Programming News
Hackernoon
267

Image Credit: Hackernoon
The HackerNoon Newsletter: The Double Life of a TensorFlow Function (6/4/2025)
- The HackerNoon Newsletter on June 4, 2025, features top tech articles including AI companions, reinforcement learning, RTOS guide, AWS Q Developer, and TensorFlow functions.
- AI companions have evolved into a multi-billion industry, with a story on saying 'I Love You' to an AI bot.
- Reinforcement Learning and its impact on technology are discussed in another article.
- A hands-on guide for beginners using Cortex-M4, Exploring AWS Q Developer, and insights on TensorFlow's tf.function are also highlighted in the newsletter.
Read Full Article
6 Likes
Logrocket
384

Image Credit: Logrocket
UXers don’t need to code — but vibe coding might still be worth it
- Vibe coding is a creative, AI-assisted approach to software development where ideas flow and AI generates most of the code.
- Understanding how code works allows UX designers to use AI tools like ChatGPT or GitHub Copilot to bring their ideas to life faster.
- The evolution of tech stacks has led to more options like Tailwind, React, Vue, Angular, and specialized groups like MERN, JAMstack, and MEAN.
- UX designers are not required to code, but having a basic understanding of HTML, CSS, and possibly JavaScript can be beneficial.
- Vibe coding as a UX designer can lead to rapid prototyping, creating a shared language, and having a gentler learning curve for better code understanding.
- Designers using vibe coding can have improved collaboration and contribution in projects, beyond creating wireframes and mockups.
- Despite its benefits, vibe coding has downsides like lost context, messy code structure, overengineering, inconsistent quality, and outdated code.
- Vibe coding does not replace deep frontend expertise or design taste and product sense for designers.
- Designers are encouraged to try vibe coding if it excites them, but it should not distract from their primary design objectives.
- Vibe coding can be a powerful way for UX designers to explore ideas, learn how designs are built, and improve collaboration with developers.
Read Full Article
23 Likes
Python Blogs
150

Image Credit: Python Blogs
4 Amazing WhatsApp Automation Tools for Businesses
- WhatsApp automation tools have become essential for businesses seeking personalized customer engagement and streamlined interactions.
- Four notable WhatsApp automation tools for businesses include WATI, Zoko, Respond.io, and Twilio WhatsApp Business API.
- These tools offer features such as CRM integrations, chatbot builders, automation of sales, omnichannel communication, and developer-level customization.
- WhatsApp automation tools help improve response times, deliver consistent service, comply with WhatsApp's policies, and enhance customer relationships through meaningful conversations.
Read Full Article
9 Likes
Johndcook
353

Additive and multiplicative persistence
- Casting out nines is a method to find the remainder when a number is divided by 9 by adding all the digits repeatedly.
- Persistence of a number with an operation is the number of times the operation needs to be applied to reach a fixed point.
- The additive persistence of a number is the number of times the digit sum operation needs to be applied before reaching a fixed point.
- Multiplicative persistence involves multiplying digits together, and it is conjectured that this persistence is bounded for all integers.
Read Full Article
21 Likes
Discover more
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Javacodegeeks
313

Image Credit: Javacodegeeks
How to Use Spring AI to Extract Structured Data from Images
- Extracting structured data from images is crucial in various domains, and with the advancement of AI models like GPT-4o, it's feasible to extract information directly from images using prompts.
- The article demonstrates how to utilize Spring Boot and OpenAI’s GPT-4o via Spring AI to extract structured data from images.
- Project setup involves configuring Java 21 and incorporating essential dependencies like spring-boot-starter-web and spring-ai-openai-spring-boot-starter.
- Application properties are set to enable OpenAI integration, define upload limits, and facilitate image processing with the GPT-4o model.
- A use case example involves counting balloons of different colors in an uploaded image using structured data extraction.
- Data models such as BalloonColorCount and BalloonCountSummary are defined to represent color-count pairs and total counts of balloons.
- The BalloonAnalysisService class uses the ChatClient to communicate with GPT-4o, providing instructions and image data for structured response.
- A REST API in the BalloonImageController handles image uploads and color filtering requests, returning structured JSON responses.
- Post request to count colored balloons, along with a sample cURL request and expected JSON output, is provided.
- The application leverages Spring AI's ChatClient to send prompts, user input, and image attachments for structured data extraction from images.
Read Full Article
18 Likes
Dev
339

