Info. Security News News
Amazon
393

Image Credit: Amazon
AWS renews its GNS Portugal certification for classified information with 66 services
- Amazon Web Services (AWS) has renewed its Portuguese GNS certification for handling classified information.
- The certification confirms that AWS cloud infrastructure, security controls, and operational processes meet the requirements for handling classified data up to the Reservado (Restricted) level.
- The certification covers a total of 66 AWS services, including 40 new additions.
- This allows AWS customers in Portugal, including public sector organizations and defense contractors, to securely use AWS cloud services for handling restricted information.
Read Full Article
23 Likes
Kaspersky
283

Image Credit: Kaspersky
Kaspersky AI Technology Research Center | Kaspersky official blog
- Since its inception, Kaspersky has been a pioneer in integrating artificial intelligence (AI), specifically machine learning (ML), into its products and services for cybersecurity. The Kaspersky AI Technology Research Center is comprised of data scientists, ML engineers, and other cybersecurity experts to address complex threats related to AI and ML.
- Kaspersky has developed a variety of AI/ML-powered threat detection technologies, primarily to identify malware, which include neural network algorithms and decision-tree ML technology. They have also developed AI technologies specific to corporate products and services such as Kaspersky Managed Detection and Response, Kaspersky SIEM and Kaspersky XDR.
- Kaspersky also explores the capabilities of generative AI, particularly large language models (LLM), to explore new solutions through the use of LLM tools such as ChatGPT.
- Additionally, Kaspersky is researching the use of AI/ML in industrial environments with Kaspersky MLAD (Machine Learning for Anomaly Detection) and the Kaspersky Neuromorphic Platform (KNP). These focus on predictive analytics, automatic recognition of early signs of impending attacks or failures, and AI solutions based on spiking neural networks and the energy-efficient neuromorphic processor developed by Russian-based Motive Neuromorphic Technologies (Motive NT).
- Kaspersky is actively patenting its AI technologies, both for detection technologies such as malware detection and improving datasets for ML, but also for technologies related to anomaly detection and the use of neuromorphic networks in industry-relevant tasks.
- Kaspersky's AI expertise is not limited to research teams. Other teams also contribute significantly, apply ML in many tasks like Machine Vision Technologies in the Antidrone team or AI coding assistants in the CoreTech and KasperskyOS departments.
- The primary goal of Kaspersky's AI Technology Research Center is to develop AI technologies for cybersecurity, raise awareness about the pros and cons of AI and its applications in security, and actively monitor improper or malicious AI usage.
- Kaspersky's efforts to raise awareness include demonstrating the danger of deepfake videos and sponsorships of educational courses on AI for cybersecurity. They are also involved in the creation of international standards for the use of AI and presented the first principles for the ethical use of AI systems in cybersecurity at the Internet Governance Forum in 2023.
Read Full Article
17 Likes
Securityintelligence
347

Image Credit: Securityintelligence
CISA chief AI officer follow-up: Current state of the role (and where it’s heading)
- The appointment of CISA’s AI specialist as CISA’s first-ever CAIO is a sign of the importance of understanding, leveraging and cautiously navigating the new digital landscape.
- The role of the CAIO is relatively new to the C-suite, but it has the potential to reshape how companies are organised as AI technology continues to disrupt business operations.
- The reporting lines of the CAIO vary depending on the existing structure of the organisation. Some CAIOs report to the CEO, while others report to the COO, CTO, or CIO.
- The CAIO's responsibilities include being well-versed in AI developments and its supporting technologies, articulating a compelling vision for the company’s AI potential while navigating ethical considerations from AI adoption.
- The surge in demand for AI expertise has increased the importance of AI-focused leadership across organisations. LinkedIn data shows that views and applications for AI-related jobs continue to grow, with many nations globally having seen more than 10% growth in these areas.
- AI-related roles could previously have been spread across multiple senior titles, but the CAIO consolidates these AI-related responsibilities and elevates them to the C-suite level.
- The DHS has also been focusing on AI-related initiatives, with the establishment of the Artificial Intelligence Safety and Security Board.
- CISA's chief AI officer will help the agency leverage AI technology while ensuring that critical infrastructure providers can develop and adopt AI in ways that are safe and secure.
- CISA’s initiatives have been instrumental in advancing the agency’s understanding of the potential security impacts of AI, with several executive orders to develop and implement comprehensive AI strategies.
- The CAIO position highlights the need for a unique blend of technical expertise, strategic vision and leadership skills to succeed. The CAIO needs to effectively balance the opportunities and the challenges presented by AI.
Read Full Article
20 Likes
Securityaffairs
150

