Hacking News
Idownloadblog
83

Image Credit: Idownloadblog
Software tinkerer gets iOS running on a first-generation Nintendo Switch via QEMU
- A software tinkerer managed to run a version of iOS on a first-generation Nintendo Switch using QEMU.
- The content was initially shared on social media by @Patrosi73.
- The iOS version running on the Nintendo Switch via QEMU is a full-fledged build, not a simplified simulation version.
- However, there are limitations such as a 20-minute boot time, frequent kernel panics, and inability to launch apps successfully.
- This lack of functionality is attributed to various factors like incompatible hardware drivers and missing dependencies.
- The Nintendo Switch's hardware, including its CPU and GPU, is inferior to modern iPhones, contributing to the limited usability of running iOS on it.
- Despite the limitations, the achievement of running iOS on a Nintendo Switch is seen as an intriguing concept.
Read Full Article
5 Likes
Hackers-Arise
260

Image Credit: Hackers-Arise
VPN Hacking: Authentication Bypass on Fortinet Fortios
- A vulnerability was discovered in Fortinet's FortiOS, FortiProxy, and FortiSwitchManager, allowing attackers to bypass authentication and log in as admin.
- Security researchers developed a proof of concept exploit for this vulnerability.
- Attackers can upload their own SSH keys to the Fortinet device via the web server.
- Login attempts to SSH on the Fortinet device can lead to lockout after 3 failed attempts.
- Users are advised to create a pair of RSA keys for SSH when attempting to login.
- A proof-of-concept exploit for CVE-2022-40684 is available on GitHub for exploiting the vulnerability.
- The exploit involves pointing towards the target system IP address, defining the username to exploit, and sending the keyfile for the SSH user to the server.
- By successfully adding the key file to the SSH server, attackers can log in as admin and gain complete control of the Fortinet device.
- Once logged in as admin, attackers can manipulate the device, monitor traffic, and perform various actions.
- The vulnerabilities in VPNs and routers pose significant security risks, as many devices lack basic cybersecurity practices.
- Testing the security of these devices is crucial, and a necessary aspect of any pentest or cyberwar strategy.
- There is a call to attend upcoming VPN and Router Hacking training to learn techniques for testing and hacking vulnerable devices.
Read Full Article
15 Likes
Securityaffairs
407

Image Credit: Securityaffairs
U.S. CISA adds Apple products, and TP-Link routers flaws to its Known Exploited Vulnerabilities catalog
- U.S. Cybersecurity and Infrastructure Security Agency (CISA) added Apple products and TP-Link routers flaws to its Known Exploited Vulnerabilities catalog.
- A recently patched vulnerability in Apple's Messages app, actively exploited in the wild, targeted journalists with Paragon's Graphite spyware.
- Apple addressed the flaw in its products with various software updates.
- Citizen Lab confirmed the use of Paragon's Graphite spyware to hack fully updated iPhones, targeting journalists in Europe.
- Apple alerted select iOS users of spyware targeting and patched the zero-click exploit used in the attack.
- Paragon accused the Italian government of refusing its offer to help investigate spyware use against a journalist.
- CISA added a command injection vulnerability in TP-Link routers to its catalog.
- Federal agencies are required to address the vulnerabilities identified in the catalog by July 7, 2025.