Image Credit: Dev
How I Built My First Web3 dApp: A "Buy Me a Coffee" Ethereum Tip Jar ☕
- The author shares their experience of building their first Web3 project, a 'Buy Me a Coffee' Ethereum tip jar.
- The dApp allows users to send ETH as tips, connect their MetaMask wallets, check the contract balance, and withdraw funds for coffee purchases.
- The author discusses the tech stack used, including HTML, CSS, JavaScript, TypeScript, Ethereum, Viem, and MetaMask.
- Key takeaways include starting small, learning TypeScript, handling MetaMask issues, and enjoying the process of building with Web3 technology.
Read Full Article
20 Likes
Dev
77

Image Credit: Dev
😵💫 The Solo Dev Struggle Is Real: Projects, Deadlines, Life… All at Once!!
- Developers often struggle with managing various aspects such as learning new frameworks, building side projects, and balancing work/life commitments.
- The challenges intensify for solo developers who have to juggle multiple roles like developer, designer, project manager, and even janitor.
- Many developers have unfinished projects due to external factors like exams, client work, or burnout, leading to a 'Unfinished Projects' Graveyard on their desktop.
- The article emphasizes the importance of collaboration and support within the developer community to overcome challenges, normalize sharing half-done projects, asking for help, and building together.
Read Full Article
4 Likes
RealPython
375

Image Credit: RealPython
Python Project: Build a Word Count Command-Line App
- Practice exercise to build a simplified version of the Unix wc command using Python.
- Tasks include reading content from files/stdin, counting lines, words, and bytes, handling Unicode, and implementing command-line arguments.
- Utilizes Python standard library modules like pathlib and argparse.
- Provides detailed instructions, examples, automated feedback, and support for learners.
Read Full Article
22 Likes
RealPython
44
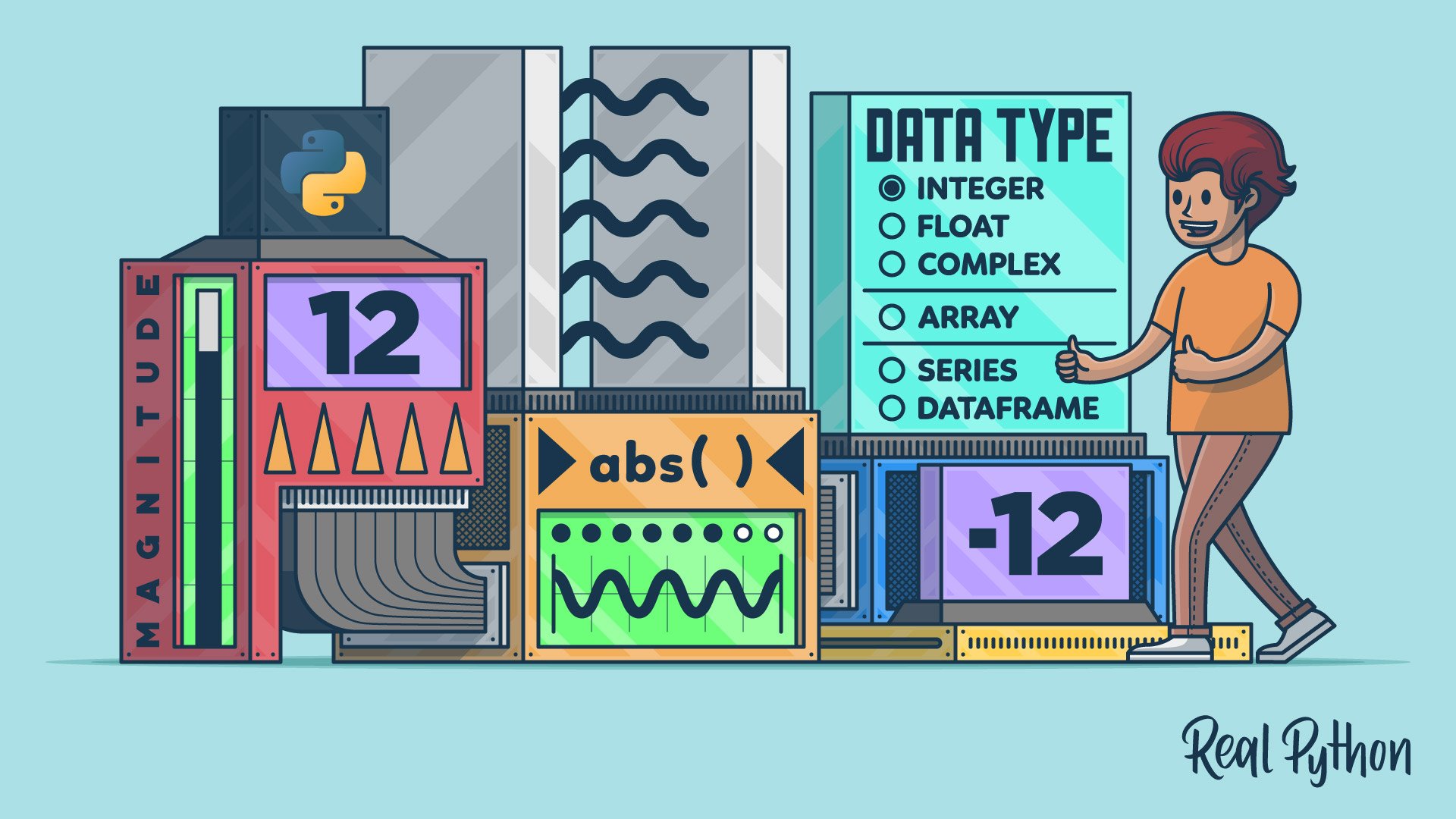
Image Credit: RealPython
How to Find an Absolute Value in Python
- Learn how to work with absolute values in Python using the built-in abs() function for numbers, arrays, and custom objects.
- Implement the absolute value function from scratch, use abs() with numbers, and customize its behavior for data types like NumPy arrays and pandas Series.
- Python's abs() function efficiently handles integers, floating-point numbers, complex numbers, and more.
- NumPy and pandas extend the abs() function to work directly with arrays and Series.
- Customize the behavior of abs() for your own data types by implementing the .__abs__() method.
- The abs() function can process fractions and decimals from Python's standard library.
- Absolute value helps determine the magnitude of an object, like a number or vector, regardless of direction.
- Absolute value function in Python can be implemented using conditional statements or mathematical operations.
- Visualizing absolute value as the distance from the origin on a number line or in multi-dimensional space like vectors.
- Understand how to calculate the length or magnitude of vectors using Euclidean norm.
Read Full Article
2 Likes
Medium
264