Image Credit: Securityaffairs
SIEM for Small and Medium-Sized Enterprises: What you need to know
- Research from the Identity Theft Resource Center (ITRC) recently found that 73% of US small business owners experienced a cyberattack in 2023.
- Security Information and Event Management (SIEM) solutions combine security information management (SIM) and security event management (SEM) into a single security management system, providing organizations with a centralized location to understand the activities in their IT environments.
- Contrary to what they might believe, small and medium-sized enterprises (SMEs) are a favorite target for cybercriminals.
- SMEs must find a way to protect themselves without breaking the bank. Security Information and Event Management (SIEM) solutions are a great way to achieve this.
- SIEM solutions offer many benefits for SMEs, enhancing their security posture while keeping costs relatively low.
- SIEM solutions help SMEs demonstrate compliance by continuously generating audit and reporting trails, which organizations can present to regulators.
- The best SIEM solutions will have pre-defined playbooks that outline response actions for the most common types of security incidents.
- Most SMEs want to grow their business, so they must look for security solutions to grow with them. The best SIEM solutions use flexible cloud infrastructure.
- However, it’s crucial for SMEs to recognize that not all SIEM solutions are equal.
- All in all, SIEM – particularly SIEM-as-a-Service – can have a transformative impact on the security of SMEs without overstretching their understandably tight budgets.
Read Full Article
9 Likes
Securityaffairs
265

Image Credit: Securityaffairs
Antivirus firm Dr.Web disconnected all servers following a cyberattack
- Russian anti-virus firm Doctor Web (Dr.Web) disconnected all servers following a cyberattack on September 14.
- The company detected unauthorized interference to its IT infrastructure but assured that no user systems were affected.
- As a security precaution, all resources were temporarily disconnected from the network for investigation.
- The company has resumed its virus databases and the release will resume shortly.
Read Full Article
15 Likes
Amazon
315

Image Credit: Amazon
Refine unused access using IAM Access Analyzer recommendations
- AWS Identity and Access Management (IAM) Access Analyzer offers prescriptive recommendations with actionable guidance that you can share with your developers to quickly refine unused access.
- IAM Access Analyzer continuously analyzes your accounts to identify unused access and consolidates findings in a centralized dashboard.
- To use IAM Access Analyzer recommendations to refine unused access, focus on the recommendations to refine unused permissions and filter unused permission findings.
- Analyze outdated resource policies and remove access permission that are no longer in use.
- Generate remediation policies based on least privilege principles and use the recommendations provided by IAM Access Analyzer.
- IAM Access Analyzer also provides policy recommendations with actionable steps that guide you to refine unused permissions.
- To generate recommendations for unused permissions, you can use the IAM console, AWS CLI, and AWS API.
- Review all recommended policies before applying them as they are based on the original policy and might not be optimal for your business needs.
- After updating the policies based on the recommended policy proposed, the finding status will change from active to resolved.
- IAM Access Analyzer saves considerable time by analyzing and identifying unused access and guiding you to refine it.
Read Full Article
18 Likes
Amazon
398

