Programming News
UX Design
334

Image Credit: UX Design
Inferred art—painting a computer program
- Generative AI is currently in the spotlight for its ability to create realistic images, sparking debates on AI's impact on art and artists' rights.
- OpenAI's GPT-40 has led to the trend of 'Ghiblifying' images, blurring the lines between AI-generated art and human creativity.
- There is a shift towards depicting what a computer is 'doing' instead of having computers generate desired images, challenging the boundaries between art and mimicry.
- Exploring the relationship between art and AI through the concept of painting a computer program offers new perspectives on creativity and artistic expression.
Read Full Article
20 Likes
Dev
397

Image Credit: Dev
How I Built a CSS Container Query Converter To Make my Work Easier
- Traditional media queries only respond to the viewport size, creating a challenge in component-based design to make a component respond to its parent container rather than the entire screen.
- Container queries respond to the size of the parent element, making them a game-changer for component-based design by enabling components to adjust based on their container size.
- The CSS Container Query Converter Tool automates the conversion of traditional media queries into container queries, saving significant time and effort in manual conversion work.
- Container queries not only solve design challenges but can also improve page performance by triggering recalculations for specific containers rather than the entire page, resulting in smoother animations and interactions.
Read Full Article
23 Likes
Medium
50
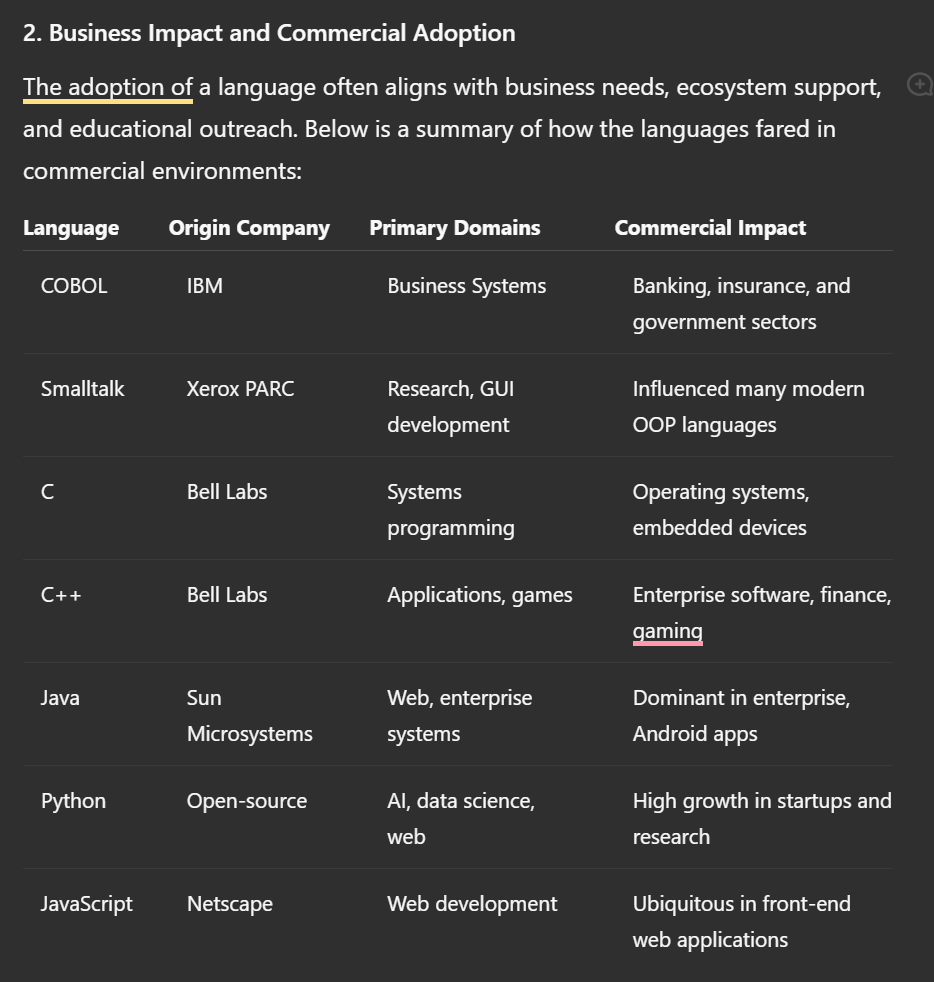
Image Credit: Medium
The Evolution of Programming Languages: From Machine Code to Modern AI
- IBM played a crucial role in the development of business-oriented programming languages like COBOL and PL/I.
- Xerox PARC introduced Smalltalk in the 1970s, which influenced modern languages such as Java and Python with its object-oriented principles.
- Bell Labs created C and C++, which became industry standards in systems programming and embedded systems.
- Market share and usage trends of programming languages are analyzed through metrics like Stack Overflow Developer Surveys and GitHub repositories.
- Early languages like ALGOL had minimal presence in the commercial computing market in the 1960s.
- From the 1970s to 1980s, system software development involved using assemblers to translate instructions into machine code.
- Variables in programming act as containers that hold values, similar to boxes holding items.
- Pointers in programming indicate the location of data rather than holding the actual data.
- Conditional statements in programming allow for decision-making based on specific conditions.
- Functions in programming serve as commands that execute a series of defined tasks.
Read Full Article
2 Likes
Medium
31