Image Credit: Medium
4D Hairy Ball and the Woven Continuum Theory with Numpy Proof
- The Woven Continuum Theory explores resolving topological obstructions in 3D systems by projecting higher-dimensional fields, such as in the 4D Hairy Ball theorem where singularities may be addressed in 4D or higher dimensions.
- The theory combines results like the parallelizability of S³, explicit recursion schemes, and fractal dynamics to unify topology, physics, and metaphysics under a balance paradigm.
- By embedding the 3-sphere S³ into 4D, a continuous, nowhere-zero vector field can cover what appears as zeros in 3D, presenting a topological foundation for '4D weaving.'
- The iterative correction formula in the Woven Continuum Theory continually corrects emergent zeros in a 3D field by drawing on an extra 4th dimension, ensuring a smooth passage through higher dimensions.
- Fractal dynamics and the use of 4D constructions like the Hopf fibration and quaternionic algebra play key roles in the iterative weaving procedure to avoid zeros in the field.
- The theory's application extends to addressing concrete areas like plasma confinement in fusion energy, quantum decoherence in quantum computing, and gravitational singularities in astrophysics through the lens of higher-dimensional weaving.
- Higher-dimensional embeddings like in the Randall–Sundrum model provide solutions to interpreting black holes and wormholes as folds in higher-dimensional weaves, showcasing how singularities may be a projection of a smooth higher-dimensional geometry.
- The Woven Continuum Theory emphasizes a philosophical viewpoint that singularities are not true endpoints but rather opportunities for evolution through higher-dimensional corrections, reflecting interconnected patterns in the universe.
- Concrete next steps outlined include explicit constructions, toy simulations, and experimental or computational tests to further validate and explore the implications of the theory in various fields.
- A Numpy proof example illustrates how the theory operates in a toy model scenario, showing how a 4D-inspired correction can eliminate zeros in a 3D field by borrowing from a quaternionic basis.
- The article delves into the Network of Hairy Balls, illustrating how multiple singularities can be addressed in a larger dimensional framework, presenting a metaphor of interconnected 'hairy balls' in a multi-dimensional weave.
- The Woven Continuum Theory not only introduces mathematical and physical concepts but also carries philosophical principles that view limits as illusions, advocate balance through recursion, and highlight the interconnected nature of complex systems in the universe.
Read Full Article
15 Likes
Dev
123

