Hacking News
Securityaffairs
126

Image Credit: Securityaffairs
Experts published a detailed analysis of Cisco IOS XE WLC flaw CVE-2025-20188
- Details of a critical vulnerability, tracked as CVE-2025-20188, impacting Cisco IOS XE WLC have been made public.
- An unauthenticated, remote attacker could exploit the flaw to upload arbitrary files, perform path traversal, and execute arbitrary commands with root privileges.
- The vulnerability impacts various Cisco products such as Catalyst 9800 Series Wireless Controllers and Embedded Wireless Controller on Catalyst APs.
- Users are urged to disable the Out-of-Band AP Image Download feature as a mitigation while awaiting a fix, as no workaround exists.
Read Full Article
7 Likes
Hackersking
308

Image Credit: Hackersking
Instagram Account Details By Username: A Complete Guide Of 2025
- Instagram has become more than a photo-sharing platform, serving various purposes like showcasing lives, promoting businesses, networking, and building careers.
- Ways to obtain Instagram account details include checking basic profile information like username, bio, and profile picture, examining posts and captions, analyzing followers and following insights, exploring Instagram Stories and Highlights, and checking linked external accounts and contact options.
- Ethical methods involve using Instagram's built-in features like search bar, followers list, and Instagram Stories, along with manual search techniques on Google, and third-party tools like Noxinfluencer, Social Blade, IGLookup, and Phantombuster for public info.
- Reverse image search can help in verifying a user's profile picture, while checking comments and likes can provide insights into a user's social interactions.
Read Full Article
18 Likes
Medium
243

Image Credit: Medium
What is Security Operations Center (SOC)
- A Security Operations Center (SOC) is a centralized function that deals with security issues using people, processes, and technologies to monitor, detect, prevent, investigate, and respond to cybersecurity threats.
- The SOC collects telemetry from an organization's IT infrastructure and serves as the hub for security, correlating events and determining responses.
- The evolution of SOC includes generations like 1st Gen focusing on defense measures, and the latest being the NGSOC incorporating AI, Machine learning, SOAR, UEBA, Threat Intelligence platforms, EDR, and XDR.
- Monitoring cloud threats, the NGSOC era expands SOC responsibilities to include cloud security.
- SOC Analysts play a crucial role in different tiers with specific duties. Processes like Incident response plans and technology such as SIEM and SOAR are vital components of an effective SOC.
- An In-House SOC provides visibility and control but can be costly, while an MSSP-managed SOC offers cost-effectiveness and scalability.
- Hybrid SOC combines advantages of both in-house and outsourced SOC models, suitable for organizations with specific needs.
- SOC Maturity Models like SOC-CMM assess maturity levels across capability domains to determine the effectiveness of SOC operations in handling cybersecurity threats.
Read Full Article
14 Likes
Pymnts
252

Image Credit: Pymnts
Hacking Ringleader ‘Stern’ Identified by Law Enforcement
- Law enforcement in Germany has identified the leader of hacking gang Trickbot, known as 'Stern', as Vitaly Nikolaevich Kovalev, a 36-year-old Russian.
- Kovalev is wanted in Germany for allegedly being the 'ringleader' of a 'criminal organisation', according to a recently issued Interpol red notice.
- As one of the most noteworthy figures in the Russian cybercriminal underground, Stern's real name had been unknown for years despite his involvement in Trickbot and previous hacking activities.
- In other cybersecurity news, data breaches involving third parties have doubled from 15% in 2023 to 30% in the following year, with a surge in lawsuits filed related to such breaches.
Read Full Article
15 Likes
Metro
185
Image Credit: Metro
Warning issued to 1,800,000,000 iPhone users over security risk
- Apple has issued a warning to all 1.8 billion iPhone users regarding a security gap in the operating system.
- The latest iOS 18.5 update targets potential vulnerabilities that could compromise users' photos, messages, and private data if not addressed.
- The software update is critical for iPhone models after iPhone XS and iPads, including the latest iPad mini, to protect against malware threats.
- Apple experts recommend users to update their devices promptly as a necessary security measure to safeguard their personal information and prevent potential cyber attacks.
Read Full Article
11 Likes
Pymnts
72