Image Credit: Amazon
Using Amazon Detective for IAM investigations
- Amazon Detective is a tool to investigate IAM users and roles to help determine if a resource is involved in a security event and obtain an in-depth analysis.
- Detective Investigation uses machine learning and threat intelligence to identify potential indicators of compromise (IoCs) or suspicious activity.
- It can help determine if IAM entities have potentially been compromised or involved in known tactics, techniques, and procedures (TTPs) from the MITRE ATT&CK framework.
- To start an investigation, sign in to the console and choose the desired scenario.
- Some of the scenarios use Amazon GuardDuty, an intelligent threat detection service.
- Scenario 1 involves automated investigations and allows the users to view the number of IAM roles and users impacted by security events over a set period.
- Scenario 2, Investigator Person, involves triaging the resources associated with a GuardDuty finding wherein an IAM user or role has been identified in an anomalous behavior.
- Scenario 3, Threat Hunter Persona can be used to investigate suspicious activity in an organization and to find out which IAM entities have been communicating with a command-and-control IP address.
- There's no additional charge for this capability, and it's available today for existing and new Detective customers in AWS Regions that support Detective.
- Detective Investigations offer a proactive approach to threat identification and mitigation and can prove to be a useful tool for security analysts.
Read Full Article
23 Likes
Krebsonsecurity
141

Scam ‘Funeral Streaming’ Groups Thrive on Facebook
- Scammers are spamming Facebook with groups that claim to offer live streaming of funeral services for recently deceased individuals.
- The scammers include images of the deceased as profile pictures, and attract users to newly created, fake live streaming websites that request credit card payments.
- Some sites also ask for donations in the name of the deceased, leading to an unknown number of victims.
- The scam has also expanded to include live streaming for any advertised event or social occasion on Facebook.
- Many of these scam funeral groups have subscribers who followed the link in anticipation of the funeral service being streamed online.
- The groups are typically linked to newly-registered video streaming websites that ask users for credit card information and other personal details.
- One popular streaming site linked to funeral service scams is livestreamnow[.]xyz, which is hosted by a Bangladeshi web hosting provider.
- Other fake streaming sites include onlinestreaming[.]xyz, and live24sports[.]xyz.
- The registrant of livestreamnow[.]xyz is a small IT company in Bangladesh called Apkdownloadweb.
- The admin of Apkdownloadweb is a Bangladeshi individual named Mohammod Abdullah Khondokar, according to stolen login credentials.
Read Full Article
8 Likes
Securityaffairs
68
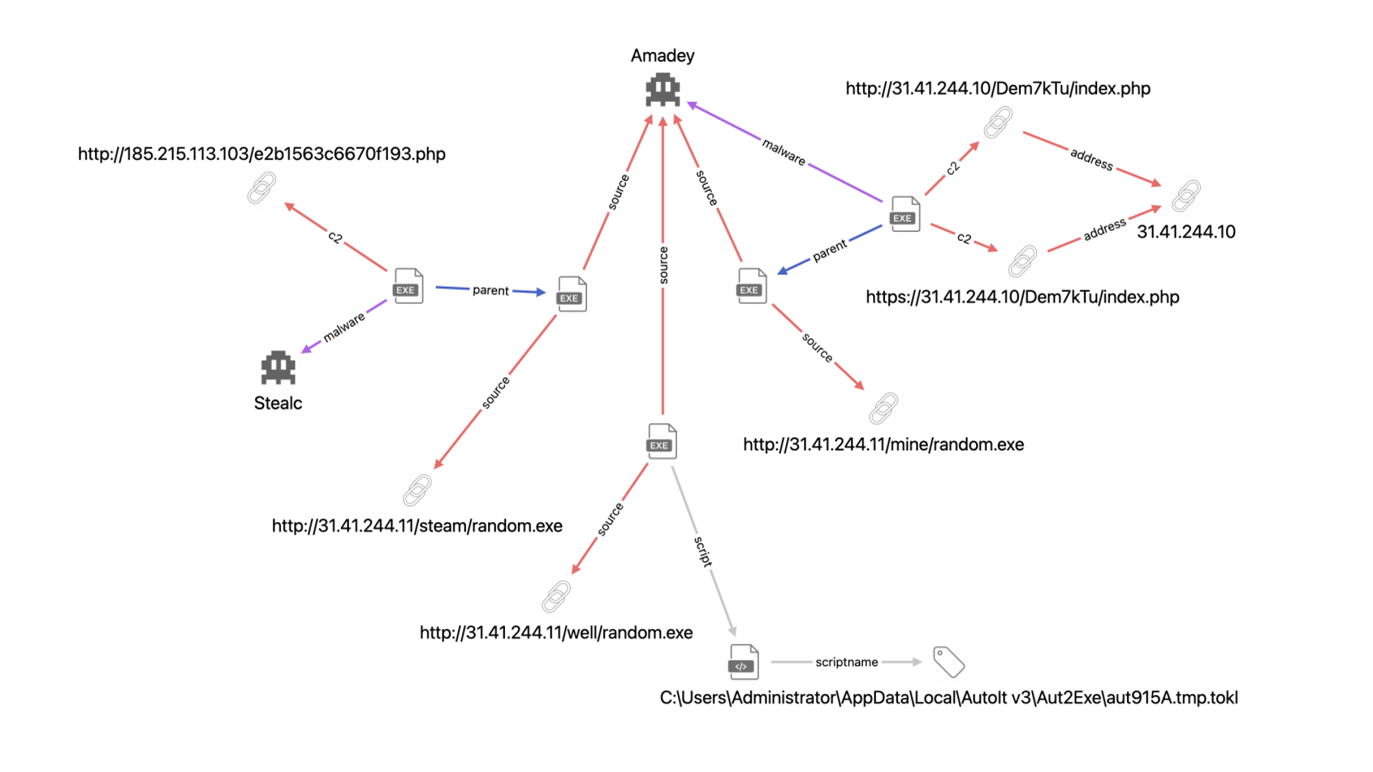
Image Credit: Securityaffairs
Credential Flusher, understanding the threat and how to protect your login data
- Credential Flusher is a method that allows hackers to steal login credentials directly from the victim’s web browser.
- The method utilizes an AutoIt script to force users to enter their credentials in a browser operating in kiosk mode, making it easier for hackers to obtain the desired information.
- The stolen credentials can be used to access various online accounts, leading to identity theft and financial losses.
- Protective measures include using updated antivirus software, enabling 2FA authentication, being cautious of phishing attempts, regularly updating software, and using complex and unique passwords.
Read Full Article
4 Likes
Amazon
187

