Hacking News
Securityaffairs
63

Image Credit: Securityaffairs
Cartier disclosed a data breach following a cyber attack
- Luxury-goods conglomerate Cartier suffered a data breach due to a cyberattack.
- The breach exposed customers' personal information like names, email addresses, and countries.
- Cartier contained the issue, enhanced system protection, and alerted authorities and impacted customers.
- This incident is a part of a series of cyberattacks on luxury fashion brands, including Adidas, Dior, and Victoria's Secret.
Read Full Article
3 Likes
Guardian
72
Image Credit: Guardian
What to do if your email account is stolen – and how to stop it happening again
- Email accounts have become essential for various online services, therefore, it is crucial to secure them.
- If your email account is stolen, promptly change your password using a familiar device and follow the account recovery process provided by the email service provider.
- If unable to recover the stolen account, create a new email account and migrate your logins to it for security reasons.
- Once regaining access to your account, set a strong, unique password, enable two-step verification, use security questions, and set up recovery options to enhance security.
Read Full Article
4 Likes
Securityaffairs
31

Image Credit: Securityaffairs
U.S. CISA adds ASUS RT-AX55 devices, Craft CMS, and ConnectWise ScreenConnect flaws to its Known Exploited Vulnerabilities catalog
- U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added ASUS RT-AX55 devices, Craft CMS, and ConnectWise ScreenConnect flaws to its Known Exploited Vulnerabilities catalog.
- ConnectWise detected suspicious activity from an advanced nation-state actor impacting a small number of its ScreenConnect customers due to CVE-2025-3935, a vulnerability that may have led to a breach.
- A new AyySSHush botnet with over 9,000 compromised ASUS routers exploits an authenticated command injection flaw (CVE-2023-39780) to establish a persistent SSH backdoor.
- Federal agencies have until June 23, 2025, to address the identified vulnerabilities in the catalog as per the Binding Operational Directive (BOD) 22-01 issued by CISA.
Read Full Article
1 Like
TechCrunch
288

Image Credit: TechCrunch
Health giant Kettering still facing disruption weeks after ransomware attack
- Kettering Health in Ohio is still recovering from a ransomware attack, causing significant disruption in its operations for the past two weeks.
- Core components of the electronic health record system have been restored, allowing for updates and access to records, but issues with phone lines and services persist.
- Patients are facing challenges such as difficulty in refilling medications, closed emergency rooms, and delays in care due to manual record-keeping processes.
- The ransomware gang called Interlock is believed to be behind the attack, with hackers potentially trying to negotiate a ransom payment, making Kettering Health the latest in a series of healthcare companies targeted by cyberattacks.
Read Full Article
17 Likes
Securelist
40

Image Credit: Securelist
Host-based logs, container-based threats: How to tell where an attack began
- Containers, while providing isolated runtime environments, still pose security risks due to shared host system kernel.
- Many organizations lack container visibility for security monitoring, making it challenging for threat hunters and incident responders.
- Understanding how containers are created and operate is essential for investigating security incidents in containerized environments.
- Containers rely on namespaces, control groups, union filesystems, and Linux capabilities for resource management and isolation.
- Host-based execution logs are crucial for gaining insight into processes and activities within containers from the host's perspective.
- Different container creation workflows involve high-level container runtimes like containerd or CRI-O interacting with low-level runtimes like runc.
- Processes in detached containers are reparented to a shim process, which manages the standard input/output for the container and ensures process cleanup.
- BusyBox-based containers use minimalist utilities to reduce image sizes, with applets managing and executing commands within the container.
- Threat hunters can leverage knowledge of container execution behaviors, such as BusyBox processes, to detect suspicious activities within containers.
- Monitoring container activity and abnormal entrypoints is crucial for identifying and responding to container-based threats effectively.
Read Full Article
2 Likes
Siliconangle
320

Image Credit: Siliconangle
Bitdefender report finds 84% of major attacks now involve legitimate tools
- A report by Bitdefender Labs has revealed that 84% of major security incidents now involve the use of legitimate system tools, a tactic known as 'Living off the Land.'
- The study of 700,000 security incidents found that nearly all major security incidents utilize trusted binaries, tools, and utilities present in enterprise environments.
- Attackers frequently use tools like netsh.exe, powershell.exe, reg.exe, cscript.exe, and rundll32.exe for malicious purposes, exploiting their dual functionality.
- The report emphasizes the challenge for defenders in distinguishing legitimate use from malicious intent within these tools and suggests a shift towards security solutions like Bitdefender's PHASR for neutralizing threats.
Read Full Article
19 Likes
Securityaffairs
284

