Hacking News
Securityaffairs
272

Image Credit: Securityaffairs
Operation Secure: INTERPOL dismantles 20,000+ malicious IPs in major cybercrime crackdown
- INTERPOL conducted Operation Secure, targeting malicious IPs tied to info-stealing malware.
- The operation, held from January to April 2025, involved 26 countries and partners like Group-IB, Kaspersky, and Trend Micro.
- 20,000+ malicious IPs/domains were dismantled, with 41 servers seized and 32 arrests made.
- Authorities alerted over 216,000 victims for securing accounts after the operation.
- Vietnam, Sri Lanka, Nauru, and Hong Kong were among the countries where arrests and seizures took place.
- Vietnam arrested 18 suspects, Sri Lanka and Nauru made 14 arrests, and Hong Kong Police exposed phishing servers.
- INTERPOL emphasized the importance of collaborative action against cyber threats during Operation Secure.
Read Full Article
16 Likes
Securityaffairs
437

Image Credit: Securityaffairs
Over 80,000 servers hit as Roundcube RCE bug gets rapidly exploited
- A critical remote code execution (RCE) vulnerability in Roundcube, tracked as CVE-2025-49113, was exploited by threat actors just days after the patch release, affecting over 80,000 servers.
- Roundcube, a popular webmail platform, has been targeted by advanced threat groups in the past, exploiting vulnerabilities for stealing login credentials and spying on communications.
- The vulnerability, with a CVSS score of 9.9, was discovered by Kirill Firsov and allows attackers to run malicious code on affected systems.
- The flaw in Roundcube Webmail before versions 1.5.10 and 1.6.x was found in the program/actions/settings/upload.php file.
- The vulnerability has been patched in versions 1.6.11 and 1.5.10 LTS.
- Approximately 53 million hosts, including systems like cPanel, Plesk, ISPConfig, and DirectAdmin, are impacted by the flaw.
- Positive Technologies researchers have confirmed the exploitability of CVE-2025-49113 in Roundcube and advise immediate updating to the latest version.
- The Shadowserver Foundation noted that around 84,000 unpatched Roundcube instances are exposed on the Internet, posing a significant risk.
- Data from Shadowserver indicates that over 84,000 Internet-facing servers are still vulnerable to the RCE flaw in Roundcube.
- The vulnerability has been a target for possible state actors in targeted attacks, emphasizing the critical need for patching.
- The situation underscores the importance of prompt software updates to mitigate cybersecurity risks and protect against potential exploitation.
- Users are urged to follow security recommendations and apply patches promptly to safeguard their systems and data.
- The security community continues to monitor the situation closely and raise awareness about the implications of unpatched vulnerabilities.
- For further updates, follow security experts on Twitter: @securityaffairs and Facebook for the latest cybersecurity news.
- Stay informed about emerging threats and best practices in cybersecurity to enhance digital defense measures.
Read Full Article
26 Likes
Securityaffairs
66

Image Credit: Securityaffairs
A flaw could allow recovery of the phone number associated with any Google account
- A vulnerability was discovered that could potentially allow for the recovery of the phone number associated with any Google account through a brute force attack.
- The flaw was found in a deprecated, JavaScript-disabled version of Google's username recovery page that lacked anti-abuse protections.
- By bypassing CAPTCHA rate limits and using BotGuard tokens, an attacker could rapidly test combinations of a user's phone number, revealing recovery details linked to a Google account display name.
- After reporting the issue to the vendor, a reward was given to the security researcher, and mitigations were rolled out to address the vulnerability.
Read Full Article
4 Likes
Idownloadblog
317

Image Credit: Idownloadblog
Nugget and Pocket Poster work on iOS 26 as developer updates Nugget to version 5.2.3
- Nugget developer LeminLimez introduced Pocket Poster add-on for iPhones running iOS 17.0 and above, allowing users to apply custom community-made animated wallpapers.
- Pocket Poster requires Nugget SparseRestore exploit at least once to initialize and Nugget version 5.2.3 to operate. Several changes were included in Nugget v5.2.3 release.
- The Pocket Poster helper button was added in the update to allow easy setup. Both Nugget and Pocket Poster are confirmed to work with iOS & iPadOS 26 according to the developer.
- It is recommended to revert resolution changes before updating to iOS & iPadOS 26 to avoid issues with existing wallpapers. Users can download the latest Nugget version from GitHub and use it alongside iOS & iPadOS 26 beta.
Read Full Article
19 Likes
Securityaffairs
50