Image Credit: Pymnts
Scattered Spider Chases Clout via Social Engineering Scams
- The hacking group known as “Scattered Spider” has been active, targeting companies like Marks & Spencer and conducting social engineering scams to obtain passwords.
- Their attacks have caused significant financial losses, such as up to $403 million for M&S and disruptions at MGM Casinos and Resorts.
- Scattered Spider seeks attention and clout rather than just financial gain, as mentioned by Charles Carmakal, chief technology officer at Mandiant Consulting.
- The group has targeted various companies and industries through impersonation tactics, with cybersecurity professionals being alert to this threat.
Read Full Article
4 Likes
Hackers-Arise
194

Image Credit: Hackers-Arise
Twitter (X) Strategic OSINT Techniques
- The article discusses the evolving landscape of open source intelligence (OSINT) on Twitter, now rebranded as X, under Elon Musk's ownership.
- The platform's changes have posed challenges for digital investigators who relied on third-party tools and APIs for data access.
- With API restrictions, traditional OSINT tools like Twint and GetOldTweets3 are now less effective, requiring a shift in investigative methodologies.
- Understanding the new Twitter landscape is crucial, as the platform's monetization model has created different user classes with various capabilities.
- The removal of legacy verification badges and the introduction of paid verification have impacted source credibility assessment.
- Effective Twitter OSINT involves crafting precise search queries using advanced search operators like from, to, near, filter, and hashtags.
- In profile analysis, investigators can derive valuable intelligence from account creation patterns, username evolution, profile image analysis, and temporal behavioral fingerprinting.
- Relationship intelligence on Twitter involves analyzing early followers, mutual connections, reply chain forensics, and systematic documentation for intelligence development.
- Successful investigations establish behavioral baselines, employ multi-vector correlation analysis, and utilize predictive behavior modeling to anticipate future activities.
- Modern Twitter OSINT demands cross-platform correlation skills and systematic investigation techniques to navigate the platform's evolving constraints.
Read Full Article
11 Likes
Securityaffairs
280

Image Credit: Securityaffairs
Security Affairs newsletter Round 526 by Pierluigi Paganini – INTERNATIONAL EDITION
- Two Linux flaws found can expose sensitive data. Meta stopped covert operations from Iran, China, and Romania spreading propaganda.
- US Treasury sanctions Funnull Technology for cyber scam facilitation. ConnectWise faces cyberattack from a sophisticated nation-state actor.
- Victoria’s Secret website offline due to a cyberattack. APT41 uses Google Calendar for malware control.
- New AyySSHush botnet compromises 9,000 ASUS routers. Czech Republic accuses China’s APT31 for a cyberattack.
Read Full Article
16 Likes
Hackersking
196

Image Credit: Hackersking
SOA OS23: Know About the Latest Update in System-Oriented Architecture
- SOA OS23 is the latest version of the SOA Operating System, focusing on system integration, flexibility, and data flow in distributed systems.
- Key features of SOA OS23 include greater control over APIs, microservices support augmentation, cyber defense mechanisms, cloud-native features adaptation, AI technology integration, and efficiency improvements.
- SOA OS23 cares about service reusability, interoperability, scalability, and maintenance, ensuring optimal assistance for developers and IT professionals.
- Industry applications of SOA OS23 include usage in telecom for billing systems, finance for transaction processing, healthcare for data exchange, and e-commerce for platform scaling.
Read Full Article
11 Likes
Hackersking
49