Image Credit: Securityaffairs
Google fixed the second actively exploited Chrome zero-day since the start of the year
- Google released out-of-band updates to address three vulnerabilities in Chrome, including one actively exploited in the wild (CVE-2025-5419).
- The actively exploited vulnerability allows an attacker to trigger heap corruption via a crafted HTML page.
- In addition, Google addressed another medium-severity flaw in the Blink rendering engine (CVE-2025-5068).
- This is the second actively exploited Chrome zero-day fixed by Google since the beginning of the year.
Read Full Article
17 Likes
Securityaffairs
284
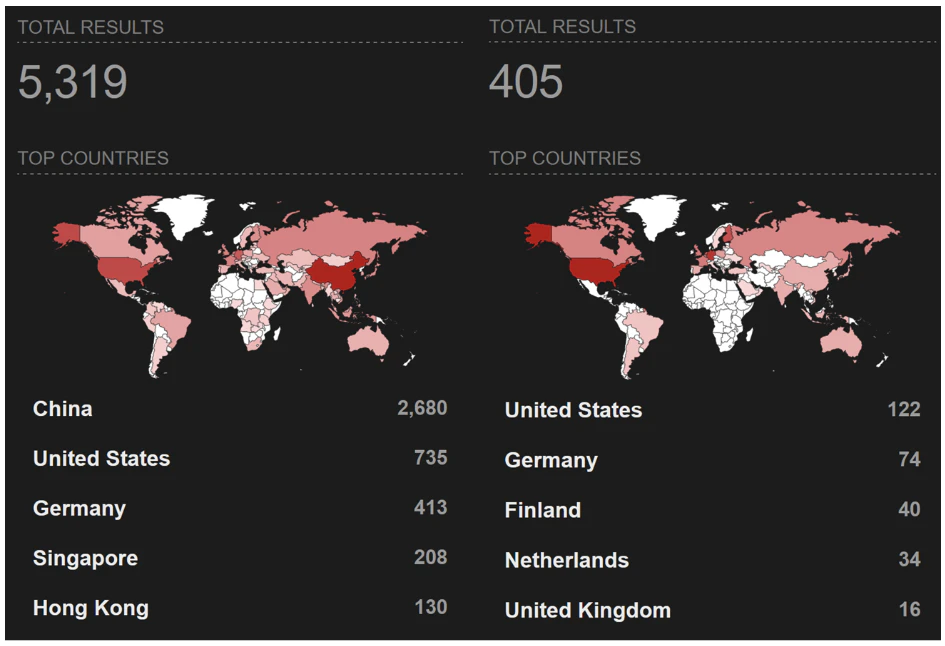
Image Credit: Securityaffairs
Cryptojacking campaign relies on DevOps tools
- A cryptojacking campaign, known as JINX-0132, is targeting exposed DevOps servers like Docker and Gitea to mine cryptocurrency secretly.
- The threat actors exploit misconfigurations and vulnerabilities in tools like Nomad, Consul, Docker, and Gitea to deliver the miner.
- The attackers rely on public GitHub tools and XMRig versions instead of custom malware, making attribution and clustering difficult.
- This campaign highlights the importance of securing DevOps tools properly, as 25% of cloud environments use these technologies, with 5% exposed directly to the internet and 30% of those misconfigured.
Read Full Article
17 Likes
Hackersking
387
Image Credit: Hackersking
Janitor AI: What is a Proxy and Why Should it Matter
- In the realm of artificial intelligence, chatbots like Janitor AI are making waves, with personas as realistic as interacting with real individuals.
- Understanding the term 'proxy' in the context of Janitor AI is crucial for users to comprehend its significance and role.
- Janitor AI is an AI chatbot platform known for complex interactions, roleplaying, and engaging conversations across various genres.
- Janitor AI uses external AI models like OpenAI’s GPT, Kobold, or others, relying on proxies to establish connections effectively.
- A proxy server acts as an intermediary between your device and another server, ensuring secure and anonymous transmission of data.
- Proxies play a vital role for Janitor AI by bypassing restrictions, reducing costs, enhancing privacy, and improving speed and load balancing.
- Types of proxies used with Janitor AI include reverse proxies, API proxies, self-hosted proxies, and public or community proxies.
- Configuring a proxy for Janitor AI involves selecting a model, joining a proxy server, inputting the proxy URL, and testing the connection.
- While proxies offer benefits like privacy and cost savings, there are risks such as security concerns and potential policy violations.
- Utilizing a proxy with Janitor AI can optimize interactions with AI models, enabling seamless and enriched chatbot experiences.
Read Full Article
23 Likes
Siliconangle
383

Image Credit: Siliconangle
Microsoft and CrowdStrike collaborate on shared threat actor mapping system
- CrowdStrike Holdings Inc. and Microsoft Corp. have announced a collaboration to address confusion in identifying and tracking cyberthreat actors across security platforms.
- The partnership will establish a shared mapping system to align adversary attribution across their threat intelligence ecosystems, reducing ambiguity caused by inconsistent naming.
- The collaboration aims to provide clarity in adversary identification, help defenders make faster decisions, correlate threat intelligence, and disrupt threat actor activity effectively.
- CrowdStrike and Microsoft have already 'deconflicted' more than 80 adversaries and plan to expand the effort by inviting other partners to contribute to a shared threat actor mapping resource.
Read Full Article
23 Likes
Livebitcoinnews
130

