Programming News
Dev
71

Image Credit: Dev
Flutter Deep Linking: Pathways to specific app content
- Deep linking in Flutter allows linking directly to specific content within a mobile app, enhancing user experience and marketing campaigns.
- It involves using traditional deep links, deferred deep links, and universal links (iOS) / app links (Android).
- Deep links consist of a scheme, host, path, query parameters, port, and fragment to direct users to app content.
- Android setup for deep linking involves adding supported hosts to the manifest, verifying domains, and testing deep links.
- iOS setup includes configuring associated domains, adding URL schemes in info.plist, and verifying the iOS server for deep links.
- Handling deep links in Flutter with GoRouter offers URL-based navigation and setting up routes for different screens.
- To navigate to the deep link destination, metadata needs to be added in AndroidManifest.xml for Android and Info.plist for iOS.
- Testing deep link implementation on Android and iOS is crucial to ensure navigation to the specific screen.
- In conclusion, deep links improve user experience by providing direct access to app content, and GoRouter supports deep linking in Flutter.
- The article covers setup, implementation, and testing of deep links in Flutter for Android and iOS, enhancing user experience and cross-platform consistency.
Read Full Article
4 Likes
Medium
14

Inferiority Complex and You
- Inferiority complex can be damaging and lead to low self-confidence and self-worth.
- It can prevent individuals from embracing their own abilities and achievements.
- Constantly comparing oneself to others can fuel feelings of inferiority.
- Inferiority complex can erode one's sense of self and lead to 'imposter syndrome.'
- People may not realize the impact of inferiority complex until others start mistreating them.
- No one deserves to be mistreated, regardless of their perceived inadequacies.
- The author shares a personal story of succumbing to inferiority complex and its consequences.
- Encourages individuals to stop comparing themselves to others and focus on self-improvement.
- Recommends reprogramming oneself and starting the journey of self-discovery and growth.
Read Full Article
Like
Dev
171

Image Credit: Dev
🚀 Hack Club Summer of Making 2025: Code, Create & Win Prizes!
- Hack Club Summer of Making 2025 offers a platform for high school students to code, create, and win prizes.
- Participants can build cool projects, including websites, robots, games, and hardware hacks, while receiving funding, mentorship, and prizes.
- It is a celebration of youth creativity and open-source building, not a competition.
- Two ways to win prizes: building projects for ages ≤18 and referring friends of all ages.
- To earn rewards, sign up on summer.hackclub.com, submit projects, and refer friends through pyramid.hackclub.com.
- Sharing referral links in various spaces like schools, coffee shops, and libraries can increase chances of winning epic prizes.
- Prizes ship globally from Hack Club HQ in Vermont, USA, with free international shipping covered.
- Joining or sharing the Summer of Making allows participants to build portfolios, gain tech experience, win prizes, and be part of a global teenage maker community.
- The initiative encourages individuals to help teens discover tech and offers rewards for spreading the word.
- The program is aimed at making the summer meaningful by engaging in tech projects and collaborations.
Read Full Article
10 Likes
Medium
343
Image Credit: Medium
The Math Problem Built for Cruelty
- A mathematics problem with a dark past was used in the Soviet Union to exclude certain students, mainly talented Jewish individuals, from top math academies in the 1970s and 1980s.
- These special entrance exams contained extremely challenging problems with surprisingly simple solutions, designed to identify and exclude undesirables.
Read Full Article
20 Likes
Discover more
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Dev
430

