Info. Security News News
Securityaffairs
283

Image Credit: Securityaffairs
U.S. Treasury issued fresh sanctions against entities linked to the Intellexa Consortium
- The U.S. Department of Treasury issued new sanctions against five executives and one entity associated with the Intellexa Consortium for their role in developing, operating, and distributing commercial spyware.
- The Intellexa Consortium was created in 2019, it has acted as a marketing umbrella for various offensive cyber companies that provide commercial spyware and surveillance tools designed for targeted and mass surveillance campaigns.
- The US government sanctioned financial entities linked to the Intellexa Consortium’s sale of surveillance software.
- The fresh package of sanctions issued by the U.S. government is part of the effort against commercial spyware vendors.
- The US government has also implemented a new policy to impose visa restrictions on individuals involved in the misuse of commercial spyware.
- The Predator spyware is known for its extensive data-stealing and surveillance capabilities.
- Commercial spyware poses a significant threat to the national security of the United States.
- The Predator spyware has resurfaced with fresh infrastructure after a decline caused by US sanctions against Intellexa Consortium.
- The Commerce Department’s Bureau of Industry and Security (BIS) added Intellexa and Cytrox to the Entity List for trafficking in cyber exploits used to gain access to information systems.
- The U.S. Government warns of the key role that surveillance technology plays in surveillance activities that can lead to repression and other human rights abuses.
Read Full Article
17 Likes
Securityaffairs
155

Image Credit: Securityaffairs
Broadcom fixed Critical VMware vCenter Server flaw CVE-2024-38812
- Broadcom has fixed a critical vulnerability, CVE-2024-38812, in VMware vCenter Server.
- The vulnerability could allow remote attackers to achieve code execution.
- Broadcom also addressed a privilege escalation vulnerability, CVE-2024-38813, in vCenter Server.
- The company released security updates to address these vulnerabilities.
Read Full Article
9 Likes
TroyHunt
45

Image Credit: TroyHunt
From Dreams to Reality: The Magic of 3D Printing, with Elle Hunt
- Elle, at the age of 11, presented at NDC Oslo about technology.
- She taught technology professionals new things they hadn't seen before.
- A video of her presentation is now available online.
- Elle displayed her 3D printed catapult and launched projectiles from a Chat GPT prompt during the Q&A session.
Read Full Article
2 Likes
Dev
417
Image Credit: Dev
What are ITDR in cyber security?
- ITDR, or Identity Threat Detection and Response, is a security practice and framework in cybersecurity.
- ITDR aims to detect, respond to, and mitigate threats related to compromised identities in an organization's IT infrastructure.
- It involves activities such as threat detection, incident response, monitoring and logging, and remediation.
- ITDR is crucial in protecting against identity-based attacks like phishing and credential stuffing.
Read Full Article
25 Likes
TheStartupMag
210

Image Credit: TheStartupMag
Top Resources for Effective Contact Center Operations
- Embracing the latest technologies, investing in agent training, and integrating omnichannel approaches are critical components in increasing contact center service.
- Leveraging technology such as real-time data analytics, CRM systems, and AI can enhance contact center performance and streamline operations.
- Training and development programs are essential for equipping agents with the necessary skills to navigate customer interactions efficiently.
- Implementing omnichannel strategies ensures consistent and seamless interactions across multiple platforms, leading to improved customer service.
Read Full Article
12 Likes
Securityaffairs
266