Read Full Article
24 Likes
Securityaffairs
106
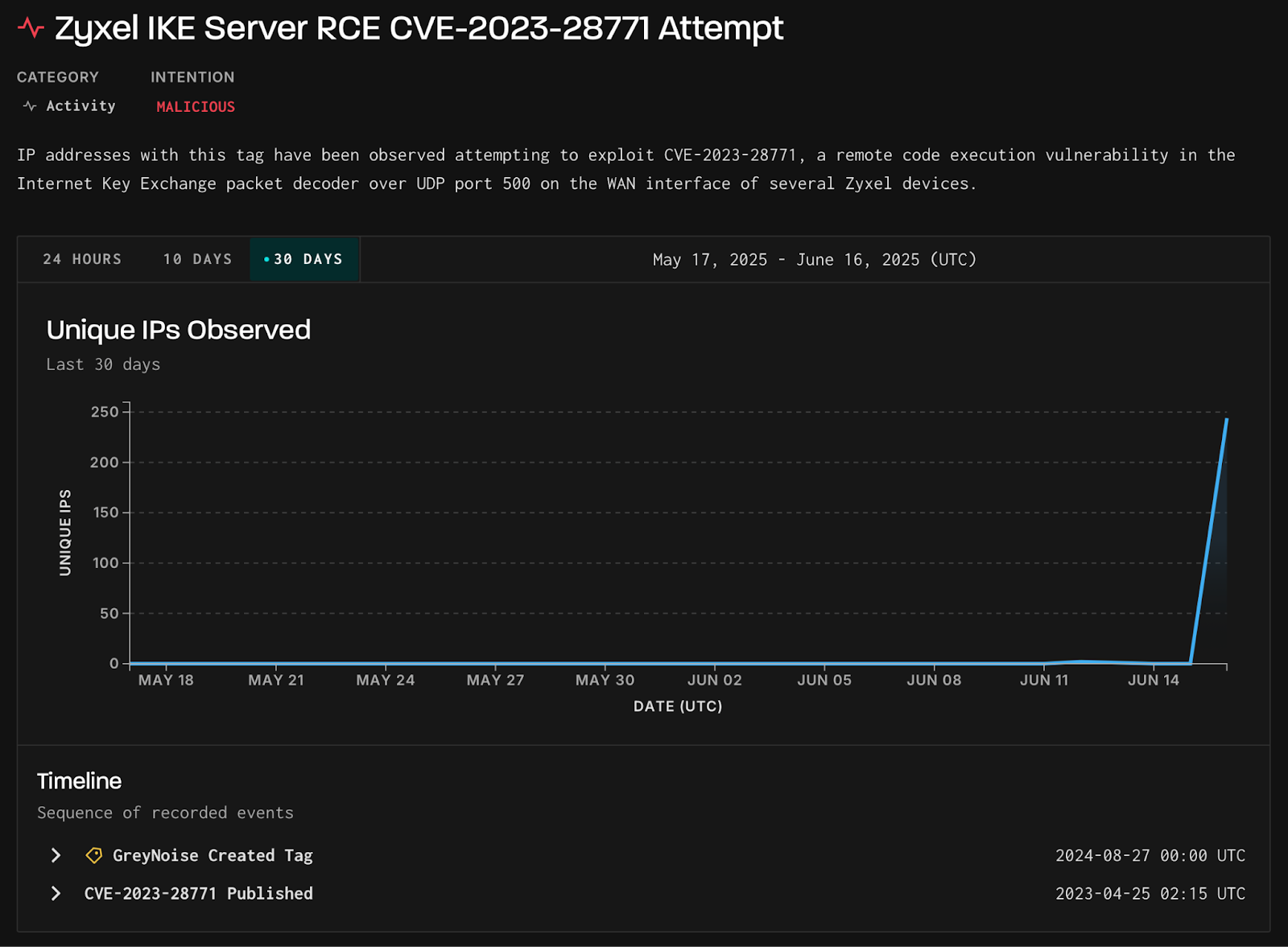
Image Credit: Securityaffairs
Attackers target Zyxel RCE vulnerability CVE-2023-28771
- Attackers are actively targeting the Zyxel RCE vulnerability CVE-2023-28771, according to GreyNoise researchers.
- On June 16, a surge in exploit attempts against the Zyxel IKE decoders vulnerability was observed, with 244 unique IPs involved.
- The main targets of the attack were the U.S., U.K., Spain, Germany, and India.
- All 244 IP addresses related to the exploitation attempts were traced back to Verizon Business in the U.S., but the use of UDP means the IPs could be spoofed.
- The exploit attempts were linked to Mirai botnet variants, as confirmed by VirusTotal.
- GreyNoise recommends blocking the identified malicious IPs, verifying device patches, monitoring for post-exploitation activities, and limiting exposure on IKE/UDP port 500.
- In April 2023, Zyxel addressed the CVE-2023-28771 vulnerability in its firewall devices and urged customers to install patches to mitigate the risk.
