Info. Security News News
Qualys
299

Image Credit: Qualys
Critical Unauthenticated RCE Flaws in CUPS Printing Systems
- A new set of critical unauthenticated Remote Code Execution (RCE) vulnerabilities were revealed in CUPS.
- These vulnerabilities can allow a remote attacker to execute arbitrary code on a target system without valid credentials or prior access.
- Major organizations like Canonical and Red Hat have confirmed this flaw, assigning it a high severity with a CVSS score of 9.9 out of 10.
- More than 75k publicly exposed assets are affected by the flaws, and a huge majority of these assets were found on the default IPP port 631. Of these, more than 42k publicly exposed assets accept unauthenticated connections.
- CUPS is the standard printing system for many Unix-like operating systems, such as GNU/Linux distributions and macOS. CVE vulnerabilities have affected several CUPS versions.
- These vulnerabilities involve multiple components of the CUPS printing system, allowing an unauthenticated attacker to replace existing printers URLs with malicious ones silently.
- The vulnerabilities exploit by directing a malicious UDP packet to port 631 on the target system, leading to remote code execution.
- Enterprises are advised to assess the exposure risk of CUPS systems. They should limit network access, deactivate non-essential services and implement strict access controls.
- The Qualys Threat Research Unit is releasing QIDs to detect these vulnerabilities.
- Organizations can inventory their infrastructure using the QID 38199: CUPS service Detected to mitigate these risks.
Read Full Article
18 Likes
Dataprivacyandsecurityinsider
163

Image Credit: Dataprivacyandsecurityinsider
Department of Commerce Takes Lead in Addressing Risks from Connected Car Technology
- The Department of Commerce has proposed a rule to address risks from connected car technology.
- The rule would prohibit the sale or import of connected vehicles and components from cyber adversaries, specifically China and Russia.
- Connected vehicles pose cybersecurity and national security threats due to the collection and exploitation of sensitive information.
- The proposed rule will impose restrictions on connected vehicle systems and will take effect in 2027 and 2029-2030.
Read Full Article
9 Likes
Dataprivacyandsecurityinsider
427

Image Credit: Dataprivacyandsecurityinsider
FTC Concentrating Enforcement Efforts on Use of AI in Operation AI Comply
- The FTC has launched a new operation, called AI Comply, and filed five enforcement actions against companies who have been using AI to deceive consumers.
- DoNotPay, one of the targeted companies, did not test whether its AI chatbot's output was equal to a human lawyer and did not hire any lawyers.
- DoNotPay will pay a fine of $193k, give notice to subscribers of the limitations of the service, and abstain from making claims without evidence.
- Ascend Ecom, accused of falsely claiming to use AI to help customers make money quickly, has been sued by FTC for defrauding customers of $25M.
- Ecommerce Empire Builders has been sued by the FTC for falsely claiming to offer programs that help consumers build an 'AI-powered Ecommerce Empire.' The company's CEO has allegedly used customers' money for personal gain and not returned the promised profits.
- Rytr has been sued by the FTC for providing a writing assistant service that produces false and deceptive written content for consumer reviews.
- FBA Machine claimed to make guaranteed income through storefronts that utilised AI-powered software, costing consumers more than $15.9 million. FBA Machine falsely guaranteed refunds for initial investments alongside an assurance of risk-free business.
- The enforcement actions make it evident that AI tools and services cannot be used fraudulently, and honest innovators and consumers must be protected.
- The hype of AI technology is being used by fraudsters to deceive consumers, and it is essential to be aware of new schemes.
- Consumer awareness and education is critical in preventing individuals from being duped by fraudsters who use AI.
Read Full Article
25 Likes
Dataprivacyandsecurityinsider
431