Image Credit: Securityaffairs
Remote attack on pagers used by Hezbollah caused 9 deaths and thousands of injuries
- At least nine individuals, including a child, were killed and over 2,800 were injured due to the explosion of their pagers across Lebanon.
- Hezbollah officials consider this incident the biggest security breach in nearly a year of conflict with Israel.
- Threat actors targeted the pagers used by Hezbollah fighters to communicate and avoid being tracked by Israeli intelligence.
- The cause of the pager explosions is still unclear, but experts speculate it could be a case of a supply chain attack.
Read Full Article
15 Likes
Hackingblogs
77
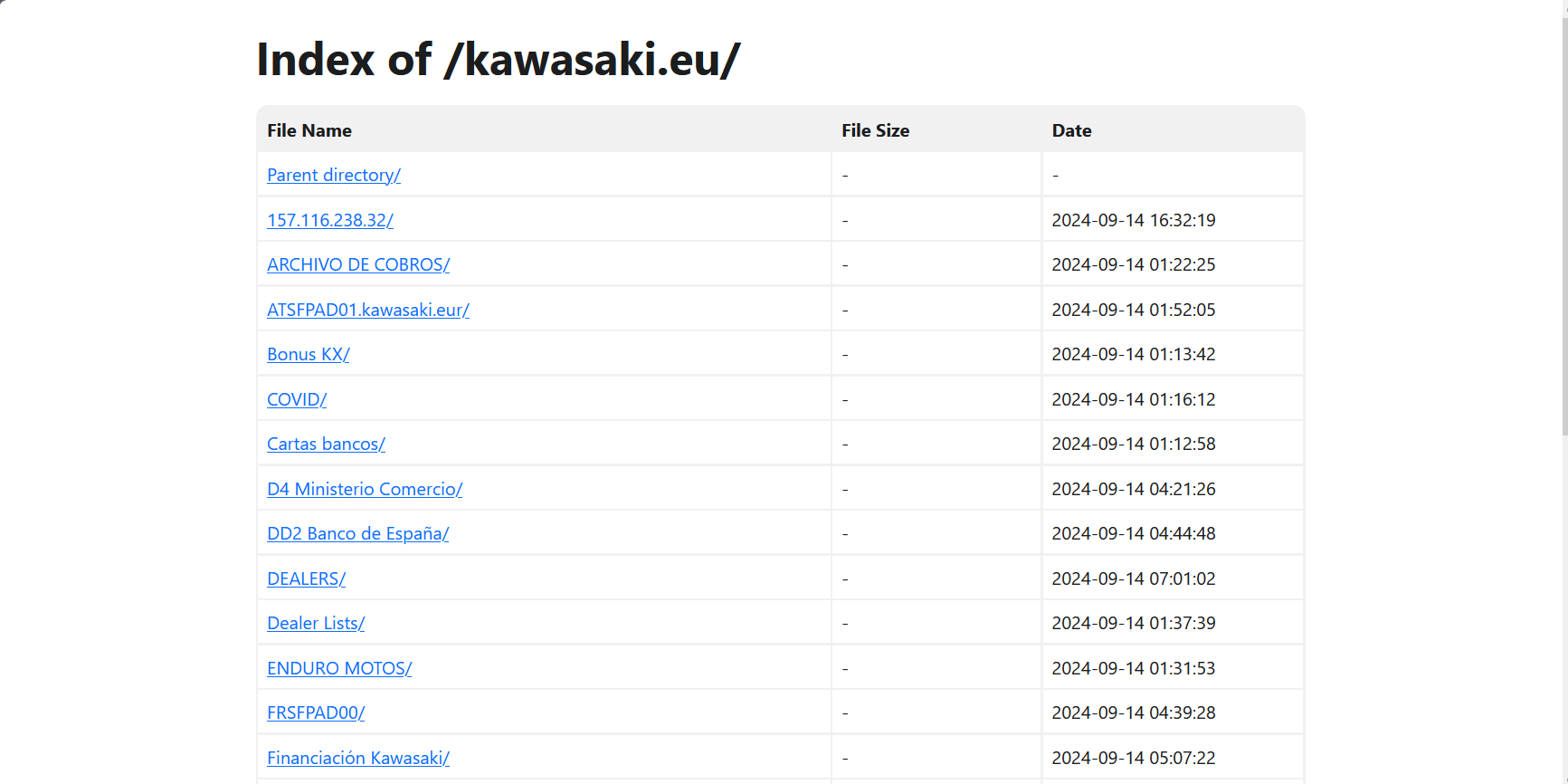
Image Credit: Hackingblogs
Kawasaki Was Hacked : RansomHub releases 487GB of Leaked Data
- Motorbike company Kawasaki Motors Europe (KME) experienced a cyberattack in early September.
- RansomHub ransomware organization released 487GB of stolen data.
- Financial and corporate information were compromised, raising cybersecurity concerns.
- The FBI, CISA, and other organizations have issued an alert to combat RansomHub.
Read Full Article
4 Likes
Sentinelone
210