Image Credit: Securityaffairs
Texas Department of Transportation (TxDOT) data breach exposes 300,000 crash reports
- Hackers breached Texas DOT (TxDOT), stealing 300,000 crash reports with personal data from its Crash Records Information System (CRIS).
- Threat actors compromised the CRIS system, leading to unauthorized access and download of crash reports containing personal information.
- TxDOT, as a state agency managing transportation systems in Texas, oversees various functions, including traffic safety and crash data management through CRIS.
- Following the breach, TxDOT disabled the compromised account, initiated an investigation, and is enhancing security measures to prevent future incidents.
Read Full Article
2 Likes
Securityaffairs
169

Image Credit: Securityaffairs
SAP June 2025 Security Patch Day fixed critical NetWeaver bug
- SAP released a security patch in June 2025 to fix a critical vulnerability in the NetWeaver framework that allowed attackers to bypass authorization checks and escalate privileges.
- The vulnerability, tracked as CVE-2025-42989 with a CVSS score of 9.6, could impact the integrity and availability of the application by letting authenticated attackers escalate privileges.
- The flaw was found in SAP's Remote Function Call (RFC) framework, enabling attackers to bypass checks and escalate privileges, posing risks to app integrity and availability.
- In addition to the critical NetWeaver bug, the June 2025 Security Patch addressed a total of five high-severity flaws and several other medium to low-severity vulnerabilities.
Read Full Article
10 Likes
Securityaffairs
380

Image Credit: Securityaffairs
U.S. CISA adds RoundCube Webmail and Erlang Erlang/OTP SSH server flaws to its Known Exploited Vulnerabilities catalog
- U.S. CISA adds RoundCube Webmail and Erlang Erlang/OTP SSH server flaws to its Known Exploited Vulnerabilities catalog.
- CVE-2025-32433 is a critical flaw impacting older versions of Erlang/OTP SSH server, leading to remote code execution.
- CVE-2024-42009 is a critical XSS vulnerability in RoundCube Webmail software, allowing malicious email-based attacks.
- CISA has ordered federal agencies to fix these vulnerabilities by June 30, 2025, to protect against potential exploitation.
Read Full Article
22 Likes
Securityaffairs
106
Image Credit: Securityaffairs
Mirai botnets exploit Wazuh RCE, Akamai warned
- Akamai researchers warned that multiple Mirai botnets are exploiting the critical remote code execution vulnerability CVE-2025-24016 in Wazuh servers.
- The vulnerability allows for remote code execution on Wazuh servers, and active exploitation of the flaw has been observed via DAPI request abuse.
- Two Mirai botnet variants named 'Resbot' have been exploiting this bug since March 2025, utilizing Italian domain names and targeting IoT devices.
- Indicators of compromise and details on the exploitation of the Wazuh servers by Mirai botnets have been shared by Akamai researchers.
Read Full Article
5 Likes
Securityaffairs
14
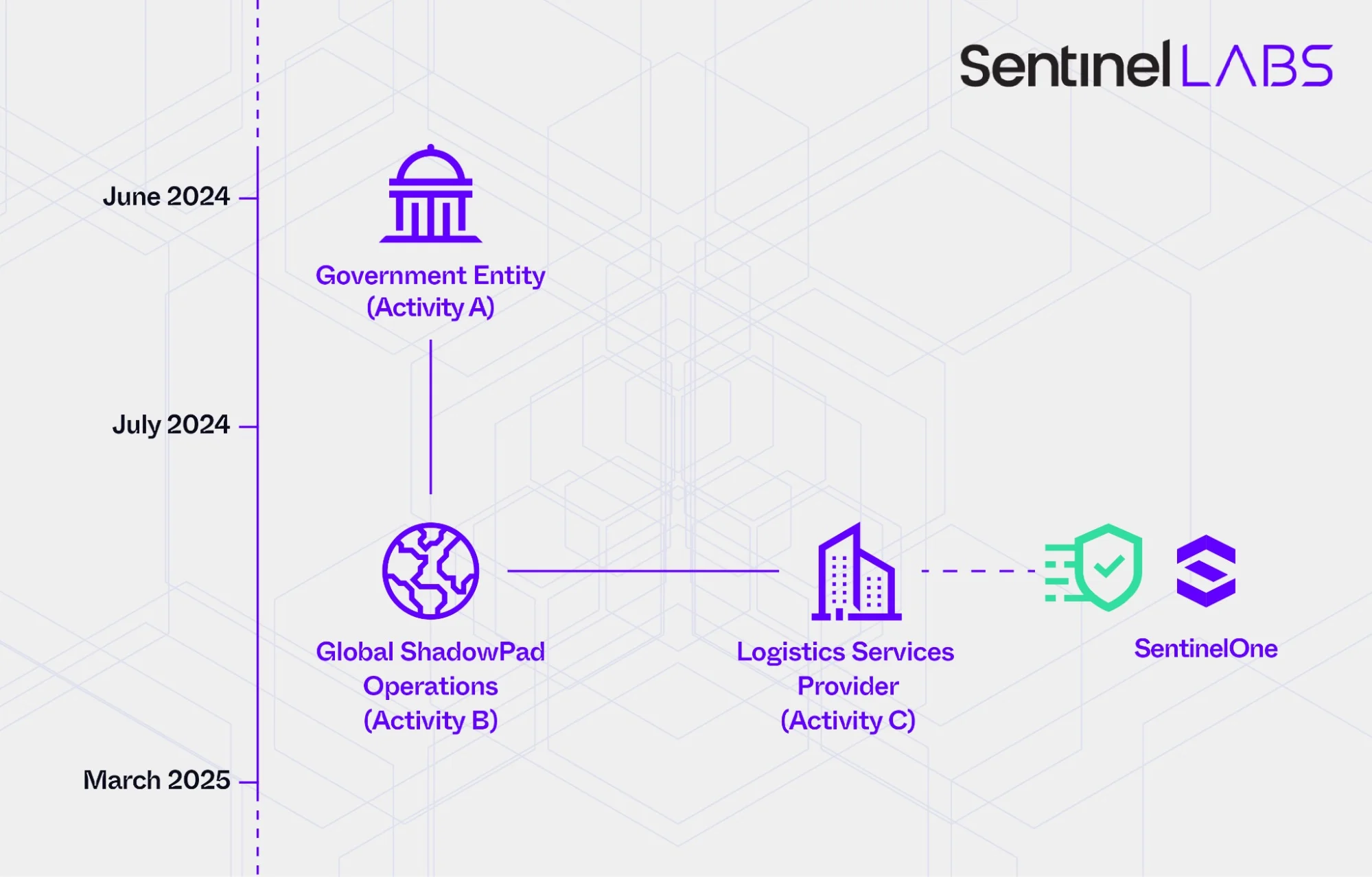
Image Credit: Securityaffairs
China-linked threat actor targeted +70 orgs worldwide, SentinelOne warns
- China-linked threat actor, PurpleHaze, targeted over 70 global organizations, including governments and media, in cyber-espionage attacks between July 2024 and March 2025.
- SentinelOne warns of targeted reconnaissance efforts by PurpleHaze to gather information for potential future attacks, with tactics and tools linked to APT15.
- The attacks used an Operational Relay Box network and a Windows backdoor called GoReShell, aligning with broader Chinese APT patterns.
- Focus on cybersecurity firms highlights the need for constant vigilance, monitoring, and rapid response capabilities to counter evolving threats.
Read Full Article
Like
Securityaffairs
192