Image Credit: Livebitcoinnews
BitoPro Hack Suspected, $11.5M Drained Across Chains
- BitoPro, a crypto exchange in Taiwan, was likely hacked with $11.5 million stolen across various blockchain networks on May 8, 2025.
- Stolen crypto was laundered through Tornado Cash, Thorchain, and Wasabi Wallet to conceal the source of funds.
- BitoPro confirmed a hot wallet breach during a system upgrade and hired cybersecurity experts to investigate the incident.
- BitoPro plans to launch a new hot wallet for transparency to rebuild user trust and improve cybersecurity measures.
Read Full Article
7 Likes
TechCrunch
347

Image Credit: TechCrunch
NSO Group asks judge for new trial, calling $167 million in damages ‘outrageous’
- NSO Group is seeking a new trial or reduction in the $167 million damages it was ordered to pay to WhatsApp by filing a motion in court.
- NSO Group's lawyers argue that the punitive damages awarded are 'outrageous' and 'unlawful,' exceeding lawful punitive damages by many orders of magnitude.
- WhatsApp vows to continue fighting the case despite NSO Group's attempts to avoid accountability and seek impunity.
- NSO Group claims that the damages awarded exceed its financial capacity to pay and reflect an improper desire to punish the company.
Read Full Article
20 Likes
Securityaffairs
85
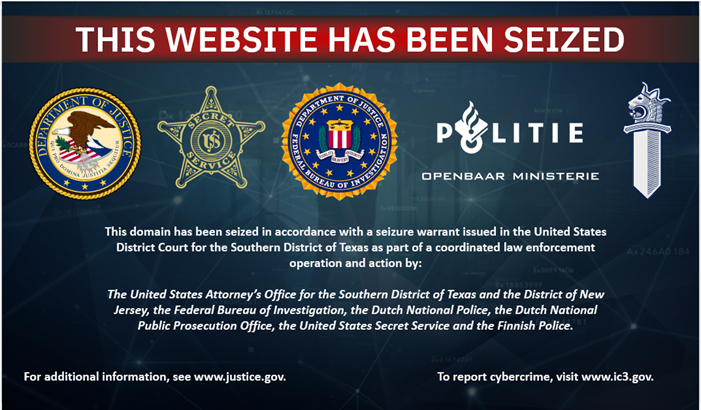
Image Credit: Securityaffairs
Police took down several popular counter-antivirus (CAV) services, including AvCheck
- On May 27, 2025, authorities seized crypting service sites (including AvCheck, Cryptor, and Crypt.guru) used by cybercriminals to test malware evasion capabilities.
- An international law enforcement operation, spearheaded by the U.S. Department of Justice, dismantled an online cybercrime syndicate providing encryption services to help malware evade detection.
- The operation, named Endgame, involved global efforts from U.S., Dutch, Finnish, and other national police forces to shut down malware services. The seized domains offered counter-antivirus tools for cybercriminals.
- CAV services like AVCheck enable cybercriminals to test their malware against antivirus programs discreetly, allowing them to gain unauthorized access to computer systems undetected. Undercover agents confirmed the services were linked to ransomware groups behind attacks in the U.S. and abroad.
Read Full Article
5 Likes
Securityaffairs
198

Image Credit: Securityaffairs
A cyberattack hit hospitals operated by Covenant Health
- A cyberattack hit three hospitals operated by Covenant Health, leading to a shutdown of all systems to contain the incident.
- The cyberattack impacted services at St. Mary’s Health System and St. Joseph Hospital, requiring adjustments in outpatient lab services.
- Covenant Health Systems, a non-profit Catholic regional health care system, experienced the cyberattack, starting on May 26, 2025.
- At this time, no ransomware group has claimed responsibility for the attack, while previous cyberattacks have targeted healthcare organizations in the U.S.
Read Full Article
11 Likes
Silicon
45
Image Credit: Silicon
Victoria’s Secret, Adidas Hit By Cyber-Attacks
- Victoria's Secret and Adidas were hit by cyber-attacks, affecting their online and in-store services.
- Victoria's Secret paused online orders and some in-store services after a security incident, while Adidas reported stolen customer contact information from a third-party provider.
- Recent incidents of cyber-attacks also impacted British retailers like Marks & Spencer and the Co-op Group in late April.
- UK authorities are investigating potential connections to a hacking group called Scattered Spider, which has a history of targeting companies in various sectors using social engineering techniques.
Read Full Article
2 Likes
For uninterrupted reading, download the app