- The U.S. CISA added the vulnerability to its Known Exploited Vulnerability to Catalog after observing active exploitation.
Read Full Article
6 Likes
Securityaffairs
433

Image Credit: Securityaffairs
India-based car-sharing company Zoomcar suffered a data breach impacting 8.4M users
- India-based car-sharing company Zoomcar has disclosed a data breach affecting 8.4M users after attackers compromised its systems and contacted the company staff.
- The breach involved unauthorized access to Zoomcar's information systems, leading to exposure of names, contacts, and addresses of users.
- No financial data or passwords were compromised in the breach.
- Zoomcar is investigating the security incident and has taken measures to enhance cloud and network security with the help of cybersecurity experts.
- The company notified authorities about the breach, and its operations have not been significantly impacted so far.
- Legal, financial, and reputational impacts of the breach are being assessed by Zoomcar.
- The company has not provided specific details about the cyber attack, and no ransomware group has taken responsibility for the incident.
- Zoomcar had previously experienced a data breach in July 2018 that affected over 3.5 million users.
Read Full Article
26 Likes
Securityaffairs
398

Image Credit: Securityaffairs
State-sponsored hackers compromised the email accounts of several Washington Post journalists
- State-sponsored hackers compromised the email accounts of several journalists at the Washington Post.
- The cyberattack, believed to be carried out by state-sponsored hackers, targeted Microsoft email accounts of Washington Post journalists covering China and national security.
- The attack was discovered on June 13, with the intrusion potentially granting access to work emails of affected journalists.
- The Washington Post notified its employees about the incident on June 15 and reset all employee passwords as a precaution.
- News Corp, the owner of the Washington Post, revealed in February 2022 that it fell victim to a cyber attack by an advanced persistent threat actor.
- The attack on News Corp was believed to be conducted by a nation-state actor, with suspicions pointing towards a China-linked APT group.
- Mandiant, a cybersecurity firm, has been enlisted to assist in the investigation into the News Corp breach.
- The compromised systems at News Corp gave attackers access to employee emails and documents.
- The attack on News Corp also affected other media outlets under the conglomerate, such as The Wall Street Journal and New York Post.
- The Washington Post is one of the most influential newspapers in the U.S., known for its investigative journalism and political coverage.
- Jeff Bezos acquired the Washington Post in 2013.
- The intrusion at the Washington Post did not impact other systems or customers of the newspaper.
- Cybersecurity incidents like these highlight the ongoing threats faced by media organizations and the need for robust security measures.
- The attack on the Washington Post underscores the importance of cybersecurity vigilance, especially for journalists covering sensitive topics.
- The motive behind the cyber attacks appears to be espionage, targeting sensitive information to benefit the interests of the sponsoring nation.
- The cyber threats faced by media organizations emphasize the critical role of cybersecurity in safeguarding journalistic integrity and protecting sensitive data.
Read Full Article
23 Likes
Idownloadblog
146

Image Credit: Idownloadblog
LeminLimez says upcoming hack could enable custom CarPlay wallpapers without a jailbreak
- LeminLimez, lead developer of Nugget and Pocket Poster, shared a post suggesting that it would be possible to have custom CarPlay wallpapers using Pocket Poster without jailbreaking.
- Implementing this hack would require a separate app hash and could be somewhat tedious but does work, allowing customization without a jailbreak.
- While this feature only supports still images and not video wallpapers, the fact that it's achievable without jailbreaking is noteworthy.
- The process involves editing caches, something Pocket Poster can do while Nugget cannot.
- Support for different iOS versions may vary due to differences in wallpaper names.
- The custom wallpaper is limited to images and cannot include videos.
- The exact iOS versions supported by this feature remain uncertain as different versions use varying wallpaper names.
- There is a possibility of LeminLimez making this a public feature in the future, with further updates by iDownloadBlog team.
- This hack brings an exciting customization opportunity for CarPlay users who prefer not to jailbreak their devices.
Read Full Article
8 Likes
Idownloadblog
4

Image Credit: Idownloadblog
Nugget v6 now available with new features & bug fixes, including preliminary iOS 26 beta support
- Nugget v6.0 has been released by LeminLimez, the lead developer, offering new features and bug fixes.