Image Credit: Securityaffairs
DOJ moves to seize $7.74M in crypto linked to North Korean IT worker scam
- The US Department of Justice (DoJ) has filed a civil forfeiture complaint to seize $7.74 million in crypto connected to North Korean fake IT worker schemes.
- The frozen assets include cryptocurrency, NFTs, and other digital assets tied to the indictment of North Korean Foreign Trade Bank representative Sim Hyon Sop.
- North Korean IT workers obtained illegal employment to amass millions in cryptocurrency, evading US sanctions.
- These workers used fake IDs and deceptive tactics to hide their identities while gaining remote jobs in blockchain firms, paid in stablecoins unknowingly supporting North Korea's revenue stream.
- Illicit gains were laundered through various means and funneled back to the regime, including using US accounts to mask their origins.
- The US authorities unsealed charges against individuals aiding overseas IT workers to defraud US companies, with North Korea dispatching IT workers globally using stolen US identities.
- The operations financed North Korea's illicit nuclear program, highlighting the country's exploitation of global remote IT contracting and cryptocurrency ecosystems to circumvent sanctions.
- Several arrests were made, including Christina Marie Chapman and Oleksandr Didenko, facing charges related to fraud, money laundering, and unlawful employment.
- Additionally, Matthew Isaac Knoot was arrested for aiding North Korean IT workers, hosting company laptops and laundering payments, contributing to North Korea's illicit weapons program.
- Knoot and his associates caused targeted companies over $500,000 in costs. If convicted, Knoot could face a maximum of 20 years in prison.
Read Full Article
11 Likes
TechCrunch
322

