Hacking News
Securelist
426
Image Credit: Securelist
Analysis of the latest Mirai wave exploiting TBK DVR devices with CVE-2024-3721
- The article discusses the exploitation of CVE-2024-3721 to deploy a Mirai bot on vulnerable DVR devices.
- CVE-2024-3721 enables execution of system commands on TBK DVRs via a specific POST request.
- The malicious POST request contains a shell script to download and execute an ARM32 binary.
- The Mirai bot variant targeting DVR devices includes features like RC4 encryption and anti-VM checks.
- RC4 key decryption is used to decrypt strings within the malware implant.
- The implant conducts checks to detect if it is running within a virtual machine environment.
- Infection statistics reveal that many infected DVR devices are located in countries like China, India, Egypt, and Ukraine.
- Over 50,000 vulnerable DVR devices have been identified online, indicating a significant attack surface.
- To mitigate such threats, updating vulnerable devices promptly and conducting factory resets for exposed devices is recommended.
- Kaspersky products detect the threat as HEUR:Backdoor.Linux.Mirai and HEUR:Backdoor.Linux.Gafgyt.
Read Full Article
25 Likes
Coinpedia
130

Image Credit: Coinpedia
$31M Bitcoin Gift to Ross Ulbricht Traced to Alphabay Dark Web Wallet
- A $31 million Bitcoin donation to Ross Ulbricht, the founder of Silk Road, has been linked to Alphabay, another dark web marketplace, raising concerns about illicit crypto flows.
- Chainalysis traced the donation to a wallet associated with Alphabay, suspecting a former vendor as the sender who likely used crypto mixing services to obscure the funds' origin.
- ZachXBT confirmed the use of mixing services including Jambler, indicating common obfuscation tactics like multiple crypto mixers and transfers through centralized exchanges.
- The incident highlights the ongoing challenges of tracing illicit crypto transactions and the support Ulbricht still receives from darknet-linked actors despite his imprisonment, emphasizing the complexities of crypto regulation.
Read Full Article
7 Likes
Coinpedia
233

Image Credit: Coinpedia
North Korea Laundered $7.7M in Crypto: DOJ Reveals
- The U.S. Department of Justice has seized over $7.74 million in cryptocurrency allegedly laundered by North Korean IT workers posing as remote employees at U.S. and international companies.
- North Korea exploited the crypto and AI boom to circumvent U.S. sanctions and finance its weapons programs, with the laundering strategy involving fake IDs, stablecoins, mixing funds, converting between tokens, buying NFTs, and using known intermediaries.
- AI tools like ChatGPT were utilized by North Korean operatives to automate job applications, fabricate employment histories, and simulate work behavior, prompting actions from OpenAI and Google to shut down related accounts.
- The seizure is part of the DOJ's efforts to disrupt North Korea's cyber-financial operations and enforce sanctions, highlighting ongoing investigations and prosecutions to counter North Korea's crypto-fueled sanctions evasion.
Read Full Article
14 Likes
Idownloadblog
431
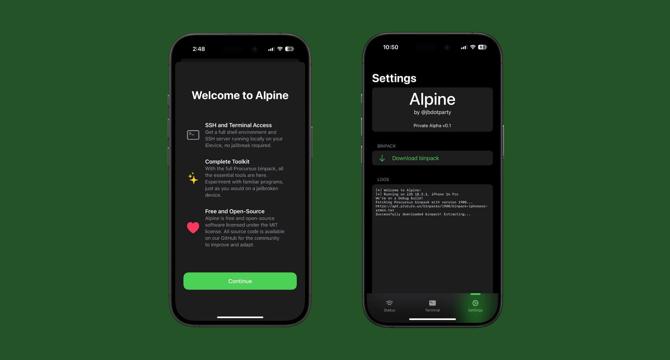
Image Credit: Idownloadblog
Alpine could one day be a CLI & SSH Server tool for iOS that doesn’t require a jailbreak
- iOS developer @skadz108 is working on a project called Alpine, which aims to be a CLI & SSH Server tool for iOS without requiring a jailbreak.
- Alpine is not a jailbreak or sideloading tool and is intended to run basic command line tools and an SSH server even on the latest iOS devices.
- The project is currently a proof-of-concept and unfinished, focusing on providing SSH and Terminal Access, a complete toolkit, and being free and open-source.
- The developer is unsure if the project will be fully realized but is exploring the possibility of implementing it for advanced users interested in iPhone and iPad customization.
Read Full Article
25 Likes
Securityaffairs
332

Image Credit: Securityaffairs
U.S. CISA adds Google Chromium V8 flaw to its Known Exploited Vulnerabilities catalog
- The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added Google Chromium V8 Out-of-Bounds Read and Write Vulnerability, CVE-2025-5419, to its Known Exploited Vulnerabilities catalog.
- Google released out-of-band updates to address three vulnerabilities in its Chrome browser, including CVE-2025-5419 that is actively exploited.
- The vulnerability in V8 JavaScript engine in Google Chrome can trigger a heap corruption via a crafted HTML page.
- CISA orders federal agencies to fix the vulnerabilities by June 26, 2025, and private organizations are advised to address vulnerabilities in their infrastructure.
Read Full Article
20 Likes
Securelist
242