- New features include templates for custom files and domains, status bar tweaks, Lock Screen footnotes, and more.
- Bug fixes involve optimizing tweak backend, fixing device selection for iOS 18.2+ devices, Windows path errors, and others.
- The update also introduces preliminary iOS 26 beta support and adds compatibility for Ubuntu 20 and newer.
- Nugget, a customization toolkit, doesn't require a jailbreak but allows significant customizations resembling jailbreak tweaks.
- It utilizes the SparseRestore exploit and works on iOS 17.0-18.1.1, with preliminary support now for iOS 26.
- Nugget is available for free download on its GitHub page and is compatible with Windows, Linux, and macOS.
Read Full Article
Like
Securityaffairs
97

Image Credit: Securityaffairs
Law enforcement operation shut down dark web drug marketplace Archetyp Market
- Europol led a global law enforcement operation that shut down Archetyp Market, a prominent dark web drug marketplace.
- The marketplace facilitated the sale of illegal drugs like cocaine, MDMA, amphetamines, and synthetic opioids through anonymous transactions.
- Around 300 officers from six countries collaborated between June 11 and 13 to target the marketplace, its administrators, vendors, and infrastructure.
- The operation resulted in the arrest of a 30-year-old German national who was identified as the marketplace's administrator and captured in Barcelona, Spain.
- Authorities in Germany and Sweden also apprehended a moderator and six top vendors, seizing assets valued at €7.8 million.
- Archetyp Market operated for over five years, attracting over 600,000 users worldwide and generating transactions worth at least EUR 250 million.
- The marketplace offered over 17,000 listings, including highly potent synthetic opioids like fentanyl, contributing to the escalating opioid threat in Europe and beyond.
- Europol and Eurojust spearheaded the investigation into Archetyp Market, leading to its takedown and reflecting a major blow to dark web drug trading.
- The platform's prominence and activities placed it among infamous darknet markets such as Dream Market and Silk Road, known for facilitating online drug trafficking.
- Europol's Deputy Executive Director underscored the significance of dismantling Archetyp Market as it disrupted a major source of dangerous substances, sending a clear message to illegal profiteers.
- Law enforcement displayed a seizure banner on the marketplace's homepage and released an operation success video as a warning to the cybercrime community.
Read Full Article
5 Likes
Securityaffairs
186
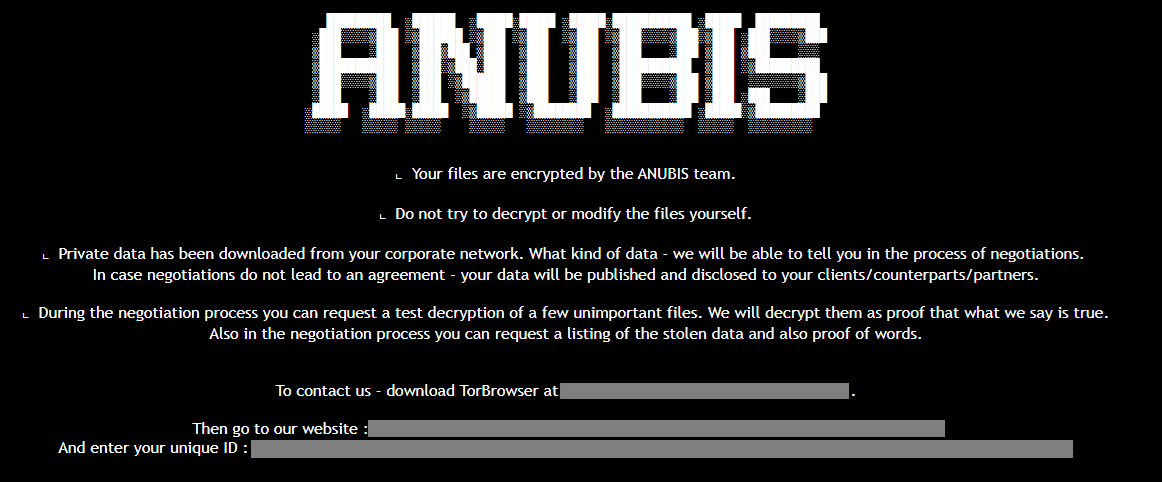
Image Credit: Securityaffairs
New Anubis RaaS includes a wiper module
- Anubis RaaS now includes a wiper module, permanently deleting files and preventing recovery even after ransom payment.