Image Credit: Dev
Node.js Image Upload System: File Handling, Storage, and Database Integration
- This tutorial focuses on building a server-side image upload system using Node.js.
- The system involves handling image uploads, storing them, managing metadata, and serving them back to the application.
- Steps include configuring routes, controllers, and using Multer for multipart/form-data handling.
- Setting up file storage, integrating with a database, and creating endpoints to manage image data are key components.
- Code snippets demonstrate creating routes for image upload and deletion functionality.
- Functionality for uploading, removing images, and sending images from the frontend are explained.
- Handling main images, additional images, and updating post data are detailed.
- Considerations such as image optimization, AWS S3 integration, and security measures are mentioned for future enhancements.
- The tutorial emphasizes error handling, security, file size limits, and encourages contributions and feedback.
- The provided code repository contains the complete tutorial implementation for reference.
Read Full Article
7 Likes
Javarevisited
322
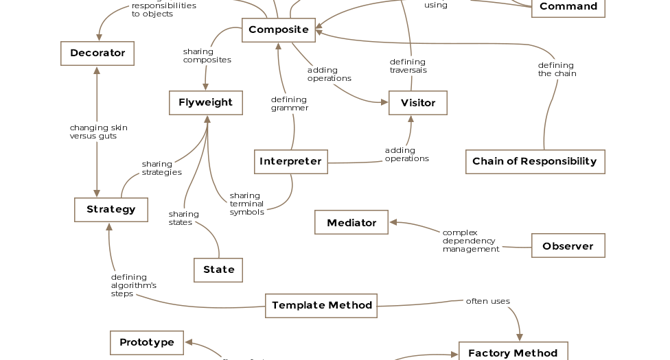
Image Credit: Javarevisited
Top 23 Design Patterns Experienced Java Programmers Should Learn
- Design Patterns are a tried and tested way of solving problems within a specific context, providing solutions discovered by the wider community.
- Learning Design Patterns can help in writing better code by utilizing established solutions to common object-oriented development tasks.
- There are 23 common object-oriented design patterns that experienced Java programmers should learn to enhance their coding skills.
- These patterns offer reliable solutions that may require some customization but generally provide effective problem-solving methods when applied correctly.
Read Full Article
19 Likes
Dev
172

Image Credit: Dev
Dumping Credentials with Python: Automating LSASS Access and Credential Extraction Post-Exploitation
- Accessing LSASS in post-exploitation scenarios provides valuable data such as passwords, hashes, and credentials, making it a prime target for red teamers and attackers.
- Extracting data from LSASS with Python offers a powerful tool for red teamers, giving insight into detection and defense measures that might obstruct such attempts.
- LSASS plays a crucial role in storing authentication artifacts, enabling attackers with the right access to perform pass-the-hash or pass-the-ticket attacks.
- Microsoft has hardened LSASS against unauthorized access through measures like running it as a Protected Process Light and utilizing Virtual Secure Mode.
- Python-based approaches for LSASS dumping include direct memory access using ctypes and Windows APIs, minidump creation with MiniDumpWriteDump, and parsing dumps with pypykatz.
- Evasion techniques to stay stealthy during credential dumping involve using legitimate processes, forking LSASS, and avoiding disk I/O to prevent detection.
- Python's flexibility allows red teamers to automate LSASS credential extraction quietly and efficiently, navigating the evolving landscape of detection by defenders.
- Understanding the mechanisms of LSASS credential extraction and employing evasive workflows are essential for red teamers to maintain their capabilities effectively.
- Automating LSASS credential dumping using Python provides red teamers with a potent capability when executed with precision and stealth.
- LSASS access and credential extraction offer red teamers key insights into Windows systems, enabling them to navigate networks effectively and escalate privileges.
- For further information and updates, follow DevUnionX at https://x.com/DevUnionX.
Read Full Article
10 Likes
Javarevisited
185

Image Credit: Javarevisited
How Long does It take To Learn Linux?
- Learning Linux can be a quick process, with the basics being graspable in a weekend. However, mastering Linux may take weeks as there are numerous commands and concepts to understand.
- The time it takes to learn Linux depends on your specific goal. For developers, it might take a week, while for System Administrators, it could be months due to the requirement of deeper knowledge.
Read Full Article
11 Likes
Medium
0
Image Credit: Medium
The Silent Threat: Unhandled Promise Rejections in JavaScript
- Unhandled promise rejections in JavaScript can lead to silent failures, missing data, broken features, or security holes.
- Unlike synchronous errors, unhandled promise rejections happen asynchronously, may not crash your script, and are not always immediately visible.
- Adding a `.catch()` handler after a promise rejection does not retroactively fix the issue; it needs to be handled immediately.
- To prevent silent failures, it is crucial to attach a `.catch()` to every promise in JavaScript or use `try/catch` with `async/await`.
Read Full Article
Like
For uninterrupted reading, download the app