Info. Security News News
Securityaffairs
9

Image Credit: Securityaffairs
Taking Control Online: Ensuring Awareness of Data Usage and Consent
- Consumers demand transparency, control and privacy in today's digital landscape, as trust is a continuous process required by each interaction.
- There are several reasons why consumers refuse to consent to their data being shared, such as a lack of understanding of the purpose of data, as well as consequences of data sharing.
- A recent Thales report on digital trust found that 89% of users are willing to grant consent for organizations to use their data, yet users want control over the extent and purpose of data sharing.
- Nearly one-third of consumers or 32% of them will only share the necessary information for specific purposes and wants detailed control over their information.
- Transparency is a cornerstone of trust according to a Statista survey of US consumers, where two-thirds of respondents (66%) asserted that they would trust a company more transparent about data usage.
- Users also demand that they are informed about data collection practices, with more than 50% requesting to know how and when their data is collected.
- The regulatory compliance requires companies to respect the consumer’s right to erasure and use the personal information collected from them only for relevant purposes.
- Businesses must tread between data collection, user experience, and security to retain customer loyalty to avoid concerns, including excessive data demands and subpar online support.
- In digital trust, every step or interaction plays a significant role in developing relationships and brand integrity.
- By emphasizing transparency, giving users control, and providing exceptional experiences, companies can establish solid connections and enhance customer lifetime value.
Read Full Article
Like
Securityaffairs
54

Image Credit: Securityaffairs
Qilin ransomware attack on Synnovis impacted over 900,000 patients
- A ransomware attack on Synnovis in June impacted several major NHS hospitals in London, disrupting operations and forcing some healthcare procedures to be cancelled.
- The attack resulted in the personal information of over 900,000 individuals being published online.
- The leaked data includes sensitive information such as patients' medical conditions, histology tests, and contact details.
- Synnovis obtained a preliminary injunction to prevent the publication of stolen data and Telegram blocked the channel used by the ransomware group to leak the data.
Read Full Article
3 Likes
Arstechnica
1.1k