Image Credit: Securelist
IT threat evolution in Q1 2025. Non-mobile statistics
- In Q1 2025, Kaspersky products blocked over 629 million attacks, with 88 million unique links detected by Web Anti-Virus.
- File Anti-Virus blocked over 21 million malicious objects, and nearly 12,000 new ransomware variants were found.
- Phobos Aetor operation led to arrests of 8Base members for cyberattacks involving Phobos ransomware.
- Law enforcement efforts resulted in extraditing a suspected ransomware developer linked to LockBit.
- New vulnerabilities in Paragon Partition Manager were exploited for BYOVD attacks in Q1.
- Akira ransomware bypassed EDR by exploiting a webcam vulnerability and using Linux-based systems.
- HellCat utilized compromised Jira credentials for attacking companies like Ascom and Jaguar Land Rover.
- Ransomware group RansomHub remained a leader in adding new victims, followed by Akira and Clop.
- Kaspersky detected three new ransomware families and 11,733 new variants, a significant increase from the previous quarter.
- 315,701 unique users worldwide were attacked by miners in Q1 2025, with various countries facing such attacks.
Read Full Article
14 Likes
Securelist
391

Image Credit: Securelist
IT threat evolution in Q1 2025. Mobile statistics
- In the first quarter of 2025, there were 12 million attacks on mobile devices involving malware, adware, or unwanted apps, with Trojans accounting for 39.56% of total threats.
- Over 180,000 malicious and unwanted installation packages were detected, including mobile bankers and ransomware Trojans.
- Attacks on Android devices surged to over 12 million, with Mamont banking Trojans and Fakemoney scam apps being major contributors.
- A new Turkish banking Trojan, Trojan-Banker.AndroidOS.Bankurt.c, was discovered, masquerading as a movie viewing app.
- The number of detected Android malware and unwanted app samples increased, with banking Trojans and spy Trojans ranking high.
- The Fakemoney apps and Mamont banking Trojan variants dominated the list of top mobile malware in Q1 2025.
- Region-specific malware targeting specific countries like Turkey and India was prominent in the first quarter of 2025.
- Mobile banking Trojans, particularly Mamont variants, saw a significant increase in installation packages and user targeting.
- The activity of Mamont banking Trojans in generating custom variants for cybercriminals led to a proliferation of distinct versions being spread.
- Various versions of Mamont dominated the top 10 mobile bankers in terms of targeting users, showcasing their prevalence.
Read Full Article
23 Likes
Hackers-Arise
395

Image Credit: Hackers-Arise
Signal Intelligence with a Software Defined Radio (SDR): The Quiet Revolution in Cybersecurity and Cyberwarfare
- Software-Defined Radio (SDR) has revolutionized communication and warfare, impacting military operations and satellite communications.
- Modern military drones like the Turkish Bayraktar TB2 and American MQ-9 Reaper utilize advanced multi-band SDR systems for enhanced capabilities.
- SDR technology allows drones to operate in multiple frequency ranges simultaneously and switch between channels seamlessly.
- The SDR systems in military drones enable features like encrypted communication links, electronic warfare capabilities, and precision attacks.
- Satellite communication systems are vulnerable to various threats, including signal interception, physical layer attacks, and command infrastructure attacks.
- Recent security incidents like the Viasat hack have prompted improvements in satellite communication security measures.
- Artificial intelligence and machine learning are being utilized in satellite security to detect and respond to evolving threats efficiently.
- SDR technology is evolving to provide better protection against jamming and interference, adapting to changing threat environments.
- The increasing role of AI, quantum computing, and SDR technology is reshaping how we interact with the electromagnetic spectrum.
- The SDR revolution offers new possibilities in cybersecurity and cyberwarfare, showcasing its potential in modern military and civilian applications.
Read Full Article
23 Likes
Securityaffairs
103

Image Credit: Securityaffairs
Law enforcement seized the carding marketplace BidenCash
- U.S. and Dutch authorities collaborated to dismantle the BidenCash cybercrime marketplace by seizing 145 associated domains.
- The U.S. Department of Justice announced the seizure of 145 darknet and clear web domains, along with cryptocurrency funds linked to BidenCash.
- BidenCash, operational since March 2022, charged a fee for transactions and distributed millions of stolen payment cards, generating around $17 million in revenue.
- Authorities shut down 145 domains related to BidenCash, redirecting them to law enforcement servers to prevent further criminal activities.
Read Full Article
6 Likes
Hackers-Arise
360