Image Credit: Sentinelone
macOS Sequoia | What’s New in Privacy and Security for Enterprise?
- macOS 15 Sequoia brings a fully standalone GUI version of password management app, which supports both passwords and passkeys and contains "Authenticator" functionality for generating verification codes.
- Gatekeeper and XProtect receive significant changes in the form of a new "xprotect" tool and tweaks to the Finder and spctl command.
- TCC has new policies in place for translucent windows, screen recording and more. macOS Sequoia also allows MAC addresses to rotate over time to avoid tracking by Wi-Fi network operators.
- The move from Apple IDs to Apple accounts aligns macOS closer to iOS and iPadOS. The long redundant periodic maintenance mechanism is no longer in use as Apple removes legacy code.
- SentinelOne announced support for macOS 15 Sequoia on launch day with extensive beta testing of macOS Agent version 24.2.2.
- Apple’s new version of macOS, Sequoia, releases with many security and privacy changes. The password app is a standalone application that supports passwords and passkeys.
- Screens recording apps will now need TCC permissions every month, and any application that requires local network access will require permission from the user.
- Rotating MAC addresses on Wi-Fi networks, easier iCloud use on virtual machines, and a change to the Gatekeeper’s underlying command line tool, spctl, are introduced.
- Apple has renamed Apple ID to Apple Account and deleted the redundant Periodic management mechanism, a legacy code on macOS.
- The take-up of Apple Silicon has made virtualization straightforward. Still, users will be required to sign in to iCloud, including Managed Accounts and will no longer be able to use legacy permissions for math notes and writing tools.
Read Full Article
12 Likes
Hackersking
4

Image Credit: Hackersking
How to use GoBuster for OSINT: Step By Step Guide
- GoBuster is a versatile tool for finding hidden directories, files, and DNS subdomains.
- GoBuster is popular among ethical hackers and cybersecurity professionals for its speed and simplicity.
- Installing GoBuster on Kali Linux is straightforward using either standard installation or cloning from GitHub.
- Practical use cases of GoBuster include directory brute-forcing, DNS enumeration, and adding extensions for specific file types.
Read Full Article
Like
Securityaffairs
435

Image Credit: Securityaffairs
Chinese man charged for spear-phishing against NASA and US Government
- The U.S. Department of Justice charged Chinese national Song Wu for spear-phishing attacks targeting NASA, U.S. Air Force, Navy, Army, and FAA.
- Wu used fake email accounts to pose as U.S.-based researchers and engineers, tricking government personnel into sharing software and source code.
- The spear-phishing campaign aimed to collect specialized software used in aerospace engineering and computational fluid dynamics.
- Wu, who remains at large, faces charges of wire fraud and aggravated identity theft with a potential sentence of up to 20 years in prison.
Read Full Article
26 Likes
Socprime
114

Image Credit: Socprime
CVE-2024-6670 and CVE-2024-6671 Detection: RCE Attacks Exploiting Critical SQL Injection Vulnerabilities in WhatsUp Gold
- Hackers are exploiting critical SQL injection vulnerabilities (CVE-2024-6670 and CVE-2024-6671) in Progress Software's WhatsUp Gold for RCE attacks.
- A tailored Sigma rule set is available on the SOC Prime Platform to detect exploitation attempts.
- Trend Micro researchers observed RCE attacks using the Active Monitor PowerShell Script feature in WhatsUp Gold.
- Mitigation measures include upgrading to the latest patched software version, restricting access, and using strong passwords.
Read Full Article
6 Likes
Securityintelligence
343

Image Credit: Securityintelligence
CVE backlog update: The NVD struggles as attackers change tactics
- The number of vulnerabilities processed by the National Vulnerability Database (NVD) started to slow down in February.
- As of May, 93.4% of new vulnerabilities and 50.8% of known exploited vulnerabilities were still waiting on analysis.
- NIST funding was cut by 12% this year, making it more difficult for the agency to identify and analyze CVEs.
- The sheer number of reported vulnerabilities poses a problem for analysis efforts. NIST reported 33,137 vulnerabilities in 2023.
- While CVEs remain critical for effective security, attackers aren’t using their severity rating as criteria for compromise.
- Attackers focus on the most exploitable vulnerabilities, which are often ranked as medium or low severity.
- Companies need to prioritize IT visibility, focusing on exploitability and share the burden between different teams.
- Security teams can leverage alternative resources- CISA Vulnrichment and The CVE Program.
- NIST hopes to eliminate the CVE backlog by September 2024, with new focus on AI-enabled threats.
- Enterprises must change their approach to align with attackers' evolving tactics.
Read Full Article
20 Likes
Precisely
311