Image Credit: Amazon
Get to know Amazon GuardDuty Runtime Monitoring for Amazon EC2
- Amazon GuardDuty Runtime Monitoring is a feature that detects threats against Amazon Elastic Compute Cloud (EC2) instances and workloads. The feature relies on a lightweight security agent that collects operating system events and sends them to GuardDuty for evaluation to identify potential threats. The runtime agent can identify running malicious files, can collect command arguments, and correlate multiple events to identify scenarios that present threats to your environment.
- GuardDuty EC2 Runtime Monitoring can generate runtime findings aligned with MITRE ATT&CK tactics, and the findings can be consumed through the AWS Management Console for GuardDuty, or through AWS Security Hub. The detailed findings are intended to help you understand the threat and plan your response. GuardDuty Runtime Monitoring currently supports 41 finding types, with five new finding types introduced with the release of EC2 Runtime Monitoring.
- GuardDuty EC2 Runtime Monitoring relies on a lightweight security agent that sends operating system events to GuardDuty. The events are thoroughly evaluated to identify potential threats to the associated EC2 instance. Five new finding types are supported by the agent, which include Execution:Runtime/SuspiciousTool, Execution:Runtime/SuspiciousCommand, DefenseEvasion:Runtime/SuspiciousCommand, DefenseEvasion:Runtime/PtraceAntiDebugging, and Execution:Runtime/MaliciousFileExecuted.
- GuardDuty Runtime Monitoring is the latest addition to AWS customers’ managed threat detection capabilities. Runtime Monitoring enables GuardDuty to provide operating system insight to detect possible threats to workloads running on AWS by utilizing the new capabilities of the security agent. GuardDuty has expanded its coverage across AWS resources, providing comprehensive compute coverage for GuardDuty across containers and EC2 instances.
- GuardDuty EC2 Runtime Monitoring has several deployment strategies. Customers can use managed installation, tag-based installation, or manual installation techniques. Each installation option is tailored to accommodate the various strategies for deploying and maintaining instances in your environment.
- GuardDuty doesn't charge customers for processing VPC flow logs while the runtime agent is active on an instance. When exploring the Runtime Monitoring feature, it's essential to understand that the foundational level of protection for your account and workloads is still present. GuardDuty processes VPC Flow Logs and DNS logs data for each instance, providing substantial defense-in-depth protection for detecting threats.
- The GuardDuty security agent can generate findings more quickly than that of processing log sources such as VPC Flow Logs and DNS logs. GuardDuty can consume runtime-related findings within a few minutes compared to the 15 minutes for log file-based findings.
- With runtime findings, it's best to enable an event-based response that can be invoked once the runtime finding is generated. Response to findings can involve sending to an AWS target service, such as AWS Lambda function, AWS Systems Manager runbook, or AWS service for further evaluation and remediation. AWS customers can investigate runtime findings in the GuardDuty or Security Hub console, research the details and formulate a response to remediate the finding.
- GuardDuty EC2 Runtime Monitoring is an essential security feature that provides customers with managed threat detection on their AWS accounts and workloads for comprehensive compute coverage in targeting threats across containers, EC2 instances, Amazon Elastic Kubernetes Service, and Amazon Elastic Container Service on Fargate.
- GuardDuty EC2 Runtime Monitoring is designed to analyze and capture operating system events to detect threats. The service provides detailed findings and insights for focused operational response and management. Use runtime monitoring in GuardDuty to get a better understanding of how to implement EC2 Runtime Monitoring for your instances and enhance your security posture.
Read Full Article
11 Likes
Sentinelone
411

