Hacking News
Securityaffairs
300
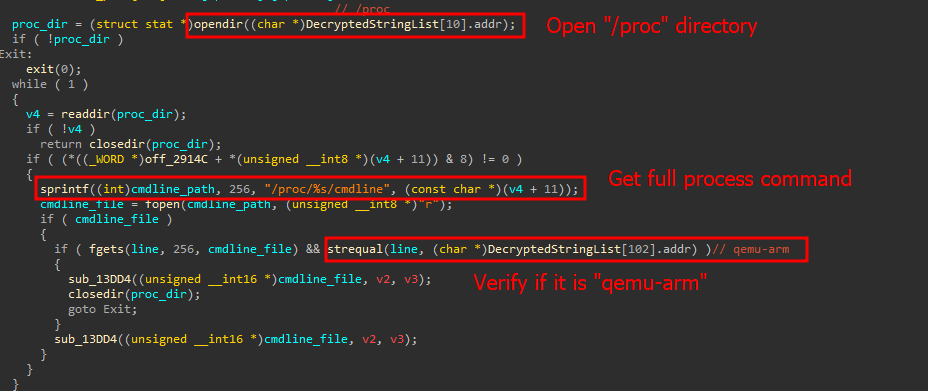
Image Credit: Securityaffairs
New Mirai botnet targets TBK DVRs by exploiting CVE-2024-3721
- A new variant of the Mirai botnet exploits CVE-2024-3721 to target DVR systems.
- The variant uses a command injection vulnerability in TBK DVR-4104 and DVR-4216 devices to execute malicious commands.
- This Mirai variant includes new features like RC4 string encryption and anti-virtual machine checks.
- Over 50,000 exposed DVRs have been found as potential targets in countries like China, India, Egypt, Ukraine, Russia, Turkey, and Brazil.
Read Full Article
18 Likes
Securityaffairs
0

Image Credit: Securityaffairs
BadBox 2.0 botnet infects millions of IoT devices worldwide, FBI warns
- BadBox 2.0 malware infects millions of IoT devices globally, forming a botnet for cyber criminal activities, as warned by the FBI.
- FBI issues a Public Service Announcement (PSA) highlighting the use of the BADBOX 2.0 botnet by cybercriminals to exploit IoT devices, predominantly made in China.
- The malware gains unauthorized access to devices, targeting Android devices and compromising home networks to become part of the BADBOX 2.0 botnet for illicit purposes.
- FBI advises checking IoT devices for compromise signs, disconnecting suspicious ones, monitoring network traffic, avoiding unofficial app stores, and promptly patching vulnerabilities to mitigate risks.
Read Full Article
Like
Idownloadblog
107

Image Credit: Idownloadblog
Hacker publishes steps to upgrade unsupported iPad (6th generation) to iPadOS 18
- Hacker Nick Chan shared steps to upgrade unsupported iPad (6th generation) to iPadOS 18 via GitHub.
- The process is complicated and involves a series of Terminal commands.
- Drawbacks include it being a tethered process, Lightning and VGA adapters not working, wasted storage space, and limitations on Camera app and settings feature.
- The motivation behind attempting this upgrade is to potentially jailbreak the iPad (6th generation) on iPadOS 18, making it the second-supported iPad for such an action.
Read Full Article
6 Likes
Idownloadblog
62

Image Credit: Idownloadblog
Security researcher wh1te4ever demos WebKit-based re-jailbreak utility for iOS 12
- Security researcher @wh1te4ever demonstrated a WebKit-based re-jailbreak utility for iOS 12 devices.
- The demo showed an iPhone 5s running iOS 12.5.7 being re-jailbroken using a WebKit exploit triggered via Safari.
- The proof-of-concept currently supports only the iPhone 5s with firmware 12.5.7 and needs updating for more device and firmware combinations.
- There is no set release date for this tool, and it's uncertain if it will be made available to the public.
Read Full Article
3 Likes
Hackingblogs
345