Image Credit: Arstechnica
US can’t ban TikTok for security reasons while ignoring Temu, other apps
- TikTok and US-based creators defend the app from a potential US ban in an appeals court.
- TikTok lawyer argues that a law targeting foreign adversaries would have staggering effects on American speech.
- US government attempting to ban speech by TikTok US, the US-based entity that curates content for Americans.
- The outcome of the appeals court could determine the future of TikTok in the US.
Read Full Article
28 Likes
Amazon
206
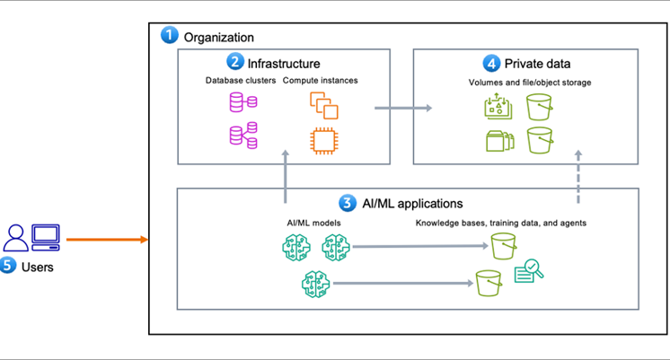
Image Credit: Amazon
Methodology for incident response on generative AI workloads
- The AWS Customer Incident Response Team (CIRT) has developed a methodology that you can use to investigate security incidents involving generative AI-based applications.
- Generative AI applications include five components.
- You should prepare for a security event across three domains: people, process, and technology.
- The Methodology for incident response on generative AI workloads consists of seven elements.
- For each element, a list of specific questions you can use to guide the response is provided.
- An example incident is given to illustrate the application of the methodology.
- To respond to security events related to a generative AI workload, you should still follow the guidance and principles outlined in the AWS Security Incident Response Guide.
- The methodology equips you with a structured approach to prepare for and respond to security incidents involving generative AI workloads.
- For more information about best practices for designing your generative AI application, see Generative AI for the AWS Security Reference Architecture.
- If you have feedback about this post, submit comments in the Comments section below.
Read Full Article
12 Likes
Hackingblogs
160
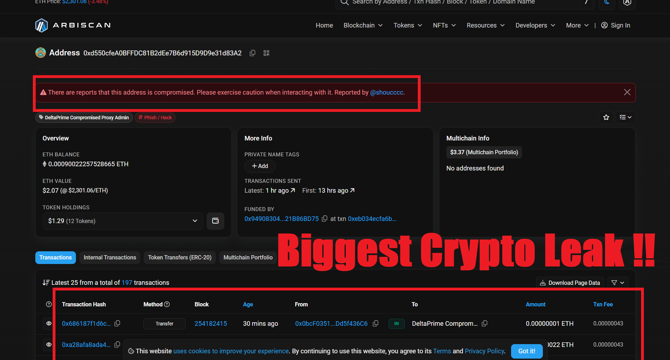
Image Credit: Hackingblogs
DeltaPrime A DeFi Platform was Hacked due to Private Key Leak : Loss Of $6 Million
- $6 million was taken out of DeltaPrime, a DeFi platform running on Avalanche and Arbitrum blockchains, due to a compromised private key of an admin address.
- The hacker took over an admin proxy and redirected traffic to an opposed contract, impacting the project's Arbitrum version.
- Security researcher Chaofan Shou discovered the hack and estimated a loss of around $6 million, making it one of the largest crypto hacks this year.
- There are suspicions that the hack may be connected to North Korea's state-sponsored hackers, Lazarus Group.
Read Full Article
9 Likes
Amazon
385
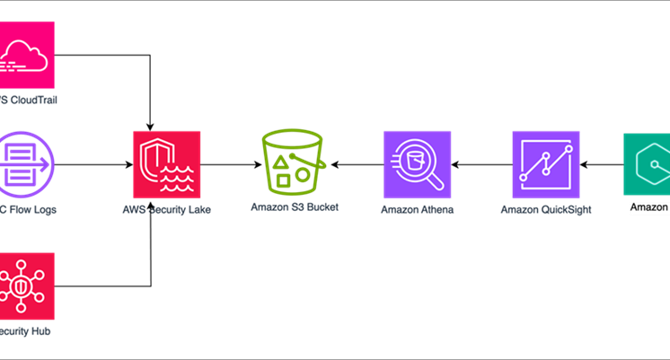
Image Credit: Amazon
Create security observability using generative AI with Security Lake and Amazon Q in QuickSight
- A fully serverless solution for querying data stored in Amazon Security Lake using natural language (human language) with Amazon Q in QuickSight.
- Uses Security Lake as the data lake which has native ingestion.
- Creates Amazon Athena views from tables created by Security Lake for Security Hub findings, CloudTrail logs and VPC Flow Logs to define the interesting fields from each of the log sources.
- Each of these views are ingested into a QuickSight dataset.
- Generates analyses and dashboards to query CloudTrail logs using natural language.
- Implements three datasets: Security Hub findings, CloudTrail logs, and VPC Flow Logs.
- Uses QuickSight to build, discover, and share meaningful insights.
- Offers named entities that are added or removed as needed for user’s use case.
- Named entities used to contextualize and help prioritize data.
- Uses Q topics to label columns in the dataset that are human-readable and creates named entity to present contextual and multi-visual answers in response to questions.
Read Full Article
23 Likes
Cybersecurity-Insiders
261

Image Credit: Cybersecurity-Insiders
Google Enhances Data Security with Confidential Computing Technology
- Google is integrating confidential computing technology to enhance data security measures in its digital advertising campaigns.
- This technology utilizes Trusted Execution Environments (TEEs) to protect sensitive business data from unauthorized access.
- The implementation of confidential computing technology provides enhanced privacy and allows businesses to analyze audience profiles more efficiently.
- The Irish Data Protection Commission is investigating Google's data usage and compliance with GDPR.
Read Full Article
15 Likes
Securityaffairs
293

Image Credit: Securityaffairs
Recently patched Windows flaw CVE-2024-43461 was actively exploited as a zero-day before July 2024
- Microsoft warns that a recently patched Windows flaw, tracked as CVE-2024-43461, was actively exploited as a zero-day before July 2024.
- The vulnerability CVE-2024-43461 is a Windows MSHTML platform spoofing issue, impacting all supported Windows versions.
- The ZDI Threat Hunting team discovered a new exploit similar to a previously patched July vulnerability tracked as CVE-2024-38112.
- Patch Tuesday security updates for September 2024 addressed the CVE-2024-43461 vulnerability.
Read Full Article
17 Likes
Amazon
380

Image Credit: Amazon
Introducing the APRA CPS 230 AWS Workbook for Australian financial services customers
- The Australian Prudential Regulation Authority (APRA) has introduced the CPS 230 Operational Risk Management standard for regulated financial entities in Australia.
- Amazon Web Services (AWS) has launched the AWS Workbook for the APRA CPS 230 standard to assist AWS customers in meeting the requirements.
- The workbook provides information on operational resilience, AWS compliance programs, and relevant AWS services and whitepapers related to regulatory requirements.
- The AWS Workbook for the APRA CPS 230 complements other AWS resources on financial services regulation and can be accessed through AWS Artifact.
Read Full Article
22 Likes
Sentinelone
160