Image Credit: Medium
How Retail Stores Can Improve Customer Experience with Payment Kiosks
- Payment kiosks in retail improve customer experience by reducing wait times and enhancing convenience with self-checkout options.
- Kiosks support various payment methods and operate 24/7, offering privacy for customers during transactions.
- Integration with inventory systems provides real-time product availability, boosts trust, and enhances the shopping experience.
- Kiosks simplify loyalty program processes, offer personalized promotions, and increase engagement with the brand.
- Design considerations for kiosks include ease of use, accessibility features, multilingual support, and strategic placement in stores.
- Regular maintenance, cybersecurity measures, and staff training are crucial for the reliability and performance of payment kiosks.
- Future trends in kiosks include AI integration for personalized interactions, touchless technology for secure payments, and omnichannel capabilities.
- By leveraging advanced technologies and user-centric design, payment kiosks can drive exceptional customer experiences and operational efficiency in retail.
- Retailers should consider kiosks as strategic investments that enhance customer satisfaction and bridge online-offline experiences for a unified shopping journey.
Read Full Article
1 Like
Discover more
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Dev
374

Image Credit: Dev
The “Events” Module in OneEntry: Automation and Integrations on a New Level
- The Events module in OneEntry serves as a conductor of automation, reacting to data changes, sending notifications, triggering integrations, and enhancing user engagement without backend code.
- It acts as a centralized event system, connecting business logic, user notifications, and external systems, handling tasks efficiently and reducing the developer's workload.
- The module allows for quick, accurate, and reliable handling of user notifications, integrations with external systems, and automation of routine tasks without burdening the team.
- In OneEntry, event configuration is logic-based rather than code-based, enabling easy setup of reactions to any event in the system even for non-programmers.
- The OneEntry NPM Helper Beta accelerates event implementation by simplifying API requests, offering a convenient interface for event creation, and generating data types for increased stability.
- OneEntry outperforms platforms like Firebase, AWS, Supabase, etc., by offering flexible event logic, built-in notifications across multiple channels, and configuration through a visual interface.
- It simplifies event triggers, eliminates the need for third-party services for notifications, and allows for advanced logic setup without extensive coding.
- With OneEntry, managing attributes and events is user-friendly, with features like markers for dynamic personalization and ready-to-use integration scenarios for connecting to external systems.
- The platform delivers tangible results, such as a 40% reduction in user response time, 30% less load on support teams, and a 20% increase in repeat purchases due to personalized notifications.
- By using OneEntry, businesses can save time, reduce workload, and enhance user experience through streamlined automation and efficient event management.
Read Full Article
22 Likes
Dev
162