- Active since December 2024, Anubis launched an affiliate program in February 2025, breaching organizations in various sectors like healthcare and construction.
- It combines file encryption with a rare 'wipe mode,' erasing data effectively, as per a report by Trend Micro.
- Anubis evolved from an earlier variant called Sphinx, offering multiple monetization paths, including data theft and access resale.
- The ransomware operates with the ECIES encryption scheme and uses double extortion tactics, threatening to leak data if ransom demands are not met.
- Upon activation of the wiper mode, files are left with a 0 KB size, indicating complete erasure.
- Anubis supports various commands for privilege escalation, directory exclusion, and targeted encryption, ensuring successful data encryption.
- The ransomware's use of dual-threat capabilities and flexible affiliate programs represents a significant evolution in cyberthreat landscape, maximizing revenue potential and victim pressure.
- Trend Micro released a list of indicators of compromise (IoCs) related to the Anubis threat.
Read Full Article
11 Likes
Securityaffairs
416
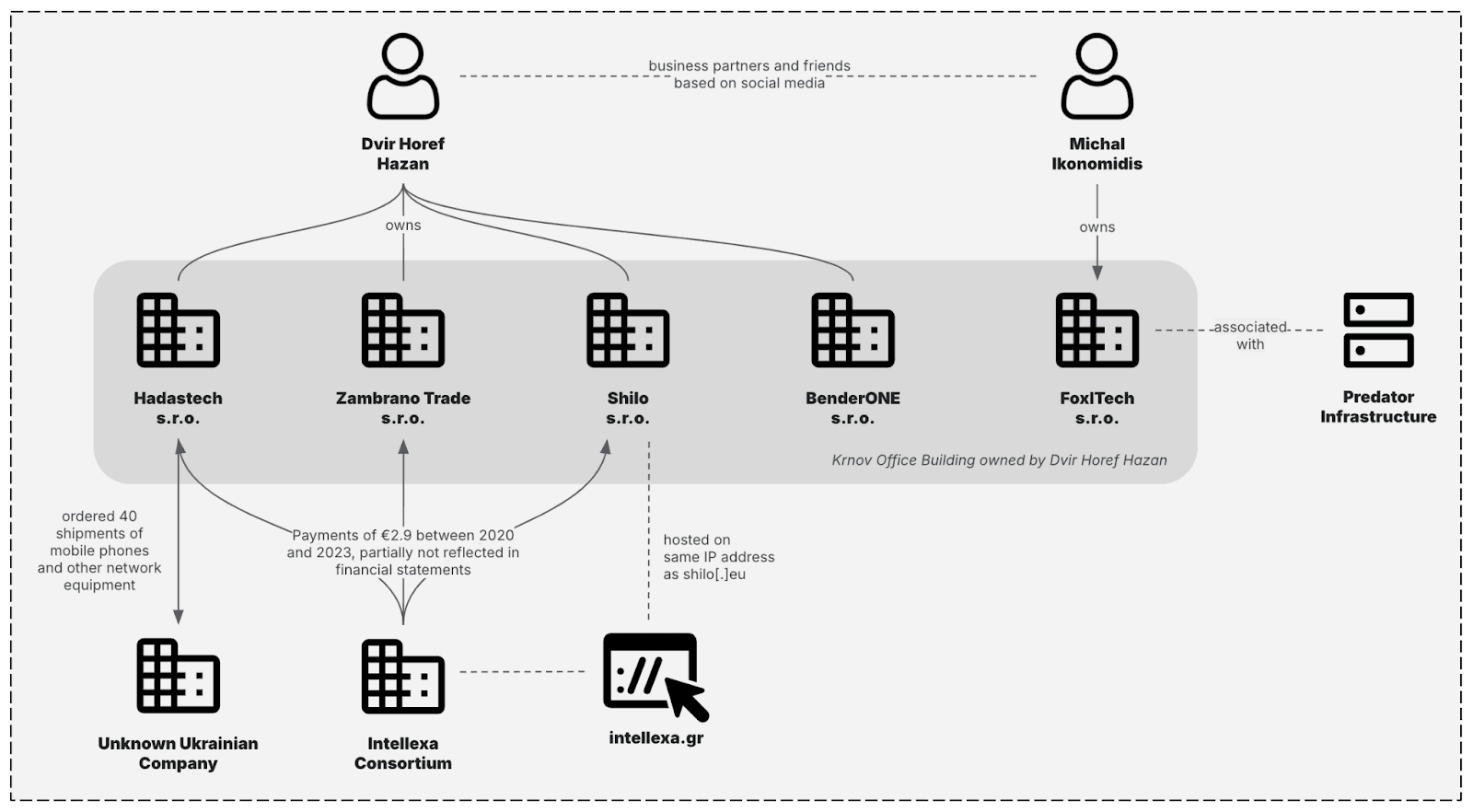
Image Credit: Securityaffairs
New Predator spyware infrastructure revealed activity in Mozambique for the first time
- Insikt Group analyzed the new Predator spyware infrastructure and found it is gaining users despite U.S. sanctions.
- Predator spyware has resurged after a decline and is being used in Mozambique.
- Over half of Predator's identified clients are in Africa, with links to the Intellexa Consortium.
- In March 2024, OFAC took actions against Intellexa Consortium members for their role in distributing Predator spyware.
- The Intellexa Consortium markets offensive cyber companies providing surveillance tools.
- Predator spyware enables compromising devices through zero-click attacks.
- Insikt Group uncovered a new Predator spyware infrastructure, including updates and high-tier components.
- The infrastructure showed renewed activity in various countries, including Mozambique.
- Predator's domains now use deceptive tactics and target specific regions.
- The spyware's infrastructure includes a five-tiered design to hide its origin and involves a Czech company.