Image Credit: Hackersking
Indown.io: The Ultimate Tool for Downloading Videos Online Instantly
- Indown.io is an online tool that allows users to effortlessly download videos from various social media platforms without the need to install apps or register for an account.
- This tool supports multiple platforms including Instagram, Facebook, TikTok, Twitter, and YouTube, and provides high-quality downloads in HD and SD formats.
- Indown.io is fast, lightweight, mobile-friendly, and doesn't require any registration, making it convenient for users to save videos.
- Users can simply copy the video URL, paste it on Indown.io, select the download option, choose the preferred video resolution or format, and save the video to their device.
- In terms of safety, Indown.io is ad-free and safe for personal use, but users should follow copyright policies to ensure ethical usage.
- Users appreciate Indown.io for being a free service, not requiring software installation, operating on all platforms, and providing fast download speeds.
- Some alternatives to Indown.io include SnapSave, SaveFrom, Y2Mate, and SSSTikTok, but Indown.io stands out for its simplicity and clean interface.
- Overall, Indown.io simplifies downloading videos online and offers a seamless user experience for individuals across various purposes, from students to marketers.
- For the latest updates on tech tools and digital trends, Hackersking is a reliable source providing unbiased reports and accurate information for users to stay informed.
- Hackersking offers a range of resources from guides to reviews, ensuring that users are equipped to navigate the digital world efficiently and securely.
Read Full Article
2 Likes
Securityaffairs
63

Image Credit: Securityaffairs
Meta stopped covert operations from Iran, China, and Romania spreading propaganda
- Meta stopped covert operations from Iran, China, and Romania targeting social media platforms with propaganda.
- Three influence operations disrupted by Meta using fake accounts on Facebook, Instagram, and more.
- Accounts removed linked to China-based network targeting Myanmar, Taiwan, and Japan.
- Meta also removed accounts tied to Iran-based network targeting Azeri-speaking users and accounts linked to a Romania-based network.
Read Full Article
3 Likes
Hackingblogs
393

Image Credit: Hackingblogs
Want to Hack Like a Pro? These 25 Free Hacking Tools Will Get You There!
- The article discusses 25 free hacking tools necessary for hacking professionals.
- Reconnaissance and scanning tools like Masscan, Sublist3r, Nmap, Recon-ng, and Sn1per are highlighted.
- These tools assist in network discovery, subdomain enumeration, and vulnerability detection.
- Exploitation frameworks like Metasploit, Hydra, and Sqlmap are crucial for exploiting vulnerabilities.
- Web penetration testing tools like Burp Suite, OWASP ZAP, and Gobuster aid in assessing online application security.
- Password cracking and authentication tools like Hashcat and John the Ripper help in breaking password hashes.
- OSINT tools such as Sherlock, SpiderFoot, and TheHarvester are used for open-source intelligence gathering.
- Post-exploitation and privilege escalation tools like PEASS-ng and PowerSploit provide capabilities for escalating privileges.
- Networking and MITM tools like Wireshark, CrackMapExec, and King Phisher are useful for network analysis and phishing simulations.
- Additional tools like Naabu, Subfinder, and BloodHound assist in port scanning, subdomain enumeration, and Active Directory mapping.
- Each tool serves a specific purpose in the hacking domain, contributing to various stages of reconnaissance, exploitation, and testing.
Read Full Article
23 Likes
Securelist
199