Image Credit: Dev
Structuring GitHub Enterprise: Best Practices from the Org Level Down
- The article discusses best practices for structuring GitHub Enterprise from the organizational level down, emphasizing the importance of proper structuring for optimal efficiency and security.
- It highlights the key layers in a GitHub Enterprise environment: GitHub Enterprise Account, Organizations, Teams, and Repositories, explaining their roles and significance.
- The post provides insights on defining clear organizational boundaries based on access rules, visibility needs, or ownership differences, and outlines scenarios for creating new organizations.
- It advocates for standardizing organizational settings, enforcing enterprise-wide policies, using tools for alignment, and utilizing teams for collaboration and permissions.
- The article also covers best practices for naming conventions, repository templates, tagging, permissions, security measures, automation, observability, and common pitfalls to avoid.
- With a focus on scalability and efficiency, it offers practical tips to optimize GitHub Enterprise setup for enhanced productivity and reduced complexities.
Read Full Article
25 Likes
Medium
414
Image Credit: Medium
Best Laptop for Coding and Programming
- Choosing the best laptop for coding and programming depends on various factors like workflow and specific needs.
- The MacBook Pro 14 (M4 Pro) is recommended for its quiet power, long battery life, and seamless experience, but the best laptop choice varies based on individual requirements.
- A ThinkPad might be ideal for a backend engineer using .NET, while a MacBook could be suitable for iOS app developers or video editors.
- Selecting a laptop for coding should prioritize efficiency, effective coding, and maintaining focus during work.
- The right laptop choice enables faster coding and improved productivity without hardware issues.
- Developers have diverse workflows, such as front-end specialists, backend architects, or AI professionals, which influence laptop preferences.
- The article encourages sharing experiences with different coding laptops to help others make informed choices and avoid costly mistakes.
- The author invites readers to comment on their coding laptop preferences and experiences.
- Honest feedback based on practical use, not marketing tactics, is offered to those struggling to decide between laptop options.
- The article aims to assist readers in choosing the right tools for coding and programming tasks and enhancing their coding experiences.
- The author emphasizes collaboration in the coding community to support each other in selecting the most suitable laptops for coding endeavors.
Read Full Article
24 Likes
Dev
303

Image Credit: Dev
6 Ways AI Can Improve Your Python Code(Tested!)
- AI is transforming how software is built and maintained, offering automation and bug detection for flawless Python code.
- Automated AI-powered code reviews streamline the review process, detect bugs, and enforce coding standards efficiently.
- Advanced static analysis with AI identifies subtle bugs and security flaws, enhancing code quality and security.
- AI-generated testing automates test case generation, improving code coverage and catching bugs early in Python applications.
- AI-driven documentation maintains code consistency, generates explanatory docstrings, and simplifies code understanding.
- AI-powered developer assistants provide code completion suggestions and accelerate coding, leading to cleaner Python code.
- AI aids code refactoring by analyzing and recommending systematic refactors, ensuring code consistency and efficiency.
- AI is essential for writing high-quality Python code at scale, enhancing processes without disruption.
- By embracing AI tools, teams can improve code quality, catch bugs early, and streamline development workflows.
- Experimenting with AI tools can lead to smoother processes, fewer bugs, and increased confidence in software releases.
Read Full Article
18 Likes
Medium
283

☕ Java the Right Way: Modern Standards for Effective & Secure Coding
- Java developers are encouraged to upgrade to Java 17+ for modern, clean, and secure coding practices.
- Spring Boot combined with Spring Security is essential for efficient Java programming.
- Prioritize code security with a checklist and use Project Lombok to reduce boilerplate code.
- Layer your application intelligently to avoid a messy, unmanageable codebase.
- Testing rigorously is crucial; avoid using main() as a test.
- Packaging your application with Docker is now a necessary step for developers.
- Using tools for code quality leads to team satisfaction and productivity.
- Stay cloud-ready and adapt to new technologies in the Java ecosystem.
- Continuous learning, refactoring, and code reviews are recommended to keep up with Java's evolution.
- Following modern coding practices ensures effective, secure, and maintainable Java code.
Read Full Article
16 Likes
Infoq
96