- Operators use fake websites and other tactics to deceive targets.
- Insikt Group has monitored Predator spyware activity in over a dozen countries since March 2024.
- Some regions stopped activity due to exposure, but Mozambique emerged as a new user.
- Despite sanctions, Predator's continued use suggests the adoption of new evasion tactics.
- Public exposure and sanctions have likely impacted Intellexa's operations.
- Predator operators are using new tactics to avoid detection.
Read Full Article
25 Likes
Hackersking
315

Image Credit: Hackersking
Zryly.com Cybersecurity: Strengthening Your Digital Safety in a Connected World
- Zryly.com offers practical tips, tools, and plans to enhance online security against cyber threats.
- The website delivers fresh tech news with a focus on cybersecurity, catering to all levels of users.
- Cybersecurity has become crucial due to the rise in cybercrime, emphasizing the need for online safety measures.
- Ransomware attacks and phishing messages have increased significantly, affecting individuals and businesses.
- Zryly.com educates users through clear articles, tutorials, and the latest cybersecurity news.
- The site also recommends security tools like VPNs, antivirus software, and password managers.
- For businesses, Zryly.com provides guides on data protection, compliance, and employee awareness.
- Parents can find tips on ensuring children's online safety, while students can learn to secure school logins.
- Zryly.com stands out for its user-centric approach, regular updates, action-based content, and minimal ads.
- Practical tips from Zryly.com include using unique passwords, avoiding suspicious links, and enabling multi-factor authentication.
- Regular software updates and data backups are also recommended for improved online security.
- Ensuring digital safety requires ongoing attention and education, with sites like Zryly.com playing a crucial role.
- For more in-depth cybersecurity insights, Hackersking offers the latest trends and expert advice to keep devices secure.
Read Full Article
18 Likes
Securityaffairs
301

Image Credit: Securityaffairs
Security Affairs newsletter Round 528 by Pierluigi Paganini – INTERNATIONAL EDITION
- Palo Alto Networks fixed multiple privilege escalation flaws.