Image Credit: Hackingblogs
Delete These 20 Google Play Apps RIGHT NOW – They’re Stealing Your Crypto Keys, Research Reveals!
- A recent CYBLE research identified more than 20 fake apps on the Google Play Store that were stealing Crypto Keys by impersonating popular wallets like SushiSwap, PancakeSwap, Hyperliquid, and Raydium.
- These malicious apps used phishing techniques to deceive users into entering a 12-word mnemonic phrase to access fake wallet interfaces, posing a significant threat to users' cryptocurrency security.
- The hacker-controlled apps disguised themselves using stolen developer accounts, making it challenging for users to differentiate between legitimate and fake applications.
- The malicious apps were found to use multiple deceptive strategies, including Command and Control URLs in their privacy policies, to remotely manage the stolen Crypto Keys and increase the difficulty of detection.
Read Full Article
20 Likes
Securityaffairs
233

Image Credit: Securityaffairs
Over 950K weekly downloads at risk in ongoing supply chain attack on Gluestack packages
- A supply chain attack targeted NPM, compromising 16 popular Gluestack 'react-native-aria' packages with over 950K weekly downloads.
- The attack involved injecting malicious code with Remote Access Trojan (RAT) capabilities into packages' files, affecting 16 out of 20 packages.
- Approximately 960,000 weekly downloads were affected by the compromised packages, and researchers believe the same threat actors were behind a previous attack on the 'rand-user-agent' package.
- Aikido Security attempted to notify Gluestack about the ongoing supply chain attack but has not received a response yet, urging users to stay updated on the situation.
Read Full Article
14 Likes
Securityaffairs
201

Image Credit: Securityaffairs
Security Affairs newsletter Round 527 by Pierluigi Paganini – INTERNATIONAL EDITION
- Security Affairs newsletter Round 527 by Pierluigi Paganini – INTERNATIONAL EDITION
- 4 billion Chinese user records leaked in the largest known data breach. Fortinet flaws exploited to deploy Qilin ransomware. Russia-linked threat actors target Ukraine with PathWiper wiper. U.S. offers $10M bounty for RedLine malware info.
- Multiple cyber attacks reported worldwide. U.S. seizes criminal marketplace domains. Ransomware gang claims responsibility for Kettering Health hack. Cyber criminals defraud Hedera Hashgraph network users. Malware exploits and vulnerabilities identified.
- Intelligence and Information Warfare updates include Ukraine hacking Tupolev and DOJ accusations against Chinese researchers. Cybersecurity incidents such as Victoria's Secret security breach and largest data leak of 4 billion user records.
- AI and cybersecurity advancements highlighted in EU initiative and increase in cyber attacks with AI involvement. Ongoing developments in digital certificate security and threat actor collaboration.
Read Full Article
12 Likes
Medium
90
Image Credit: Medium
When Deleted Isn’t Gone — Privacy Risks in Electronics Repair
- The electronics repair industry, valued at around $19 billion globally, lacks sufficient regulatory oversight on customer privacy, leading to data exploitation risks.
- Recent research indicates that repair technicians frequently access and even share customers' private data, such as personal photos and videos, despite it being unnecessary for the repair task.
- Customers' assumption of deleted files being permanently erased is debunked, as skilled technicians can easily recover such data due to the technical aspects of data storage.
- Various studies highlight a high incidence of privacy violations within the electronics repair sector, with a significant percentage of technicians found to snoop on data or copy it without consent.
Read Full Article
5 Likes
Securityaffairs
152

Image Credit: Securityaffairs
Experts found 4 billion user records online, the largest known leak of Chinese personal data from a single source
- Over 4 billion user records were found exposed online in a massive breach linked to the surveillance of Chinese citizens.
- Cybersecurity researchers discovered a 631GB unsecured database containing around 4 billion records, mainly involving Chinese users, potentially used for profiling and surveillance purposes.
- The leaked data included information from WeChat, Alipay, and other sources, posing serious risks of phishing, fraud, blackmail, and state-backed intelligence activities.
- This incident represents the largest known leak of Chinese personal data from a single source, with affected individuals having no clear way to respond.
Read Full Article
9 Likes
Idownloadblog
341