Image Credit: Dataprivacyandsecurityinsider
Privacy Tip #414 – Beware of Fraud Schemes Promising Big Monetary Rewards from AI
- Fraudsters are using the hype of new technology, specifically artificial intelligence (AI), to commit fraud on consumers.
- The Federal Trade Commission (FTC) took enforcement action against five companies that use AI hype or sell AI technology that can be used in deceptive and unfair ways.
- Fraudsters are promising big monetary rewards through the use of AI, but are unable to deliver on their promises, defrauding consumers out of millions of dollars.
- Consumers are advised to stay alert of claims that sound too good to be true, especially if they are required to pay any money upfront to benefit from AI.
Read Full Article
25 Likes
Securityaffairs
318
Image Credit: Securityaffairs
Critical RCE vulnerability found in OpenPLC
- Cisco's Talos has disclosed critical and high-severity vulnerabilities in OpenPLC, an open-source programmable logic controller.
- The vulnerabilities can lead to a denial-of-service (DoS) condition and remote code execution.
- The most severe vulnerability is a stack-based buffer overflow in the OpenPLC Runtime EtherNet/IP parser functionality.
- Users are advised to update OpenPLC to the latest version to address these vulnerabilities.
Read Full Article
19 Likes
Hackingblogs
368

Image Credit: Hackingblogs
Learning Wifi Hacking the easy way : Part 1 Wifi Basics
- This comprehensive guide on WiFi hacking for beginners covers the fundamentals including installing the program, understanding its basic functions, and being aware of some crucial WiFi facts and technological information.
- Wireless networks use radio waves similar to two-way radio communication, radios, televisions, and cell phones. Data is sent through a computer's wireless adapter, sent via an antenna, received by a wireless router, decoded, and transmitted through a physical, wired Ethernet connection to the web.
- Hackers can easily target devices and personal information connecting across airwaves including public WiFi networks in places like airports and coffee shops.
- WiFi frequencies are divided into several channels, reducing congestion and interference. WiFi uses radio waves to send data over frequencies between the device and the router, dependant on the data being delivered.
- Components of WiFi transmission include Ethernet (802.3) connection/base station, access points and accessing devices.
- Existing six WiFi standards include IEEE 802.11, IEEE 802.11a, IEEE 802.11b, IEEE 802.11g, IEEE 802.11ac, IEEE 802.11ax. The newest Wi-Fi standard IEEE 802.11ax is intended to increase efficiency and performance in crowded areas.
- WiFi security protocols help protect against data breaches and unwanted access to wireless networks. WEP is an outdated encryption technique that is not recommended for use while WP2, released in 2019 WPA3 offers enhanced defence against brute-force and offline dictionary attacks.
Read Full Article
22 Likes
TechCrunch
177

Image Credit: TechCrunch
Kaspersky defends force-replacing its security software without users’ explicit consent
- Kaspersky's antivirus software was force-replaced with UltraAV without users' consent due to the U.S. government's ban on Kaspersky.
- Approximately one million U.S. customers woke up to find their Kaspersky software uninstalled and replaced by UltraAV.
- Some users expressed confusion and concern over the lack of consent and choice in the migration process.
- Kaspersky defended the automatic migration, citing the need to ensure continuous protection for customers.
Read Full Article
10 Likes
VentureBeat
113

What’s the minimum viable infrastructure your enterprise needs for AI?
- Enterprises of all sizes are increasingly looking to adopt generative AI to increase efficiency and reduce time spent on repetitive tasks.
- Understanding the essential components of an AI solution is crucial.
- The foundation of any effective gen AI system is data.
- Businesses can use off-the-shelf chatbots powered by large language models (LLMs) like Google’s Gemini or OpenAI’s ChatGPT without inputting any company data, but feeding these with your company’s data would provide better benefits.
- Once you have identified the data, the next step is selecting an appropriate LLM to power AI system.
- An open-source LLM is the way to go if you prefer hosting a model on your own private infrastructure for enhanced control and data security.
- Using a retrieval augmented generation (RAG) framework is essential to create relevant answers for a chatbot or AI system.
- The RAG framework is particularly useful for enterprises that need to integrate proprietary company data stored in various formats.
- Technical expertise is still required for the implementation of AI, and development costs for a basic chatbot range from $15,000 to $30,000.
- The AI system will need regular maintenance, and maintenance costs can start at $5,000 per month.
Read Full Article
6 Likes
Krebsonsecurity
404