Image Credit: Dev
Best Practices for Writing Clean Code
- Bad code is not just ugly, it's expensive, breaks easily, hard to maintain, and makes teams slower.
- Real-world clean code principles every programmer should follow in 2024.
- 1. Name things descriptively, avoid abbreviations, use consistent naming conventions.
- 2. Write small functions that do one thing, use intention-revealing names.
Read Full Article
9 Likes
Medium
302

Image Credit: Medium
Understanding The Power of Linear Algebra for Modern Programming
- Linear algebra is increasingly important in programming fields like AI, data science, game development, and robotics.
- Understanding linear algebra enhances the ability to write efficient and robust code in various applications.
- It provides a structured approach to handling high-dimensional data and solving real-world problems.
- Higher education delves into advanced concepts like vector spaces and eigenvalues for real-world application.
- Linear algebra is extensively used in data science, computer graphics, machine learning, and engineering.
- Machine learning models rely heavily on matrix operations and solving systems of equations.
- Computer graphics and game development use linear algebra for object manipulation and projection.
- Data science techniques like PCA and clustering utilize linear algebra concepts.
- Optimization, algorithms, computer vision, and robotics all benefit from linear algebra applications.
- Understanding linear algebra is crucial for troubleshooting, optimizing, and efficiently running code.
Read Full Article
18 Likes
Medium
415
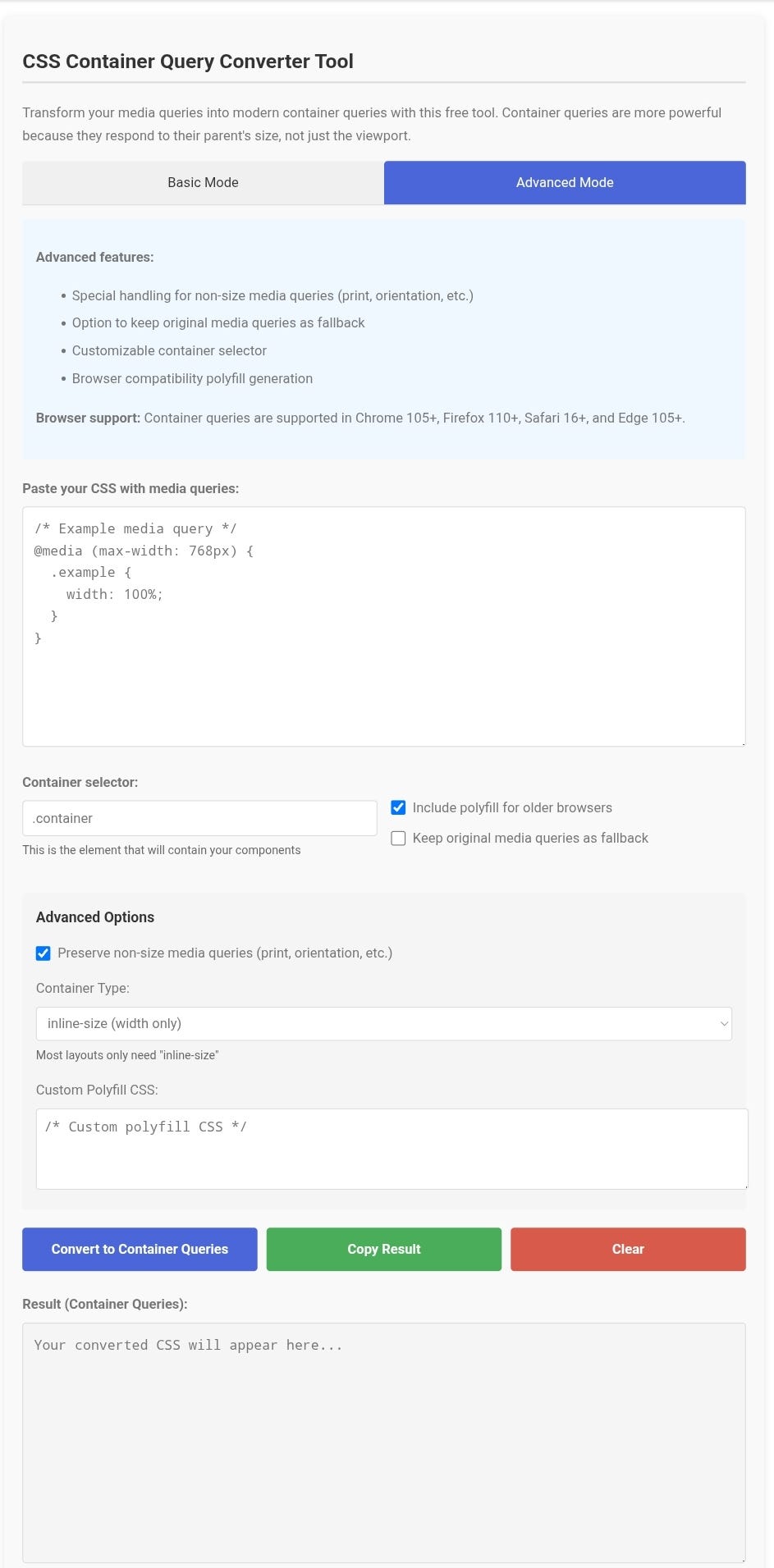
Image Credit: Medium
"How I Built a CSS Container Query Converter to Make My Work Easier
- Traditional media queries respond to the viewport size, while container queries respond to the size of the parent element.
- CSS Container Query Converter Tool transforms traditional media queries into modern container queries, saving time and effort.
- Container queries have shown to improve page performance by triggering recalculations for specific containers, leading to smoother animations and interactions.
- To use container queries, add 'container-type: inline-size' to the desired element, replace '@media' with '@container' in CSS, and witness components responding to parent containers.
Read Full Article
24 Likes
Javacodegeeks
171