Image Credit: Precisely
Understanding DORA: What It Is and Why It Matters for Financial Entities
- The Digital Operational Resilience Act (DORA) is a regulation for the financial sector designed to enhance and unify cyber resilience across Europe. DORA mandates that financial institutions and ICT service providers adopt stringent cybersecurity measures starting in January 2023.
- DORA aims to mitigate the risks posed by the growing complexities of cyber threats and to safeguard the sector against potential fallout.
- DORA introduces key requirements that financial entities must comply with, including implementing an ICT risk management framework, incident reporting, digital operational resilience testing, third-party risk management, and sharing information with entities within the financial ecosystem.
- To comply with DORA, organizations should follow these five essential steps: conducting a comprehensive gap analysis, developing or enhancing an ICT risk management framework, implementing a robust incident reporting procedure, enhancing third-party risk management, and planning and executing regular digital resilience testing.
- DORA may require only incremental changes for large financial institutions with mature cybersecurity measures in place. However, for smaller entities or those with less developed security postures, DORA represents a significant regulatory burden.
- DORA's requirements extend beyond traditional financial institutions to include critical ICT service providers as well.
- DORA's introduction is indicative of the increased importance that regulators place on cybersecurity within the financial sector and seeks to ensure that financial entities are not only aware of, but actively managing cyber risk.
- As we approach the deadline for full compliance in 2025, now is a crucial time for financial institutions to assess their current cybersecurity measures and implement necessary changes to meet DORA's requirements.
- Understanding and implementing DORA is crucial for financial services entities to ensure the digital resilience of their organization, safeguard against potential cyber incidents, and continue to serve customers with confidence.
Read Full Article
18 Likes
Socprime
201

Image Credit: Socprime
Celebrating Detection Engineering Excellence
- SOC Prime empowers skilled threat researchers and detection engineers to enhance their impact on collective cybersecurity efforts via its Threat Bounty Program.
- SOC Prime has provided Threat Bounty Program members with access to Uncoder AI –– a professional IDE & co-pilot for detection engineering.
- SOC Prime has shifted all activities of the Threat Bounty Program to Uncoder AI, providing users with advanced features for creating, validating, and storing detection rules.
- Uncoder AI acts as an integrated development environment (IDE) and Detection Engineering co-pilot, harnessing the power of augmented intelligence to enable SOC teams to seamlessly code, validate, and share detection ideas using Sigma and MITRE ATT&CK as code assistants.
- Uncoder AI's smart autocomplete and quality control features help researchers code detections flawlessly, faster and with ease.
- SOC Prime has introduced digital recognition badges for Uncoder AI mastery, celebrating outstanding contributions to detection engineering.
- SOC Prime is committed to equipping cybersecurity practitioners with the tools to sharpen their skills and bolster global cyber defense. Uncoder AI helps researchers stay ahead of emerging threats, making them vital contributors to the fight against cybercrime.
- Threat Bounty Program provides unique opportunities for detection engineers and threat hunters to challenge and monetize their skills with Uncoder AI.
Read Full Article
12 Likes
Securityaffairs
100

Image Credit: Securityaffairs
U.S. CISA adds Microsoft Windows MSHTML Platform and Progress WhatsUp Gold bugs to its Known Exploited Vulnerabilities catalog
- U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Microsoft Windows MSHTML Platform and Progress WhatsUp Gold bugs to its Known Exploited Vulnerabilities catalog.
- CISA added SonicWall SonicOS, ImageMagick and Linux Kernel vulnerabilities to its Known Exploited Vulnerabilities catalog.
- CVE-2024-43461: Microsoft Windows MSHTML Platform Spoofing Vulnerability
- CVE-2024-6670: Progress WhatsUp Gold SQL Injection Vulnerability
Read Full Article
6 Likes
For uninterrupted reading, download the app