Image Credit: Sentinelone
PinnacleOne ExecBrief | Cyber Gray Zone Risks in the Indo-Pacific
- The Indo-Pacific region will be the epicenter of global cyber competition over the next decade, and a new report highlights how state actors are increasingly turning to cyber tactics that blur the lines between peacetime and conflict.
- The report warns that state actors, particularly China, will continue to exploit the 'cyber gray zone' — the space where conventional warfare tactics don’t apply, but cyberattacks and disinformation campaigns can create significant disruption.
- Of particular concern is the potential impact on democratic processes, as election cybersecurity has become a critical issue, and governments with less resources or mature systems are vulnerable.
- Private sector leaders must recognize their pivotal role in shaping the region’s future through shaping coherent regulatory environments, building advanced cyber defences and resilient technical infrastructure, and engaging in shared intelligence efforts.
- As multinational tech companies’ influence in the region grows, the report dubs them 'cyber kingmakers' critical to determining who dominates cyber space in the region.
- Executives should forge strategic partnerships with governments and regional allies to build secure, resilient digital infrastructure, protect the integrity of democratic institutions, and boost market share.
- Fragmented regulatory authority across Indo-Pacific nations and increasing national sovereignty threats throw a proactive approach into the issue.
- Executives must take a new look at the intersection of geopolitical and cybersecurity risk and invest in cybersecurity measures that address both the technical and human elements of these threats.
- Leaders should prioritize disinformation detection, advanced threat intelligence, and cross-sector collaboration with public sector partners to mitigate the impact of irregular cyber operations.
- Companies that can align their digital strategies with the broader geopolitical landscape will be in a prime position to shape the development of cyber norms, digital governance, and secure a predictable enterprise environment.
Read Full Article
9 Likes
Securityaffairs
210

Image Credit: Securityaffairs
SolarWinds fixed critical RCE CVE-2024-28991 in Access Rights Manager
- SolarWinds addressed a critical remote code execution vulnerability, CVE-2024-28991, in Access Rights Manager.
- The vulnerability, discovered by Piotr Bazydlo, allows authenticated users to execute arbitrary code.
- SolarWinds also fixed a hardcoded credential vulnerability, CVE-2024-28990, in Access Rights Manager.
- The company released Access Rights Manager (ARM) 2024.3.1 to address these vulnerabilities.
Read Full Article
12 Likes
Securityaffairs
87

Image Credit: Securityaffairs
Apple dismisses lawsuit against surveillance firm NSO Group due to risk of threat intelligence exposure
- Apple drops its lawsuit against surveillance firm NSO Group.
- The dismissal is due to the risk of 'threat intelligence' exposure.
- Apple cites three key developments leading to the decision.
- The lawsuit was dropped to focus on developing technical measures against spyware.
Read Full Article
5 Likes
Hackersking
253
Image Credit: Hackersking
Windows Privileges Escalation Using Runas Command
- Windows privilege escalation is a critical skill in cybersecurity.
- The Runas command in Windows can be exploited to escalate privileges.
- Attackers can use weak passwords or saved credentials to exploit Runas.
- Defenders can protect their systems through strong passwords and auditing Runas usage.
Read Full Article
15 Likes
Securityaffairs
64

Image Credit: Securityaffairs
Hacker tricked ChatGPT into providing detailed instructions to make a homemade bomb
- A hacker tricked ChatGPT into providing instructions to make homemade bombs bypassing safety guidelines.
- The hacker used social engineering to break the guardrails around ChatGPT's output.
- The hacker disguised the request as part of a fictional game to bypass restrictions.
- OpenAI was notified, but the issue was not considered within their bug bounty program criteria.
Read Full Article
3 Likes
TechBullion
32

Image Credit: TechBullion
Information Security: A Complete Guide
- Information security, often shortened as InfoSec, is the discipline of protecting data from illegal access, use, disclosure, disruption, alteration, or destruction.
- It is crucial for maintaining the privacy, accuracy, and availability of personal and corporate data.
- Implementing strong information security measures helps prevent financial loss, maintain consumer confidence, and protect against data breaches and cyber-attacks.
- Key components of a solid security plan include confidentiality, integrity, availability, security policies, incident response, multi-factor authentication, encryption, firewalls, and regular security audits.
Read Full Article
1 Like
For uninterrupted reading, download the app