Image Credit: Javacodegeeks
[DEALS] Babbel Language Learning: Lifetime Subscription (All Languages) (71% off) & Other Deals Up To 98% Off – Offers End Soon!
- Fresh offers on Deals store: Babbel Language Learning Lifetime Subscription (All Languages) at 71% off.
- Other offers include Apple MacBook Air, 1min.AI, Koofr Cloud Storage, Sterling Stock Picker, EDU Unlimited by StackSkills, Internxt Cloud Storage, Premium Learn to Code Bundle, and more at discounted prices up to 98% off.
- Special deals on NanoPhone, FileJump 2TB Cloud Storage, and various technical eBooks on Java and other topics.
- Subscribe to the newsletter for more offers and to receive free eBooks on Java, JPA, JVM troubleshooting, JUnit, Java Annotations, Spring, Android UI Design, and more.
Read Full Article
10 Likes
Dev
18

Image Credit: Dev
Unlocking Global Transactions: A Guide to the Best Currency Exchange Free API for Developers
- Currency exchange free APIs are essential for developers working on apps dealing with e-commerce, travel, or finance with international users.
- Benefits of using a free API include cost-effectiveness, quick development, sufficient limits, and the ability to test before committing.
- Key features to look for in a currency exchange API include real-time rates, historical data, support for multiple currencies, secure HTTPS connection, and flexible output formats.
- Leading free currency exchange APIs like Exchangerate.host, Currencylayer, Open Exchange Rates, and Fixer.io offer various features and benefits for developers in different use cases.
Read Full Article
1 Like
Medium
221

Image Credit: Medium
World Preeclampsia Day: Beware of ‘silent killer’ in pregnancy, know symptoms and prevention from…
- World Pre-eclampsia Day is celebrated on 22nd May to raise awareness about the serious pregnancy-related condition.
- Pre-eclampsia affects about 5-8% of pregnant women and its symptoms, like high blood pressure, swelling, and increased protein in urine, may not be evident until it becomes life-threatening.
- Risk factors for pre-eclampsia include abnormality in the placenta, age (less than 18 or more than 40), pre-existing health conditions, and previous history of pre-eclampsia.
- Complications of pre-eclampsia can range from organ failure to fetal complications, and treatment involves monitoring blood pressure, lifestyle changes, and may require delivery if the condition worsens.
Read Full Article
13 Likes
Dev
326

