victims Identified
- A major phishing network has been busted in Spain and Latin America.
- Europol, along with law enforcement agencies from Europe and Latin America, assisted in the operation.
- 17 cybercriminals were arrested, and over 480,000 victims were identified.
- The criminals operated a phishing-as-a-service platform targeting mobile phone users globally.
Read Full Article
3 Likes
Securityaffairs
410

Image Credit: Securityaffairs
Hackers stole over $44 million from Asian crypto platform BingX
- Cybercriminals stole more than $44 million worth of cryptocurrency from the Singaporean crypto platform BingX.
- BingX reported a cyberattack on Friday after discovering unauthorized transfers of funds.
- The incident targeted BingX's hot wallet, but measures were taken to secure assets and withdrawals were temporarily suspended.
- Blockchain security firm SlowMist assisted in the investigation, revealing that hackers stole over $47 million worth of crypto.
Read Full Article
24 Likes
Securityaffairs
342

Image Credit: Securityaffairs
OP KAERB: Europol dismantled phishing scheme targeting mobile users
- A joint international law enforcement operation led by Europol dismantled a major phishing scheme targeting mobile users.
- Europol supported European and Latin American law enforcement agencies in dismantling an international criminal network that unlocks stolen or lost mobile phones using a phishing platform.
- The operation, code-named 'KAERB,' resulted in 17 arrests, 28 searches, and the seizure of 921 electronic devices, including mobile phones, vehicles, and weapons.
- The criminal network, using a phishing-as-a-service (PhaaS) platform called iServer, targeted mobile device owners who were attempting to regain access to their phones.
Read Full Article
20 Likes
Securityaffairs
278

Image Credit: Securityaffairs
Ukraine bans Telegram for government agencies, military, and critical infrastructure
- Ukraine's NCCC bans Telegram app for government agencies, military, and critical infrastructure.
- The ban is due to national security concerns.
- Russian intelligence could potentially access Telegram users' data.
- Telegram CEO, Pavel Durov, recently charged with facilitating criminal activities.
Read Full Article
16 Likes
Securityaffairs
283

Image Credit: Securityaffairs
Tor Project responded to claims that law enforcement can de-anonymize Tor users
- The Tor Project has responded to claims that German police have classed a technique to deanonymize users.
- According to German media, law enforcement agencies have been surveilling Tor network by operating their own servers for months.
- Research conducted by ARD’s Panorama and STRG_F revealed that data collected during surveillance is processed using statistical methods, effectively breaking Tor’s anonymity.
- While investigating the pedo-criminal darknet platform “Boystown” between 2019 and 2021, Germany’s Federal Criminal Police Office (BKA) successfully identified Tor nodes used by Andreas G., an administrator of the platform.
- Experts who reviewed the research documents from Panorama and STRG_F confirmed that law enforcement de-anonymized the suspect.
- The Tor Project commented on the case in a post published on its website.
- The maintainers said they have not received the technical details related to the reported deanonymization methods and is seeking the same information given to the Chaos Computer Club (CCC) for further investigation.
- The Tor Project believes that a user of the now-retired Ricochet application was fully deanonymized through a guard discovery attack.
- This occurred because the user was using an older version of Ricochet that lacked the Vanguards-lite protection and the vanguards addon, which were designed to prevent such attacks.
- Matthias Marx warned that authoritarian governments could use the technique to de-anonymize to target opposition, journalists and whistleblowers worldwide.
Read Full Article
17 Likes
Cybersecurity-Insiders
261
Image Credit: Cybersecurity-Insiders
Is Telegram safer than WhatsApp when it comes to Data Security
- Telegram does not provide encrypted conversations for all chats by default.
- Regular chats on Telegram lack encryption.
- Law enforcement can easily monitor non-encrypted chats on Telegram.
- Messages designated as 'Secret Chats' are stored only on the user's device.
Read Full Article
15 Likes
Hackersking
68

Image Credit: Hackersking
Download Free Latest Crack RAT's For Windows & Android
- Remote Access Trojans (RATs) are essential tools for the hacker community to perform various tasks like monitoring, data extraction, etc.
- Cracked RATs offer the full functionality without paying for premium versions.
- There are several websites where you can download free cracked RATs, but make sure to use a VPN and malware scanner before installing any cracked software.
- Top 3 Cracked RATs for Windows and Android are Quasar RAT (Windows), AndroRAT (Android) and njRAT (Windows).
- Cracked RATs also make it easier to test systems that would usually require paying for a license.
- Always check trustworthy sources if you're downloading RATs for ethical hacking or penetration testing purposes.
- For cybersecurity experts, keeping cracked RATs updated will help avoid bugs and security loopholes.
- Using a VPN and burner device can help you stay anonymous while testing vulnerabilities.
- It's crucial to stay ethical while using RATs for testing vulnerabilities. Make sure you have permission!
- Downloading cracked RATs can offer a lot of flexibility. Just remember to stay safe and always verify your sources.
Read Full Article
4 Likes
For uninterrupted reading, download the app