- Unusual toolset used in recent Fog Ransomware attack.
- Cyberattack on United Natural Foods led to bread shortages and bare shelves.
- Apple confirms actively exploited flaw in Messages app.
- Trend Micro fixes critical bugs in Apex Central and TMEE PolicyServer.
- Paragon Graphite Spyware hacks two journalists' iPhones with zero-day exploit.
- SinoTrack GPS device flaws allow remote vehicle control and tracking.
- U.S. CISA adds Wazuh and WebDAV flaws to Known Exploited Vulnerabilities list.
- Over 40,000 security cameras exposed to remote hacking.
- INTERPOL dismantles 20,000+ malicious IPs in cybercrime crackdown.
- Roundcube RCE bug exploited on over 80,000 servers.
- Data breach at Texas Department of Transportation exposes 300,000 crash reports.
- Mirai botnets exploit Wazuh RCE, and a China-linked threat actor targets over 70 orgs.
- DOJ aims to seize $7.74M in crypto related to North Korean IT worker scam.
- OpenAI bans ChatGPT accounts linked to Russian, Chinese cyber ops.
- New Mirai botnet targets TBK DVRs, and FBI warns of BadBox 2.0 botnet affecting millions of IoT devices.
- Over 950K weekly downloads at risk in Gluestack supply chain attack.
Read Full Article
18 Likes
Guardian
8
Image Credit: Guardian
‘We’re being attacked all the time’: how UK banks stop hackers
- UK banks face constant cyber threat, with a successful hack potentially causing widespread chaos and financial disruption.
- Billions are being spent on cybersecurity to prevent devastating attacks like those seen at major retailers.
- Banks invest heavily in security to combat evolving cyber threats, with a focus on protecting customer data.
- The attack surface for banks has increased, posing challenges in defending against cyber-attacks.
- Past bank hacks targeted customer data and account information, emphasizing the importance of robust cybersecurity measures.
- Efforts are made to stay ahead of cyber threats through continuous investment and testing of security measures.
- Regulators push banks to prepare response and recovery plans to avoid prolonged outages in case of successful cyber-attacks.
- Ensuring cybersecurity is crucial to maintain trust and protect customer information and financial assets.
- Banks work to restore reputation following IT outages, highlighting the impact on customer trust and financial stability.
- Overall, the banking industry remains vigilant against cyber threats to safeguard operations and customer trust.
Read Full Article
Like
Hackers-Arise
408

Image Credit: Hackers-Arise
Logic in Cybersecurity: One of the Most Under-Rated Skills in Cybersecurity
- Logic is a crucial skill in cybersecurity for tasks like system exploitation, network defense, and malware analysis.
- Logic helps in determining the truth or falsehood of system aspects, deciding next steps, and identifying vulnerabilities.
- Propositions in logic are statements that are either true or false, crucial in cybersecurity assessments.
- Logical operators like AND, OR, and NOT are used to combine propositions in cybersecurity scenarios.
- Conditional statements like 'If...Then' are common in cybersecurity, guiding actions based on conditions.
- Deductive reasoning applies general rules to specific cases, aiding in vulnerability assessments.
- Inductive reasoning draws general conclusions from specific instances, useful in identifying trends.
- Logical fallacies like false cause and hasty generalization should be avoided in cybersecurity analysis.
- Buffer overflow exploits exemplify the importance of logical chains in cybersecurity attack scenarios.
- Defenders use logic to create rules for blocking IPs based on login attempts or alerting on malware traffic.
- Logic is integral in scripting for tasks like writing firewall rules and coding for cybersecurity purposes.
- Clear and logical thinking is essential in navigating the complexities of cybersecurity challenges.
- Understanding logic is crucial for every aspect of cybersecurity, from scanning and exploiting to defending systems.
- The article emphasizes the significance of logic in cybersecurity, often undervalued but essential for various cybersecurity tasks.
- Applying logic ensures better decision-making in cybersecurity activities, from scripting to coding and defending systems.
- The mastery of logical thinking is highlighted as a key factor in overcoming complex hacking challenges effectively and safely.
Read Full Article
24 Likes
For uninterrupted reading, download the app