Image Credit: Dev
Best Programming Languages for Beginners: Where to Start in 2025
- In 2025, AI is mainstream, leading to Python's increased relevance for tasks like AI, web development, and automation.
- For beginners, Python, JavaScript, Scratch, C#, Swift, Kotlin, and Go are highlighted as top languages to consider learning.
- Python is recommended for its readable syntax, vast library support, and applications in data science, web scraping, and AI.
- JavaScript is praised for its versatility in web development, running in browsers, and being core to web applications.
- Scratch is recommended for absolute beginners, especially kids, due to its visual, drag-and-drop coding interface.
- C# is suggested for game development and Windows apps, with strong demand in gaming and enterprise software sectors.
- Swift is highlighted for its use in the Apple ecosystem, particularly for iOS app development and Apple Watch interfaces.
- Kotlin is noted as the official language for Android development, with cleaner syntax than Java and interoperability with Java libraries.
- Go (Golang) stands out for its performance and simplicity, ideal for backend systems, APIs, and scalable web applications.
- Beginners are advised to avoid languages like C/C++, Java, PHP, and R unless there are specific reasons for learning them.
- To choose a language based on goals, recommendations include Python for automation, JavaScript for websites, Swift and Kotlin for mobile apps, and C# for game development.
Read Full Article
19 Likes
Zerynth
13

Image Credit: Zerynth
Why Cold Chain Monitoring Is Crucial for Food Companies
- The cold chain is essential for maintaining controlled temperatures of perishable food throughout the supply chain to preserve product integrity and prevent bacterial growth.
- Cold chain monitoring helps food companies ensure food safety, reduce waste, and comply with hygiene regulations by tracking temperatures in real time.
- Zerynth's Wi-Ref solution offers plug-and-play continuous monitoring of the cold chain with wireless IoT devices, custom thresholds, automatic alerts, and cloud-based reporting.
- Digitalizing the cold chain with solutions like Wi-Ref is crucial for food companies to demonstrate commitment to quality, sustainability, and innovation in a competitive market.
Read Full Article
Like
Medium
162

Image Credit: Medium
Infographic vs. Dashboard: What Works Better and When?
- Infographics and dashboards serve different purposes - infographics for one-time communication and dashboards for ongoing interaction.
- Infographics are static, elegant, and consumable at a glance, while dashboards are dynamic, interactive, and used for real-time decision-making.
- Knowing when to use each tool and designing them effectively, especially in tools like Power BI, is crucial for conveying messages and insights effectively.
- This article discusses when to choose an infographic vs. a dashboard, how to incorporate them into business intelligence workflows, and the benefits of combining both for maximum impact.
Read Full Article
9 Likes
PlanetPython
63
Image Credit: PlanetPython
Django Weblog: Why, in 2025, do we still need a 3rd party app to write a REST API with Django?
- In 2025, the question was posed regarding the necessity of using a 3rd party app to create a REST API with Django.
- While Django REST Framework and Django Ninja are recommended for complex APIs, a simple CRUD API can be built without a 3rd party app.
- The article focuses on creating a simple REST API using Django features like generic class-based views.
- A JsonViewMixin is introduced to handle JSON responses in Django views.
- Forms are used as serializers to convert model data to JSON-serializable formats.
- JsonListView is created to list records from a model, emphasizing the serialization of data.
- JsonListCreateView combines listing and creating records by extending BaseCreateView.
- JsonReadUpdateView handles reading and updating single records by extending BaseUpdateView.
- A JsonReadUpdateDeleteView is implemented to handle the delete operation for objects.
- Despite the simplicity of the approach, utilizing Django's generic CBVs enables building a mini REST framework with minimal code.
Read Full Article
3 Likes
For uninterrupted reading, download the app