Image Credit: Idownloadblog
Aquila untethered jailbreak for iOS 6 devices uses a newer, faster kernel exploit than previous options
- Aquila is a new untethered jailbreak tool by iOS developer staturnz for iOS 6 devices.
- The jailbreak utilizes a faster and more reliable kernel exploit named bad_queue compared to other iOS 6 jailbreaks.
- Aquila runs in a Terminal window and requires following text prompts for the jailbreaking process.
- This tool targets older devices running iOS 6 and is aimed at hobbyists interested in jailbreaking for tinkering purposes.
Read Full Article
20 Likes
Securityaffairs
381
Image Credit: Securityaffairs
Attackers exploit Fortinet flaws to deploy Qilin ransomware
- Qilin ransomware is now exploiting Fortinet vulnerabilities, including CVE-2024-21762 and CVE-2024-55591, for remote code execution.
- The ransomware group has been active since August 2022 and gained attention in 2024 for attacking Synnovis, a UK healthcare service provider.
- Threat actors are actively exploiting Fortigate vulnerabilities to deploy Qilin ransomware, with the attack being fully automated.
- Despite initially targeting Spanish-speaking countries, experts warn that the Qilin ransomware group could expand globally and is capable of independent intrusion operations.
Read Full Article
22 Likes
TechCrunch
76

Image Credit: TechCrunch
Italian lawmakers say Italy used spyware to target phones of immigration activists, but not against journalist
- Italian lawmakers confirm Italy used Paragon spyware to target immigration activists but not a journalist, as concluded by a parliamentary committee's report.
- The report raised key questions about the spyware attacks, with the investigation leaving many aspects unanswered.
- WhatsApp notifications in January alerted 90 users, leading to revelations and a scandal in Italy regarding spyware use.
- Italian nonprofit activists were found to have been targeted lawfully by intelligence agencies for alleged illegal immigration facilitation.
- No evidence was found of journalist Francesco Cancellato being targeted by Italy's intelligence agencies, as per the COPASIR committee.
- Paragon's foreign government customers and unanswered questions about the journalist targeting leave scope for further investigation.
- Cancellato, a journalist, and director of Fanpage.it, doubted COPASIR's conclusions and sought explanations.
- COPASIR's report disclosed new details on Paragon's spyware operations and the relationships with Italian intelligence agencies.
- The report indicated legal approval for spyware deployments by Italian intelligence agencies AISE and AISI.
- Paragon's contracts reportedly contain clauses prohibiting spyware use against journalists and human rights activists.
Read Full Article
4 Likes
Securityaffairs
188

Image Credit: Securityaffairs
Russia-linked threat actors targets Ukraine with PathWiper wiper
- A Russia-linked threat actor targeted a critical infrastructure organization in Ukraine with a destructive malware named PathWiper, according to Cisco Talos researchers.
- The attackers utilized a legitimate endpoint administration tool to deploy the PathWiper wiper, indicating access to the administrative console.
- PathWiper is a destructive malware that overwrites disk artifacts and files with random data, targeting NTFS structures and dismounting volumes before wiping.
- Russia-linked APT groups have carried out multiple wiper campaigns against critical organizations in Ukraine, using various wipers in attacks.
Read Full Article
11 Likes
Kotaku
327