Image Credit: Sentinelone
LABScon 2024 | Security Research in Real Time – Talks Not to Miss
- LABScon 2024 is a cybersecurity conference focused on showcasing the latest in threat hunting techniques, cutting-edge research, and new vulnerabilities, exploits, and tooling.
- LABScon 2024 will feature leading experts, threat investigators, academics, government partners, and journalists.
- The event will take place from September 18th to 21st at the Mountain Shadows Resort in Scottsdale, Arizona.
- The event will provide valuable context for defenders to enhance their cyber threat intelligence (CTI) collection efforts by exploring China’s CTF landscape.
- A talk on UNC4221’s espionage for Military Advantage will examine the group's efforts to gather battlefield data through Android malware, phishing attacks posing as Ukrainian military apps, and targeting messaging platforms like Telegram and WhatsApp.
- Another talk will discuss the rising trend of foreign investment in U.S. agricultural land and its impact on national security, particularly with controversial land purchases near sensitive military sites.
- PKFAIL is a critical firmware supply-chain issue affecting hundreds of devices that allows attackers to bypass Secure Boot and launch firmware-level threats, like bootkits and BlackLotus malware.
- A talk on unearthing the archaic will focus on long-standing vulnerabilities in SSL VPNs, which are frequently exploited through known CVEs and zero-day attacks.
- Another talk will explore a cutting-edge technique using SSH public keys to track and correlate malicious activities across different systems.
- A talk will focus on UNC1860, a covert Iranian state-sponsored threat actor, to reveal their full scope and operations across the Middle East.
Read Full Article
24 Likes
Securityintelligence
362