Image Credit: Securelist
Exploits and vulnerabilities in Q1 2025
- The first quarter of 2025 revealed continued publication of vulnerabilities discovered and fixed from 2024, with a shift towards older OS versions being targeted in attacks.
- There was a notable delay between problem investigation and patch release, emphasizing the importance of reserving CVE IDs early.
- Linux kernel vulnerabilities in Q1 2025 were predominantly related to CWEs like Null Pointer Dereference and Use after Free.
- Microsoft software vulnerabilities in the same period commonly involved issues like Heap-based Buffer Overflow and Out-of-bounds Write.
- Exploiting vulnerabilities in common CWEs demands sophisticated capabilities due to Linux's robust mitigations.
- Windows exploits in Q1 2025 targeted vulnerabilities like CVE-2018-0802 and CVE-2017-11882, emphasizing the need for regular updates.
- The most exploited Linux vulnerabilities included CVE-2022-0847 (Dirty Pipe) and CVE-2019-13272, highlighting the importance of system updates.
- Published exploits in Q1 2025 mostly targeted operating systems, browsers, and Microsoft Office products.
- APT attacks focused on exploiting vulnerabilities in perimeter devices and server software, with the Zerologon vulnerability reappearing in the top 10 list.
- Prominent vulnerabilities included a Windows LNK file display flaw and a NetNTLM hash leakage vulnerability in the file system indexer.
- To mitigate risks, it is crucial to promptly install updates, monitor infrastructure, implement strong patch management, and use effective cybersecurity solutions.
Read Full Article
11 Likes
Securityaffairs
176
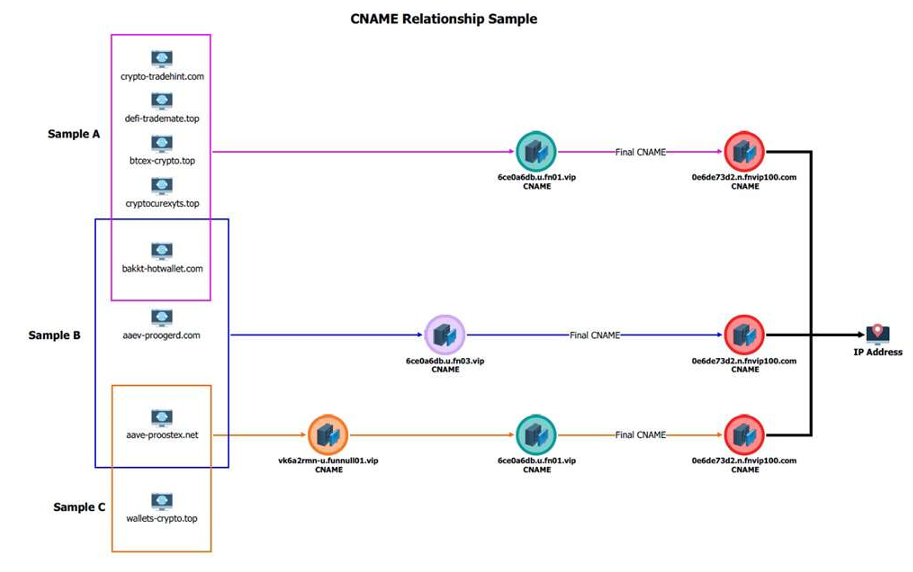
Image Credit: Securityaffairs
US Treasury sanctioned the firm Funnull Technology as major cyber scam facilitator
- The U.S. Treasury sanctioned Funnull Technology and Liu Lizhi for facilitating romance scams leading to significant losses in cryptocurrency fraud.
- Funnull Technology Inc. aided in cyber scams by providing infrastructure for fake platforms, resulting in over $200 million in losses for U.S. victims.
- Romance scams involve scammers building fake romantic relationships to exploit victims for financial gain by manipulating them into sending money or sensitive information.
- The FBI issued a FLASH alert highlighting indicators of compromise associated with Funnull's malicious cyber activities, including patterns of IP address activity and domain migrations.
Read Full Article
10 Likes
Securityaffairs
221

Image Credit: Securityaffairs
ConnectWise suffered a cyberattack carried out by a sophisticated nation state actor
- ConnectWise detected suspicious activity linked to a nation-state actor, impacting a small number of its ScreenConnect customers.
- ConnectWise confirmed the cyberattack and launched an investigation with cybersecurity firm Mandiant, patching the flaw in ScreenConnect and implementing enhanced security measures.
- The breach possibly occurred in August 2024 and went unnoticed until May 2025. The ScreenConnect flaw (CVE-2025-3935) may have allowed remote code execution via stolen machine keys.
- Threat actors exploited ScreenConnect vulnerabilities (CVE-2024-1709 and CVE-2024-1708) in early 2024, with Black Basta and Bl00dy ransomware groups actively exploiting the flaws.
Read Full Article
13 Likes
For uninterrupted reading, download the app