Image Credit: TechCrunch
Paragon says it canceled contracts with Italy over government’s refusal to investigate spyware attack on journalist
- Spyware maker Paragon canceled contracts with Italy over the government's refusal to investigate a journalist's spyware attack.
- Paragon claims it offered a solution for Italy to determine if its system was used against the journalist but terminated contracts when Italian authorities did not proceed with it.
- The Italian government rebuffed Paragon's remarks, stating the decision to suspend and terminate the contract was mutual, citing concerns over national security and confidentiality.
- The spyware scandal involves Paragon, WhatsApp, and Italian intelligence agencies, with ongoing investigations and disputes regarding targeted individuals and their activities.
Read Full Article
19 Likes
Securityaffairs
353

Image Credit: Securityaffairs
OpenAI bans ChatGPT accounts linked to Russian, Chinese cyber ops
- OpenAI banned ChatGPT accounts connected to Russian and Chinese hackers engaging in malicious activities, including malware development, social media abuse, and U.S. satellite tech research.
- Accounts tied to Russian-speaking threat actors and two Chinese nation-state actors were blocked, with the Russian group operating under the cyber operation called ScopeCreep, focusing on stealthy malware distribution and C2 infrastructure.
- OpenAI collaborated with industry partners to detect and ban these malicious accounts early on, preventing widespread impact and disrupting operations like ScopeCreep, Helgoland Bite, Sneer Review, VAGue Focus, VIXEN PANDA, KEYHOLE PANDA, and Operation Uncle Spam.
- The report highlights the varied global origins of such malicious operations, with notable cases possibly originating from China, in addition to instances from countries like Cambodia, the Philippines, Russia, and Iran.
Read Full Article
21 Likes
Hackingblogs
120

Image Credit: Hackingblogs
A Secret Hacker GangExposed Is Exposing the Real Names of the World’s Most Dangerous Ransomware Criminals : Complete Detailed Article
- An anonymous hacker, known as GangExposed, has leaked sensitive information about top ransomware groups such as Conti, revealing real names and profile pictures of members.
- GangExposed, an independent investigator with no professional IT training, claims to have obtained data from darknet sites and state records with dishonest insiders.
- The hacker exposed the real identity of Vitaly Nikolaevich Kovalev, the leader of Conti ransomware group, linking him to other cybercrime organizations like Royal and Trickbot.
- GangExposed's detailed investigation uncovered Kovalev's role as the mastermind behind various ransomware gangs, coordination of attacks, money laundering networks, and technical infrastructure.
Read Full Article
7 Likes
TheNewsCrypto
394

Alex Protocol Launches Treasury Grant After $8.3M Hack
- Alex Protocol launches Treasury Grant Program to reimburse users affected by an $8.3 million hack on June 6. The grants provide compensation in a combination of actual tokens and USDC equivalents based on the type of asset lost.
- Impacted users can link their affected wallets to the official grant interface, review their compensation offers, and accept terms by signing an authentication message.
- Reimbursement structure includes complete USDC compensation for STX holdings, 100% reimbursement in aBTC, and 91% reimbursement in aUSD, with the remainder in USDC at parity. Support payments will be made to eligible Ethereum addresses by June 17.
- A community member speculates the hack may be related to a Stacks limitation. An earlier update mentioned payout amounts depend on average on-chain prices observed from 10:00 am to 2:00 pm UTC during the incident.
Read Full Article
23 Likes
Securelist
282

Image Credit: Securelist
Sleep with one eye open: how Librarian Ghouls steal data by night
- Librarian Ghouls, also known as “Rare Werewolf” and “Rezet”, is an APT group targeting entities in Russia and the CIS with a preference for legitimate third-party software.
- The attackers use phishing emails with password-protected archives containing malicious files disguised as official documents to infect victims.
- Upon infection, the attackers establish remote access using tools like AnyDesk and deploy an XMRig crypto miner to mine cryptocurrency.
- The attackers utilize various legitimate utilities like Blat, cuRL, and NirCmd for malicious activities, making detection challenging.
- The attackers leverage tools like Mipko Personal Monitor and WebBrowserPassView to monitor victims and steal credentials.
- Phishing campaigns by Librarian Ghouls target Russian users and industrial enterprises, with infrastructure linked to command-and-control servers downdown[.]ru and dragonfires[.]ru.
- The attackers install a crypto miner, collect data like cryptocurrency wallet credentials, and use legitimate software like AnyDesk for remote access.
- Librarian Ghouls show traits of hacktivist groups, constantly updating their implants and utilizing over 100 malicious files in their campaigns.
- The article emphasizes the importance of monitoring and sharing information on this active APT group for better protection against their evolving tactics.
- The summary covers the technical details of Librarian Ghouls' attack methods, infrastructure, victims, and indicators of compromise related to their ongoing campaigns.
Read Full Article
16 Likes
For uninterrupted reading, download the app