Image Credit: Hackers-Arise
BusyBox: The Swiss Army Knife of Embedded Linux
- BusyBox is a lightweight software suite known as 'The Swiss Army Knife of Embedded Linux' that combines multiple Unix utilities into a single small executable file.
- It was created in 1996 by Bruce Perens and gained traction among embedded Linux developers for its essential Unix tools in resource-constrained devices.
- BusyBox's approach combines various functionalities into one binary, providing over 300 Unix utilities in a minimal footprint, typically under 1MB.
- Advantages of BusyBox include space efficiency, memory optimization, simplified deployment, consistent behavior, customizability, and performance benefits.
- It is used in embedded systems, container environments like Alpine Linux, IoT devices, recovery systems, mobile devices, and educational environments like Raspberry Pi.
- BusyBox utilities are useful in network reconnaissance, file operations, system analysis, and text processing for penetration testing purposes.
- While generally secure, security concerns around BusyBox include firmware vulnerabilities, IoT botnet attacks, supply chain issues, and configuration complexities.
- Its embedded nature poses challenges for security updates in deployed devices, leading to persisting vulnerabilities in the devices.
- BusyBox's small size, comprehensive functionality, and reliability ensure its relevance in the embedded Linux ecosystem amidst diverse computing environments.
- As computing expands into IoT and resource-constrained systems, understanding BusyBox and Linux becomes crucial for hackers and technology enthusiasts.
Read Full Article
21 Likes
Securityaffairs
274
Image Credit: Securityaffairs
Ukraine’s military intelligence agency stole 4.4GB of highly classified internal data from Tupolev
- Ukraine’s military intelligence agency GUR hacked the Russian aerospace and defense company Tupolev, stealing 4.4GB of highly classified internal data.
- The breach exposed internal communications, staff details, engineers' resumes, procurement records, and confidential meeting minutes.
- Ukrainian intelligence source stated that nearly all of Tupolev's secrets are now exposed, impacting Russia's strategic aviation operations.
- Ukraine's GUR had monitored Tupolev's internal flow for months, defacing Tupolev's website symbolically and targeting Russia's defense industry.
Read Full Article
16 Likes
TechCrunch
225

Image Credit: TechCrunch
Ransomware gang claims responsibility for Kettering Health hack
- A ransomware gang, Interlock, has claimed responsibility for the hack on Kettering Health, a network of hospitals, clinics, and medical centers in Ohio, which forced the healthcare system to shut down all computer systems for two weeks.
- Interlock stated they stole more than 940 gigabytes of data from Kettering Health and published some of the stolen data, including private health information and employee data, on their dark web site.
- Interlock's public acknowledgment of the breach could indicate that negotiations with Kettering Health have stalled, potentially leading to the exposure of the stolen data. Kettering Health's senior vice president stated that the company did not pay any ransom to the hackers.
- Kettering Health was able to restore core components of its electronic health record system provided by Epic, marking a significant step towards normal operations post-cyberattack.
Read Full Article
13 Likes
Securityaffairs
144
Image Credit: Securityaffairs
HPE fixed multiple flaws in its StoreOnce software
- Hewlett Packard Enterprise (HPE) addressed multiple flaws in its StoreOnce data backup and deduplication solution.
- HPE released security patches for eight vulnerabilities in its StoreOnce backup solution, including remote code execution, authentication bypass, data leaks, and more.
- The vulnerabilities in HPE StoreOnce software could lead to remote code execution, disclosure of information, server-side request forgery, authentication bypass, arbitrary file deletion, and directory traversal information disclosure.
- The most severe vulnerability addressed by HPE is an Authentication Bypass issue (CVE-2025-37093) impacting all versions prior to 4.3.11, with a CVSS score of 9.8.
Read Full Article
8 Likes
Securityaffairs
22

Image Credit: Securityaffairs
Roundcube Webmail under fire: critical exploit found after a decade
- A critical flaw in Roundcube webmail software, known as CVE-2025-49113, has been discovered after being undetected for over a decade.
- This flaw allows attackers to execute arbitrary code and take control of affected systems, posing significant risks to users and organizations.
- The founder of FearsOff, Kirill Firsov, identified the vulnerability in Roundcube Webmail before version 1.5.10 and 1.6.x before 1.6.11.
- To mitigate the risk, users are advised to update their Roundcube installations to the latest version immediately.
Read Full Article
1 Like
Securityaffairs
220

Image Credit: Securityaffairs
U.S. CISA adds Multiple Qualcomm chipsets flaws to its Known Exploited Vulnerabilities catalog
- U.S. CISA added multiple Qualcomm chipset flaws to its Known Exploited Vulnerabilities catalog.
- The vulnerabilities include CVE-2025-21479, CVE-2025-21480, and CVE-2025-27038.
- Qualcomm has released patches for these vulnerabilities after limited, targeted attacks.
- CISA has ordered federal agencies to address these vulnerabilities by June 24, 2025.
Read Full Article
13 Likes
For uninterrupted reading, download the app