Image Credit: Securityintelligence
Cybersecurity risks in healthcare are an ongoing crisis
- Healthcare providers are at risk of cyberattacks due to the lack of diligence in securing their medical devices, which are critical for patient care. Several healthcare providers have experienced cybersecurity breaches this year, compromising vast amounts of electronic personal health information. Medical devices have become a vital entry point for hackers. Many older devices still in use were not designed with cybersecurity in mind and run outdated software, introducing vulnerable points of entry. There is still inconsistent compliance with medical device regulations from manufacturers and healthcare providers alike. Healthcare providers can significantly improve medical device security by implementing cybersecurity best practices and leveraging the power of gen AI to improve the quality of patient care.
- A lack of secure-by-design principles introduces vulnerabilities to hospital networks, which comprise interconnected medical devices. The total number of worldwide hospitals is set to reach 166,548 by 2029, with an estimated 1.67 million connected medical devices in circulation, emphasising the imperative for improved cybersecurity measures. The design flaws of medical devices can pose a severe risk, owing to lack of regulation in the area. Medical devices such as insulin pumps, MRI machines, infusion pumps, pacemakers, and unpatched nurse call system hardware are critical ransomware targets. Healthcare providers can improve cybersecurity by implementing gen AI-driven threat analysis, patch management, incident response systems, and compliance monitoring.
- Medical devices are complex systems that can be difficult to secure because of their multiple components, interfaces and connectivity options. Although the FDA has made significant efforts in regulating medical devices, compliance remains inconsistent. Many older devices still in use were not designed with cybersecurity in mind. Hackers are now targeting these medical devices, putting the safety of patients at risk. Legacy devices often run outdated software, which presents a vulnerable interface for attackers to manipulate. Medical devices that have unsecured interfaces, inadequate security protocols, lack of cyber expertise, and limited end-to-end visibility across supply chains, create a significant risk to healthcare providers.
- Medical device security can be enhanced by employing AI-assisted vulnerability assessments to mitigate security risks, employing AI-based cybersecurity training for healthcare providers, conducting AI-driven patch management systems, and ensuring the most critical vulnerabilities are patched first. Along with their efforts towards Medical device security, healthcare providers should ensure adherence to HIPAA and other regulatory standards, as well as implement threat intelligence to analyse large amounts of data and detect and respond to potential threats.
- Ransomware attacks are on the rise, threatening the healthcare industry that relies on the digital connectivity of medical devices. With approximately 10 to 15 medical devices per bed, much like gen AI, cybersecurity measures will grow to be integrated if the industry is to continue caring for patients safely and securely. It is imperative that medical device hardware and software are secure, reliable, tested against failure and institutionalised adherence to cybersecurity measures where possible. Improving cybersecurity in healthcare environments will not only protect patient data but also safeguard patient care from potentially life-threatening interruptions caused by cyberattacks.
Read Full Article
21 Likes
Metaoption
453

Image Credit: Metaoption
How to Improve Compliance with a Document Management Solution?
- Businesses face common challenges in document management compliance, such as meeting legal, regulatory, and operational requirements for handling sensitive or critical information.
- A Document Management Solution, i.e., MetaDocs, plays an important role for businesses in improving compliance by digitizing, organizing, and automating documents.
- The document management solution helps improve compliance through centralized storage and accessibility, automated document retention policies, restricting document access, regulatory updates and workflow automation, and audit trails and version control.
- In a world with increased regulation, a Document Management Solution provides full compliance management, document security, automation, and audit trails, decreasing the possibility of risk and increasing organizational effectiveness.
Read Full Article
27 Likes
Hackersking
164

Image Credit: Hackersking
Best 10 Open Source Malware Analysis Tools for Cybersecurity Researchers
- Open-source tools for malware analysis have become essential allies in the ongoing battle against cyber threats.
- Malware is any software designed to cause damage, theft of sensitive data, or unauthorized access to a computer system.
- Malware analysis is the process of examining and understanding malware behaviors to identify vulnerabilities and mitigate risks.
- There are two main types of malware analysis: static and dynamic.
- Cuckoo Sandbox is an advanced open-source malware analysis system that analyzes suspicious files in a sandboxed environment.
- YARA is a powerful open-source tool that helps track malware based on predefined rules.
- Ghidra is a comprehensive reverse-engineering tool that analyzes malicious code and malware.
- VirusTotal is a free online service that analyzes files and URLs for viruses, trojans, and other malicious content.
- Wireshark captures and interactively analyzes network traffic, making it an essential tool for network analysis and troubleshooting.
- Volatility is a memory forensics framework used for incident response and malware analysis by allowing analysts to extract data from RAM dumps.
Read Full Article
9 Likes
Kaspersky
256

Image Credit: Kaspersky
SambaSpy, a new RAT | Kaspersky official blog
- SambaSpy is a new RAT Trojan discovered by Kaspersky.
- It is obfuscated using Zelix KlassMaster, making it difficult to detect.
- SambaSpy can manage files, control webcams, steal passwords, and more.
- The attackers behind SambaSpy are targeting victims in Italy.
Read Full Article
15 Likes
For uninterrupted reading, download the app