U.S. Indicts 2 Top Russian Hackers, Sanctions Cryptex
- The US has charged the owner of now-defunct carding shop Joker's Stash, Timur Shakhmametov, with overseeing the sale of tens of millions of cards stolen from US retailers.
- The shop was unique in that it claimed to sell only cards it had hacked itself, rather than reselling cards stolen by third-party hackers.
- The US has also charged and sanctioned Russian cybercriminal Sergey Ivanov, who went by the name Taleon and whose Cryptex cryptocurrency exchange allegedly laundered billions of dollars.
- Taleon was also found to have worked with BriansClub, which has sold at least $242m worth of stolen cards in the past two years, and was responsible for one-third of cards for sale in underground shops.
- Other charges include Taleon apparently moving large amounts of physical cash, and using one of the last remaining domestic cash-delivery services still operating after Russia's invasion of Ukraine in 2014.
- Cryptex has received more than $1.6bn since its inception in 2018, according to Chainalysis.
- Joker's Stash is believed to have earned at least $280m (possibly over $1bn) in revenue.
- In January, Joker's Stash announced its closure after European law enforcement seized a number of its servers.
- Cryptex has allegedly become a major conduit for ransomware transactions, including what is believed to be the largest ransomware payment to date.
- Charges laid out in US Department of Justice indictments include both Taleon and Shakhmametov laundering virtual currency for ransomware actors and darkweb marketplace vendors.
Read Full Article
24 Likes
Socprime
406

Image Credit: Socprime
Gamaredon Attack Detection: Cyber-Espionage Operations Against Ukraine by the russia-linked APT
- Cyber-espionage campaigns against Ukraine have been launched by state-sponsored and Russia-linked Gamaredon since 2014.
- The group, also known as Hive0051, UAC-0010, or Armageddon APT, remains the most active hacking collective in the Ukrainian cyber threat landscape.
- The group has been consistently deploying its malicious tools despite escalating conflict in the region.
- The group presents significant challenges to cybersecurity defenders and is constantly evolving its tactics.
- To detect Gamaredon APT attacks, security professionals might rely on SOC Prime Platform, offering advanced threat detection, automated threat hunting, and AI-powered detection engineering solutions.
- Gamaredon’s attack methods include spearphishing campaigns, installation of backdoors and using fast flux DNS.
- The group's cybere-spionage capabilities have evolved significantly, developing new PowerShell tools designed to steal sensitive data from web applications, email clients, and messaging apps.
- Gamaredon uses third-party services like Telegram, Cloudflare, and ngrok to bypass network-based detections.
- The list of groups' toolset includes downloaders, droppers, weaponizers, stealers, backdoors, and specialized utilities.
- The aggressive tactics and persistence of the group pose a significant threat to potential victims, which stresses the need for ultra-responsiveness from defenders.
Read Full Article
24 Likes
Securityaffairs
22