Image Credit: Infoq
Article: Beyond Objects and Functions: Exploring Data-Oriented Programming
- Data-oriented programming (DOP) focuses on data, memory access patterns, and performance optimization, complementing OOP and FP especially in compute-heavy environments like gaming and trading.
- DOP separates data from behavior, optimizes memory access by storing data in contiguous memory blocks, reduces cache misses, and utilizes SIMD algorithms for batch processing.
- Advantages of DOP include improved data access speed, flexibility in logic/data structure changes, optimized for modern hardware, and reduced coupling between program components.
- Challenges of DOP include complexity for OOP developers, potential over-optimization, integration complexities with other paradigms, and fewer specialized tools compared to OOP.
- DOP benefits from features like Struct of Arrays (SoA) layout, Entity Component System (ECS) frameworks, parallel processing, SIMD aware data layouts, and batch-oriented processing.
- Java 21 introduces Unnamed Patterns and Variables to align with DOP principles, improving readability and efficient data manipulation in Java programming.
- DOP is crucial for performance-critical applications but may not be suitable for all projects, offering advantages in scalability and data processing efficiency.
- Some articles on DOP lack practical solutions and beginner-friendly explanations, highlighting the importance of understanding when DOP can outperform OOP and FP.
- DOP optimized for large data processing while OOP focuses on individual object manipulation with tight coupling between data and behavior.
- By implementing DOP techniques, developers can enhance scalability and efficiency, creating opportunities for rapid calculations and effective data processing in various fields.
Read Full Article
5 Likes
Medium
426
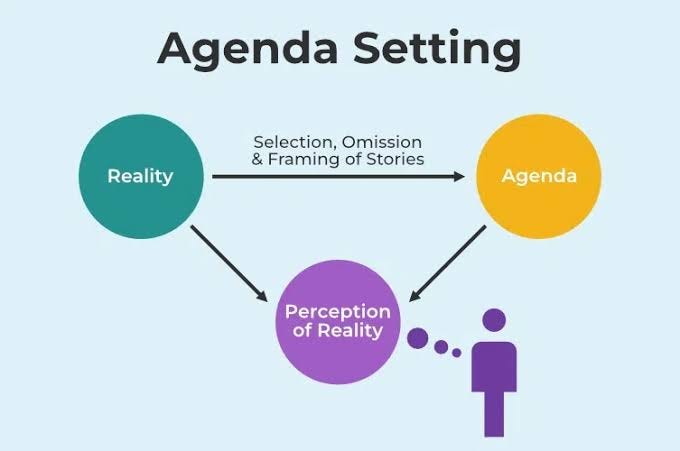
Image Credit: Medium
Agenda Setting Theory: How the Media Decides What You Care About
- Agenda Setting Theory, developed by McCombs and Shaw in 1972, suggests that the media influences what the public considers important by determining what stories receive attention.
- The theory was first showcased during the 1968 U.S. presidential election, where media coverage correlated with public opinion, indicating media's role in shaping viewpoints.
- Agenda setting works through tools like frequency, placement, tone, and omission to highlight specific issues and make them appear more significant.
- In the digital age, agenda setting has evolved with the internet and social media, as trending topics influence news coverage and algorithms determine content visibility.
- Agenda setting impacts various sectors including politics, advertising, entertainment, public health, and international relations by influencing focus areas and public discourse.
- Benefits of agenda setting include raising awareness about urgent matters, guiding public conversation, and mobilizing action, as seen during the COVID-19 pandemic.
- However, agenda setting also poses risks such as bias, manipulation, distraction from real issues, and polarization, potentially leading to misinformation and societal divisions.
- Key takeaways include understanding how agenda setting shapes awareness, recognizing the importance of overlooked stories, and acknowledging the influence of individual participation in setting agendas.
Read Full Article
25 Likes
PlanetPython
149

Image Credit: PlanetPython
Python Software Foundation: The PSF's 2024 Annual Impact Report is here!
- The Python Software Foundation had a remarkable year of growth in 2024.
- Python became the most popular language on GitHub, and community engagement reached record levels.
- Key highlights of the year include welcoming a PyPI Support Specialist, revival of workgroups, and continued investment in grants and infrastructure.
- The Annual Impact Report includes a letter from the Executive Director and updates from various key figures.
- Developers-in-Residence achievements and PyPI updates are featured in the report.
- The report also covers PyCon US 2024, fiscal sponsees, sponsors, and PSF financials.
- The PSF encourages sharing the report with the Python community and providing feedback.
- The report encapsulates significant numbers, details, and insights from the past year.
- Updates on PyPI Safety & Security Engineer's work are included in the report.
- Readers can find information about PyCon US 2025, achievements of Developers-in-Residence, and PyPI stats.
- Sponsors who supported the PSF and the Python ecosystem are highlighted in the report.
- PSF Financials, financial statements, and grants data are part of the Annual Impact Report.
- The PSF recommends engaging with them on social media platforms or through the Python Discuss thread.
- The report provides a comprehensive overview of the Python Software Foundation's activities and accomplishments in 2024.
- Community members are encouraged to review the report and share their thoughts with the PSF.
- The Python Software Foundation's growth and achievements are highlighted in the 2024 Annual Impact Report.
Read Full Article
9 Likes
Medium
400

Earn More with Roam App: Simple Ways to Maximize Your Roam Points
- Roam's core feature, the Roam Miner, allows users to passively earn Roam Points by running the app and scanning WiFi signals.
- Adding new WiFi networks through the app can increase earnings and contribute to improving location services for everyone.
- Consistent daily check-ins on the Roam App can earn users extra Roam Points with just one tap.
- Roam offers a referral program where users can earn bonus points for successful referrals, helping the network grow and getting rewarded.
- Participants in Roam's community events, challenges, and campaigns can earn extra Roam Points and token rewards.
- Joining the Roam community allows users to engage in events, meet fellow users, and boost their earnings.
- Roam App provides an opportunity to earn crypto rewards by mining, connecting WiFi, referring friends, and participating in community events.
Read Full Article
24 Likes
Javacodegeeks
101