Image Credit: Kotaku
The Teen Who Hacked Elon Musk And PlayStation Network Is Getting A Docuseries
- A docuseries is being released about the teenage hacker who hacked Elon Musk's Twitter account and shut down the PlayStation Network.
- The docuseries, titled 'Most Wanted Teen Hacker', will explore the cyber exploits of the Finnish hacker Julius Kivimäki, resembling Mr. Robot's theatrics.
- Kivimäki, now incarcerated for various cybercrimes, triggered a U.S. Air Force alert and engaged in 'swatting' FBI agents, ultimately receiving a six-year prison sentence.
- The series will feature victims of Kivimäki's hacks, fellow hackers, law enforcement, and Kivimäki himself, offering a deep dive into his criminal activities and mindset.
Read Full Article
19 Likes
Securityaffairs
224
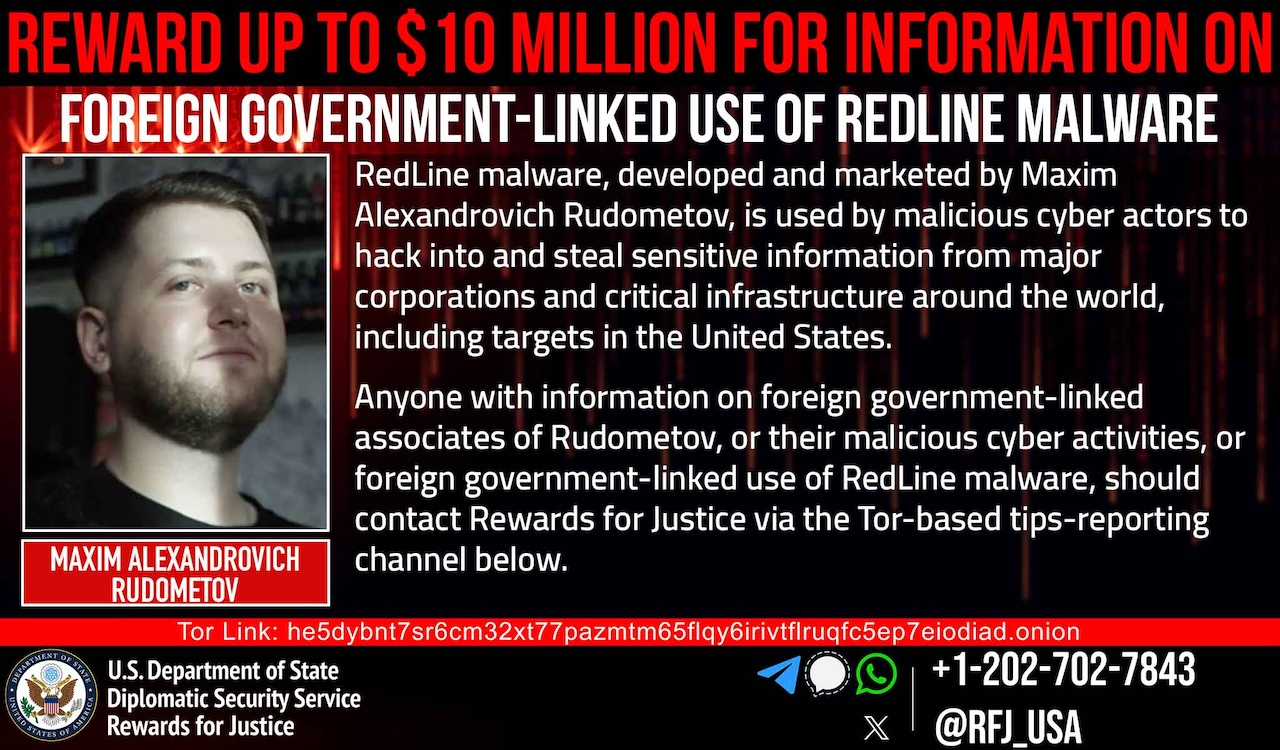
Image Credit: Securityaffairs
U.S. Offers $10M bounty for info on RedLine malware creator and state hackers
- The U.S. is offering up to $10 million for information on state hackers tied to the RedLine malware and its creator, Maxim Rudometov, associated with attacks on U.S. infrastructure.
- Maxim Rudometov, a Russian national, developed the information stealer malware RedLine and is being sought by U.S. authorities for cyber operations on critical infrastructure in the U.S.
- The reward is part of the US Department of State's Rewards for Justice program aiming to deter foreign government hackers targeting U.S. entities.
- An international operation led by Eurojust dismantled the RedLine and META malware infrastructure, affecting millions of victims worldwide and led to arrests in Belgium, seizure of servers in the Netherlands, and cooperation from multiple countries.
Read Full Article
13 Likes
For uninterrupted reading, download the app