Image Credit: Securityaffairs
China-linked APT group Salt Typhoon compromised some U.S. internet service providers (ISPs)
- China-linked APT group Salt Typhoon has breached several U.S. internet service providers in recent months to gather intelligence or carry out disruptive cyberattacks.
- Experts are investigating whether the attackers gained access to Cisco Systems routers.
- The group is also known as FamousSparrow and GhostEmperor.
- The campaign appears focused on intelligence gathering rather than crippling infrastructure.
- Chris Krebs from SentinelOne suggested that the group behind Salt Typhoon may be affiliated with China’s Ministry of State Security.
- Chinese nation-state actors have shifted focus from stealing secrets to infiltrating critical U.S. infrastructure.
- In August 2021, researchers reported that a China-linked APT group successfully compromised an internet service provider in order to poison DNS responses for target organisations.
- China-linked APT group Daggerfly infiltrated an African telecom operator and used new malware in 2023.
- In June 2019, a Chinese APT group named as APT10 was linked to the espionage campaign targeting telco providers in Operation Soft Cell.
- China has consistently denied accusations about its involvement in cyberattacks.
Read Full Article
1 Like
Amazon
168
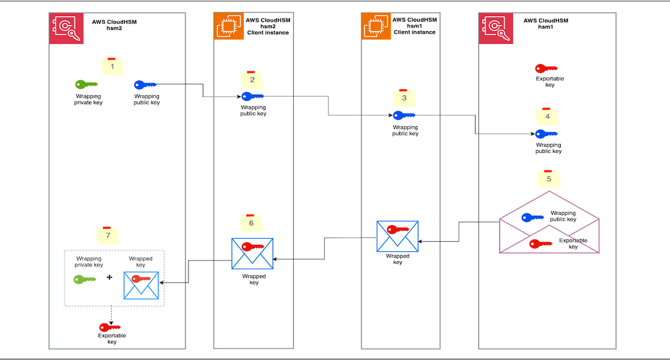
Image Credit: Amazon
How to migrate 3DES keys from a FIPS to a non-FIPS AWS CloudHSM cluster
- AWS has introduced a new CloudHSM hardware security module (HSM) instance type called hsm2 that supports Federal Information Processing Standard (FIPS) 140-3 Level 3.
- AWS CloudHSM hsm2 offers increased storage capacity of 16,666 total keys, the ability to run CloudHSM clusters in non-FIPS mode, and support for Mutual Transport Layer Security (mTLS) between CloudHSM client SDKs and the CloudHSM cluster.
- To securely and efficiently migrate Triple DES (3DES) keys from a hsm1 CloudHSM cluster to a new hsm2 cluster, the RSA-AES wrapping mechanism is suggested.
- Customers that don’t use 3DES can migrate keys to an hsm2 cluster by creating an hsm2 cluster running in FIPS mode from an hsm1 backup.
- AWS recommends migrating 3DES workloads to Advanced Encryption Standard (AES), but if this isn't feasible and you intend to continue to use 3DES, an hsm2 cluster running in non-FIPS mode can manage your 3DES keys and take advantage of the new hsm2 benefits.
- To migrate keys between CloudHSM clusters without using backups, CloudHSM CLI is used with the RSA-AES wrap mechanism.
- There are important considerations when migrating cryptographic keys, including the fact that the solution only works for exportable keys, and when a key is migrated, the crypto user who unwraps the key becomes the key owner.
- To test whether your 3DES key was migrated successfully, you can encrypt and decrypt a simple message using your migrated key to obtain plaintext that should match the original message.
- The same methodology can be used to migrate keys between many AWS CloudHSM cluster pairs and can be extended to other CloudHSM SDKs, like JCE and PKCS #11, to automate the migration process.
- To migrate keys from on-premises or other non AWS HSMs to AWS CloudHSM, the same principle of wrap and unwrap can be applied.
Read Full Article
10 Likes
Securityintelligence
190

Image Credit: Securityintelligence
Ransomware on the rise: Healthcare industry attack trends 2024
- According to the IBM Cost of a Data Breach Report 2024, the global average cost of a data breach reached $4.88 million this year.
- For the healthcare industry, the report offers both good and bad news.
- As noted by data from the Office of the Director of National Intelligence, the number of ransomware attacks almost doubled between 2022 and 2023.
- Compromise through any of these paths provides the opportunity for cyber criminals to download and install ransomware.
- Attackers are looking to encrypt and exfiltrate any data, which makes it harder for healthcare organizations to carry out key tasks or puts them at risk of regulatory compromise.
- Ransomware attacks are trending upward in part because hackers are seeing repeated success.
- Reducing ransomware risks requires a two-part approach that includes protection and detection.
- AI and automated tools can help shorten the time required for organizations to detect and, therefore, mitigate attacks.
- While it’s impossible to fully eliminate the risk of ransomware, businesses can reduce their compromise potential by combining email protection tools with AI detection solutions.
- Ransomware attacks on healthcare organizations continue to rise as cyber criminals recognize the value of operational and patient data in compelling action from affected companies.
Read Full Article
11 Likes
Securityaffairs
122

Image Credit: Securityaffairs
Privacy non-profit noyb claims that Firefox tracks users with privacy preserving feature
- Privacy non-profit noyb filed a complaint with the Austrian DPA against Firefox for enabling tracking in Firefox without user consent.
- The complaint claims that the Privacy-Preserving Attribution (PPA) feature in Firefox allows the browser to track user behavior on websites without explicit consent.
- The feature was enabled by default in a recent Firefox update, without informing or seeking consent from users.
- Noyb argues that the PPA feature violates user privacy and adds another method for websites to target ads, despite Mozilla's intention to enhance user privacy.
Read Full Article
7 Likes
Securityaffairs
9

Image Credit: Securityaffairs
Data of 3,191 congressional staffers leaked in the dark web
- The personal information of over 3,000 congressional staffers was leaked on the dark web.
- The leaked data includes passwords, IP addresses, and social media information.
- Approximately 1 in 5 congressional staffers had their personal information exposed.
- The leaks occurred due to staffers using their official email addresses for third-party services.
Read Full Article
Like
For uninterrupted reading, download the app