Image Credit: Javacodegeeks
How to Replace a Specific Word in a File Using Java
- The article discusses various methods to replace a specific word in a text file using Java.
- The first method involves java.nio.file.Files for reading and writing files, replacing the target word and updating the file using Streams.
- The second method uses classic java.io classes BufferedReader and BufferedWriter for memory efficiency, replacing the word and updating the file securely.
- The third method showcases the use of Apache Commons IO for simplified file reading and writing with utility methods.
- Each method demonstrates how to replace occurrences of a word in a file with another specified word.
- The article provides code snippets and explanations for implementing each method.
- The Java program using java.nio.file.Files reads all lines of the file, replaces the target word, and writes the updated content back to the file.
- The Java program using BufferedReader and BufferedWriter processes the file line by line, replaces the word, and updates the file securely.
- The Java program using Apache Commons IO simplifies file reading and writing, making word replacement more concise.
- The article concludes by summarizing the different approaches discussed in the text.
Read Full Article
6 Likes
Nordicapis
13

APIs and Identity in the Age of the Sovereign Cloud
- Peter Steiner’s 1993 cartoon in The New Yorker humorously depicted online anonymity with the famous phrase 'On the Internet, nobody knows you're a dog.' The rise of the sovereign cloud movement, emphasizing control and compliance, is impacting identity management in the digital space.
- The sovereign cloud movement, gaining traction in the EU, focuses on ensuring proper authorization amid new legislation and federated login systems, sparking significant changes in authentication standards and API access with regional restrictions.
- European lawmakers aim to reduce reliance on foreign-owned digital services, favoring 'sovereign digital infrastructure' to enhance economic independence and security, reflecting global concerns around data jurisdiction and control.
- Sovereign clouds, tailored for specific regulatory environments like the EU's GDPR, require compliance with data processing laws of their respective regions, leading major providers like Amazon and Google to engage in such initiatives.
- In the context of digital sovereignty, ensuring cross-border compliance for API data transfers between jurisdictions becomes crucial, with GDPR-inspired practices such as access controls and encryption playing a key role in meeting regulatory standards.
- The emergence of regional identity providers like itsme and SwissID challenges existing authentication protocols, potentially necessitating a shift towards decentralized identity standards to address interoperability and compliance hurdles.
- The shift towards enhanced identity verification, potentially via self-sovereign identity and verifiable credentials, may lead to greater data security but also raise concerns about privacy and anonymity, as seen in recent legal and ethical debates.
- While sovereign cloud initiatives aim to improve security and control over data access, the trade-off with online anonymity is evident, prompting discussions on how to balance identity verification without compromising individual privacy.
- The move towards stricter data controls and regional identity verification may offer opportunities to innovate in secure authentication methods, leveraging technology like zero trust architecture and decentralized identifiers via APIs.
- In this evolving landscape of digital sovereignty and identity management, APIs could serve as a vital tool in maintaining online security and privacy while adapting to changing regulatory landscapes and technological advancements.
- The article delves into the implications of the sovereign cloud movement on digital identity, highlighting the tension between enforcing compliance and protecting user privacy in an increasingly regulated and interconnected online environment.
Read Full Article
Like
Dev
17

Image Credit: Dev
Setting up a Python project with CMake
- CMake can be used to set up and run Python applications in mixed-language projects.
- The unique approach allows for running any application with a single command.
- Project structure includes separate directories for each application, each with its own CMakeLists.txt file.
- CMakeLists.txt file includes functions to create Python virtual environments and install dependencies from requirements.txt.
- Individual app directories contain CMakeLists.txt files to setup virtual environments and run applications.
- Running 'cmake .' in the build folder initiates the setup of virtual environments and downloads dependencies.
- Build all targets using 'cmake --build .' command.
- Applications can be run using 'make run_app1', 'make run_app2', and 'make run_app3' commands.
- Targets can also be executed in VS Code using the CMake GUI interface.
- Ninja can be used as an alternative to 'make' for generating configuration.
- Generate Ninja configuration with 'cmake .. -G Ninja' and build with 'cmake --build .'.
- Run applications using 'ninja run_app1', 'ninja run_app2', and 'ninja run_app3' commands.
Read Full Article
1 Like
For uninterrupted reading, download the app